Contents:
This year we saw massive spam campaigns like NonPetya or Locky fly below the radar of antivirus software and went undetected during the first hours or even days. Some of them actually went undetected even for months. Second-generation malware usually has the ability to evade detection and bypass antivirus programs users have installed on their computers to keep their data safe. Maybe you’ve never asked yourself this, but do you know how long it takes for antivirus programs to detect advanced types of malware?ra In this article we’ll show you several examples of spam campaigns which went undetected by antivirus software and explain why this happens in the first place. We’ll also provide details on how you can protect efficiently against such threats and close the various security gaps in your system. Did you know that a new malware strain was discovered every 4.2 seconds in the first quarter of 2017? Security experts came to this conclusion in their “Malware trends 2017” report.
How antivirus software detects malware
Modern malware threats are too sophisticated and can be devastating for your PC without proper online protection. Antivirus programs might not offer 100% protection for your devices, so it’s for the best not to depend solely on them. As users, we need to strengthen our defences and consider adding other security software to keep cybercriminals away. Antivirus is sometimes known as antimalware program, and people tend to use both terms interchangeably, believing that antivirus programs can defend from all types of malware, which is not the case. Here’s what antivirus software can do for you:
- Virus scanning, which is done in the background for your files that will open only after the scanning process is over. Most antivirus programs are packed with real-time scanning feature which allows to quickly detect any malicious files on your PC.
- Blocks malicious files and prevent them from running, because they put your computer at risk of being infected with malware.
- Automatic updates are must-have features to easily track and detect new threats that didn’t exist when your antivirus software was installed;
- Malware removal is used to detect and remove specific malware from your devices. AV software might be limited to detecting only old strains of malware and miss the new forms of online threats.
- Antivirus might also include phishing protection, vulnerability scan, browser protection and system optimization features.
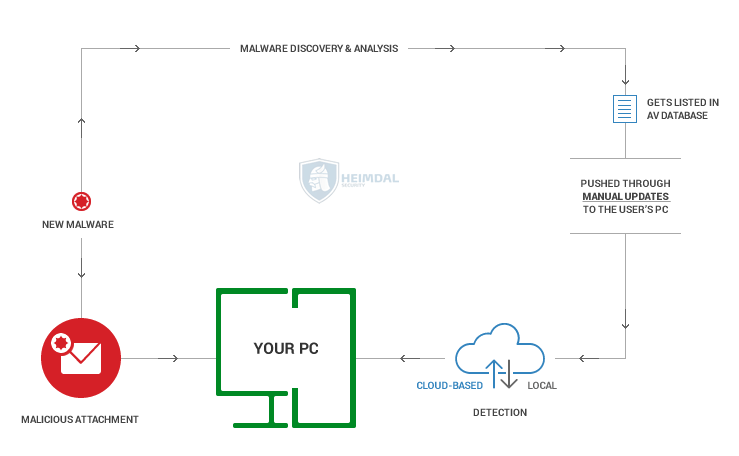
The image above loosely explains how AV can find and detect new malware which is usually delivered via email through a malicious attachment. If your AV program is up to date on your PC and the malware is listed in the AV database, it will be detected and isolated. If it the AV is not up to date, the malware will go undetected. It’s worth mentioning that not all antivirus products offer the same level of computer protection, because each one may include specific and/or advanced features included. In terms of virus detection techniques, AV includes:
- Signature-based detection method is using examined files to create a static fingerprint of known malware. It has its limitations: can’t detect new malware for which signatures have not yet been developed;
- Heuristic analysis is a method designed to identify new malware by statically examining files for suspicious behaviour without an exact signature match. One of its downsides is that can accidently detect legitimate files as malicious;
- Behavioral detection method is rather based on observation, rather than execution, and tries to identity malware by looking for suspicious behaviors in files;
- Cloud-based detection can identify malware by collecting data from protected computers while analyzing it on the provider’s infrastructure, instead of performing a local analysis.
False positive detections in the antivirus industry
We know we have a false positive when an antivirus program informs users there’s a specific vulnerability or a potential infection on their devices, and in fact there isn’t. What’s really happening is that your antivirus programs might block a piece of software that proves to be safe. These mistaken detections are known as false positives and might represent a serious problem for users being impacted by potential malicious attacks. In fact, no antivirus software is perfect, and they might report a false positive at some point. The State of Malware detection and prevention report conducted by Ponemon Institute analyzed how IT security experts manage preventing and detecting malware and advanced threats. Investigations of malware threats are often false positives and a high volume of these false positives will prevent them for seeing the real problems faced by any organization. Those responsible with security operations spend a significant amount of time investigating and chasing false positives. However, study found that only 32% of respondents say their security teams spend time prioritizing alerts that need to be investigated. This graphic below give details on how an average of 40% of malware alerts investigated by security teams are considered to be false positives. 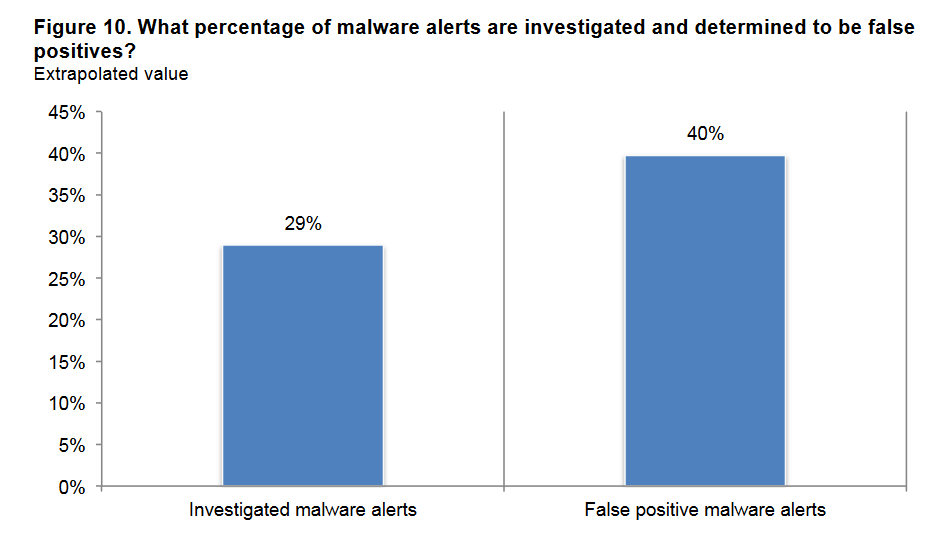 Source: Ponemon Institute Report This means that no antivirus software (or other software product) is 100% accurate and may not offer the best accuracy in terms of detection rate and false positives. The antivirus software market is dynamic and complex, and it gets harder to track all the threats targeting users from everywhere. New malware continue to rise at an alarming rate and cybercriminals become more successful in combining technical and psychological skills to launch new cyber attacks.
Source: Ponemon Institute Report This means that no antivirus software (or other software product) is 100% accurate and may not offer the best accuracy in terms of detection rate and false positives. The antivirus software market is dynamic and complex, and it gets harder to track all the threats targeting users from everywhere. New malware continue to rise at an alarming rate and cybercriminals become more successful in combining technical and psychological skills to launch new cyber attacks.
Antivirus software has a hard time detecting new malware threats
Antivirus programs aren’t effective as they used to be because of the rise of new malware attacks which they can’t fend off. Online threats have evolved greatly during the last years and users need to find alternative security solutions to enhance protection for these new threats. Malwarebytes analyzed information from scans of approximately 10 million endpoints, the majority of which had one or more traditional AV programs installed. The results of these scans showed that traditional AV solutions are weak and fail to protect against even the most common forms of malware spotted in the wild. Almost 40% of all malware attacks in the wild cleaned by Malwarebytes among endpoints with AV installed occurred on endpoints that had two or more traditional AV solutions installed. You can read the full Malwarebytes report here to see its findings. When it comes to zero-day attacks, the malware is brand new and antivirus software might have problems in detecting them. Antivirus programs do a better job at protecting against known types of viruses and online threats, such as: Trojans, rootkits, backdoors, phishing attacks or botnets. From exploiting a vulnerability in Windows to changing the type of malware delivered ((Non)Petya ransomware, for example), from switching to new infection vectors to delay strain detection, to using auto-updating elements that automate new payload delivery or social engineering attacks, cybercriminals are getting better and better at spreading malware and infecting a large number of computers. Antivirus software might fail to detect malware for various reasons, but one major cause is its reactive scanning procedure. Online criminals often find innovative ways to evade the threat analysis system and infect users’ computers. Here’s how:
- From our experience, over the last years, we noticed that antivirus products still have issues in detecting second generation malware in a timely manner. It can take up one or two days to spot them, especially those AV products that aren’t rated as the best top 10 AV software. In this time, cybercriminals can do a lot of things: from stealing your financial information to encrypting your data via a ransomware infection;
- Malware creators constantly look for different ways to avoid AV detection. For instance, they equip malware strains with the ability to detect sandboxing mechanisms by checking registry entries, computer’s video and mouse driver, specific communication ports and more. When malware detects that it’s running in a virtual environment (sandbox) it will stop its activity, so antivirus products may conclude that it’s a safe file and just let it pass. Plus, AV don’t spend too much time on a file and might be difficult to detect a code as being malware.
- Online criminals often use an evasion technique called Fast Flux to make it more difficult for AV to detect malware. It is usually used by botnets to hide phishing campaigns, malware-loaded websites and other infection sources targeting a large group of users.
- Malicious actors can also use encrypted payloads to infect victims’ PCs which will lead to a delay detection by antivirus products and more time for cybercriminals to deploy the malware and spread infection.
- Recent attacks targeting MS Office can run malware without the need to trick users to enable macros and making difficult for AV to detect it. Malware authors take advantage of a legitimate Office feature called Microsoft Dynamic Data Exchange (DDE) allowing an Office application to load data from other Office apps.
- Cybercriminals use domain shadowing to hide exploits and communication between the payload and the servers they control. For that they need a vast number of URLs they can use and discard.
- The bad guys are agile and move faster than security vendors, so they rely on other tactics by using a polymorphic behaviour which involves changing file names and file compression.
How second generation anti-malware programs detect new threats
Most of the tactics used by malware creators to spread infections are hard to be detected by antivirus programs. Especially second generation malware that might go undetected for months, because malicious actors always update and improve their tactics to avoid detection. Detection continues to be a major issue for both organizations and home users, due to the fact that new malware threats often remain invisible to an antivirus product. This happens because most people rely on a single product, usually an AV product, and don’t update it regularly. Without constant updates, users expose themselves to more attacks, being more vulnerable to be hit by them. Antivirus is not a “set-it-and-forget-it” solution and neither is any other security setup you may install on your device. AV may be your go-to solution to fight malicious software, but there’s always room for improving things. This is why, occasionally, it is important for you to automate everything they can: software updates, traffic filtering, or use other tools to help them improve online security. To enhance protection, you should be using a modern anti-malware solution that is mainly focused on detecting new malware antivirus products can’t easily block. Anti-malware software programs try to scan and detect new cyber attacks based on the data collected from the cybercriminals operation. In this graphic below you can the process for second-generation protection solutions to detect new threats. Malware is usually delivered via spam email with a malicious attachment or links that potential victims might click and get infected. Hackers can also use infected servers and domains to deliver the malware. 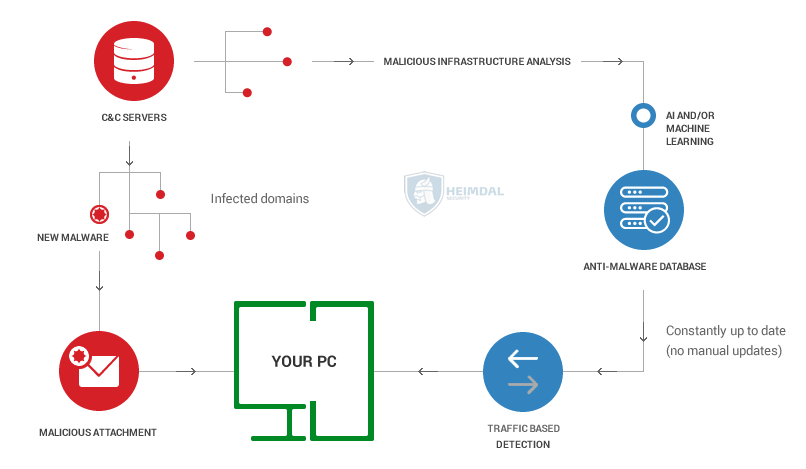 Think of cyber attacks like an iceberg that hits and causes unprecedented amount of damage for organizations and home users alike. There’s a lot going behind the scenes and you need a bunch of settings and legitimate software products to fight back and protect yourself against these advanced cyber attacks.
Think of cyber attacks like an iceberg that hits and causes unprecedented amount of damage for organizations and home users alike. There’s a lot going behind the scenes and you need a bunch of settings and legitimate software products to fight back and protect yourself against these advanced cyber attacks.
What can you do
You need to filter and sanitize your Internet traffic by eliminating various online threats that you can’t block without getting help. We recommend checking this list of 4 tools that can help you with web traffic filtering:
- Use a Virtual Private Network (VPN), which can anonymize Internet traffic and secure it through encrypted connections and communication. With the help of a VPN, you can reduce being exposed to cyber attacks.
- Enable your firewall, which is a network system designed to protect unauthorized access to public or private networks. If you have Windows system installed on your PC, you should use its own firewall for free and always on. Otherwise, we recommend using a firewall from a trusted source.
- Install a reliable antivirus program. Despite its reactive protection provided, it’s still useful to have a good AV software to help you with web traffic filtering. It might also block blacklisted websites and infected domains, keeping a malware infection away.
- Use a second generation anti-malware program to filter your web traffic and block advanced malware threats. A proactive cyber security solution can detect and stop online threats at different stages and provide multi layers of protection. They do that based on the type of infrastructure or infection detected in the first place, which is relatively easy to track.
When it comes to the threat landscape, malware authors have switched to more sophisticated attack vectors. When they launch a new attack, cybercriminals rely on innovative tactics and easily target businesses with an outdated infrastructure or software. It’s worth reminding how essential is for businesses to keep their infrastructure up to date and upgrade it. We all know the consequences: security data breaches, business disruption, sensitive data loss, financial damage and many more. Cyber attacks have been happening for many years now, because online criminals keep trying to gain access to a massive volume of users’ data, steal money or financial data, or simply disrupting business operations. What’s changed is the way they operate. Being more skilled and using new methods mean that they know which tactics (will) work. From exploiting a vulnerability in Windows system to changing the type of malware delivered (the case of (Non)Petya ransomware), from switching to new infection vectors to delay strain detection, to using auto-updating elements to automate new payload delivery or social engineering attacks, cybercriminals are getting better and better at spreading malware and infecting a large number of computers. There’s been a lot of talk about botnets used by online criminals for malicious purposes, and for a good reason. Botnets are a bigger problem than we can imagine. A botnet is a large network of compromised computers that are being controlled by online criminals to serve their malicious interests and avoid detection. Hackers use botnets to do a lot of things: launching massive attacks, deliver ransomware, spam or phishing emails and other malicious acts. [Tweet “To better secure your data, you need AV and other security layers to fight against cyber attacks”] For example, last year, the Mirai botnet launched one of the biggest DDoS attacks by compromising a major DNS provider that managed to take down big sites like Reddit, Airbnb, Twitter or Spotify. Last month, security researchers warn about the Reaper botnet, a new IoT botnet which seems to be larger than the popular Mirai. In terms of infrastructure used during cyber attacks, there’s been some infamous family of financial stealing malware like Zeus Gameover takedown used by cybercriminals to collect users’ financial information. It has been estimated that this financial malware has infected 1 million users around the world. Another example is the Angler exploit attack in which cybercriminals used two core techniques (domain hijacking and domain shadowing) to bring in new servers and IP addresses from users to grow their distribution network. In this type of attack, AV detection was generally low generating serious problems for businesses and public institutions in Europe and other places. These kind of cyber attacks keep happening and we’ll explain in the following spam campaigns behind-the-scenes why antivirus software has a low detection rate when it comes to new malware.
12 spam campaigns behind the scenes
Detection is still an issue for antivirus and antivirus software have fallen behind in terms of effectiveness, because they lack the ability to detect and remove second generation malware in a timely manner. We analyzed 12 different spam campaigns happening in specific days and the data found in VirusTotal indicated a low detection rate for AV engines during the first stages of an attack. 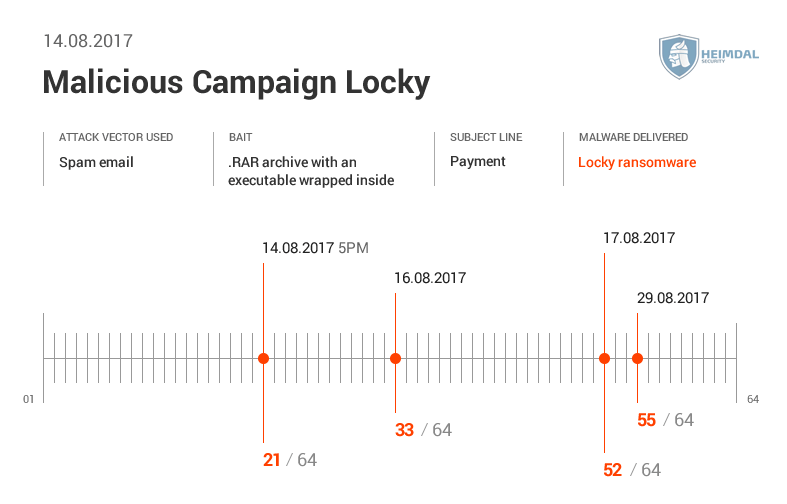 See here the data shown by VirusTotal and how many antivirus engines initially detected the spam campaign.
See here the data shown by VirusTotal and how many antivirus engines initially detected the spam campaign. 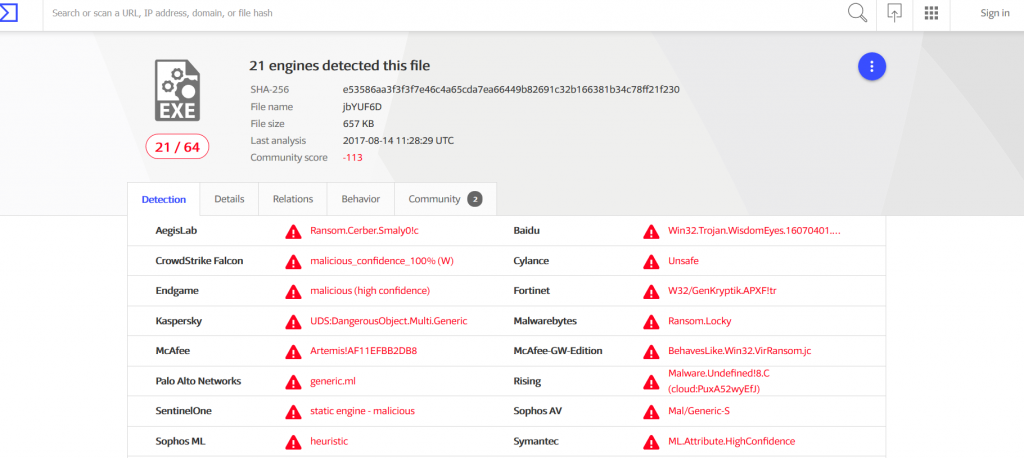
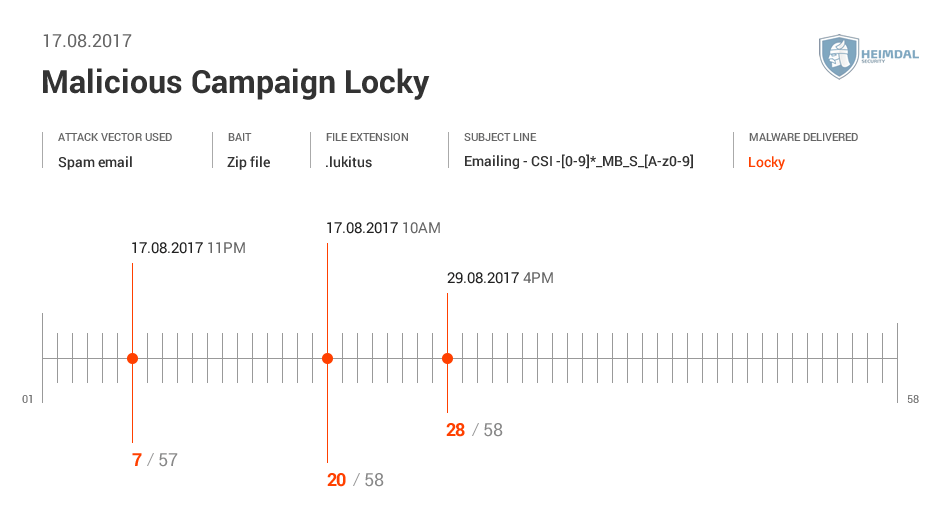 See more details from Virus Total below:
See more details from Virus Total below: 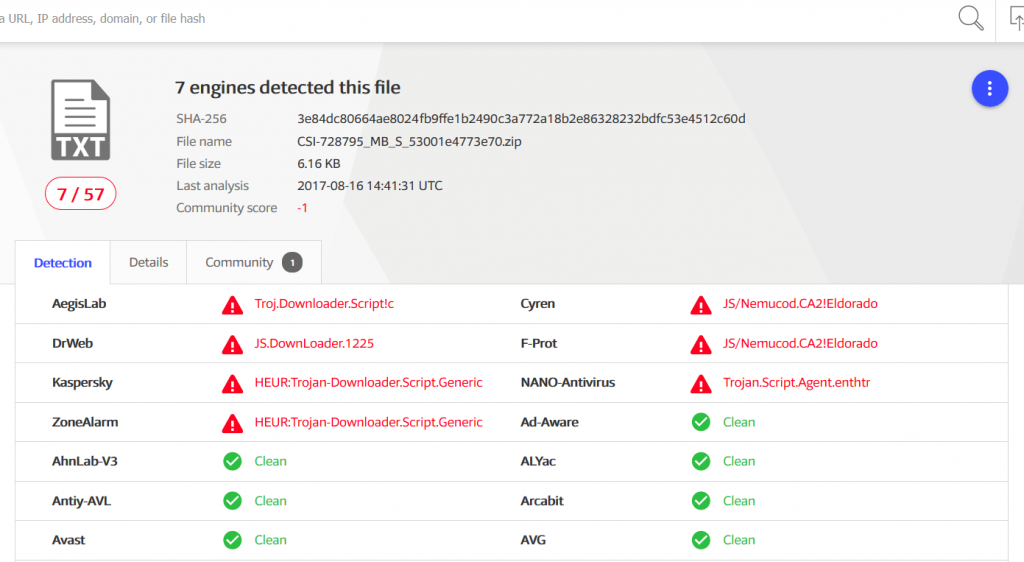
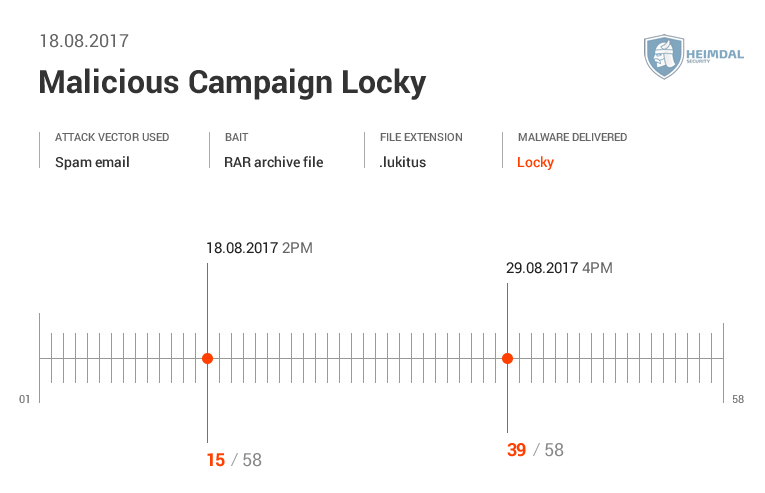 Data shown by Virus Total.
Data shown by Virus Total. 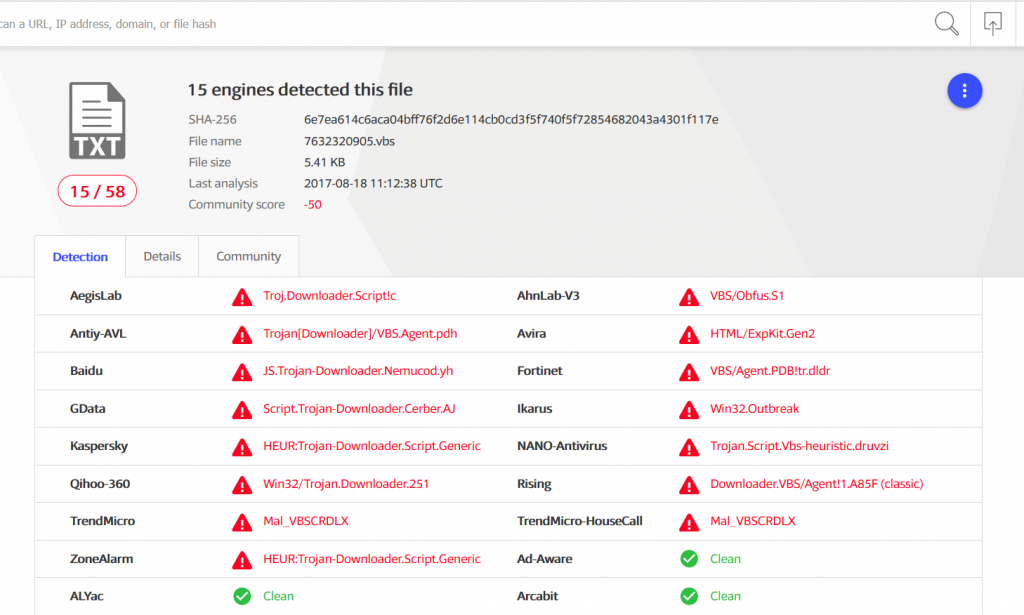
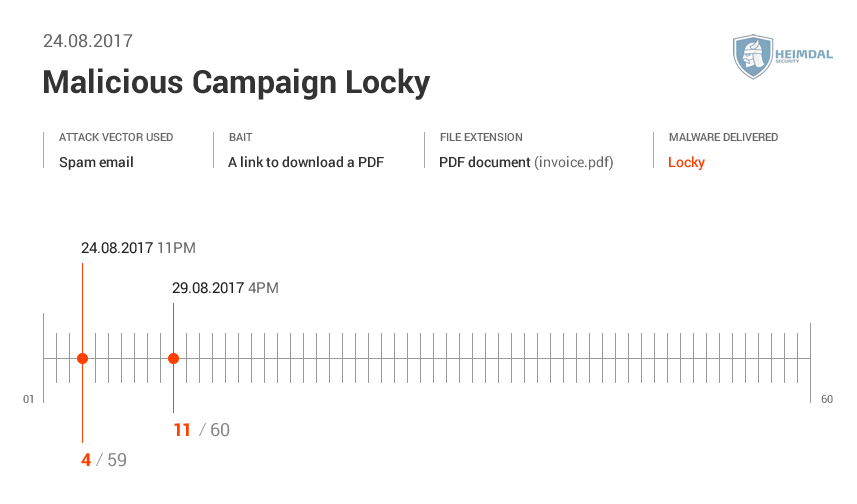 You can see below data from Virus Total and the number of AV engines detecting the spam campaign.
You can see below data from Virus Total and the number of AV engines detecting the spam campaign. 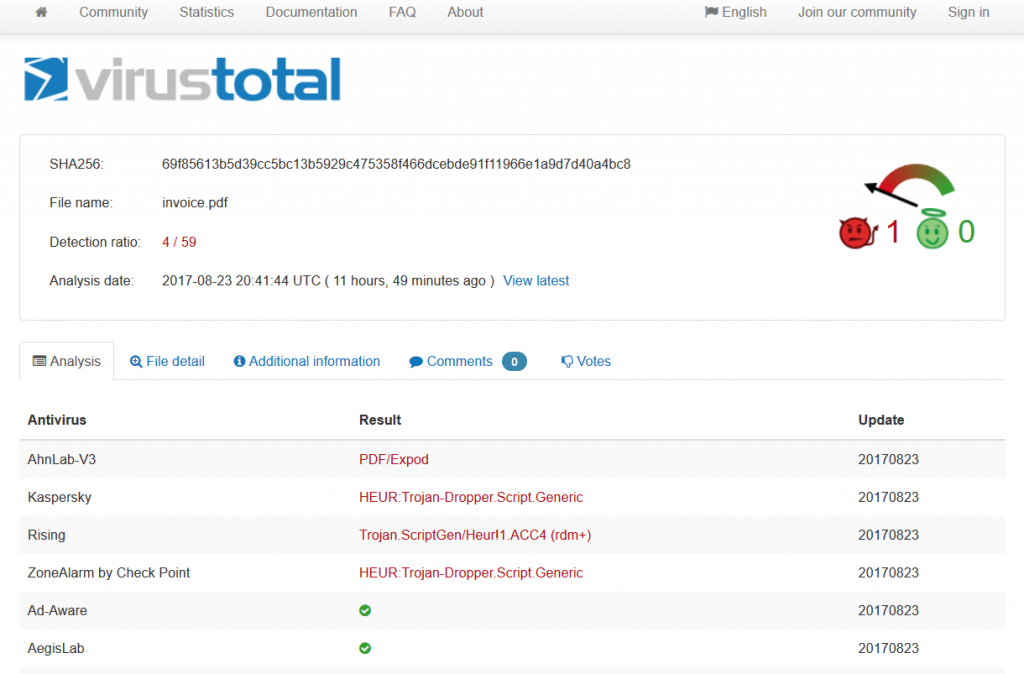
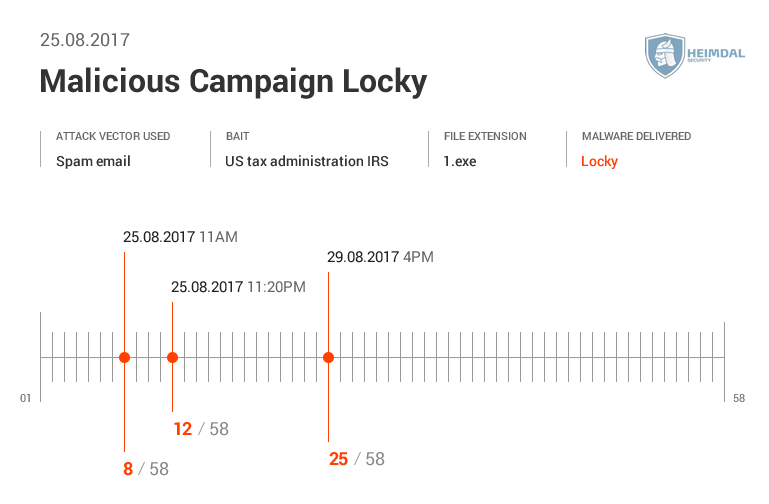
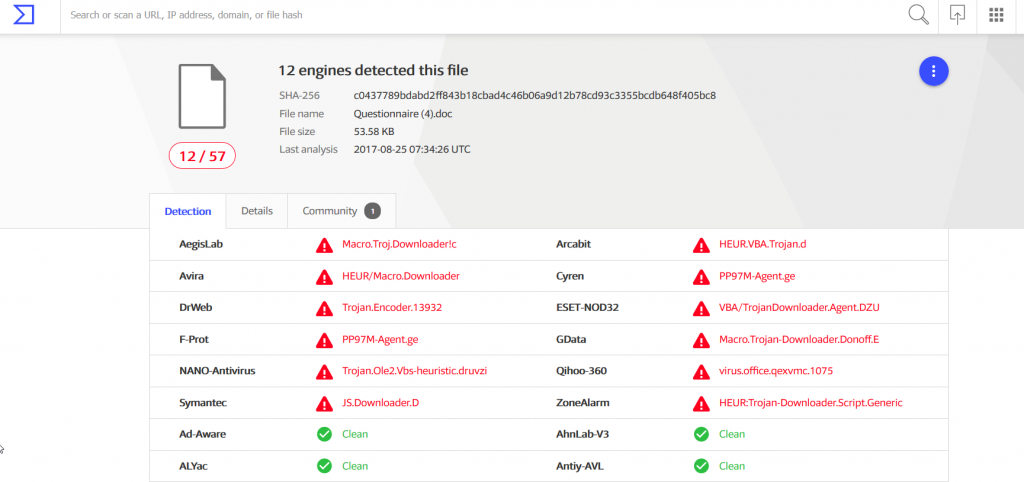
 Virus Total shows us how many AV engines detected this malicious spam campaigns.
Virus Total shows us how many AV engines detected this malicious spam campaigns. 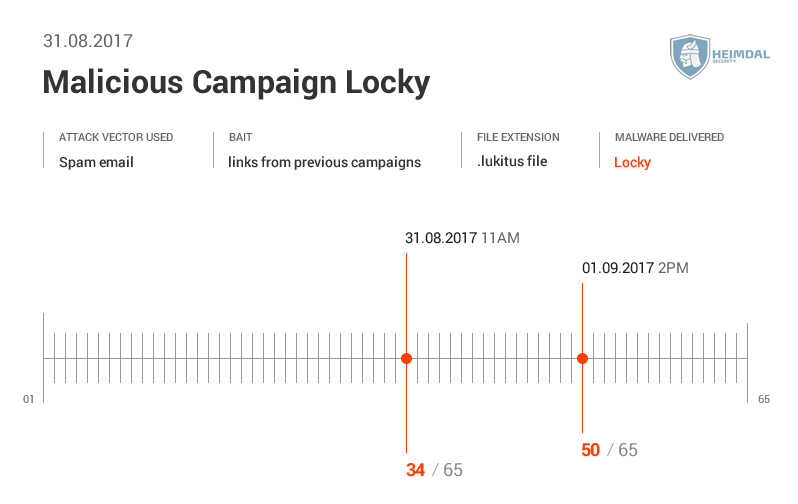 See more details from Virus Total here.
See more details from Virus Total here. 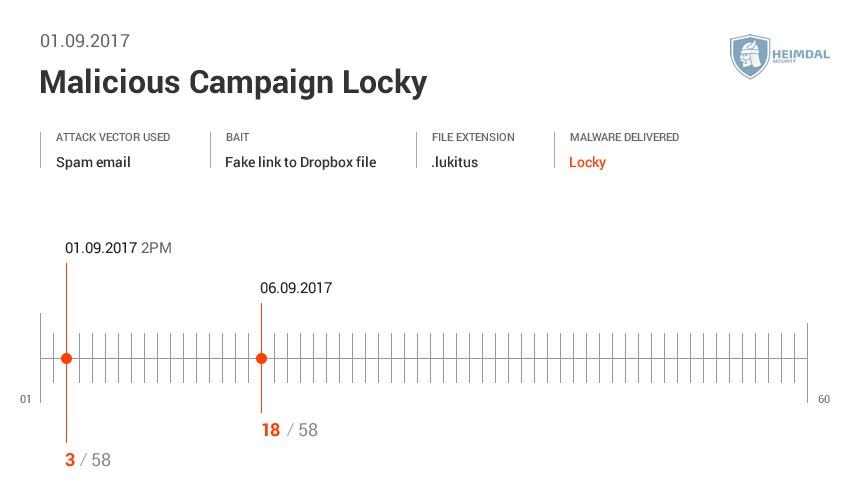 More details from Virus Total here
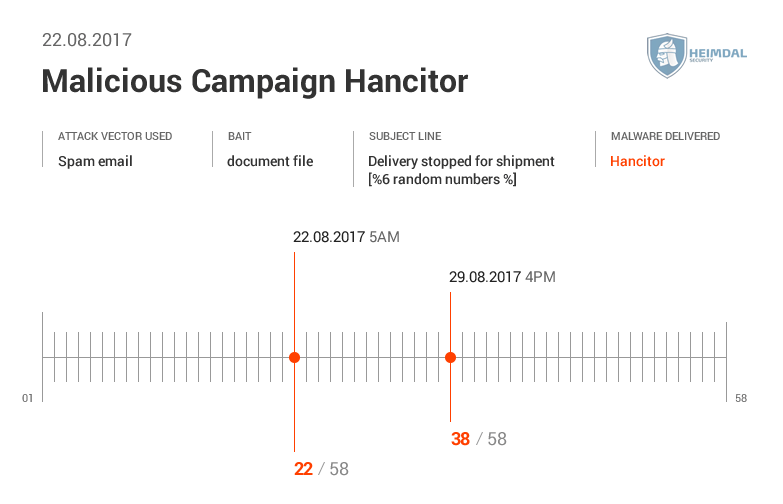
More details from Virus Total here 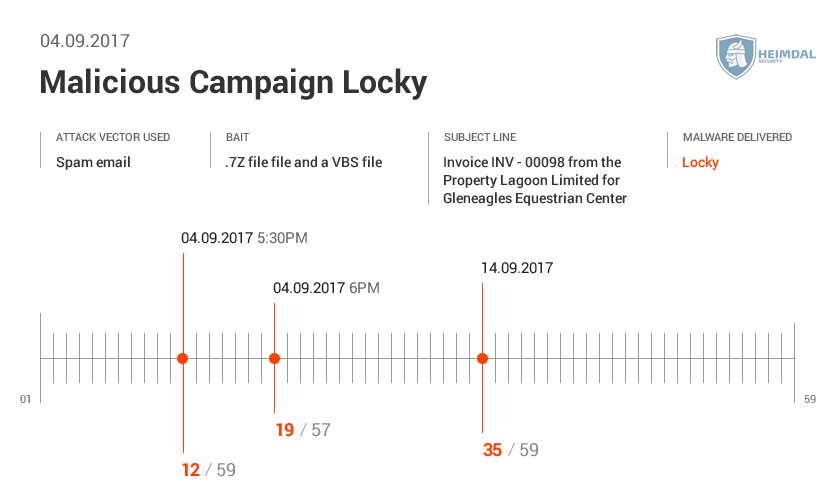 Here’s the AV detection rate by Virus Total.
Here’s the AV detection rate by Virus Total. 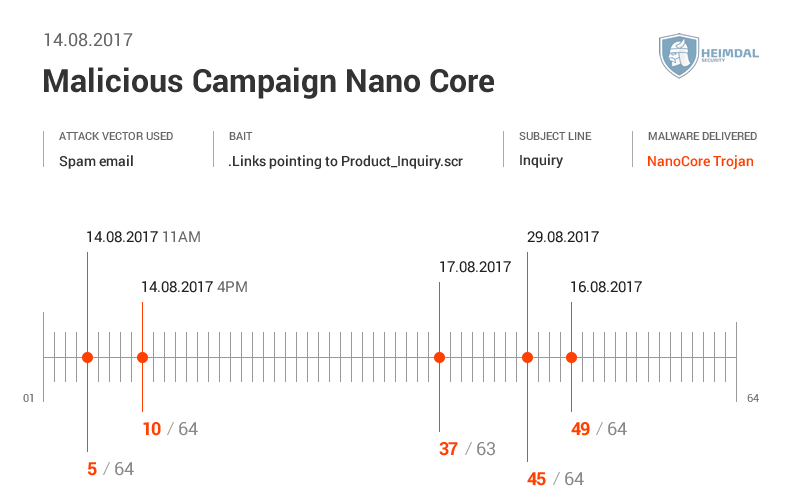 Virus Total gave us the following data:
Virus Total gave us the following data: 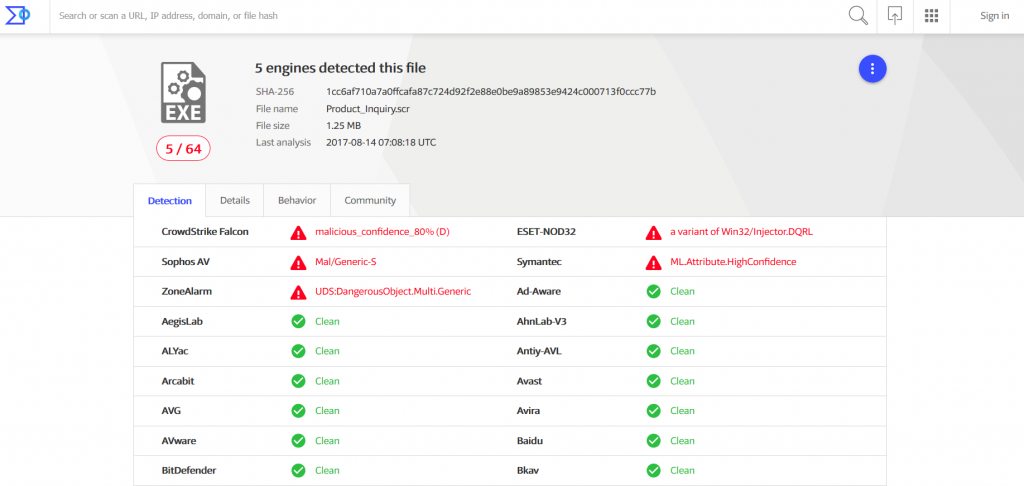
 See details here:
See details here: 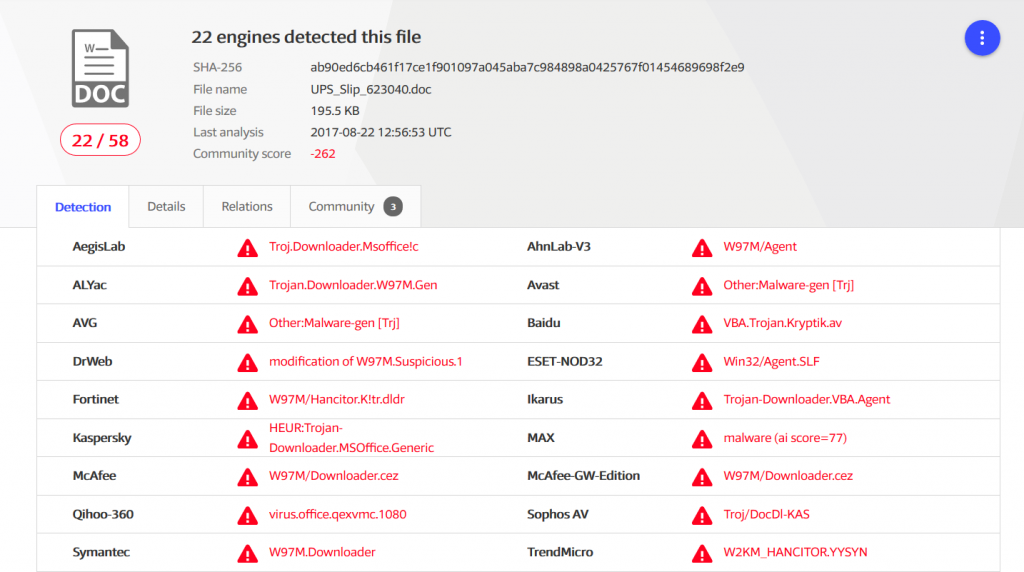
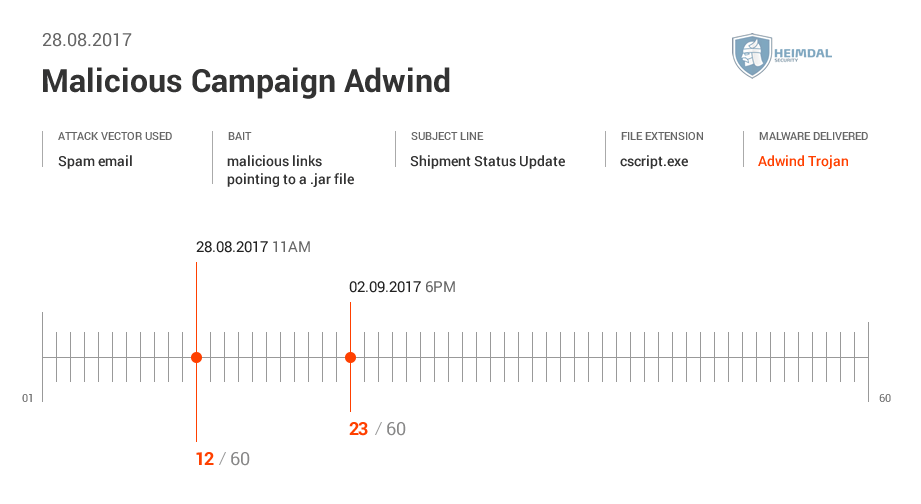 See the AV detection rate below:
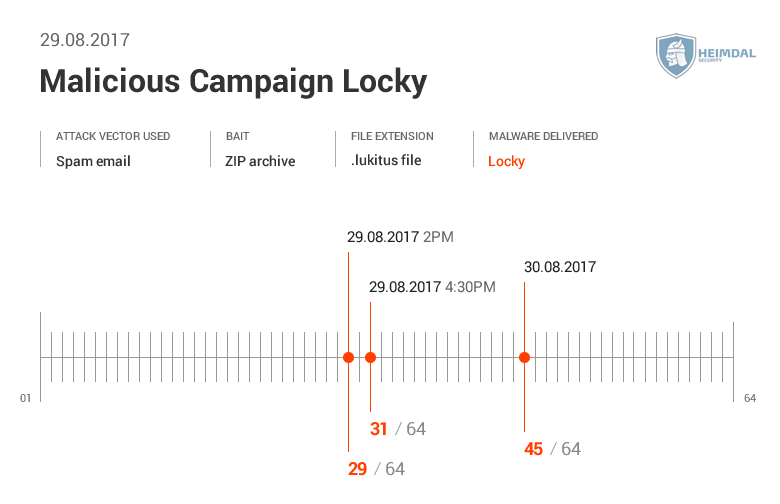
See the AV detection rate below: 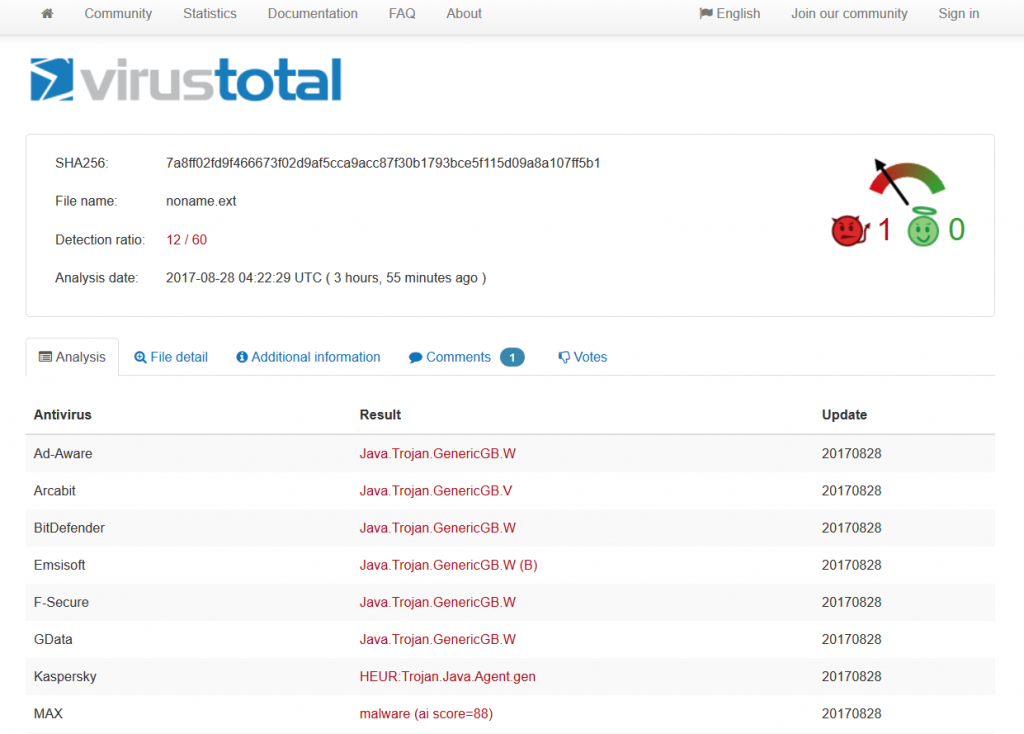 As seen in these pictures, it took AV at least two days to detect malware. During different malicious campaigns analyzed (Locky, Hancitor or Hancitor), it took antivirus products even more time (8 days, 12, or 29 days) to spot malware. During these days, plenty of things can happen: cybercriminals can harvest your financial data (online banking credentials, usernames, passwords, etc.), or they can encrypt data via a ransomware infection. Whether it’s 2 days, 8 or 12 days, time to detection is too much and reactive protection offered by AV is not enough. Why does that happen? Traditional antivirus products are mainly effective against known online threats, and the malware scanning is rather reactive than proactive. The older a malware strain is, the easier for AV is to detect it. This scenario doesn’t apply for new and advanced malware. AV might block websites and domains that are known to be infected, and keep malware infection at bay. However, cybercriminals move extremely fast and could change methods, making difficult for antivirus software to detect sophisticated malware strains and strengthen security. All these evasion tactics trigger low detection rates in antivirus products, which means that a proactive-based model is needed. To enhance online protection you should use a proactive cyber security solution. An antimalware program isn’t meant to replace the antivirus, but complement it, so users can benefit of multiple layers of protection to defend and stop the growing number of malware attacks. What these examples teach us? Both organizations and home users shouldn’t rely on a limited number of software products to keep their data safe and secure.
As seen in these pictures, it took AV at least two days to detect malware. During different malicious campaigns analyzed (Locky, Hancitor or Hancitor), it took antivirus products even more time (8 days, 12, or 29 days) to spot malware. During these days, plenty of things can happen: cybercriminals can harvest your financial data (online banking credentials, usernames, passwords, etc.), or they can encrypt data via a ransomware infection. Whether it’s 2 days, 8 or 12 days, time to detection is too much and reactive protection offered by AV is not enough. Why does that happen? Traditional antivirus products are mainly effective against known online threats, and the malware scanning is rather reactive than proactive. The older a malware strain is, the easier for AV is to detect it. This scenario doesn’t apply for new and advanced malware. AV might block websites and domains that are known to be infected, and keep malware infection at bay. However, cybercriminals move extremely fast and could change methods, making difficult for antivirus software to detect sophisticated malware strains and strengthen security. All these evasion tactics trigger low detection rates in antivirus products, which means that a proactive-based model is needed. To enhance online protection you should use a proactive cyber security solution. An antimalware program isn’t meant to replace the antivirus, but complement it, so users can benefit of multiple layers of protection to defend and stop the growing number of malware attacks. What these examples teach us? Both organizations and home users shouldn’t rely on a limited number of software products to keep their data safe and secure.
Protection guide against second generation malware
Keeping malware attacks under control is a challenge for many businesses. Same goes for home users who are vulnerable and easy targets to different cyber attacks. Malware threats are widespread and difficult to spot by anyone, so prevention is the best strategy to stay safe online. We recommend using these security measures to keep your sensitive data away from online criminals trying to steal it:
- Always keep your software up to date, including operating system and every application you may use on your device;
- Have a backup of your important data in at least two separate locations: an external drive and in the cloud;
- Do not open an email from the spam folder or click on suspicious links you might receive in your inbox’
- Remember to set strong and unique passwords with the help of a password manager system. This guide will help you everything you need to know about password security;
- Use a reliable antivirus program as a basic protection for your device, but also consider including a proactive cyber security solution as a second layer of defense to secure your data and block most attacks;
- Always secure your browsing while navigating the Internet and click on websites that include only HTTPS certificate;
- Teach yourself (and master basic cyber security) to detect potential online threats delivered via emails, social engineering attacks or other methods;
The low detection rates for AV found in these spam campaigns have shown us that AV can’t sometimes keep up with the high number of malware threats rising every day. An antivirus solution alone is not enough to keep users safe. For better online safety, you need to add security layers to fend off the rise of advanced cyber attacks. Let’s keep in mind that the impact of these low detection rates for AV along with the prevalence of software monocultures system have their risks. If everyone is using the same OS, apps, or network protocol, and security vulnerabilities are being discovered, it will impact everyone and could potentially lead to massive cyber attacks. Let’s not forget that the increasing amount of security holes in some of the most used apps is a great opportunity for cyber criminals to exploit. They take advantage of everything and easily target everyone. We all know the consequences: security data breaches, business disruption, sensitive data loss, financial damage and many more. How do you keep your computer protected? Using any proactive security solution besides antivirus to secure your data from cyber attacks? Let us know your thoughts in a comment below.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










