Contents:
When it comes to banking malware and all the variants of credentials-stealing Trojans, we agree that there are simply too many out there that you need to pay attention to, so we organized a list of the most dangerous. What you’ll find below is a short presentation for some of the most advanced banking Trojans on the web and prevention strategies you can use to stay safe.
Let me start by clarifying our key notions – malware, Trojan, banking malware:
What Is a Banking Malware and How Does It Work?
Ergo, a banking Trojan/banking malware represents a malicious computer program that tries to obtain access to confidential information which is stored or processed through online banking systems, while operating just like the Trojan horse from Troy’s legend.
Banking Trojans disguise as innocent applications, but they’re actually trying to steal information and avoid being detected by “having dormant capabilities, hiding components in other files, forming part of a rootkit, or using heavy obfuscation.”
Banking malware is “built with a backdoor, allowing outside parties to gain access to a computer, or it may instead copy a bank client’s credentials by spoofing a financial institution’s login webpage”.
The term malware is a general one, it is the short version for malicious software and refers to “software that is defined by malicious intent. This type of ill-intentioned software can disrupt normal computer operations, harvest confidential information, obtain unauthorized access to computer systems, display unwanted advertising, and more.”
Trojan, another term that will often appear in this article, is
any type of malicious program disguised as a legitimate one. Often, they are designed to steal sensitive information (login credentials, account numbers, financial information, credit card information, and the like) from users. Trojan malware takes its name from the classic Trojan horse ploy from the war between the Greeks and the independent city of Troy. The ancient Greeks were able to defeat the city of Troy by hiding soldiers inside a giant wooden horse they left behind as a gift while they feigned retreat following a 10-year war. Little did the Trojans realize that by taking the horse as a trophy of war, they were bringing an elite Greek fighting force right inside the walls of their city, ultimately leading to the fall of Troy. A malicious gift thus became known as a Trojan Horse.
Here’s the list of the most dangerous banking malware families and what you can do to avoid becoming their next victim!
Notable Banking Malware Families
1. Zbot/Zeus
Zeus, also known as Zbot, is a notorious Trojan that infects Windows users and tries to retrieve confidential information from the infected computers. Once it is installed, it also tries to download configuration files and updates from the Internet. The Zeus files are created and customized using a Trojan-building toolkit, which is available online for cybercriminals.
Zeus has been created to steal private data from the infected systems, such as system information, passwords, banking credentials, or other financial details and it can be customized to gather banking details in specific countries and by using various methods. Using the retrieved information, cybercriminals log into banking accounts and make unauthorized money transfers through a complex network of computers.
2. Zeus Gameover
Zeus Gameover is a variant of the Zeus family – the infamous family of financial stealing malware – which relies upon a peer-to-peer botnet infrastructure. The network configuration removes the need for a centralized Command and Control server, including a DGA (Domain Generation Algorithm) which produces new domains in case the peers cannot be reached. The generated peers in the botnet can act as independent Command and Control servers and can download commands or configuration files between them, finally sending the stolen data to the malicious servers.
Zeus Gameover is used by cybercriminals to collect financial information, targeting various user data from credentials, credit card numbers, and passwords to any other private information which might prove useful in retrieving a victim’s banking information. Zeus Gameover is estimated to have infected 1 million users around the world.
3. SpyEye
SpyEye is a data-stealing malware (similar to Zeus) created to steal money from online bank accounts. This malicious software is capable of stealing bank account credentials, social security numbers, and financial information that could be used to empty bank accounts.
This banking Trojan contains a keylogger that tries to retrieve login credentials for an online bank account. The attack toolkit is popular among cybercriminals because it can be customized to attack specific institutions or target certain financial data.
SpyEye can start a financial transaction as soon as a targeted user initiates an online operation from his bank account.
4. Shylock
Shylock is a banking malware designed to retrieve user’s banking credentials for fraudulent purposes. As soon as it is installed, Shylock communicates with the remote Command and Control servers controlled by the cybercriminals, sending and receiving data to and from the infected PCs. Like Zeus Gameover, this malware uses a (DGA) Domain generation algorithm to generate several domain names that can be used to receive commands between the malicious servers and the infected systems.
The Trojan is delivered mostly through drive-by downloads on compromised websites and via malvertising, where malicious code is inserted in adverts that are then placed on legitimate websites. Another popular method of spreading this financial malware is by inserting malicious JavaScript into a web page. This technique produces a pop-up that pushes the user to download a plugin, apparently necessary for the media display on the website.
5. DanaBot
First emerged in the middle of 2018, DanaBot is a banking Trojan that started by targeting Australian users, but then moved to European banks and email providers, and also US companies.
DanaBot banking malware has multiple variants and functions as malware-as-a-service, with a number of active affiliates that keeps growing. The original multi-stage infection used to start “with a dropper that triggers a cascading evolution of hacks. These include stealing network requests, siphoning off application and service credentials, data exfiltration of sensitive information, ransomware infection, desktop screenshot spying, and the dropping of a cryptominer to turn targeted PCs into cryptocurrency worker bees.”
6. TrickBot
TrickBot malware targets the user’s financial information and usually spreads through malicious spam emails. Its first main targets were banks from Australia, the UK and Canada, but also Germany and US credit card companies and CRM providers.
Originally a banking Trojan, TrickBot has evolved “into highly modular, multi-stage malware that provides its operators a full suite of tools to conduct a myriad of illegal cyber activities.” It is known to use man-in-the-browser attacks to obtain information like login credentials and can use macros in Excel documents for downloading and deploying malware on the users’ devices.
7. Panda
Panda is a banking Trojan that uses many of the Zeus’s malware techniques like man-in-the-browser and keylogging, but has advanced stealth capabilities. A Panda attack can begin with spam messages that contain malicious attachments.
This banking malware’s target list goes beyond financial services institutions – even some cryptocurrency exchanges and social media websites fell victims in 2018. Cryptocurrency exchanges are appealing targets not only because more and more people are interested in cryptocurrency, but also because “unlike with a bank robbery or credit card theft, there may not be a central authority that can undo malicious transactions. Once you lose your money and the transaction goes on the blockchain, it’s likely gone forever.”
8. GozNym
GozNym was a hybrid banking malware that started by targeting Polish banks, but then spread all over the world, from Canada to Japan, from Spain to Brazil. Its operators captured login credentials to gain access to their victims’ online banking accounts, and then stole money and laundered the funds using American and foreign beneficiary bank accounts.
GozNym banking malware was taken down in an “unprecedented, international law enforcement operation”, when Europol conducted searches in Moldova, Bulgaria, Ukraine and Georgia. However, although many distributors have been arrested, the GozNym threat is still active in the sense that parts of the banking malware can still reappear in new forms.
9. Kronos
Kronos is another name that echoes the Greek Mythology, where Kronos was known as the father of Zeus. Kronos banking malware is one of the most sophisticated Trojans, whose code is obfuscated using a multitude of techniques.
Like Zeus, Kronos focused on stealing banking login credentials from browser sessions using a combination of web injections and keylogging and targeted countries like Poland, Germany and Japan.
Recent research in the malware field shows that Kronos was rebranded and is now being sold as the Osiris banking Trojan.
10. Bizzaro
Bizzaro is one of the latest banking Trojans, currently “sweeping through Europe and large parts of South America, attempting to pilfer consumer financial information and mobile crypto wallets as it goes.” Many of the victims of this banking Trojan are from Italy, France, Spain and Portugal, but Bizzaro is thought to have originated in Brazil.
The malware spreads “either via malicious links contained within spam emails, or through a trojanized app.” After installing malware on the targeted device, the cybercriminals’ complex backdoor will allow them to use keystroke loggers to gather personal login information, but also command the victim’s crypto wallet.
What Is the Typical Spreading Method for Banking Malware?
Most dangerous pieces of financial malware are usually distributed through:
The user receives an e-mail message from a well-known organization with some false banking information attached or with a link included in the e-mail. The system becomes infected when the user clicks the link or downloads the file attached to the e-mail, usually disguised as an important invoice or job offer.
- drive-by downloads
A drive-by download occurs when the user visits a website or clicks a deceptive pop-up window.
A diagram of the typical spreading method of financial malware can be seen below:
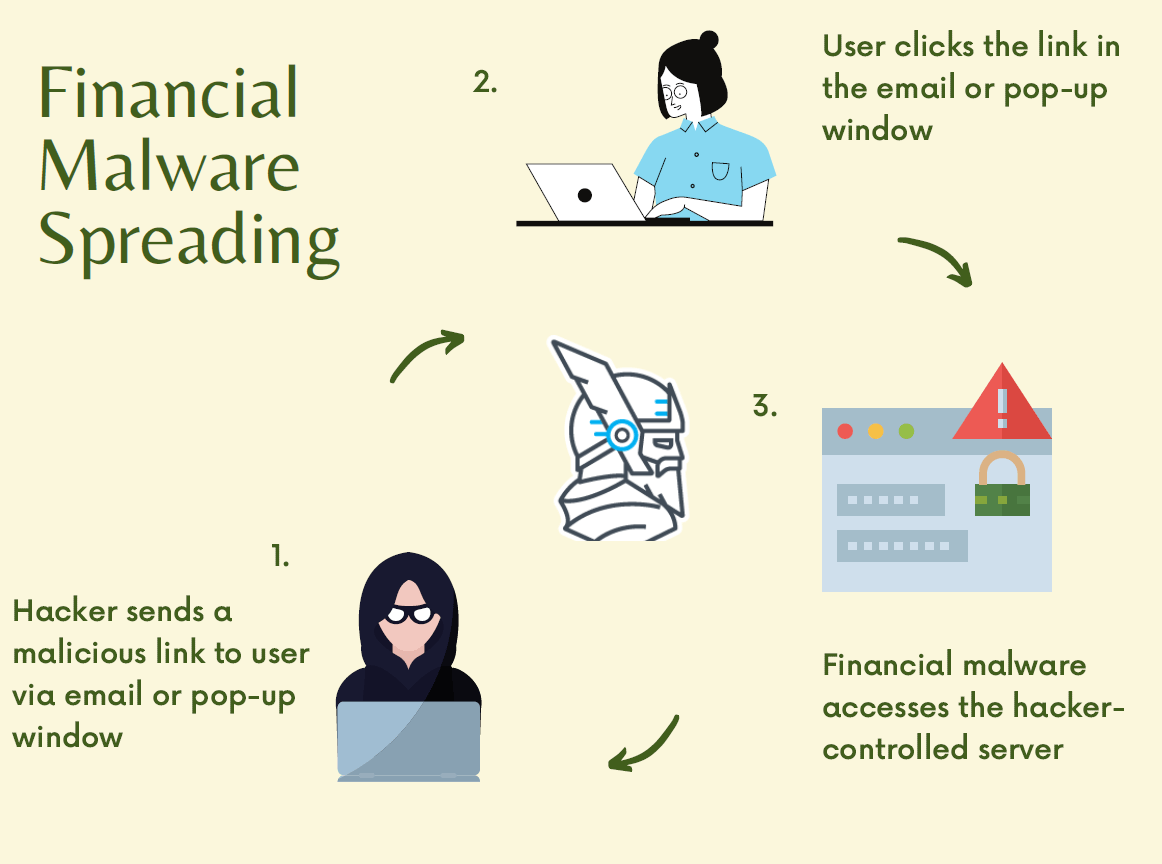
How Does a Typical Financial Attack Look Like?
We will start from the point where a normal machine is already infected by credentials stealing malware. As I mentioned before, the machine may have become infected through:
- an e-mail attachment (or an e-mail link)
- a drive-by download (which occurs when visiting a website)
- a deceptive pop-up window.
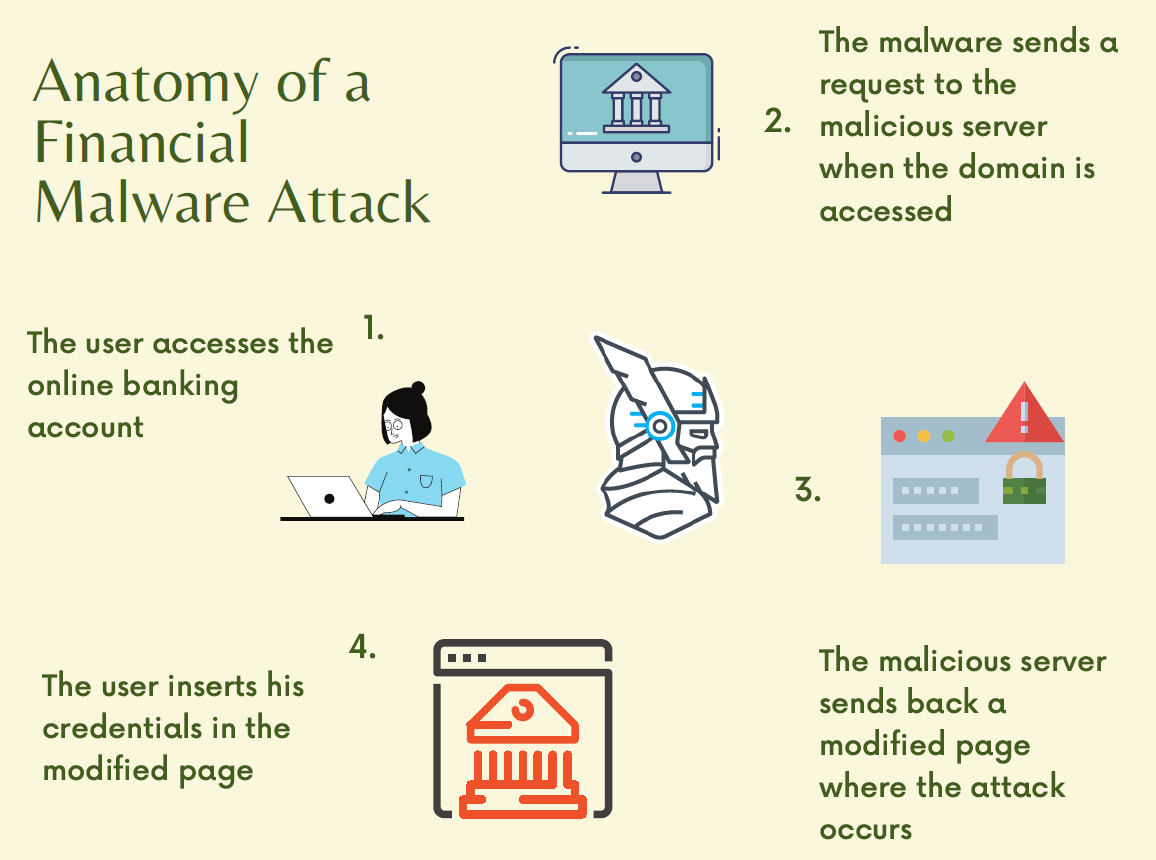
The steps that usually occur in a typical financial attack are the following:
- The user accesses his online banking account. The domain is specified in the configuration file downloaded by the malware from the malicious servers controlled by the hackers.
- The malware sends a request to the malicious servers controlled by cybercriminals and lets them know the user is trying to access the domain specified in the configuration file.
- The malicious server specifies a page on the online banking account – usually the login page – where the attack should occur.
- When the user accesses the specified page, the malware sends a request to the malicious server, sending back a modified page into the user’s browser. The modified page should trick the user into believing he enters his credentials in the normal page of the online banking account.
- The modified page (the login page in our case) asks for the user’s sensitive information, such as credentials for the online banking websites or the credit card number.
Here’s a diagram for a typical financial malware attack:
This is just a typical attack used by IT criminals, but their means and tools vary from stealing the credentials through the classical method of using a keylogger software to withdrawing money directly from the online banking account.
Indicators of Compromise
How can you tell that your devices have been affected by banking malware? Well…
Users might notice that:
- browsers load pages very slowly;
- the computer’s start-up is slow, and no application seems to perform as it should;
- the computer opens programs that they didn’t open or repeatedly closes programs;
- banking web pages may have extra fields that ask for credit card numbers or PINs in new or unexpected forms;
- the login fails, even if they use the right passwords.
Enterprise owners and their employees might deal with:
- unexpected pop-up windows;
- files missing;
- hijacked emails or accounts;
- malfunctioning of antivirus solutions;
- slow applications;
- active computer processes, even if no one is using the device.
How to Protect against Banking Malware
Now that we’ve clarified what banking malware is, how it works and learned about some of the most dangerous Trojan families that are lurking on the Internet, it’s time to also learn what we can do to stay safe.
What can users do?
- make sure all the software they use is always up to date;
- always download applications and files from secure sources;
- use two-factor authentication whenever possible and all the security features that their online banking service offers;
- use a secure browser when they shop online or visit banking websites;
- use a password manager to avoid physically typing in the login credential since, as we have seen, many banking Trojans pay particular attention to keystrokes;
- learn how to identify fake websites and phishing emails – any security awareness program should help you with that;
- use traffic filtering solutions for extra safety.
What can enterprises do?
- provide security awareness training for all their employees;
- install a privileged access management solution to make sure no intruder can access their IT infrastructure;
- change the email addresses of the employees that (might) have been targeted;
- install a web application firewall;
- deploy a traffic filtering solution that can spot even hidden threats and log your network traffic.
Heimdal® Network DNS Security
Final Thoughts
If you were wondering “Can malware access my bank account?” or “Can malware get my info on phone?”, the answer is yes. Cybercriminals use a multitude of techniques to infect your devices with banking malware in order to get access to your information and money.
For this reason, we recommend, as always, security awareness and prevention as the best ways to keep malicious actors away.
However you choose to proceed, please remember that Heimdal™ Security always has your back and that our team is here to help you protect your home and your company and to create a cybersecurity culture to the benefit of anyone who wants to learn more about it.
This post was originally published by Andra Zaharia and updated by Elena Georgescu in July 2021.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security











