Contents:
When defining what is a botnet, we need to take into consideration that since it’s one of the most sophisticated types of modern malware, botnets are an immense cybersecurity threat to governments, enterprises, and individuals alike.
What Is A Botnet?
A botnet is a network of infected computers or other internet-connected devices, that communicate with each other in order to perform the same malicious actions, like launching spam campaigns or distributed denial-of-service attacks. The network can be controlled remotely by online criminals to serve their interests and, at the same time, this allows the hackers to avoid detection or legal actions by law agencies.
The term “botnet” comes from combining the words “robot” and “network”. Thus, botnets are entire networks of computers controlled and instructed to:
- attack other computers,
- send spam or phishing emails,
- deliver ransomware, spyware, or any other similar malicious acts.
And all this can happen without you having even the slightest idea about it. As you are aware, a single piece of malware can cause enormous damage. Now imagine what an army of millions of computers can do through coordinated attacks. Even small botnets can affect a business. And the worst part is that your computer can be recruited into a botnet as easily as 1-2-3. All it takes is a browser plugin update you just keep postponing. Or click on a link that you don’t know where it leads you to. And with our busyness and attention span that’s shorter than goldfish, the odds are forever in the cybercriminals’ favor.
Now we wouldn’t want to cause an unnecessary paranoia outbreak, so please keep on reading in order to find out more about what is a botnet and:
- What Can Hackers Do with Botnets
- How cybercriminals create and grow botnets
- How your computer can be recruited into a Botnet
- How to prevent that from happening
- How and what to check if you’re part of a botnet
What Can Hackers Do with Botnets
Fun fact: if you have been using the Internet since the late ‘90s / beginning of the 2000s, you most likely remember mIRC, the popular chat program. mIRC was actually using harmless botnets – like all other Internet Relay Chat text messaging programs, for that matter. However, most of the botnets are created for malicious purposes. Botnets can be used to:
1. Send out spam emails – If a spammer has access to a botnet, it’s very cost-effective and it will cost them close to nothing to do this. Although email is widely seen as an older vector for attack, spam botnets are some of the largest in size. They are mainly used for sending out spam messages, often with malware, in towering numbers from each bot, and spread bots to recruit more computers to the botnet.
2. Launch a Distributed Denial of Service Attack (DDoS) on a website, company, government, etc. – This happens by sending so many requests for content that the server cannot cope and it drowns (aka goes offline). Even very large websites struggle to remain online when botnets target their servers. Because malware and infrastructure dedicated to cybercrime have become commercially available, costs have decreased and allowed more attackers to have access to these types of services.
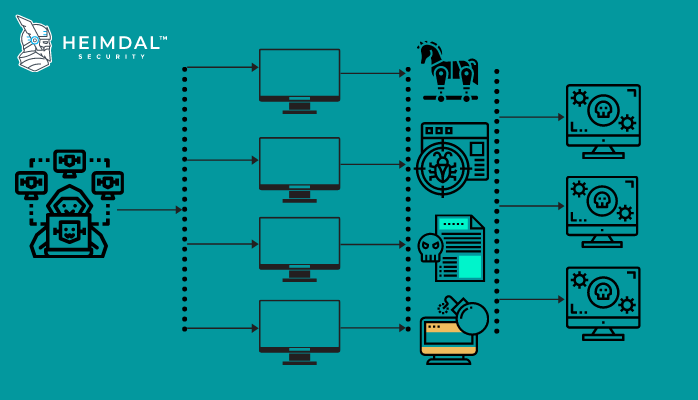
3. Commit advertising fraud – Computers all around the world can generate fake clicks on ads – this helps scammers raise serious amounts of money. According to a recent report by the Association of National Advertisers, marketers all over the world could lose this year up to $7.2 billion because of it.
4. Keep phishing websites active and frequently change their domains to remain anonymous and undetected by law enforcement.
5. Distribute malware, ransomware, or spyware. Besides the direct financial damage incurred, this can also expand the botnet further. Short (moral) story: Zeus was one of the most powerful financial malware on the internet. A botnet ready-to-deploy for cyber attackers. Its primary function was to steal online credentials, especially banking-related ones.
Zeus is very difficult to detect even with up-to-date antivirus and other security software as it hides itself using stealth techniques. It is considered that this is the primary reason why the Zeus malware has become the largest botnet on the Internet: some 3.6 million PCs are said to be infected in the U.S. alone.
Another ransomware that has been causing damage, Locky, also enrolls the affected PC into a botnet. Botnets became so large and distributed across the world, that they can be very challenging to take down. It takes a lot of effort from many cooperating parties in order to bring down a large botnet. Here’s another example: the Simda botnet infected more than 770.000 computers in over 190 countries (among them: US, UK, Canada, Russia, Turkey). It was active for years and used to distribute pirated software and different types of malware, including stealing financial credentials. Creators of the specific malware types simply rented it from Simda creators and paid them a fee for every attack. Last year, Kaspersky researchers published an interesting blog article explaining the efforts needed to take Simda down:
A simultaneous take-down of 14 command and control servers of the Simda botnet located in the Netherlands, US, Luxembourg, Russia and Poland was carried out on Thursday, April 9th. The list of organization involved in this shut down operation perfectly illustrates its complexity. INTERPOL, Microsoft, Kaspersky Lab, Trend Micro, Cyber Defense Institute, FBI, Dutch National High-Tech Crime Unit (NHTCU), Police Grand-Ducale Section Nouvelles Technologies in Luxembourg, and Russian Ministry of the Interior’s Department ‘K’ were working together to counteract the cybercriminals.
How Cybercriminals Create and Grow Botnets
Now that you have a clear definition of what is a botnet, we can move on to explain how threat actors create and use them. We can sum it up in one word that covers it all: malware. Cybercriminals will do anything to trick you into downloading and executing the malicious code that recruits your computer to their botnet. They will lure you into a drive-by download. They will exploit vulnerabilities in websites and software, such as your browser’s outdated plugins. They will trick you into clicking on links or opening malicious email attachments. We’ll come back to these later on. Once executed, the malicious code will use the Internet to make contact with the control computer, the one that operates the botnet (it’s also called a Command & Control server).
Your computer will remain idle, except for periodically checking for instructions from the control computer. In the meantime, the one pulling the strings will focus on recruiting more computers to the initial botnet. As they don’t appear to be doing anything, the botnet could contain even hundreds of thousands of zombie computers without raising suspicions. The cybercriminals who operate the botnet will most likely sell it or rent time on it – kind of like subcontracting. Sooner or later, they will issue a command through the Command-and-Control server, and the botnet will wake up and launch an attack.
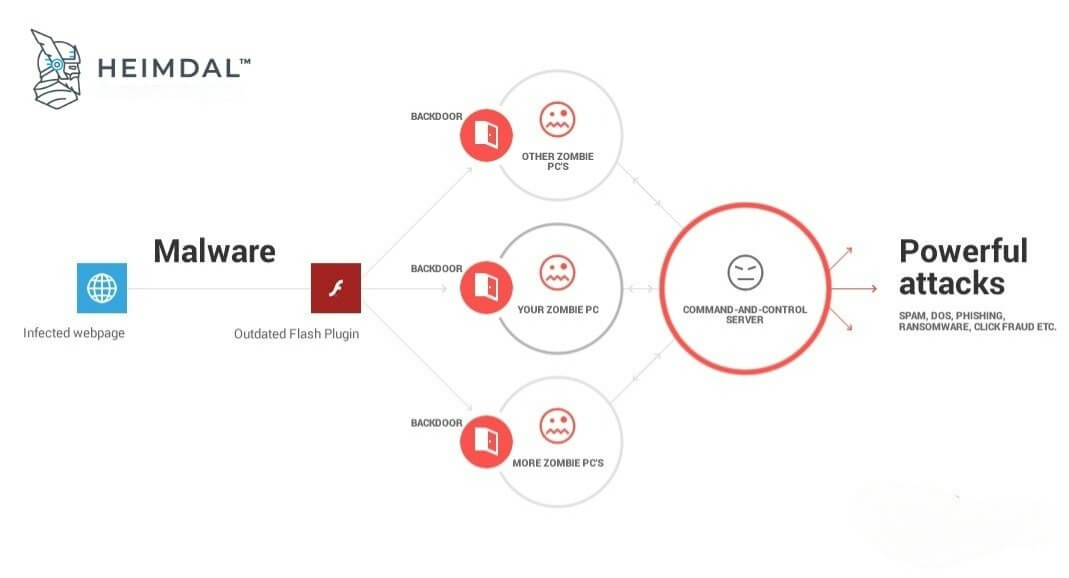
How Your Computer Can Get Recruited Into A Botnet
Recently, the conversation around what is a botnet has grown from one that only existed in the cybersecurity landscape to a more universal discourse. We were saying earlier that the most common method for recruiting computers into a botnet is through malware. The owners of the botnet will do anything to get the malicious bot code on your computer. There are a few ways they can achieve this:
Via Email
Attackers will send you emails that contain malicious attachments or links to websites they control, where malicious code is hosted. Locky, the ransomware that also recruits your PC into a botnet, was distributed via a massive email spam campaign.
Via Social Networks / Messaging Apps
Similar to emails – they’ll trick you into clicking on links that you received on a social network.
Via Drive-by Downloads
These work by exploiting vulnerabilities from your web browser, browser plug-ins, or add-ons. Other times, the attackers will trick you into downloading the malicious software, without fully understanding its impact. For example, while visiting a legit website, you’ll see a pop-up that says your computer was infected and prompts you to download antivirus protection. Beware – that’s actually malware.
Via IoT Devices
Mirai Botnet appeared for the first time in 2016 and has continually posed a threat to IoT devices. Mirai made headlines in September 2016 by taking down several high-value targets including Krebs on Security, the private cloud provider OVH, and DNS provider Dyn. What makes Mirai stand out in a crown is its IoT propensity; while most botnets target servers, personal computers, networking peripherals, Mirai zeroes in on Internet-of-Things devices (e.g., connected appliances, biometric scanners, wearable health monitors, smart security cameras, DVRs, etc.). As per the Q4 2016 State of Security report, at its peak, the Mirai ‘zombified’ network totaled over 600,000 infected IoT devices coordinated by no less than 484 unique Command-and-Control servers.
Preventing Your Computer from Becoming Part of A Botnet
After defining what is a botnet and how your PC can get recruited into one, it’s now time to explain how to prevent your computer from being infected and becoming part of a botnet in the first place. Here are the basic rules that you should follow to avoid becoming part of a botnet:
1. Don’t click on any suspicious links that you’re not sure / don’t know where they lead – not even the ones you received from friends or family or social network buddies. Their accounts might have been compromised, so it’s safer to be patient and ask them what it’s all about, before rushing into clicking on the links.
2. Do not download any attachments that you never requested.
3. You need a good antivirus and antispyware software, installed from a reputable source. Avoid online ads that are telling you that your computer was infected – these are malware in disguise.
4. If you already have antivirus and antispyware software, check to see if they are activated, patched, and up-to-date. Do a full, in-depth scan with the antivirus. Sometimes, a bot code will deactivate your antivirus.
5. Make sure that your firewall is on. Set it to the maximum security level – this will require all applications seeking internet access to notify you, enabling you to track incoming and outgoing traffic.
6. Keep all your software up to date, especially your browser, Adobe Flash, Adobe Reader, and Java. These are the most vulnerable ones – and also the most exploited by cybercriminals to recruit computers into a botnet. Updating apps can lock out 65% of attack vectors that target your apps, so don’t disregard this very important proactive security measure (you can check out our Heimdal FREE, which does just that – automatic software updates).

How to Check If You’re Part of A Botnet
Is your computer or internet connection running slower than normal? Did your computer start behaving erratically? Does it crash frequently? Do you receive unexplained error messages? Did the fan kick into overdrive when your computer is idle? Did you notice unusual internet activity (like high network usage)? Does your browser close frequently and unexpectedly? Did your computer take a long time to start or shut down or didn’t shut down properly?
These can indicate that a program is running without your knowledge and using a fair amount of resources. The next step would be to check the Task Manager – see what’s going on in there. You can also disconnect from the Internet and see if there are any differences. Of course, all these could also indicate that your fan is full of dust and it just needs to be cleaned. Or that your computer is obsolete and needs an upgrade. However, if this is not the case and you discover that you’re computer is part of a botnet, the standard advice would be to wipe it all out. Format it and reinstall the operating system. In order to minimize any potential damage, make sure that you always backup all your important files and folders. This is a piece of advice most people ignore, but I know you know better than that.
Understanding what is a botnet and a botnet attack is the first step to protecting your devices.
Conclusions
Botnets are a much bigger problem than we can imagine. Both in terms of size and impact, because the sheer numbers and possibilities will make you gasp for air. This infrastructure gives cybercriminals the possibility to expand their reach, launch powerful attacks, and cause irreparable damage. And that’s something that every Internet and computer user can prevent, by taking the necessary security measures. And remember this: if malicious code to recruit your computer into a botnet can get in, so can ransomware, financial malware, and other threats.
By learning more about what is a botnet, how it works, and implementing the appropriate measures in your network, you can make sure your system is protected against such threats.
Drop a line below if you have any comments, questions, or suggestions related to botnets.
Note: This article was initially published by Cristina Chipurici in February 2016.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










