Contents:
The alarming growth of malware attacks in the last years should concern each of us, but what is more important, should make us AWARE of the risks and consequences. Taking action and preventing these malicious activities operated by cybercriminals has to be a top priority IF we want to stay safe online.
The reality is that cyber attackers now use different strains of malware, much more sophisticated and agile that prove to be effective and successful, challenging us to build a stronger defense against them.
Malware evolves at a rapid pace because of advanced malware mastering the art of evasion. Thus, traditional antivirus engines find it difficult to detect attacks in the first stages. Malware is getting bigger and bigger. It fuels growth, innovation and encourages malicious actors to easily reach their goals.
In this article, we’ll have an in-depth analysis of malware and learn: where it hides, what are the most dangerous malware attacks so far, why malware a profitable business for cybercriminals and offer actionable security tips to help you better prevent these attacks and keep yourself (and your digital assets) safe.
Why malware attacks keep happening?
In the context of this ever-changing threat landscape that never ceases to challenge everyone from home users, organizations to security researchers and communities, this question makes a good point.
It’s simple. Malware still works, and humans have their contribution to helping attackers succeed with their malicious plans.
True fact: Throughout our old habits that seem to die hard (not updating our software frequently, or reusing the same password for various online accounts), we maintain security holes that malicious actors are exploiting and fueling this growing malware business.
According to a report from Trustwave security company, 22 percent of respondents (security respondents) said that “preventing malware, including ransomware, was their biggest security threat and obligation for 2018”, while the second biggest pressure was identifying vulnerabilities (17%) and the third one (13%) was preventing social engineering and phishing attacks.
Paul Edmunds, Head of Technology at the National Crime Agency’s National Cyber Crime Unit (NCCU) states that:
It’s really important to understand the impact that malware has. It’s a massive criminal enabler that underlines most cybercrime. It’s an infrastructure that’s used for compromising devices to conduct most of the prominent attacks that you see.
The evolution of malware
Before we understand its impact, let’s take a few steps back and have a look at how malware evolved lately to become such a serious and threatening business to everyone.
The malware market evolved from something that was tested and probably used for fun, – with hackers creating programs to see how they can gain access to unauthorized places and then focusing on money and going for stealing personal data – into a more targeted attack vector.
Did we ask for malware? No, but there’s a big business out there and we are all responsible in a way or another for making it alive and growing.
According to Cisco 2018 Annual Cybersecurity Report, the evolution of malware was “one of the most important developments in the attack landscape in 2017”. “Malware is becoming more vicious. And it’s harder to combat. We now face everything from network-based ransomware worms to devastating wiper malware.”
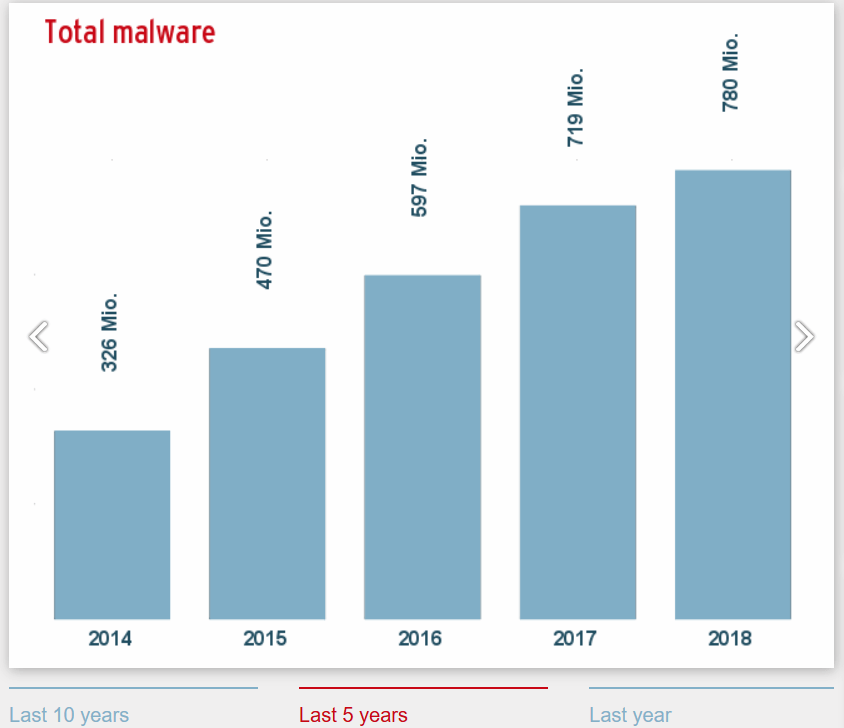
This graphic from AV-Test shows the growth of total malware over the last five years:
Source: AV-TEST.org
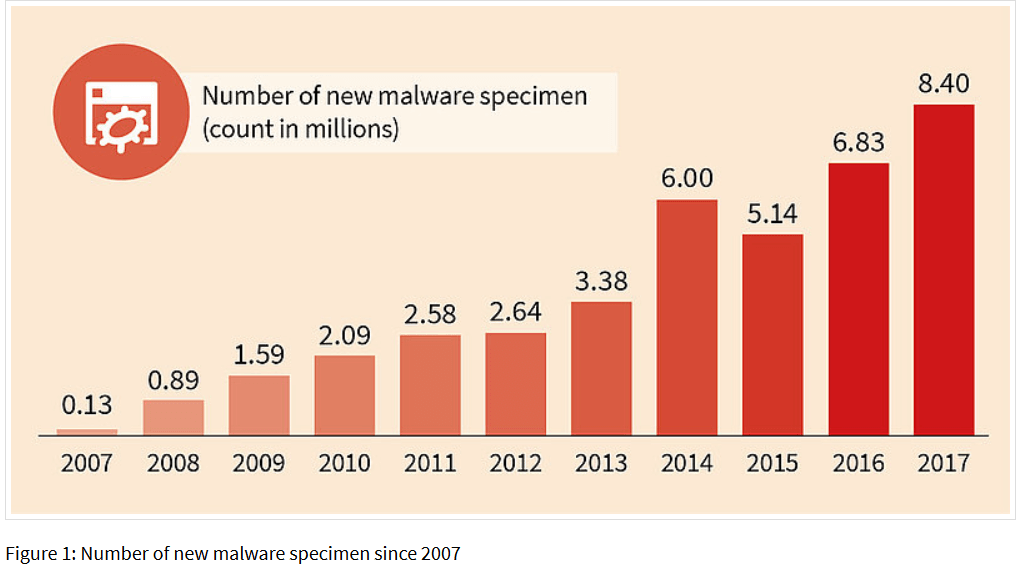
Also, did you know that “in the second half of 2017 on average 795 new malware specimen were discovered per hour i.e. 13 per minute.”?
Source: Gdatasoftware.com
Regardless of the smartphone landscape, mobile malware is one of the fastest types of malware, targeting more and more Android users. In the first quarter of 2018, the G DATA security experts detected “an average of 9,411 new malware every day for the popular Android operating system”. This means: A new malware appearing every 10 seconds.
The rise of ransomware attacks
Perhaps a clear evolution of the malware economy has seen last year with the two massive and devastating cyberattacks: WannaCry and (non)Petya.
The first one was called by Europol an attack of “an unprecedented level” that took down entire networks and caused business disruption across 150 countries and infecting more than 200,000 computers. Not to mention the financial damage caused, because many companies and public institutions have had their computers and data encrypted, and the only way to get it back was to pay a ransom.
If during the WannaCry ransomware, cyber criminals used the EternalBlue method, with (non)Petya ransomware outbreak, – that also spread fast and had self-replicating abilities. -, they changed the type of malware from ransomware to wiper. How is this different? The purpose of a wiper is to destroy and damage, while ransomware is mainly focused on making money.
In 2018, malware is even more agile, and Gandcrab ransomware is a great example. It is a fast-growing malware that’s been used and spread in waves of spam campaigns. While it reached version 4 already, this piece of malware was initially distributed via exploit kits which abuses software vulnerabilities found in systems.
[Tweet “Here’s what you need to know about the growth of malware as a business.”]The newest version 4 of this malware family includes “different encryption algorithms, a new .KRAB extension, new ransom note name, and a new TOR payment site”. So far, Gandcrab is one of the most prevalent and biggest ransomware attacks in 2018. Here’s a more in-depth and technical analysis of how Gandcrab ransomware evolved if you want to dive into this topic.
If you’ve been hit by any of these ransomware attacks or others, we strongly advise you NOT to pay the ransom to get your data back. Instead, check out this list of decryption tools to unlock your data for free.
5 key places where malware can hide
Malware authors often look out for new techniques to hide their malicious files which often go unnoticed by antivirus software or threat intelligence analysis.
Here are the most common places where malware can hide:
- Email attachments – Most of the security alerts we’ve written talk about malware being delivered via emails to potentially infect victims’ computers. Sadly, many people still download, open, click and enable malicious attachments to run on their computers. Here the example of a variant of Trickbot malware in which cybercriminals lure victims into clicking on a malicious word document attached in the email.
- Links sent via email – Another common place where malware can hide is a link received via email which is more tempting for users to simply click it than downloading an attachment. This mindless clicking behavior is known and exploited by cybercriminals.
- Traffic redirect – Another place that malicious actors exploit to hide malware is in the Internet traffic(especially in the browser). As we spend most of the time reading online, browsing blogs or buying on the Internet, it’s easy to become a target. Traffic redirect may be invisible for the unskilled users, so they land on sites where malware is hidden in the code of the page or on the ads listed on the site.
- Software updates – Probably the story of compromised versions of CCleaner software apps is the best example here. Hackers spread hidden malware in the version 5.33 of the CCleaner software which has been downloaded by more than two million users. Full story here.
- Hidden and infected mobile apps – Given the rise of mobile apps, we’re likely to download and install all kind of apps on our device, without taking any caution. Here’s an example of malware threat known as hidden administrator app that targets Android users. It is an infected app that installs itself with administrator privileges and takes control of your mobile device.
If you want to find out more about how and where cybercriminals hide their malicious code in files, links, apps we use on a daily basis, read this guide.
Why Malware is a profitable business for malicious authors
Just like any other business, the purpose of malware authors is to turn it into a big and profitable business of millions (or even billions of dollars). To do that, it’s important for them to know and ask for the right price.
Making money from malware has proved to be a winning option for cybercriminals. Usually, they choose rich and developed countries, target large and successful organizations, from where they can extort a lot of money and access their valuable data.
As the number of ransomware attacks continue to grow exponentially, its authors will keep making a lot of money, because most of the victims choose to pay the ransom.
According to the Telstra Security Report, more than half of businesses who were victims of a ransomware attack have paid the ransom and they would do it again. “Some 60 percent of ransomware victims in New Zealand and 55 percent in Indonesia paid the ransom, making it the highest for Asia. In Europe, 41 percent of respondent ransomware victims paid up.”
On top of that, another research conducted by Cybersecurity Ventures estimates that ransomware damages will cost the world more than $8 billion in 2018 and they will reach $11.5 billion annually by 2019.
The attackers behind Wanna cry ransomware may have caused global panic among users and organizations, but what about its financial costs? In total, it has been estimated that they made $143,000 in Bitcoin of this massive attack.
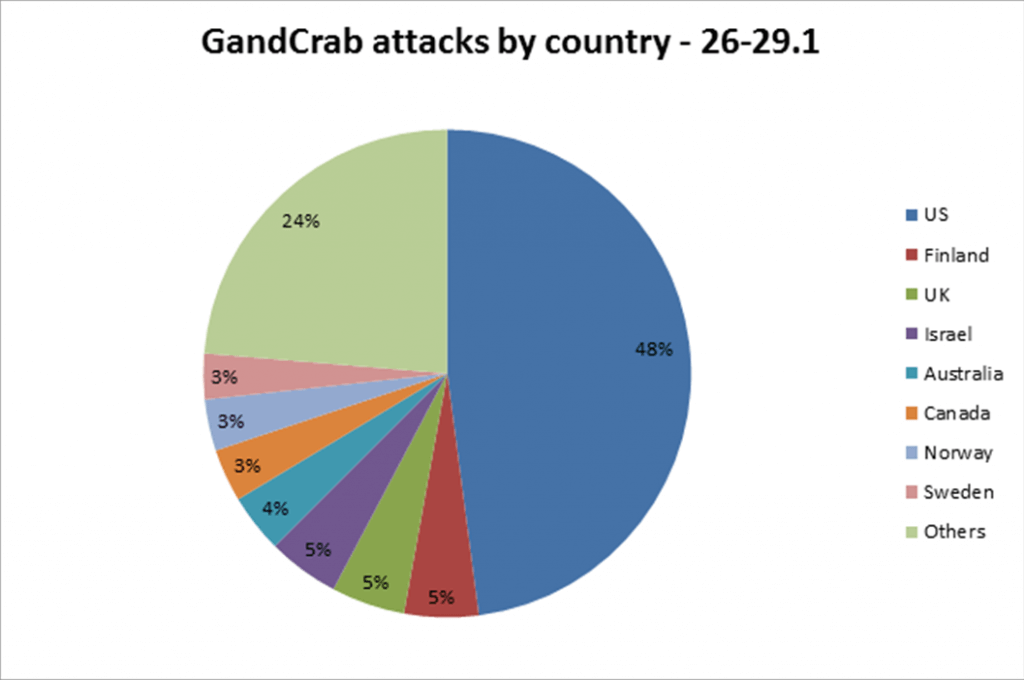
The Gandcrab ransomware that continues to evolve and quickly being spread into various spam campaigns “has infected over 50,000 victims and claimed an estimated $300-600K in ransom payments”, according to Check Point Research. In the figure below, you can see the attack by geographic location of a target.
Source: Checkpoint.com
The success of Bitcoin cryptocurrency and its price reaching a historic $20K at the end of 2017 influenced the rise of cryptojacking malware attacks.
New findings from Check Point research stated that “the number of global organizations affected by crypto-mining malware more than doubled from the second half of 2017 to the first six months of this year, with cybercriminals making an estimated $2.5 billion over the past six months.”
The research also discovered that hackers are now targeting cloud services because most businesses store their sensitive data there. And there are more cyber security threats that should concern us and determine to implement solid prevention and security measures.
All these examples from above show that malware business is still growing, by switching from a macroeconomic level to microeconomic level. The malware market, like any other, offers a wide range of products to fit users’ diverse needs. You can find APTs, ransomware, banking trojans, cryptojacking, data breach, online scams, malware families with as many names as you can possibly wish for. Just like when you go to the supermarket and you have a plethora of vegetables and fruits to choose from.
Today’s malware is more targeted, but not necessarily more sophisticated. They still exploit software vulnerabilities found in devices, and that’s not something too complicated about it. Today malicious actors are both agile and creative and try techniques that still work. Today next-gen malware attacks have the ability to evade detection and bypass antivirus programs users install on their computers to keep their data safe.
Security measures to apply against malware attacks
We might not have asked for a malware market, but we are still serving it through unpatched software, by not backing up data, not getting enough education and knowledge of cyber security and many more.
Time to act is right NOW!
Malware threats are wide spreading and difficult to combat, so, once again, we emphasize that prevention is the best strategy to stay safe online.
Make sure you don’t fall victim to malware and follow these cyber security measures:
- Always keep your software patched and up to date, including the operating system and every application you’re using on a daily basis;
- Keep a backup with all your important data on external sources like a hard drive or in the cloud (Google Drive, Dropbox, etc.). This guide shows you how to do it;
- Once again, we urge you: Do NOT OPEN emails or click on suspicious files/attachments. Be very cautious!
- Remember to set strong and unique passwords with the help of a password management system. This security guide comes in handy.
- Use a reliable antivirus program as a basic protection for your device, but also consider including a proactive cyber security solution as a second layer of defense for maximum protection.
- Always secure your browsing while navigating the Internet and click on websites that include only HTTPS certificate;
- Teach yourself (and master basic cyber security) to easily spot online threats delivered via emails, social engineering attacks or any other method attackers may use.
- We remind you that security is not just about using a solution or another, it’s also about improving our online habits and being proactive every day.
Will malware as a business continue to grow? I think it will, as long as was – and still is – heavily sustained by ransoms paid by victims who want immediate access to their valuable data. It will continue to grow as long as we don’t apply basic security measures that can make us less vulnerable to these attacks.
This article was initially written by our CEO, Morten Kjaersgaard, in 2015, but refreshed and improved by Ioana Rijnetu in July 2018.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security