Contents:
Looking to sink your teeth into some good security tips you can actually apply? Today’s collection of action-ready cybersecurity advice might be just what you need. There are no less than 131 ways in which you can improve your online safety and they’re all FREE to use and apply. You’ll be surprised by the things you can do to better secure your data! All it takes is spending some time reading the right things and adjusting a few settings. Applying these security tips feels just as good as digging into a plate of hot, fluffy, syrupy pancakes. Seriously, you have to try it! 
Cyber Security Tip #1: How to be realistic about your online presence
Understand that you’re an attractive target for cyber criminals. If you have money (doesn’t matter how much), data (usernames, passwords, documents, emails, etc.) or a place to work, you’re going to be targeted. It’s not even personal, as cyber criminals automate most of their attacks. Don’t ever say “it can’t happen to me.”
Cyber Security Tip #2: The basics of safe online shopping
Online shopping safety: never do ith from a device that isn’t yours or on a network you don’t own. Your data could be copied and harvested by cyber criminals. Make sure you’re the only one spending your money by:
- Using safe network
- Employing strong passwords (password managers FTW!)
- Being careful about which websites you shop at
- Never saving your card details in an online account
- Verifying your transactions weekly to make sure there’s nothing fishy going on.
Want more tips? Get them here: All the Actionable Tips You Need to Safely Shop Online.
Cyber Security Tip #3: Should you plug that in?
Careful on what you plug into your computer. Never use a USB whose source you don’t know! It can be infected with malware that can even resist formatting. Don’t let curiosity get the best of you.
Cyber Security Tip #4: Who’s that friend request from?
Facebook friends or foes? Cyber criminals often create fake profiles to befriend you. The ultimate goal is to get you to leak confidential data to them (either about you or the company you work for). Be careful of the friend requests you accept. Trust no Facebook friend (unless you know them in real life and you’re absolutely, positively sure they can be trusted).
Cyber Security Tip #5: How to protect your passwords in real life
Who’s looking over your shoulder? Did you know that bystanders or co-workers can steal your passwords only by peeking at what you’re typing? This is especially true is your passwords are as easy as 123456 (please change them if it’s the case). Take a look around and make sure everything’s safe before typing a password. Also: NEVER share your passwords. Ever.
Cyber Security Tip #6: You still need antivirus (yes, really)
Get protection for your connection! Do a bit of research and choose an antivirus you trust. Paid is better than free. Antivirus is still very necessary, so don’t skip it. How to do it: What Is the Best Antivirus for My PC? A Step-By-Step Research Guide.
Cyber Security Tip #7: Get your 2-FA on
Use 2-factor authentication everywhere you can. Set it up to receive authentication codes via sms or on an authenticator app. Moar layers = moar securiteh! How to do it: Why You Should Start Using Two-Factor Authentication Now
Cyber Security Tip #8: Keep it in check
Check your bank statements on a weekly basis (your online banking can help you do that easily). Look for suspicious activity and, if any, alert your bank, change all passwords related to that account and make sure to activate every security measure available. Financial malware lurks just around the corner.
Cyber Security Tip #9: Lock it up
Never leave your laptop/smartphone/tablet unlocked while you’re away. Don’t make it so easy for anyone to get into your system. Set up a password for your account asap (it’ll only take 2-3 minutes).
Cyber Security Tip #10: How to protect what matters
Prioritize your most sensitive accounts. Here’s a quick list:
- Online banking / Paypal
- Amazon / other ecommerce website you use
- Any account where you’ve put in your card details
- Any account that has sensitive info (social security number, address, phone no., etc.).
Secure them with strong passwords + two-factor authentication. Make it as difficult as possible for anyone other than yourself to access them. Be a cyber security ninja!
Cyber Security Tip #11: Cleaning out your closet
Here’s a tip that applies to both your wardrobe and your apps: if you haven’t used it in the past 6 months, it should go. Clean out old apps you don’t use to get rid of vulnerabilities that cyber criminals can exploit. Keep it fresh!
Cyber Security Tip #12: A cure for your Internet addiction
How badly do you need to use someone else’s computer? You can never know if someone else’s computer is infected with malware, has a keylogger (that tracks and stores everything you type on the keyboard) or is simply unsafe. Stick to your own devices as much as possible.
Cyber Security Tip #13: Trace your digital steps
Do an inventory of your digital footprint. Step 1: Make a list of online accounts. Step 2: Set strong passwords for them. All of them. Step 3: Delete the accounts you haven’t used in the past 6 months. Decluttering feels goooood!
Cyber Security Tip #14: Why paranoia can be good
It’s okay to be (a little) paranoid. Being aware of what’s going on, online and offline, can help you keep safe from compromise. Simple rules to live by online: If it sounds/looks too good to be true, it’s probably not true. If it looks fishy, better stay away. If someone asks for your confidential data, don’t give it to them. In small doses, paranoia is a good thing.
Cyber Security Tip #15: Ulterior motives
Linkedin recruiter or attacker in disguise? Cyber criminals often create fake Linkedin profiles to gain access to details about you that they can use later. They collect data about your studies, names of employers and connections, etc. Check out their profiles before accepting their connection request. Warning signs to look for:
- too little, generic info
- picture that looks like stock photography
- Very few connections.
Cyber Security Tip #16: How to automate software updates for free
Did you know that updating your apps can prevent 85% or targeted attacks? (According to US-CERT.) Rule of thumb: keep your operating system and your applications up to date. All. The. Time. No exceptions! Don’t have time / don’t feel like dealing with constant updates for your apps? Get Heimdal FREE and let it do it for you. Update me, baby, one more time!
Cyber Security Tip #17: Beef up your passwords
One of the key pieces of advice that all cyber security specialists give is so simple it’ll blow your mind: Never, ever (ever, ever, ever!) reuse passwords! And don’t think that choosing “password123” and “passwords1234” means you’re doing it right. This is what a good password looks like (but don’t use this one): c.*%7(:wQ,28{T^7 Online password generator: https://identitysafe.norton.com/password-generator/ Check your passwords’ strength: https://howsecureismypassword.net/ Can’t remember them? (Of course you can’t. I can’t either.) Use a password manager.
Cyber Security Tip #18: Be wary of social engineering
Social engineering is quite big with cyber criminals. What it is: a type of psychological manipulation to get people to bypass normal security procedures or divulge confidential information. How it can happen:
- At home: someone pretending to be from your bank can call to ask you for your online banking password via a link provided by that person. Your password could be harvested and then used to empty your account.
- In the workplace: a contractor your company works with asks for private company information that grants access into your system.
In both cases, you answer should be a big, fat NO. Check with your boss and double check info directly with any company/institution before providing any confidential info.
Cyber Security Tip #19: Ransomware 101
Ransomware is one of the biggest cyber threats out there. What it does is it encrypts ALL your data and locks you out. It also asks for a ransom, typically between $200 and $500, to give you de decryption key. To protect yourself against ransomware, do this:
- Do frequent data backups (in multiple locations)
- Don’t keep vital information only on your computer
- Never access .zip attachments in e-mails from unknown senders
- Don’t click links in e-mails from unknown senders
- Keep your OS and apps up to date at all times
- Use a reliable antivirus
- Add another layer of security with a product that protects you from attacks that antivirus can’t block (Heimdal™ Threat Prevention Home is an option).
Wanna know more? Check out this anti-ransomware protection guide.
Cyber Security Tip #20: Too good to be hacked
A lot of people think: “I don’t need security programs because I don’t access unsafe locations.” First of all, even legit websites can be compromised. Second of all, there are plenty of attacks that happen without user action (aka clicking on something, downloading data, etc.) – they’re called drive-by attacks. Third, even if you were a cyber security expert, there are still plenty of vulnerabilities that attackers can exploit to get to you. To be safe online is quite similar to driving your car. You may have common sense and pay attention to potential dangers, but can you always predict what others are doing around you, in traffic? Don’t think you’re too good to be hacked. You’re not. No one is. (Sorry to burst your bubble there.) 
Cyber Security Tip #21: Gone phishing
Cyber criminals are very creative about their malicious methods. Take phishing for example. It’s an attempt to gather sensitive information (usernames, passwords, card details, etc.) by impersonating a trustworthy entity. Attackers can pose as your bank, you Internet provider, your insurance company, etc. Basic online security settings can help you keep safe:
- Regular OS and apps updates
- Strong passwords
- Reviewing bank statements on a regular schedule
- Checking senders’ email addresses
- Double checking the info in the potential phishing email with the issuing entity.
Looking for more detailed advice? Review the ABCs of Detecting and Preventing Phishing.
Cyber Security Tip #22: Do you https?
How can you tell if a website can securely handle your data? Check if it starts with https. The added “s” is key here. A website starting with https encrypts the data you put in the website and the data you get from it, so that no one can eavesdrop or tamper with the data flow. If a website doesn’t start with https, don’t give them confidential info (card details, social security number, address, etc.).
Cyber Security Tip #23: No PUPs allowed
Hang on, I’m not puppy haters. PUA / PUP (potentially unwanted application / potentially unwanted program) is a software that you may not have installed willingly, as sometimes it comes bundled with free apps. (Nothing is ever free – keep that in mind.) Although it doesn’t cost anything to use it, a PUA / PUP may display pop-ups (uhg!) or even install a toolbar in your browser of choice. It can even go so far as to replace your default search engine. This type of software can become malicious over time, if cyber criminals get a hold of it. So the fix is to uninstall it. And next time you install an app, go to advanced settings and make sure nothing else is installed without your consent.
Cyber Security Tip #24: Oversharing and identity theft
I bet you love sharing stuff on social media. Who doesn’t? You may even have a blog. But oversharing can influence your online security aka make you a target for cyber criminals. When it’s SO easy to gather info about you, why wouldn’t they? Data like phone numbers, names of relatives, your pet’s name, credit card info and more can be collected and put together to:
- Attack your accounts
- Compromise your accounts
- Empty your credit card
- Send spam and malware from your computer or email address.
If you’re looking to prevent identity theft, here’s your go-to guide: How to Prevent Identity Theft in 20 Essential Steps.
Cyber Security Tip #25: Give me email security!
Email – the place we call home when we go online. The contact we use for all our other accounts. The place we store everything from conversations with loved ones to documents and personal info. It’s invaluable! Can you imagine someone breaking into it? If you want air-tight security for your email account, check the following:
- Your recovery information
- Your recent activity
- Your account permissions
- Your app passwords
- Your 2-step verification settings.
More actionable tips included in the Complete Guide to Email Security.
Cyber Security Tip #26: Less spam, less problems
Is spam clogging your inbox? There are a couple of things you can do to weed most of it out and keep your inbox and devices safe:
- Be careful where you submit your email address
- Unsubscribe from any unnecessary newsletters
- Use filters and mark emails as spam to help your email provider block it more effectively
- NEVER click on links in spam emails
- NEVER download and open attachments in spam emails
- Disable the automatic downloading of HTML graphics in your mails
- Open an additional email account to keep your most important one safe
- When using social media, enhance your privacy settings so no one can see your email account
- If you have a website, protect your email address from automatically being scanned and harvested by spammers.
Spam campaigns are still one of the main attack vectors that cyber criminals use, so less spam means you’ll be a bit more secure. More on this: Analysis – How Malware Creators Use Spam to Maximize Their Impact.
Cyber Security Tip #27: 3 good security habits
Take up these 3 security habits to be safer online:
- Use antivirus on your computer and on your phone.
- Disconnect your computer from the Internet when you aren’t using it.
- Never, ever share your passwords.
Also, teach your family and friends what you know. They could find the advice useful.
Cyber Security Tip #28: Your phone is smart, but is it secure?
Many neglect smartphone security, but with so much sensitive data on it, you should everything you can to keep it safe. Here a few basic and vital steps to take:
- Turn on your screen lock and use it at all times.
- Use encryption to protect confidential information stored on your phone.
- Turn your Wi-Fi and Bluetooth off when you don’t use them.
- Install an antivirus for smartphones (if your phone allows it – Android phones do).
- Check permissions before installing an app.
- Don’t install rogue apps.
- Back up your data.
Don’t do it like this guy:
Cyber Security Tip #29: Ramp up your privacy
Privacy = security But privacy can improve your security. Get it done: use a VPN (Virtual Private Network) to protect your online identity and activity. Useful if you have to use public Wi-Fi or want to be anonymous online. This will help provide an additional layer of data encryption that can keep your safe from MitM (Man in the Middle) attacks.
Cyber Security Tip #30: Bad, bad ads
Did you know that attackers can inject malicious code or malware-filled ads into legit online advertising networks and websites? This tactic is called malvertising and it can get your computer infected with all sorts of malware, Trojans, and so on. How it happens: you browse your favorite website at FavoriteWebsite.com and there are many ads on it. But one is infected. The malicious code in the ad will search for vulnerabilities in your system. If it finds one (and it’s not difficult to do so), it’ll infect your computer with malware. What to do?
- Use an adblocker.
- Use a reliable antivirus.
- Use protection against attacks that antivirus can’t block.
Cyber Security Tip #31: How to check for fake social media profiles
Here’s a simple way to check if a social profile is fake or not. Step 1: Download the profile picture. Step 2: Use https://www.tineye.com/ or Google image search to see if that profile pic is a stock photo or if someone else has used it. If it’s fake, lots of results will pop up. 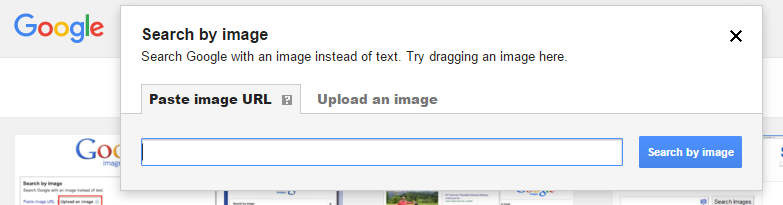 Step 3:
Step 3: 
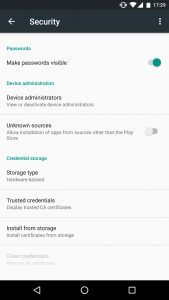
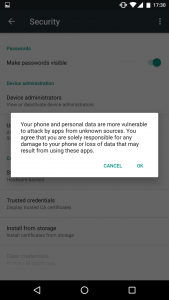
Cyber Security Tip #32: How to weed out untrusted sources
There’s an app for that. But where does it comes from? Never, EVER install apps, on your computer, phone or tablet from untrusted sources. If a website looks like this, navigate away immediately: 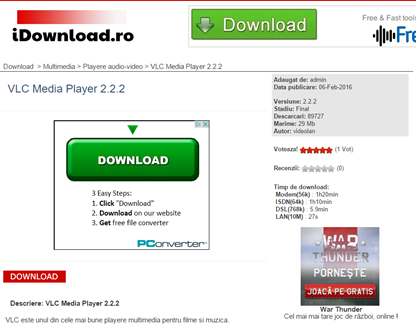 Make sure you have this turned on your Android phone or tablet:
Make sure you have this turned on your Android phone or tablet:
And never tap “Install” on apps like these on your iPhone/iPad:  Rule of thumb: always use official websites and official app stores to download and install apps. Fake apps can pack malware, adware and other types of infections you do not want on your PC/tablet/phone.
Rule of thumb: always use official websites and official app stores to download and install apps. Fake apps can pack malware, adware and other types of infections you do not want on your PC/tablet/phone.
Cyber Security Tip #33: Why social check-ins are not harmless
That’s not the question. Because the answer is a big, fat NO. Don’t check in at the airport when you’re leaving for a vacation. Don’t check in on Instagram when you take those holiday pics. The more data there is about you online, the more cyber criminals can gather and use to compromise you. And even common criminals can use this information to break into your house while you’re away. And, whatever you do, do not check in while you’re at home! Why would you want strangers to know your exact location?
Cyber Security Tip #34: Make your browsing more secure in 1 minute
Install HTTPS Everywhere for: Chrome Firefox Android Opera This free extension will encrypt your communication with many major websites, thus increasing your browsing security. The data you send and receive from the websites will be encrypted, so cyber criminals won’t be able to snoop on the information transfer and steal your data (credit card information, email address, passwords, etc.). More details here: https://www.eff.org/Https-everywhere
Cyber Security Tip #35: Stay away from bad neighborhoods
Nobody will brag about the fact that they navigate in shady online places. But we all know that’s not true, because it starts with P2P sharing websites and ends who knows where. Yes, I know you can’t wait to see that new show or movie, but P2P sharing websites are still dangerous. See those pics of strangely intriguing topics? Cyber criminals can infect those banners with malware, even if the rest of the website is clean. And you don’t even have to click to get infected. The whole thing is called fileless malware, you should read about it. 
Cyber Security Tip #36: The extent of your security
It’s time for an extension check! Cyber criminals target outdated plugins or browser extensions in most of their cyber attacks. That’s because we, as users, often leave them out of date or simply forget about them. Go to the browsers you use and uninstall/delete old browser plugins and extensions, and make sure the ones you use are up to date. Put out the fire before it starts. 😉 PS: If you want to go all the way, follow these recommendations.
Cyber Security Tip #37: Cyber crime as a business
You’ve probably never thought of this, but cyber criminals do run their operations like a business. They:
- Search for new ways to monetize their attacks (sell data on the Dark Web, purchase new types of ransomware that is impossible to break, etc.);
- Monitor their income and use all kinds of tactics to expand their reach, harvest more data and launch stronger and more lucrative attacks;
- Hire blackhat hackers to do it (they’re the bad kind, because there are good hackers too – the whitehat kind);
- Invest in acquiring infrastructure they can use to launch attacks and keep them anonymous;
- Buy exploit kits and ready-made malware that can be deployed instantly.
Malware creators often sell their malicious code, which is often modular and comes with pre-coded targets ready to be infected. Consequently, the malware economy is kept alive through this way of doing “business”. But it’s also constantly fed by the vulnerable systems that exist (because people and companies don’t keep their software updated and don’t implement enough protection for their data). Now you know.
Cyber Security Tip #38: What a phishing email looks like
Ever wondered what a phishing email looks like? Maybe you’ve already seen one, but didn’t know it was a malicious attempt to collect your personal data.
So here are the elements you should watch out for:
- Serious websites will never display your email address in the subject line
- Check out the sender’s email to verify the validity of the email
- Don’t be scared or pressured into clicking on anything, even though the email may seem urgent (the more urgent the email, the higher the chances of infection).
This is quite a poorly designed phishing attempt, but there are others which really look like the real deal. But don’t be fooled and always check links before you click (how to do it – in the next security tip!).
Cyber Security Tip #39: Check it before you click it
Check if a link is safe before you click it: https://www.virustotal.com/ http://global.sitesafety.trendmicro.com/ http://zulu.zscaler.com/ If you use a reliable antivirus solution, this may also help you detect if a website is dangerous to your security and/or privacy. It may do so by displaying a green icon next to Google search results or by blocking pages if they’re unsafe. Potentially harmful links may come to you via:
- Facebook, Twitter and other social networking links
- Instant messaging apps
- Spam (which is also email, I know), etc.
More about this: How Traffic Filtering Can Secure your PC from Cyber Threats.
Cyber Security Tip #40: There’s a scam for that
On the Internet, if it’s free or sounds too good to be true, you should be highly suspicious. The web is plagued by thousands of scams, some simple, some very elaborate, but all aimed at one thing: getting your money. And the astonishing fact is that the same, notorious scams still work. Here’s a quick example:  Source. http://www.hoteliermiddleeast.com/16297-thousands-duped-in-social-media-airline-scam/ What to do? Learn about them and stay away from them. Start here: Social Scams – The Full Breakdown and Protection Plan.
Source. http://www.hoteliermiddleeast.com/16297-thousands-duped-in-social-media-airline-scam/ What to do? Learn about them and stay away from them. Start here: Social Scams – The Full Breakdown and Protection Plan.
Cyber Security Tip #41: No Admin rights for routine stuff
Don’t count on your good karma. Don’t pray to God (no matter if your God is Steve Jobs or Bill Gates). It’s not a matter of it, but when you’ll become a victim to a cyber attack. But there’s no reason for you to take it personally and wonder why would anyone take interest in you – most of the attacks are automated. Malicious code will just scan for your system’s vulnerabilities, to see how it can be exploited. Chop off their odds to succeed: create a regular User, that doesn’t have Administrator rights, and use it when you run your operating system. When you run your PC as an administrator, it makes your system vulnerable to security risks. Log in as a User when you perform routine tasks, such as navigating the web and running programs. This will limit the cyber risks you expose your data to.
Cyber Security Tip #42: Why your data security should be like an onion
You can run, you can hide, but you’ll never be 100% protected against cyber attacks. Don’t fall for marketing tricks. No matter how much a security product will claim to make your system bulletproof, be warned: that there’s always a fine print written at the bottom. No system is impenetrable. Of course, this doesn’t mean you shouldn’t take all the necessary measures against cyber criminals. It’s just that you shouldn’t rely completely on them. Try a multi-layered security approach, onion-style. If one layer falls, you’ll always have another one set up in place, that will protect you.
Cyber Security Tip #43: Do a security risk assessment checklist
In “The Art of War”, Sun Tzu said that you should fully know your enemy and know yourself. Translating this into securities world plan of attack:
- Do an information assessment list. What type of data do you have stored on your devices? (It can be photos, work documents, but also passwords or account login credentials).
- What online accounts do you have? Which do you use more often?
- After you made the list, evaluate how valuable is the data that you keep on them. What would happen if you wouldn’t have access to them anymore or that information was lost, deleted or leaked online?
- How do you keep the most sensitive information safe? What security measures did you take in order to prevent something to happen to your data?
- What about shared files and devices? Who else has access to that data?
- What backup solutions do you have in place?
Do a security risk assessment checklist.
Cyber Security Tip #44: Common scams evolved into cyber scams
Benjamin Franklin used to say that in this world nothing is certain, except death and taxes. If he were alive today, he would most likely add social scams to the list. Three common tricks you may come across in the digital world: – Shocking news or fake celebrity news – Remember the saying “Curiosity killed the cat”? Cyber criminals will use anything that’s hot right then in the media, in order to capture your attention. – Free stuff. Free mobile phones, free trips, free flight tickets, free beauty products. Always works! – Urgency. Click here now, the discount is only available today, download this now or never, etc. Wanna know more about scams? Read this.
Cyber Security Tip #45: Check your email’s activity log
Do you have a Google account? Did you know that you can check a recent activity log for your account? It will show you from what browsers and devices you’ve accessed it, when and from what IP. If there’s something that you don’t recognize there or an old session from a friend’s computer, you can choose to terminate it. Same option is available for many other online accounts, such as Facebook, Yahoo or Dropbox. Access it to monitor where your accounts have been used and end any sessions that you don’t recognize. If you also activate two-factor authentication, your accounts will be more secure against intruders. [Tweet “I had no idea that there were SO many #cybersecurity tips I could apply for free!”]
Cyber Security Tip #46: Don’t wait for bad things to happen
Most people wait for something bad to happen before they take any security measures. They either don’t realize the threats they expose themselves to, or just consider protection to be too consuming of time, money and comfort. Unfortunately, nobody is and never will be safe online. Any of the online accounts that we use can be breached. What if that lesson is too expensive to learn the hard way? What would happen if you lost one of your accounts? Or the data you had on them? What if that data was sold? Or used to blackmail you? How much would that ruin your reputation? If it’s too late and you’ve already been hacked, here’s a plan with all the actions that you should take in order to control the damages.
Cyber Security Tip #47: No reckless clicking
You’ve probably heard about the study that shows how humans became so distracted because of computers and internet, that we are now competing with the attention span of a goldfish (and the goldfish will probably win in a year or two). I don’t know how researchers ended up with this conclusion or how they measured it (perhaps they made it watch 50 Shades of Grey?), but I do know that it only takes one misfortunate click to end up with a malware infection. Stuff not to click on:
- Any short links, that you have no idea where they lead
- Any emails or attachments that you never requested
- Any shady Facebook apps (especially those who claim to let you see who visited your profile).
Cyber Security Tip #48: Stop measuring yourself against others
Stop comparing yourself to those around you. So what if they don’t use two-factor authentication? So what if they don’t pay for a trustworthy antivirus? So what if they don’t update all their software or backup their data? You should know better. Don’t let them influence you or he measures you take in order to protect your data. Learn from the experts.
Cyber Security Tip #49: New scams era – bigger, better, bolder
Do you remember the scam with the Nigerian prince who claimed to be rich and endangered and asked for your money? Those scams never disappeared, they just evolved into bigger and more complex scams. They now take the form of contests on social networks, with airlines that offer free tickets or Apple giving away free iPhones. Or videos and eBooks that claim to help you get rich in no time. Three basic rules:
- If it’s too good to be true, it probably is.
- Nothing in this world is free.
- Always check from at least three trustworthy sources. “Trustworthy” = official website, official social channel (look for the blue check mark), legit media or by directly contacting the company.
Cyber Security Tip #50: Purge your mobile apps
Take a quick glance over your mobile apps, see what you have installed there.
- Remove any apps you haven’t been using – they are vulnerabilities for your security and privacy.
- Revoke permissions for apps that require access to sensitive information – why would a flashlight app request access to read your messages, for example?
- Keep your apps update – this lowers the chances for malware to take advantage of their vulnerabilities.
And remember to never install apps from anywhere else but the official app store. In Android, there’s a setting that also doesn’t allow apps from third parties to be installed. Here you can find more handy security tips for your smartphone.
Cyber Security Tip #51: Never trust anyone
Not your employees, not your buddies, not your brother or mother, nobody. You can never be too careful. You never know who’s standing right next to you. Even if you’d currently be willing to jump through fire for a person, you never know how your relationship is going to evolve in the long term.
Cyber Security Tip #52: Smartphone security ftw – Auto lock
Never leave your mobile phone unattended, without a security password in place. Activate your smartphone to auto lock the screen after a short period of inactivity, like 15 seconds. 4 digit PINs are the easiest to break, so you should skip using those and instead set a good password, similar to those you use for your online accounts. That means it’s long, random, with mixed lower and upper cases, digits and symbols. Or draw a pattern. Or, even better, activate fingerprint authentication, if that’s available on your device. It won’t be a secret, as we leave our fingerprints everywhere, but biometrics are the hardest to replicate. Here are more ways to protect your smartphone.
Cyber Security Tip #53: Nothing is bulletproof against cyber attacks
You shouldn’t rely exclusively on your antivirus for protection. No matter how good it is, it doesn’t protect you from all threats that are out there. It won’t protect you against a vengeful former employee or a disgruntled ex-boyfriend / ex-girlfriend.
Cyber Security Tip #54: Got tape? Stick it over your laptop’s webcam
Put tape over your laptop’s webcam. The FBI director does it. You should do it too, because you never know who’s watching you. A few examples from the past years that might give you the creeps:
- In 2009, a student sued his high school for taking photos of him through the laptop they provided him.
- Miss Teen USA was photographed without her knowledge by an ex high school colleague, who infected her PC with spyware. In that case, the victim fought back and the man was sent to jail.
Here are more paranoid measures (better paranoid and safe than sorry, right?)
Cyber Security Tip #55: No real time check-ins
Never check in when you are leaving the house for longer periods of time (such as holidays). That includes no posting of flight tickets and holiday pics – at least not while you’re still away from home. Something so common and apparently innocent can turn into a nightmare. There were plenty of cases of people who checked-in from their holidays, bragged about the wonderful places they’re visiting, only to come back home and find out that their house became the target of burglars. You never know who else can benefit from the information you are sharing. You can never fully control and restrict who’s watching your social networks posts.
Cyber Security Tip #56: Moms and Dads, no photos of your kids please
Dear parents, please don’t post photos of your children on your social accounts. First of all, think about when those kids will grow up and their whole lives will be available publicly, will be there to use against them, to shame them. This is most likely to happen among teenagers, a period when kids are extremely harsh with each other. Second, you never know where those pics will end up. There’ve been cases of private Facebook groups where people were sharing other people’s kid pics and making fun of them. Or, even worse: pedophiles. Imagine what could happen if a pedophile would put together all the information you are willingly sharing on your social network: the area where you live, your kid’s school, the park where your kid plays, etc. Here are more reasons.
Cyber Security Tip #57: Keep those browsers up to date
Browser are one of the most common security holes, if you don’t keep them up to date. And the same goes for the add-ons and plugins you installed. Cyber crooks frequently scan websites and PCs for vulnerabilities, such as outdated software. They use those backdoors to penetrate your systems and infect you with malware. Keep those browsers updated. If you have browsers plugins, go to their settings and choose either to “Ask to activate” or even to “Never activate”.
Cyber Security Tip #58: Remove past geotags from your social accounts
In one of the previous tips, I approached the dangers of real time check ins on social network. If it’s too late for that and you already have tons of check ins from your home, you also have the option to delete previous history location. In Facebook you’ll have to do that manually for all the photos you uploaded and turn off Location for future posts. In Instagram, you can Remove Geotag for all your uploaded pics.
Cyber Security Tip #59: Be careful with those mobile apps
Only download and install mobile apps that you can find in the official app stores. Make sure that the option to allow installation of third party apps is disabled. That means no apps from your online buddies, ads, blogs or torrents. Those usually carry malware that will harm your smartphone. However, this doesn’t mean that an app or game from the official store is 100% secure – sometimes, even popular apps, with more than 5 million downloads, can prove to be infected.
Cyber Security Tip #60: Create multiple email accounts
Create completely separate email accounts with different purposes.
- One email account to subscribe to newsletters and shopping deals
- Another one for online accounts, such as your Facebook or Uber
- Different email accounts for work and personal conversations
It might seem like a hassle, to create and manage all those accounts, but it’s worth it. And it will also help reduce the chances to receive spam on your important emails.
Cyber Security Tip #61: Ad blockers can reduce malware attacks
If you’ve never heard about ad blockers before, here’s the short version: they’re browser extensions / apps you install to block online ads. No pop-ups, overlay ads, search ads or even pre-roll ads in videos. While blocking annoying ads is the most boasted benefit of ad blockers, they have another advantage as well: they can help you eliminate the threat of malvertising. Marlvertising = (short for “malicious advertising”) it refers to how malware is distributed through online advertising networks. This type of technique is widely use to spread financial malware, data-stealing malware, ransomware and other cyber threats. Malvertising can happen even on legitimate websites, such as Forbes, as you’ll see from the examples below: You say advertising, I say block that malware How Forbes inadvertently proved the anti-malware value of ad blockers Another Reason to Use an Ad Blocker: Malvertising Has Tripled This Year Top tip: use an ad-blocker, stay malvertising-free!
Cyber Security Tip #62: Top 10 most vulnerable software in 2015
The numbers are in! Here are the most vulnerable software apps and operating systems in 2015, according to the number of vulnerabilities they had last year. 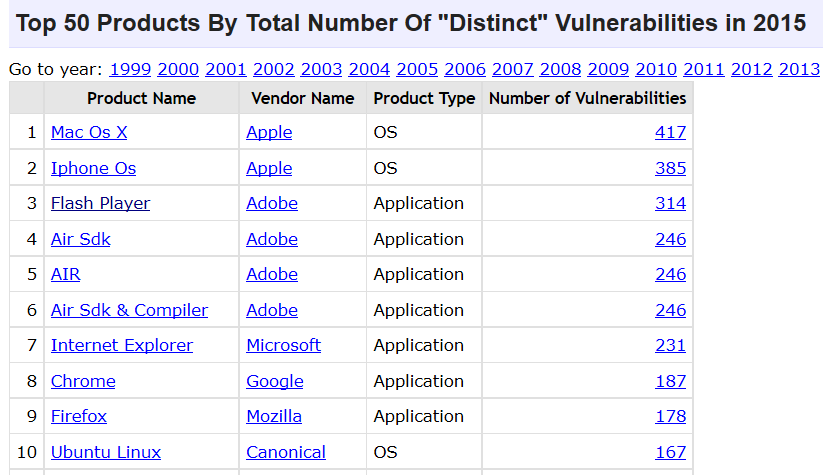 Source: CVE details. I bet you’re surprised to see that Apple operating systems have had the most vulnerabilities last year. Apple devices/operating systems being immune to cyber attacks is a common misconception (more on those myths a bit later). Also, if you still have installed Adobe Flash, it’s time to let it go. Last year, it was cyber criminals’ favorite software to exploit and infect PCs. The same goes for Internet Explorer. As for the rest, keep your apps updated and use multiple protection layers.
Source: CVE details. I bet you’re surprised to see that Apple operating systems have had the most vulnerabilities last year. Apple devices/operating systems being immune to cyber attacks is a common misconception (more on those myths a bit later). Also, if you still have installed Adobe Flash, it’s time to let it go. Last year, it was cyber criminals’ favorite software to exploit and infect PCs. The same goes for Internet Explorer. As for the rest, keep your apps updated and use multiple protection layers.
Cyber Security Tip #63: The difference between malware, viruses and ransomware explained
It’s easy to get caught up in cyber security lingo, so I wanted to explain 3 key terms you often hear, so you’ll always know what they mean. Here goes: Virus = a type of malicious software capable of self-replication. A virus needs human intervention to be ran and it can copy itself into other computer programs, data files, or in certain sections of your computer, such as the boot sector of the hard drive. Once this happens, these will elements will become infected. Computer viruses are designed to harm computers and information systems and can spread through the Internet, through malicious downloads, infected email attachments, malicious programs, files or documents. Viruses can steal data, destroy information, log keystrokes and more. Malware = (short for “malicious software”) is an umbrella term that refers to software that is defined by malicious intent. This type of ill-intentioned software can disrupt normal computer operations, harvest confidential information, obtain unauthorized access to computer systems, display unwanted advertising and more. Ransomware = a type of malware which encrypts all the data on a PC or mobile device, blocking the data owner’s access to it. After the infection happens, the victim receives a message that tells him/her that a certain amount of money must be paid (usually in Bitcoins) in order to get the decryption key. Usually, there is also a time-limit for the ransom to be paid. There is no guarantee that the, if the victim pays the ransom, he/she will get the decryption key. The most reliable solution is to back up your data in at least 3 different places (for redundancy) and keep those backups up to date, so you don’t lose important progress. I know it’s not the shortest tip, but I hope you find it useful. 
Cyber Security Tip #64: The best way to back up your photos
I’m a simple person: I know that I take too many pictures and there’s no way I can find the time to select some of them and get them printed, so I like to take good care of my memories. This is how I keep my photos safe:
- I automatically back them up in Google Photos for free. Google offers unlimited storage for high quality photos, for phones or point-and-shoot cameras that are 16 megapixels (MP) or less. I do this daily, while my phone is charging and it’s connected to my home Wi-fi.
- I also keep a copy of my photos on two external drives, to ensure that, if one backup fails, there’s another and then another one that I can multiply. I do this once a week or once every two weeks, to make sure I don’t lose any pics of my cat I may have taken.
- Before backing up my photos on the external drive, I encrypt them, so no one can access my photos if I should lose or have my external drive stolen.
The whole thing takes just a few minutes, especially because I have this routine in place. And yes, sometimes we sit around the table and look back at older pictures, especially during holidays such as Easter or Christmas. So I hope you’ll consider keeping your pics safe as well.
Cyber Security Tip #65: Cyber security myth busters (1/many)
Time to break down some common misconceptions about cyber security that you or someone you know may still believe in. Why? Because knowledge is power. Myth: I don’t need security programs because I don’t access unsafe locations. Truth: Common sense is necessary online, but it’s certainly not enough to protect you from cyber threats. Even security specialists admit that some threats are so cunning that even they have a difficult time pointing them out. Plus, as you know, cyber attacks can be delivered even from trustworthy websites, which have been infected unwillingly. To be safe online is quite similar to driving your car: you may have common sense and pay attention to potential dangers, but can you always predict what others are doing around you in traffic? Now, you understand why security is important. To be continued…
Cyber Security Tip #66: Cyber security myth busters (2/many)
Here’s another myth that‘s pure bogus: Myth: My social networks are safe places. Friends will be friends. Truth: The more information you share, the more appealing you are to cyber criminals. Consequently, social media is the perfect context for cyber criminals to do what they do best: impersonate, manipulate, steal data and/or money and compromise your account. And the infections they launch often spread like wildfire. Even if you are cyber security savvy, that doesn’t mean your Facebook friends are too. Plus, social media threats are getting more varied and sophisticated (Top 9 social media threats of 2015).
Cyber Security Tip #67: The problem with unsupported software
In your journeys across the web, you may come across the following news title: “Company XYZ has discontinued support for the ZXY software application.” Ending support for a software means that the software had reached end-of-life, and that the software maker stops sustaining it through sales, marketing and especially through support. Ending support for a software means that the software maker will no longer create and implement security, performance or feature updates to that application. For example, Microsoft ended support for Windows XP in July 2014 and Apple discontinued support for QuickTime for Windows in April 2016. As a consequence, those who continue to use unsupported software expose their system to a huge range of vulnerabilities. Given that the software maker no longer provides security updates, these vulnerabilities will be left unpatched and cyber criminals will be able to exploit them as long as they want to. The moral of the story is to never use unsupported software and keep all your apps up to date.
Cyber Security Tip #68: Beware of fake antivirus
This is one of the oldest tricks in the cyber criminals’ book. We all saw this message at least once on our screens: “You have been infected! Download antivirus X right now to protect your computer!” 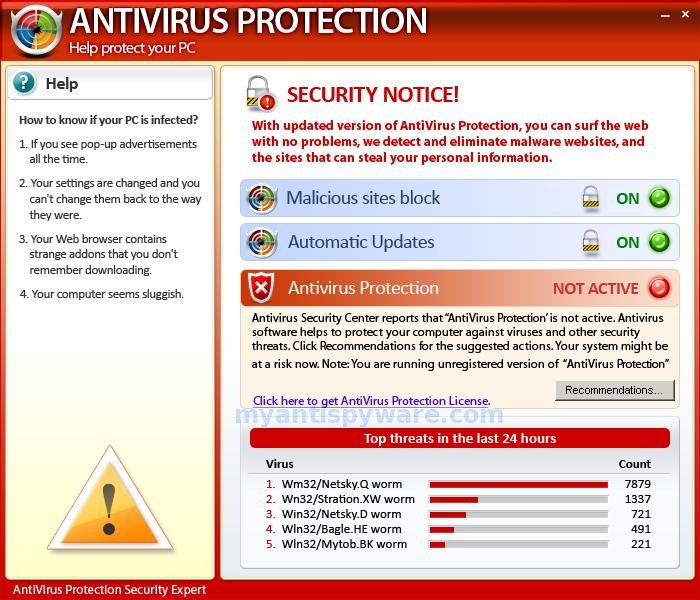 You should know that a legitimate antivirus company will never advertise its products like that. These fake antivirus scams are so well created that they could fool even the most cyber security savvy user. What fake antivirus can do to your system:
You should know that a legitimate antivirus company will never advertise its products like that. These fake antivirus scams are so well created that they could fool even the most cyber security savvy user. What fake antivirus can do to your system:
- It can infect your PC with adware
- It can trick you into installing something that look like an antivirus and that really is malware (which can be anything from financial malware to a keylogger to ransomware).
And this scam is gaining popularity on mobile devices too, for example on Android. Key take-away: only download and install antivirus products from trusted sources.
Cyber Security Tip #69: Not all hackers are bad (they come in 3 shades)
We rarely hear the term “hacker” in a positive context and I decided to try and clear things a bit. The definition says that a hacker is someone who’s proficient at computers and computer networks. Shortly, hackers come in three shades:
- Whitehat hackers – who are cyber security experts and use their knowledge and skills for good, helping protect companies and individuals;
- Greyhat hackers – are right in between, as they use methods which are not entirely ethical, but not necessarily illegal to acquire information which they then sell to third parties;
- Blackhat hacker – who are cyber criminals and choose to put their know-how and resources to work for malicious purposes.
An article in Wired explains the difference between these categories quite well. So the next time you want to say hacker and mean cyber criminal, make sure to use the latter term.
Cyber Security Tip #70: Should you pay in case of a ransomware attack?
This question may have crossed your mind. If it hasn’t, you should consider it. Simply put, there are two scenarios: A. If you have a back-up of your data, then the answer is NO, you shouldn’t pay. Even if you do get infected with ransomware, you can always wipe your system, do a clean install of your OS, restore your backup and carry on. It’s not simple, not pleasant, you may lose a bit of data on the way, but not so much that is justifies doing “business” with cyber criminals. B. If you don’t have a backup of your data, the answer is still NO. Even the FBI advises the same. There are several reasons for this:
- Cyber attackers are not exactly trustworthy individuals, so there’s no guarantee that you’ll get your decryption key and your data back;
- By paying the ransom, you’re fueling the malware economy, which is already thriving and affecting all of us through the damages it creates;
- Every paid ransom is feeding another similar attack on other people, and the next victim could be someone your love.
Your data is important, and, trust me, I get it. But, in situations like these, you should also consider the bigger picture. Every action determines a reaction somewhere and this law is true for cyber security as well. Do the right thing, back up your data often.
Cyber Security Tip #71: Activate remote device locator for your smartphone
In case that your smartphone is ever lost or stolen, the easiest way to remotely locate it is by installing a dedicated app. For Apple there’s the tracking solution called “Find my iPhone”, Microsoft has “Find my phone”, and Android has “Android Device Manager”. Make sure that the option to track its location is always turned on. 
Cyber Security Tip #72: Cyber security myth busters (3/many)
The series continues! Myth: I only open e-mails from people I know, so I should be fine. Truth: Phishing and spam emails / SMS often use forged sender addresses (example), numbers (spoofing) and contact details to look legitimate and trick the victim into opening them. And spam is still one of the most used distribution tactics for spreading malware. How many of us already received a strange email from a friend or from a relative? One click on an infected link or one download of a malicious file and cyber criminals have a way in. It’s all they need. And they attackers won’t shy away from using trusted companies and all sorts of mind gamed to lure victims. If you have doubts about the origin of an email, simply contact the organization or your friend directly and ask if they sent that particular email.
Cyber Security Tip #73: Remember to do a Factory Data Reset
Planning or selling your phone? Make sure you don’t forget to have a Factory Data Reset before you give it away. It will wipe all the data that was stored on it, including access to your personal accounts, system and apps data and settings, photos, videos, music or any other data. Back up your information first, then wipe it clean, so the next phone owner can’t log into your accounts or use your private pictures, contacts and other confidential info. How to do it:
Cyber Security Tip #74: Think like a journalist
The best way to go about any information you find online is to think like a journalist. This is not just for your cyber protection, but for it’ll also help you maintain a rational perspective and tell apart the good from the bad data.
- Don’t trust unsupported claims.
- Verify the information from at least 3 credible sources.
- Maintain a critical attitude towards the information you receive.
- Question the claims you find difficult to believe (and even those easy to believe).
If you’re interested in more netiquette advice, read this.
Cyber Security Tip #75: A ransomware infection chain – visualized
Cyber attacks are very difficult to imagine, because the concepts involved are quite abstract. I know. That’s why I created this graphic that shows the simple version of a ransomware attack. 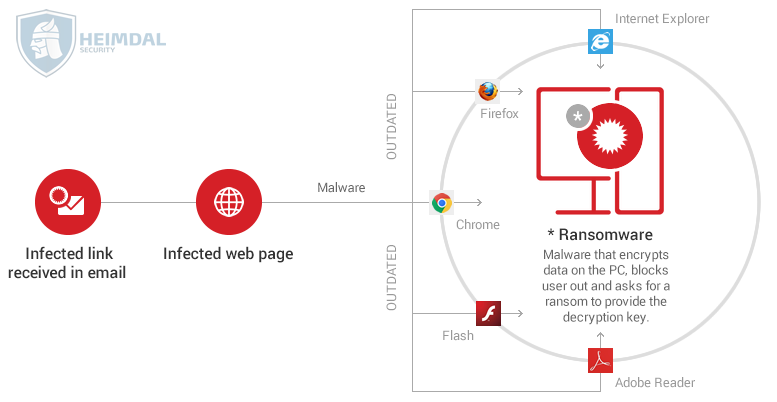 Wanna get into the details? Here’s the long(er) version.
Wanna get into the details? Here’s the long(er) version.
Cyber Security Tip #76: Cyber security myth busters (4/many)
Do you believe in this too? Myth: I download and access information from trusted sources. This keeps me safe. Truth: Current cyber threats are able to infiltrate even the most secure websites and software, so don’t think that you’re protected if you only access the online locations you know are safe. You’ve seen what malvertising can do (security tip #61) and there are worse threats out there. And not even antivirus is enough, which is why I always insist on multiple layers of protection.
Cyber Security Tip #77: Make WhatsApp more secure
Navigate to Settings (bottom right corner in your app) – Tap on Account
Tap on Security next and enable Show Security Notifications: 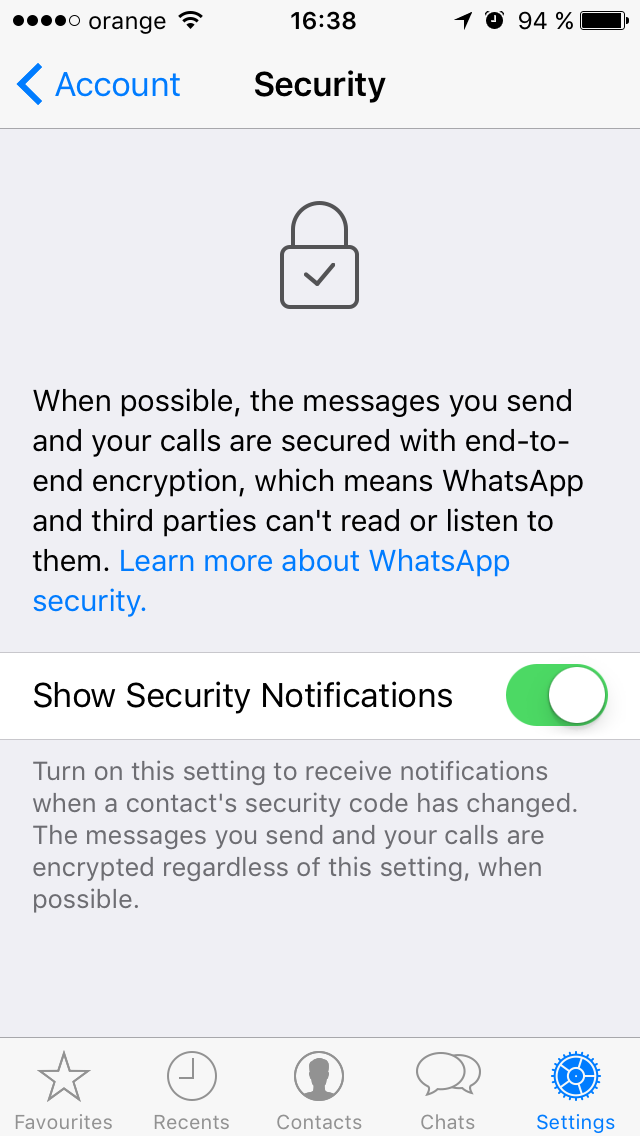 Here’s what this option does, in WhatApps’ words.
Here’s what this option does, in WhatApps’ words.
Each of your chats has its own security code used to verify that your calls and the messages you send to that chat are end-to-end encrypted. This code can be found in the contact info/group info screen, both as a QR code and a 60-digit number. These codes are unique to each chat and can be compared between people in each chat to verify that the messages you send to the chat are end-to-end encrypted. Security codes are just visible versions of the special key shared between you – and don’t worry, it’s not the actual key itself, that’s always kept secret. At times, the security codes used in end-to-end encryption may change. This is likely because someone reinstalled WhatsApp or switched phones. Important: You and your contacts must be using the latest available version of WhatsApp for end-to-end encryption to be activated.
More on WhatsApp security, here.
Cyber Security Tip #78: Do a Facebook security check
Hav e you ever done a Facebook security check? It’s a simple and useful tool offered by Facebook. It’ll help you:
- Log out of unused apps (which can compromise your data)
- Get login alerts (so no one else gets into your account)
- Protect your password (by making it stronger).
Here’s how the homescreen looks like:  It only takes a couple of minutes and it can really help safeguard your Facebook accounts, which probably has a lot of data you want to keep private. Start here: https://www.facebook.com/help/799880743466869
It only takes a couple of minutes and it can really help safeguard your Facebook accounts, which probably has a lot of data you want to keep private. Start here: https://www.facebook.com/help/799880743466869
Cyber Security Tip #79: Remove past geotags for your Instagrams
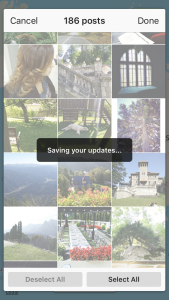
If you have some regret over tagging your Instagram photos with the location they were taken in, there’s a way to reverse it. 1. Go to your app. Tap the location icon.  2. Tap the icon highlighted below to select all the photos with geotags. Then click on Edit (top right corner).
2. Tap the icon highlighted below to select all the photos with geotags. Then click on Edit (top right corner).
3. Tap on Deselect all. 4. Confirm that you want to remove the geotags. This will remove any location information about your past Instagram posts. The photos will be just fine, don’t worry about that.
5. Check the map to see it clean – no geo-tagged photos there!  Rest assured that your privacy is not a bit stronger.
Rest assured that your privacy is not a bit stronger.
Cyber Security Tip #80: Cyber security myth busters (5/many)
Time to crack one more! Myth: I don’t have important information or sensitive data on my system. Why should I worry? Truth: First of all, are you sure there is nothing valuable on your system? Have you not saved any passwords in your browser? Do you have no browser history? Do you never send emails with documents and other information in them? You may think that your data is not important for cyber criminals, but you should know they can collect and assemble information about you from other sources as well. Sources like your public information from your social media profile, stuff you’ve posted on forums, your email address, etc. This gives them a big picture of your online habits. Later on, they can use the information to steal your online identity and/or use it against you. And even when there is no important data for a potential criminal on your system, they still infect your PC, tie it into a botnet and use its resources for other attacks.
Cyber Security Tip #81: Will an antivirus make me untouchable?
“But I installed an antivirus that has good reviews. That means I’m bulletproof and hackers can’t touch me, right?” Wrooong. Antivirus alone won’t keep you protected from all dangers that are out there, in the big dark web.
- It won’t detect the latest generation of financial malware, which has more sophisticated techniques.
- It won’t help you if you decide to ignore its recommendations and open that attachment or visit that suspicious link.
- It won’t protect you if you don’t keep its signature database up to date.
- And it surely won’t help you in a phishing attack.
Of course, I’m not saying that antivirus software is obsolete. It’s just not enough. It remains an essential piece in the puzzle of cyber security, so make sure you choose a reliable one. Here’s how.
Cyber Security Tip #82: There’s no harm in digging through spam, right?
“But I was expecting a document / some photos from a friend. What if that email from spam is actually a legit one and ended up there by mistake?” This is how most stories about ransomware infections begin. Here are a few hints that will help you tell that something’s fishy:
- First sign: if the email ended up in Spam, clearly something is wrong with it. Trust the spam filter. Let it stay there.
- Ok, you’re stubborn. Next step: have a look at the header. Does the email address match your friend’s one? No? Then it’s not legit. End of story. Also make sure you check for small variations in name – it can be different letters, misspellings, or a different web domain.
- Since I’m talking about the email header, if you are using Gmail you could also check if the email is encrypted – that’s a good sign.
- Moving on. You notice there’s an attachment. Before you rush to download and open it, look at its extension. What type of file is it? No photo archive will ever be an .exe. Be aware of Office files as well, as they can contain malicious code. Make sure you disable the Macros function in Microsoft Office before opening any Documents or Excels.
If it helps you to calm down, just pick up the phone and call your friend. Ask them if they sent you an email and from what address. Better be safe than sorry, right?
Cyber Security Tip #83: Cut off Microsoft Office macros
If you count on Microsoft Office to help you with your work, you should disable the Macros. What are Macros? Macros are bits of code embedded in Microsoft Office documents. They are potentially dangerous and make you vulnerable to malware infections. Keep them deactivated. Only turn them on for specific files, when there’s a document from a trustworthy source / person. Here’s how.
Cyber Security Tip #84: Keeping your Instagram account under control by making it private
Want to keep your Instagram account as secure as possible? If you are not a public person or don’t have any interest in improving your online branding, your answer is most likely YES. And you can start by making your profile private. If you only want to share your photos with the users you choose, like your close friends and family, you should follow these steps:
- Go to your Instagram profile.
- Click on the three dots in the upper right corner.
- At the bottom you’ll see the Private Account option. Turn it ON – the button should turn to Blue.
Making your account private means that you control who sees the photos and videos that you post. Every time a user will want to follow you, they’ll first have to get your approval. You should also note that this will only work for users who want to follow you in the future. Your current followers will still be able to see your profile. If you want to remove some of them, you’ll have to manually go to their profile and Block them. Here are more tips on securing your Instagram account.
Cyber Security Tip #85: How to find out if your account was ever breached
In the ocean of information that is out there, it seems like every day there’s a new data breach. Wondering if your account was ever among the hacked ones? Here are two projects that will help you tell:
- Breach Alarm – it stores a huge database of leaked, stolen or compromised passwords. Confront with yours and see if someone ever used one that’s the same with yours. If you find a match, change it asap.
- have I been pwned? – this one’s a database of past breaches. You can check if any of your accounts were compromised before.
May the odds be ever in your favor! [Tweet “This huge collection of #cybersecurity tips will change your world:”]
Cyber Security Tip #86: Keep your guard up against third-party apps
Most likely, you logged in with your social accounts to plenty of third party apps – from games to other social networks, streaming services and so on. If you’re worried about your privacy and security, pay attention to what apps you allow to connect to your accounts. They have access to your profiles and personal information, so you should only approve trustworthy ones. From time to time, do a clean-up: check every single app that you allowed access to your account. Remove the ones that you don’t use anymore (or worse, don’t even recognize).
- Revoke access on Facebook to third party apps
- Revoke access on Twitter to third party apps.
- Revoke access on Linkedin to third party apps
- Revoke access on Instagram to third party apps
Cyber Security Tip #87: Cleaning up your mobile apps
And since I brought up the subject of apps, you should also take a short break and do a cleanup on your smartphone. Take a look over the list of installed apps. Are there any apps that you don’t use anymore or you don’t even recognize? Uninstall them, as they are potential security risks. If you are using Android, you can also check what permissions you gave them access to (here’s how to do that). If anything looks out of order, deny them access to what they’re requesting.
Cyber Security Tip #88: Beware of USBs and external hard-drives
Never insert foreign USBs or external hard-drives in your PC or laptop. Even though they seem innocent, because of their common nature, they could still be infected with malware, viruses, Trojans or keyloggers. However, if you absolutely must plug-in an external drive into your device, the next secure alternative is to disable the Auto-Run option. Afterwards, use an antivirus software to scan it.
Cyber Security Tip #89: Security check-up on your Google account
Did you activate all the security options available for your Google account? If you’re not sure, the company offers you the possibility to do a security check-up. It will guide you through all the steps that you need to check or activate in order to enhance your account’s protection. Take a short break and follow all their security and privacy steps: Google security checkup. 
Cyber Security Tip #90: Don’t be lazy, stop saving your card details
Stop saving your card details on your online accounts. Don’t save them for your cloud provider, don’t save them for your favorite ecommerce retailer, don’t save them anywhere. Nada. Zip. Zero. No cards saved on any account, no matter how small or insignificant or secure you might consider it. If you want to buy something online, take your time and fill in the credit card details every single time. Yes, it’s a pain in the… fingertips. But it’s worth it to lose 30 seconds and do this manually each time you want to buy something. The lazy alternative also comes with a high risk of card fraud. You can never know who manages to breach your account (no matter who’s at fault for it) and end up using your card.
Cyber Security Tip #91: Beware of adware
Adware is a type of software that delivers ads on your system. Usually, these pop-up ads appear like annoying pop-up ads or banners while visiting websites. And they can also slow down your computer. Adware comes in “bundle” versions with other applications. Most types of adware are not dangerous, maybe a bit annoying since they deliver pop-up ads while visiting a website. But there is another dangerous form of adware that delivers spyware, which can track down your activity and retrieve sensitive information. How to protect against it: don’t download software from unsafe websites and pay attention to software that comes bundled. If you’re already infected, this clean-up guide can come in handy.
Cyber Security Tip #92: How exploit kits work (graphic)
You may have heard the term before, as more and more cyber criminals use these tools in their attacks. Exploit kits (EKs) are computer programs designed to find flaws, weaknesses or mistakes in software apps (commonly known as vulnerabilities). Online criminals use them to gain access into a system or a network. Exploit kits are extremely versatile and easy to use, which is why attackers of all ranges have access to them. EKs can download malicious files and feed the attacked system with malicious code after infiltrating it. Shortly, here is how they work: 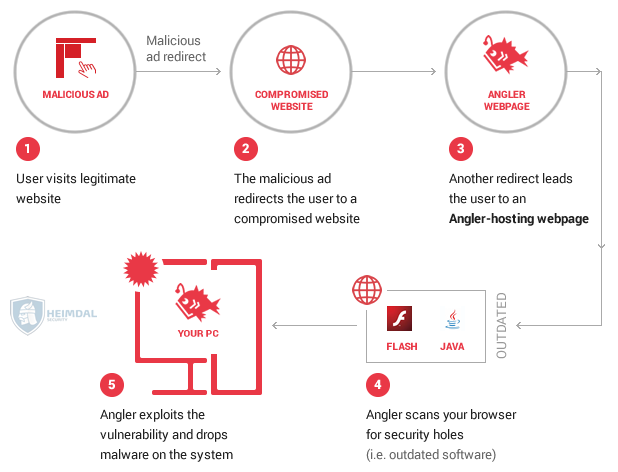 If you want to develop and perfect your protection against this kind of exploit kits, read this article.
If you want to develop and perfect your protection against this kind of exploit kits, read this article.
Cyber Security Tip #93: Types of malware you can find in the wild (wild Internet)
You probably wondered at least once how many types of malware (malicious software) are there and how they differ from one another. Here’s a super quick overview: Adware – delivers bad ads and can infect your computer with additional malware. Bots – malicious code engineered to perform specific tasks. They can be both harmless and malicious. More on bad bots in tip #97. Bug – cyber security bugs (flaw in software) open up security holes in computer systems that cyber criminals can take advantage of. In this context, bugs can allow attackers to gain access to a system and do irreparable damage. Ransomware – a type of malware that encrypts the victim’s data and demands a ransom in order to provide the decryption key. More info on how to protect yourself against it here. Rootkit – a type of malicious software (but not always) which gives the attackers privileged access to a computer. A rootkit is activated before the operating system boots up, so antivirus can’t detect it. Spyware – a type of malware that will spy on your activity (browsing habits, keystrokes, financial data, etc.) and send the information to servers controlled by cyber criminals. Trojan Horse – malware that’s able to disguise itself as a normal file, to trick victims into downloading and installing more malware on their devices. Virus – a form of malware that can copy itself so it can spread to other computers. Viruses attach themselves to other computer programs and execute malicious commands when the victim uses those compromised programs. Thus, viruses rely on the victim’s activity to spread. Worm – a type of malware that exploits security holes in operating systems. Worms use the infected system’s resources and self-replicate. They spread independently, without requiring the victim to do anything. Here’s a more in-depth read about the main types of malware.
Cyber Security Tip #94: Your one-page anti-ransomware checklist
Worried about the dangers of ransomware? I put together a one-page anti-ransomware checklist so you can make sure you have all the right safeguards in place. Download it, use it and share it with whoever you think needs it.
Cyber Security Tip #95: The 3 fundamental infosec principles
Although a general term, information security (or infosec) is a practice with a very clear goal: to protect information from:
- unauthorized access
- unauthorized use
- unauthorized disclosure
- disruption
- unauthorized modification
- unauthorized perusal
- unauthorized inspection
- unauthorized recording
- destruction.
The CIA triad of confidentiality, integrity, and availability is fundamental information security. What this means: Confidentiality – information should not be made available or disclosed to unauthorized individuals, entities, or processes. Integrity – information should not be modified in an unauthorized or undetected manner. The data should remain accurate and complete from sender to receiver. Availability – information should be readily available when needed. In order for all these principles to be respected, so you can use and enjoy your data at all times, proper safeguards must be implemented. 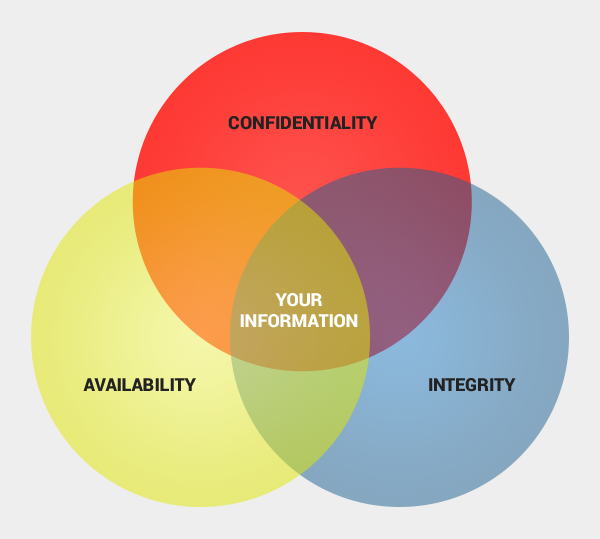
Cyber Security Tip #96: Cyber security myth busters (6/many)
Myth: In case I get infected, I will definitely notice it. Truth: Well, don’t be so sure about this. In the past, when a computer started running slow and pop-ups appeared all over the screen, maybe you could tell. But today, cyber criminal methods have evolved and increased their efficiency. In most cases, a normal user can’t tell if their system is involved in spam campaigns or coordinated online attacks. Current malware is built to be undetectable and untraceable by antivirus products, retrieving private information without the victims noticing. Designed to evade normal detection systems and working in the background, the latest data-stealing malware harvests private data like credit card details and account logins without leaving visual evidence. But you’re already applying these tips, so you’re well on your way to better online security!
Cyber Security Tip #97: What a botnet actually is (graphic)
As you’ve read in the tip about different types of malware, a botnet is also a kind of malicious software. More specifically, a botnet is a network of infected computers that communicate with each other in order to perform the same malicious actions. These actions can vary from launching spam campaigns or phishing attacks, to distributed denial-of-service attacks. The network can be controlled remotely by online criminals to serve their interests. At the same time, this allows the cyber criminals to avoid detection or legal actions by law agencies. (A detailed intro to botnets is available here.) Shortly, here’s how a botnet is created: 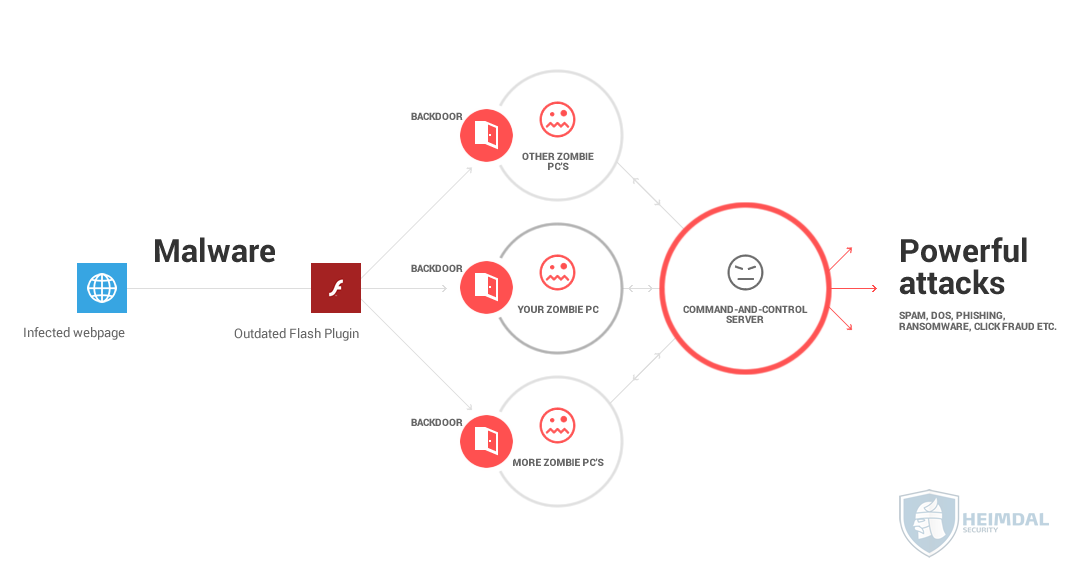
Cyber Security Tip #98: How antivirus works
Have you ever wondered how a traditional antivirus works? Here’s how: Real-time scanning – your antivirus should include this option which checks every executable program you open against known types of malware. Antivirus also looks at different types of behavior in the program to see if there’s anything potentially malicious about it. Full system scan – this is useful to check if any of the programs you already have installed is malicious or includes malware. Or you can use this scan to do a computer clean-up and rid your system of malware. Virus definitions – these are the main way an antivirus solution identifies and stops malware. These definitions pertain to different types of known malware. If a program or file on your PC matches one of these definitions, your AV will quarantine it to stop it from spreading. Unfortunately, antivirus is not enough to protect your data and you should read why that happens.
Cyber Security Tip #99: How your online accounts are connected
Have you ever thought of how your online accounts are interconnected? You may think that cyber criminals could never find your data appealing, but let me show you the truth. 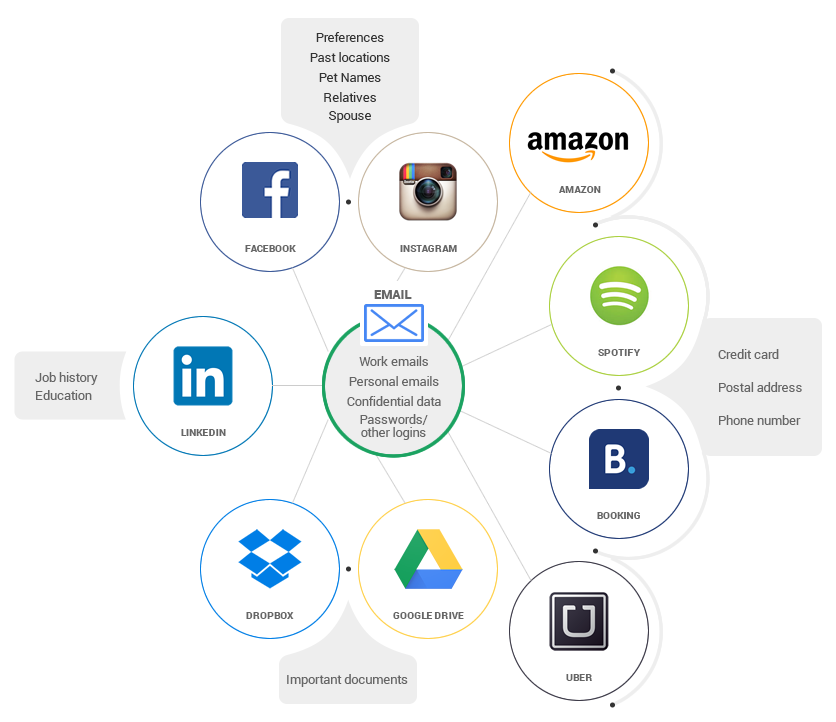 Your email holds crucial information about all your accounts, plus confidential information about your work and personal life. Your Facebook account or other social media profiles host details about your preferences, your friends and family, the places you’ve been, etc. If someone accessed your Amazon account, they’d learn about the stuff you bought, your wishlist, your shipping address and even your credit card details. And the list goes on and on and on. Are you sure that your data is not valuable? Because cyber criminals can definitely find a thousand ways to use it and make money from it.
Your email holds crucial information about all your accounts, plus confidential information about your work and personal life. Your Facebook account or other social media profiles host details about your preferences, your friends and family, the places you’ve been, etc. If someone accessed your Amazon account, they’d learn about the stuff you bought, your wishlist, your shipping address and even your credit card details. And the list goes on and on and on. Are you sure that your data is not valuable? Because cyber criminals can definitely find a thousand ways to use it and make money from it.
Cyber Security Tip #100: Why you should never, EVER reuse passwords
I hope you can take the time to think about how your online accounts are interconnected. Now think what would happen if an online criminal would find out the password of one of your accounts, Facebook let’s say. Do you use that password anywhere else? If you do, the attackers will use your email address (which they already have and try to see if you’ve set up accounts with the same credentials. How many accounts would the attacker be able to access? What kind of information could be stolen or compromised? Too few people really understand the dangers of password reuse. Apparently, not even Mark Zuckerberg is careful about his password security. Waves of attacks are often fueled by weak credentials which are easily compromised, like the TeamViewer case. And if you ever reuse your online banking password, well… you won’t enjoy the consequences. Promise yourself, here and now, that you’ll always use unique, strong passwords for every account. If you need help in doing so, this guide is your go-to solution.
Cyber Security Tip #101: Manage your Google Voice & Audio activity
Did you know that Google saves a recording of your voice and other audio to your Google Account? Google does this to learn the sound of your voice so you can use features like voice search (activated with „Ok Google”). But if you’d rather keep your privacy, here’s what to do to delete your voice recordings that Google has: Delete items one at time
- Visit the Voice & Audio Activity page. You may be asked to sign in to your Google Account.
- Check the box next to the items you want to delete.
- At the top of the page, select Delete.
Delete all items at once
- Visit the Voice & Audio Activity page. You may be asked to sign in to your Google Account.
- In the top right corner, select More > Delete options > Advanced.
- Choose Select date > All time > Delete > Delete.
More info on this here.
Cyber Security Tip #102: The best encrypted messaging apps
Encryption is a trending subject right now, although not everyone understands its applications or benefits just yet. But since the Snowden leaks, interest has definitely spiked for messaging apps that are safer from cyber criminals and even government monitoring. If you’re interested in the available options, I put together a list of the best encrypted messaging apps available at the moment. Our recommendation is you give them a try and see what fits your needs best. For business users, we also recommend you check out this extensive article that covers the pros and cons of the best business messaging apps out there.
Cyber Security Tip #103: Check these security elements on your online banking website
You probably hear a lot about financial malware. If you haven’t, you should read about it and know that it can use many insidious tactics to trick you. Here are some of the elements you should check before making an online transaction, to ensure that you cyber criminals don’t steal your card details: 1. Check is the website uses encryption (the padlock symbol) and uses https. This means you data is transmitted safely to and from the bank’s servers. 2. Check if the URL is correct and doesn’t include any typos. If you’re unsure of how the official website looks like (it may be your first time), do a quick Google search and verify the information. 3. Check if there are any unusual or extra fields added to your usual login steps. No bank will ever ask you for your address or card number or, worse, for your PIN in the login process. If you see anything out of place, leave the website, contact the bank and see how you can safely conclude the transaction. 4. Check if the logo and other elements are fuzzy, because sometimes cyber criminals use elements they can find on the web to mimic the appearance of a legitimate online banking website. Do a Google search of the official websites and compare them. If you find something strange, contact the bank and report it. 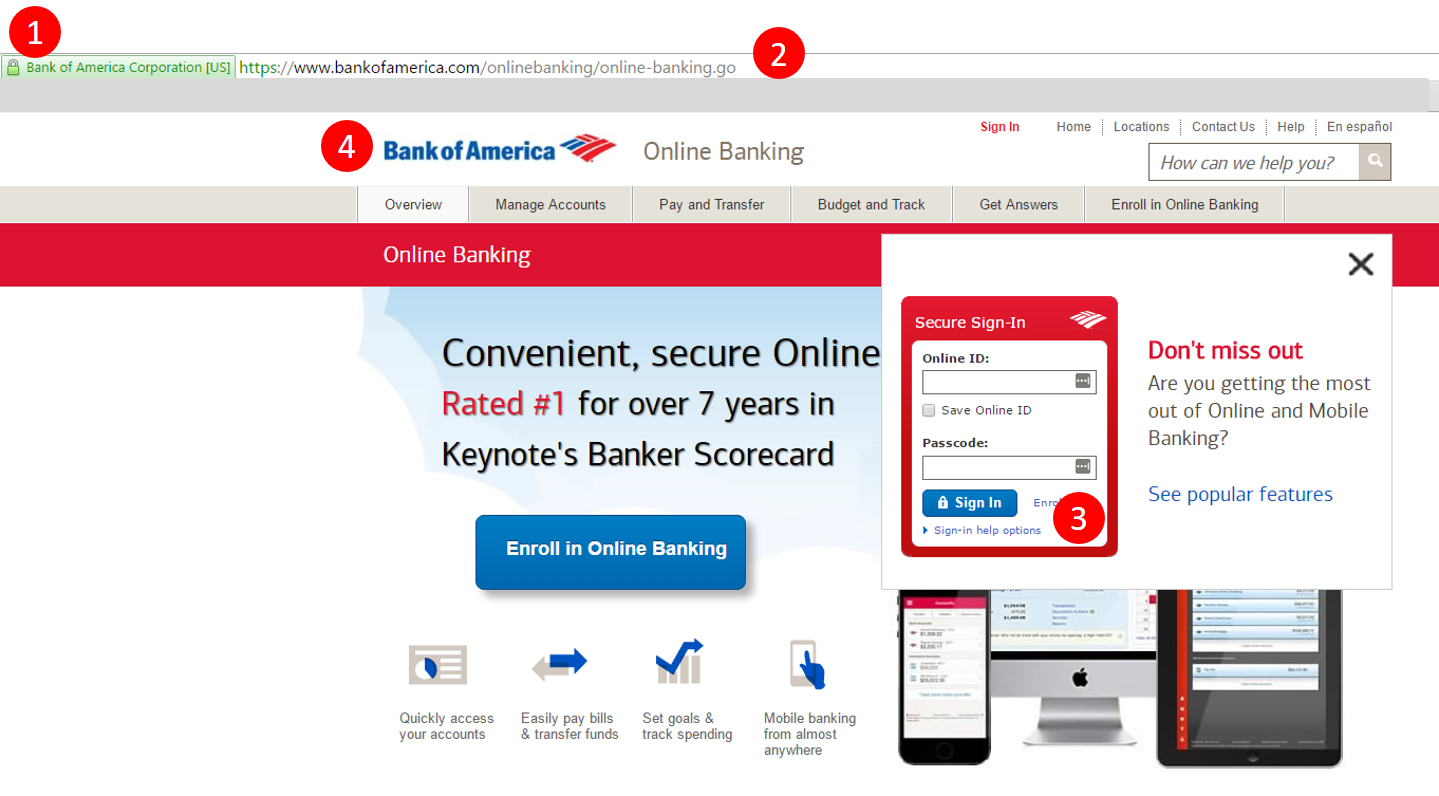 Additionally, you can check the footer of the website and see if there is any legitimate information on the bank, such as company details, locations and so on. The more information, written professionally and that can be verified, the safer you’ll know you are.
Additionally, you can check the footer of the website and see if there is any legitimate information on the bank, such as company details, locations and so on. The more information, written professionally and that can be verified, the safer you’ll know you are.
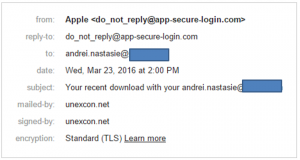
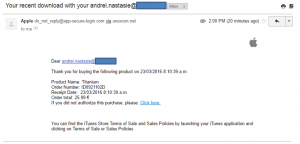
Cyber Security Tip #104: Example of a Paypal phishing attempt
I think examples are a great way to understand cyber security risks and attacks. This is why I want you to see how a Paypal phishing scam works. I recommend you read the full story, but for those who want a summary, check out the details below. Email contents: From: PayPal <donotreply@godaddy.com> Date: Sun 12/06/2016 18:10 Subject: Review your PayPal account limited statement Attachment: Issue ID Number PP 8400-7911-20-00.html Body content: —————————————————————- Review your PayPal account limited statement —————————————————————- Dear PayPal Customer, We understand it may be frustrating not to have full access to your PayPal account. We want to work with you to get your account back to normal as quickly as possible. As part of our security measures, we regularly check the PayPal screen activity. We request information from you for the following reason: Our system detected unusual charges to a credit card linked to your PayPal account. Download the attached form to verify your Profile information and restore your account access. And make sure you enter the information accurately, and according to the formats required. Fill in all the required fields. Thanks for joining the millions of people who rely on us to make secure financial transactions around the world. Regards, PayPal Some red flags you may have noticed are:
- The sender address (GoDaddy is a website hosting company, so it’s an obvious scam)
- The attachment with the weird name (banks and other financial services, such as Paypal, never send attached documents; they require you log into your account to download them)
- The attachment format: HTML – this clearly leads to an online destination. Never click on these if you spot a similar scam! The phishers probably used an HTML attachment because people have learnt that clicking on weird links in emails is a very, very bad idea.
- The lack of an official signature at the end of the email (although sometimes cyber attackers can fake those as well).
You should check out the entire story to see printscreens and other explanations. You may find this example very useful one day (soon)!
Cyber Security Tip #105: 5 key cyber security trends explained by a top expert
There are a few key trends in the cyber security world that impact all of us, as users. Mikko Hypponen, one of the most renowned and trusted cyber security researchers in the world, shared 5 of these trends and I think you should know about them. 1. Nation states may be robbing banks. It’s a known fact that nation states often create malware, especially for cyber espionage, but things may be a bit more complicated than we realize. The full article will set the proper context for this one. 2. Ransomware is not going away. The technology associated with ransomware keeps evolving, as cyber criminals incorporate new tactics. These apply to both technical aspects and the social engineering tricks played by attackers to lure potential victims. 3. Cyber crime as a business is growing. Online attackers are making big money off ransomware and other financial malware, but not only that. They’re building what you could call “business empires”, complete with teams of developers, a business strategy and the skills to implement it. 4. Poor passwords are still a pain Although cyber security specialists have been saying this for years, users continue to use weak passwords and, what’s worse, reuse them. This creates huge problems, especially in the event of a data breach. Cyber criminals only have to try and see if those users have reused their passwords to gain control of millions of accounts. I really hope you don’t do this. 5. Cyber crime empires are bigger than you can imagine Although no one can accurately and fully track all the money cyber criminals are making, their transactions amount to astounding sums! If these cyber crime-as-a-business enterprises would be legitimate, they would be HUGE! This wasn’t exactly a short tip, but you should read the entire thing to realize the extent of the problem we’re all dealing with.
Cyber Security Tip #106: Drive-by attacks – getting infected without knowing
Drive-by attacks have to be one of the worst things that can happen to an Internet user. Definition: A drive-by attack is the unintentional download of a virus or malicious software (malware) onto your system. A drive-by attack will usually take advantage of (or “exploit”) a browser, app, or operating system that is out of date and has a security flaw. Example: You’re surfing your favorite news website. On it, there’s an online ad you don’t even notice. What you don’t know is that the ad is infected with malware. Without you even clicking or hovering your mouse over it, the malware in the ad will scan your system for security holes. If it finds one, it will exploit it to gain access into your PC and create further damage. And you’ll never know this is happening. Protection tips include keeping your software up to date, using both reactive (antivirus) and proactive (traffic filtering) protection and hardening your browsers against cyber threats.
Cyber Security Tip #107: Review every device where you logged in to your Facebook account
Got a couple of minutes? Here’s a quick tip on how to check every device (mobile phone, browser, etc) where you logged in to your Facebook account. Open your Facebook account, go to Settings, click on the Security tab (it’s the second one) and review these two fields: Your Browsers and Apps – From here you can check all the web browsers and apps you saved in order to access your Facebook account without (re)confirming your identity. Don’t recognize one of them or you don’t use them anymore? Disconnect them immediately. Keeping them active only makes you vulnerable. Where You’re Logged In – Use it together with the previous feature to review your logged-in status. End activity for any device or place that doesn’t look familiar. Also make sure you remove any devices that you don’t use anymore, such as the ones used in former workplaces or ex mobile phones. Here are more tips on how to secure your Facebook account.
Cyber Security Tip #108: Was your account was involved in a data breach? What to do about it
The odds are against us when it comes to data breaches. Most likely than ever, one of our accounts will be breached. And it doesn’t even have to be our fault, as history proved. In May 2016, a cluster of mega data breaches was dissected in the media. More than 642 million social accounts were compromised – and it happened in less than two weeks. LinkedIn, MySpace, Amazon, Twitter, Badoo – they were all affected, more or less directly. Here’s what you should do in order to reduce the damage:
- Keep calm and change your password. I’m talking about the password for the hacked account – log in as soon as you find out about the breach. Change the password, make sure you set up a new, strong and unique one.
- Activate two-factor authentication, if the hacked service offers you this option. It will act as a second layer of protection, besides the initial password. Every time you’ll want to log in from a new device or browser, it will request you to authenticate using a second pass code, that’s unique and time sensitive. You’ll receive that one on your mobile phone – via a special app or text message.
- In case you were reusing the initial password, will you please stop doing that? Connect to all your other accounts and change their passwords. Start with the email account that was linked to the hacked account. Repeat the previous steps (new, strong and unique password, and activate two-factor authentication).
And, in the future, make sure you don’t recycle your passwords. EVER.
Cyber Security Tip #109: Stop and check before you click on that
Clicking on links that you have no idea where they’ll take you? Not a bright idea. I don’t care if you received that shortlink from your boss, your life partner, your favorite band or your mother (or at least so you may believe). If you don’t want to end up in a phishing or malware trap, check it first. Check it safely: you can use a service that shows you where that link redirects you to, or you can choose one that remotely takes screenshots of the website. You can use either one of these:
- Where Goes
- Redirect Detective
- Internet Officer Redirect Check
- Redirect Check
- URL2PNG
- Browser Shots
- Shrink The Web
- Browserling
Cyber Security Tip #110: Stop laziness from interfering with your cyber security
When it comes to healthy password habits, I know that sometimes I sound like a nagging mother. “Do this, do that, make it unique, make it strong, make it a hundred characters long” and so on. Yes, we’re all lazy. Yes, cyber security is hard. Nobody has the time to change all their passwords on a regular basis, make them unique AND still remember them. That’s why it’s important that we keep in mind the fact that strong passwords are the easiest and at hand way to keep intruders away from our valuable accounts. Try to remember the following analogy: We never use the same key for our car, our home and our office. If we would lose one or it would end up stolen, the thief would have access to all of our assets. Then why would we do the same with the passwords for our online accounts? Also, you can use a password management software that will remember all those passwords for you and scream at you if they aren’t unique or strong enough. And this way you’ll only have to remember one master password.
Cyber Security Tip #111: JavaScript malware explained
Don’t worry, I won’t get too technical, but you have to know this. JavaScript malware is a growing threat that will most likely have an even bigger impact in the next year than it has now. One key statistic will help you understand why: JavaScript is used by 93.6% of all the websites. If cyber criminals can manipulate JavaScript to perform malicious actions online, then they can use a huge amount of them to spread malware. In this guide, I explain how it all happens (graphic included): JavaScript Malware – a Growing Trend Explained for Everyday Users. Read it now and thank yourself later.
Cyber Security Tip #112: Watch Mr. Robot
As face as binge watching TV shows, most of us have done it. But no other show or movie has portrayed hacking and cyber crime as accurately as Mr. Robot does it. This is why I’d like to recommend you watch it. It’ll give you deep insight into how cyber attacks and data breaches happen. And it might even help you see what motives hide behind these actions. Season 2 is almost here, so you can catch up by watching the first season and the special which explains how the show was created to closely resemble reality (and sometimes even predict it).
Cyber Security Tip #113: How to protect your PC with multiple layers
I’ve often mentioned that the best approach to personal online security is to protect your data with multiple layers. While it sounds simple enough, I know the implementation is not exactly straightforward. So I created a detailed guide that explains how you can set up this multifold Internet security system: How to Protect Your PC with Multiple Layers of Security. Here’s a quick glimpse of how it looks like from a visual perspective (read the guide for specific details): 
Cyber Security Tip #114: How you can get infected via file transfers
Anything that cyber criminals can exploit to gain your trust and trick you into downloading malware will be used in attacks at some point. It’s not a matter of if, it’s a matter of when. Since a lot of people use WeTransfer, the emails they send are usually trusted and opened immediately. Online criminals take advantage of this and forge emails that looks exactly like the ones sent by WeTransfer. The malicious actors use details (names, email addresses, etc.) stolen from other victims and create the emails so that they look like the real deal. Once the victim received the email and downloads the archive, he/she will most likely open it. The problem is that the archive is loaded with Cerber ransomware, which will encrypt all the data on the PC and ask for ransom to unlock it. This doesn’t mean that WeTransfer has been compromised – they’re victims, just like you can be. The entire attack is based on social engineering tactics, which use psychological manipulation to get their way. You can read more about it here: WeTransfer random name at your own domain has sent you a file malspam delivers cerber ransomware. Top tip: always, ALWAYS analyze an email before opening it or before clicking on suspicious links and attachments. Especially if comes from an unknown sender.
Cyber Security Tip #115: Nothing comes free on the Internet
This cyber security tip is brought to you by Dave Piscitello, Vice President, Security and ICT Coordination at ICANN*: Nothing is free. This is particularly true for apps or software. Free often means if you give us access to your personal data. *ICANN is a not-for-profit public-benefit corporation with participants from all over the world dedicated to keeping the Internet secure, stable and interoperable. If you want to read more tips from 19 top security experts, check out: 50+ Internet Security Tips & Tricks from Top Experts.
Cyber Security Tip #116: How to select service providers that keep your data safe
It often happens that we share our personal information with all kinds of companies and institutions. And we do so all the time, when we open a bank account, when we set up a fidelity card and so on. But it doesn’t mean that all these organizations know how to keep our data safe. When choosing a service provider of any kind, consider these aspects:
- The general reputation of the organization
- Past security incidents (a simple Google search can bring that up)
- How secure their website it (Does it use https?)
- How focused their website it on privacy matters (Does it comply with privacy rules? Does it have a details privacy policy and terms of use?)
- How easily you can contact them if you need to (contact information, availability for customer support on social media)
- How much of your data they ask for
- If they provide detailed replies to this question: “Why do you need this personal data of mine for?”.
Maintaining a healthy suspicious attitude towards this can help you avoid becoming a statistic in a data breach, as they happen more often than not these days.
Cyber Security Tip #117: Track your web traffic on a global map
Have you ever tried to image how your Internet traffic looks like? Do you know where do your request goes when you access a website? You’re in for a big surprise! Use this tool to track your web traffic around the world and see how complicated the journey can be: https://www.ultratools.com/tools/traceRoute. This all happens in a matter of seconds, so maybe now it’ll be easier to understand how fast cyber attacks work when they use traffic redirects to reroute your Internet traffic to malicious pages.
Cyber Security Tip #118: How to stop Google from tracking you and your kids
Privacy and security are very closely related. You just can’t have one without the other. And when it comes to the ones we love, there’s nothing we wouldn’t do to protect them. This guide will show you how to:
- Block trackers
- Turn off interest-based ads in Google
- Use alternative search.
All so you can keep your privacy and protect you childrens’ right to intimacy on the web. Read more about it: How to stop Google from tracking you and your kids.
Cyber Security Tip #119: Why cyber attackers are stealing healthcare records
It’s almost impossible to avoid the news about data leaks from the healthcare industry. There are so many data breaches that people have almost gotten used to them. “Since late 2009, the medical information of more than 155 million Americans has been exposed without their permission through about 1,500 breaches.” But this matter should really not be taken lightly. If you’re wondering why cyber criminals use their resources to target healthcare organizations, here are some answers: “Healthcare records also contain the most valuable information available, including Social Security numbers, home addresses and patient health histories — making them more valuable to hackers than other types of data.” And the truth is that the organizations in this field aren’t very well equipped to protect your personal information from cyber attacks. What you can do about it is express your concern to local government, so adequate measures can be taken.
Cyber Security Tip #120: You can’t lose what you don’t have
I love learning from cyber security experts and I hope you do too. Another online security tip comes from Troy Hunt, Microsoft MVP for Developer Security: “Think twice before creating anything digital you wouldn’t want exposed including malicious email and nudie pics.” The same goes for online accounts and sharing your data on the web. If you spread it too far and wide, it’ll become impossible to control (and you’re most likely already dealing with that challenge). For more good tips, explore this expert roundup that I’ve recently updated.
Cyber Security Tip #121: Steer clear of public wi-fi
You discover a wonderful new coffee shop. The mug sits in front of you, surrounded in this wonderful light. You grab your mobile and decide to post a photo of it on Instagram. Or Snapchat – whatever works for you, I don’t judge. But first, you connect to a random wi-fi. Ok, hold it right there! Public wireless networks are a threat to your online security. Next time you want to connect to one of those, keep in mind that any data that you transfer over it can easily be tracked. That means any password you type, any private message you write – not that private anymore. According to Extreme Networks, a global networking solutions provider, a Wi-Fi attack on an open network can take less than 2 seconds. Are you willing to take that chance?
Cyber Security Tip #122: How safe official mobile app stores really are
I’m sure you’ve already heard how important it is not to install third-party apps on your mobile phone. You’ve been warned that apps that aren’t in the official app store are a security threat. But did you know that 75% of the apps in the public app stores do not pass basic security checks? (source) No matter how many measures Apple and Google take to keep their official app stores safe, chances are they’ll miss something. A malicious app will get past their strict criteria. They’ll have security bugs, they’ll ask for too many permissions, they won’t store your data in a secure manner. That’s why it’s important that you don’t rely exclusively on official app stores, as they’re not 100% bulletproof.
Cyber Security Tip #123: Major sports events attract major cyber security threats
Major sports events are a wonderful opportunity for scammers. You might not usually use sports apps or websites, but you become an active sports fan during major events, such as Euro or the Olympic Games. Cyber attackers use the hype to lure you with phishing emails and fake websites, exposing sports fans to new cyber risks. Watch out on what links you click on, what apps you download, where you give your credentials and on what sporting bets websites you end up on. Better be safe than sorry, right?
Cyber Security Tip #124: Sluggish PC? Might be sign of a malware infection
Is your computer running slower than usual? Does it take longer to start some of your programs? Malware has the tendency of slowing down your operating system, your apps or internet speed. If you notice anything like this and you’re not using any resource-heavy apps, check first for other causes. It may be that your fan is full of dust and it just needs to be cleaned. Or that it needs an upgrade. These 10 tips will come in handy when evaluating such problems. If you checked all those possible causes off the list, you can start to consider a potential malware infection. Or perhaps your computer is now part of a botnet (here’s what a botnet is and how to prevent your PC from being enslaved).
Cyber Security Tip #125: Watch out for vengeful ex-employees
Here’s an alarming statistic: almost two thirds of employees steal proprietary corporate data when they quit or are fired. If one of your soon-to-be-ex colleagues decides to do some damage before they leave the company, make sure that your work remains unaffected. Have a checklist of all the accounts that they had access to. Don’t forget to remove their permissions when they leave. Be careful of how you manage your passwords. Use strong and unique passwords, change them regularly, activate two-factor authentication and start using an app designed for password management. Have multiple backups done automatically. This way, you won’t lose any of your important files or folders.
Cyber Security Tip #126: How to stay safe on public wireless networks
I already talked about why you shouldn’t connect to a public wireless networks and the security risks you expose yourself to. However, if it’s inevitable, here’s how to make sure that your connection is somewhat secure:
- Hover your mouse over the network name to see which encryption it’s using. Check if the connection is secured using WPA security (WPA2 is even better), instead of WEP.
- It should require you to enter a password.
- Make sure that you only navigate on secure websites, with SSL certificate.
- Watch out for fake wireless networks. Make sure that you’re connecting to the ones provided by the owner and not scam ones, with similar names.
- Also watch out for fake hotspot registration pages, where you’re required to hand over your credit card details.
Cyber Security Tip #127: How not to infect your mobile phone with malicious apps
1. Only install well-known apps, ones that are extremely popular, from big companies. Odds are that they have an army of developers behind them and will make fewer mistakes than the small apps from less experienced creators. 2. Do a clean-up among the apps already installed. Get rid of the ones that you don’t use anymore. 3. Also get rid of the ones that require too many permissions. 4. Keep those apps up to date. Vendors constantly come with updates that bring new features, but also fix security and privacy vulnerabilities. 5. Install a trustworthy antivirus (again: it should be from a big, well-known vendor). In case everything else falls, you should have an automated backup. This way, if you ever end up with a malware infection, you’ll have all your important files already saved and won’t regret formatting your phone.
Cyber Security Tip #128: The list of shameful passwords
No matter how uninspired you are, never ever, under any circumstances, set one of the following passwords for your account:
- Any variation of the word “password” or “admin”.
- Your name or surname.
- Your partner’s name or surname.
- Name or surname of any member of your family.
- The dog counts as your family.
- Birthdate or birth location of anyone mentioned at the previous points.
- 12345, 123456789, 1111, 987654321. Seriously, why are you even considering any of these? Are you trying to get hacked on purpose?
- “qwerty” or “abcde” are just as bad.
- “696969”. Shame!
- “Batman”, “Superman” or any other super hero name. Except “WonderWoman”, Wonder Woman is the best! Just kidding. No super heroes.
Cyber Security Tip #129: Out of Office auto-responder? Don’t reveal too much
I’ve mentioned more than once the fact that you shouldn’t tip criminals on your whereabouts. Don’t check in on social networks when you’re on holidays, no matter how beautiful the landscape is. Your frenemies will still be envy if you post those photos after you get back home. Don’t write on your blog bragging about the wonderful places you’ll see. Write about them after you experienced them. And I’m adding a new advice to this list: watch out what you write in the out of office auto-responder. Make sure that you don’t give away too much information through your work email. Things like when you expect to be back and an alternative contact information in case of an urgency are more than enough.
Cyber Security Tip #130: Use a separate card for shopping online
The easiest way not to worry about shopping online: have a separate credit card that you only use for that activity. Transfer money on it every time you plan on buying something. Otherwise, leave it almost empty, only with enough funds for bank’s commissions. This way, in case someone manages to breach one of your online accounts and get your card details, they won’t be able to cause any serious damage. More tips on safely shopping online here.
Cyber Security Tip #131: Watch this story and apply everything you’ve read
Nothing will work unless you do, as the famous saying goes. You can install the best and most expensive security solutions in the world, but they can’t replace two things:
- a good, at least basic cyber security education
- and applying what you can from what you read.
To better understand why we’re dealing with these many cyber security challenges, watch this video:
Conclusion
Do you even need one after you’ve read all these tips? Reading time is over. Start applying these 131 cyber security tips and enjoy a safer digital life!

INSTALL IT, FORGET IT AND BE PROTECTED
Download Heimdal™ FREE

 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security