Contents:
Halfway through 2016, cyber criminals are starting to focus on a new weapon in their arsenal. This is a new piece of software they can manipulate to spread malware and infect thousands. Its name: JavaScript. Exploiting JavaScript in cyber attacks is not exactly new, but the increasing frequency of this attack vector is. Even in the odd 2020, JavaScript-based attacks are still a matter of great concern. This trend piqued the interest of many security researchers, including our team’s. The danger in these attacks lies in one key aspect: malware delivered via infected JavaScript files doesn’t need user interaction. Better said, a user like you or me could get infected with malware without doing anything else than browsing a website. So we made it our mission to explain JavaScript malware in simple terms, so anyone can learn how to protect their data against this threat. This security guide includes 6 parts from which non-technical users can:
- Learn the difference between Java and JavaScript
- Understand how JavaScript malware works
- Find out why cyber criminals are focusing on JavaScript attacks
- Discover how JavaScript malware spreads
- Learn about the types of malware that target JavaScript for distribution
- Find out how to protect yourself from malware that uses JavaScript
1. Learn the difference between Java and JavaScript
First of all, we have to get the terms right. Most users are often confused by Java and JavaScript, because of their similar names. This lack of creativity in naming gave me some trouble too, so it’s time we set the record straight, once and for all!
 And this is what JavaScript files look like on your PC (it has the .js extension):
And this is what JavaScript files look like on your PC (it has the .js extension): 
2. Understand how JavaScript malware works
Now that you know what JavaScript is, it’s time you found out how cyber criminals abuse this programming language in their attacks. The key takeaway is that JavaScript allows website creators to run any code they want when a user visits their website. Naturally, website developers can be either good or bad. What’s more, cyber criminals frequently manipulate the code on countless websites to make it perform malicious functions. However, JavaScript is not an insecure programming language. It’s just that code bugs or improper implementations can create backdoors which attackers can exploit. So here’s how it all happens. When you’re browsing a website, a series of JavaScript (.js) files are downloaded on your PC automatically. These files are executed through your browser, so you can:
- see the content of the website you’re on
- perform various actions (example: fill out a form or download a file from a website)
- see the online ads (banners) on that website, etc.
Because online browsing is one of the strongest online habits that users have, cyber criminals target exactly that. Online attackers frequently redirect users to compromised websites. These can be either created by them or they can be legitimate websites they’ve hacked into. According to Sophos, “82% of malicious sites are hacked legitimate sites”! Source: Naked Security blog by Sophos What defines an infected website is that:
- cyber criminals have injected malicious JavaScript code in the website
- attackers have compromised, through malicious JavaScript code, the online ads/banners displayed on the website
- online criminals have injected malicious JavaScript code into the website’s database
- cyber attackers have loaded malicious content or malicious software from a remote server.
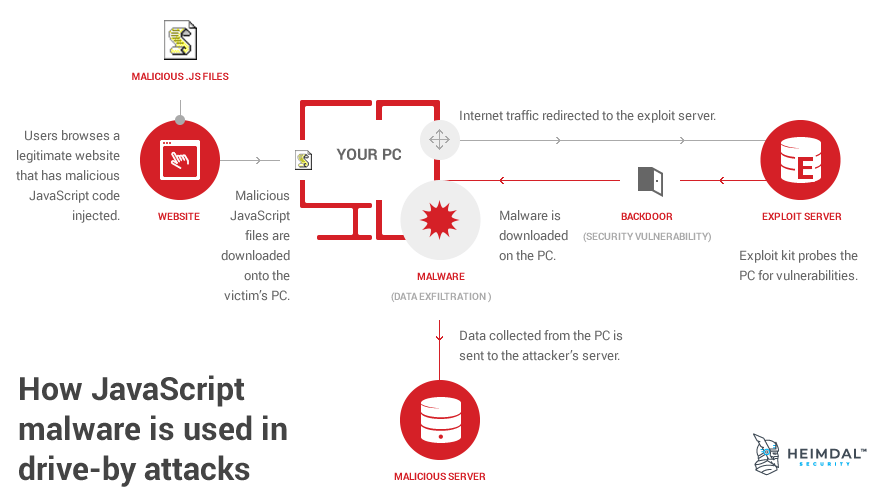
Consequently, malicious JavaScript files will be downloaded onto your PC when you unknowingly browse an infected website. This is called a drive-by attack and it generally includes 9 stages:
- You, as a user, unwittingly browse the compromised website.
- The malicious JavaScript files are downloaded on your system.
- They are executed through your browser, triggering the malware infection.
- The infected JavaScript files silently redirect your Internet traffic to an exploit server.
- The exploit kit used in the attack (hosted on the exploit server) probes your system for software vulnerabilities.
- Once the exploit finds the vulnerability, it uses it to gain access to your PC’s functions.
- This grants the exploit kit the right to execute code and download additional files from the Internet with administrator privileges.
- In the next step, malware will be downloaded onto the PC and executed.
- The malware can perform damaging functions on the PC. It can also collect information from the infected system and send it to the servers controlled by cyber criminals.
It takes just seconds for all this to happen! And you don’t have to click on anything to set off the malware infection chain. All my friends had a difficult time believing me when I first told them about this type of malware attack, but it still happens all the time. So I understand if you’ll want to read this twice before accepting it as a true fact. Another aspect that can make anyone anxious about drive-by attacks is that they’re invisible for the user. All the stages I just described happen in the background and they unfold incredibly fast! The story doesn’t end here though! Not if you want to learn how to get protected against JavaScript malware. Let’s get inside the mind of cyber criminals for a minute.
3. Find out why cyber criminals are focusing on JavaScript attacks
As you probably know by now, cyber criminals are eager to get their hands on two things: money and data. Hacking websites is a method that attackers can use to reach millions of unsuspecting users fast and at a low cost. Gone are the days when online criminals infected websites just to prove their skills. They’re not even interested in the notoriety that comes with hitting high-profile targets anymore. Compromising websites has proven its effectiveness in many occasions. JavaScript is just one of the next big things in cyber crime. One statistic will help you understand the huge opportunity that online attackers see:
JavaScript is used by 93.6% of all the websites.
Source: w3techs.com  Today’s web heavily relies on JavaScript to display content and help users all over the world do more things online. We just couldn’t use the web as we do without this programming language and its features. It would be foolish of malware creators to pass on this huge money-making opportunity! The recipe sounds simple: cyber criminals compromise high-traffic, legitimate websites and use them to redirect users to malicious web pages. The victims have no idea what’s going on, so malware spreads to millions of PCs. The infection often ties these PCs into a botnet, later used to fuel other attacks. And the cycle goes on and on and on… The reason behind the spike in interest for using JavaScript in malware attacks is that it’s easier to hide traffic redirects using these files. This growing tendency to use JavaScript in malware infections from the past few years is making a huge impact now.
Today’s web heavily relies on JavaScript to display content and help users all over the world do more things online. We just couldn’t use the web as we do without this programming language and its features. It would be foolish of malware creators to pass on this huge money-making opportunity! The recipe sounds simple: cyber criminals compromise high-traffic, legitimate websites and use them to redirect users to malicious web pages. The victims have no idea what’s going on, so malware spreads to millions of PCs. The infection often ties these PCs into a botnet, later used to fuel other attacks. And the cycle goes on and on and on… The reason behind the spike in interest for using JavaScript in malware attacks is that it’s easier to hide traffic redirects using these files. This growing tendency to use JavaScript in malware infections from the past few years is making a huge impact now.
4. Discover how JavaScript malware spreads
There are 8 main ways in which JavaScript is used to spread malware in current cyber attacks:
1. Malicious JavaScript code injections in legitimate websites – used to redirect users to malware-laden websites or to exploit servers that trigger malware infections. Here’s a notorious example:
A stored cross-site scripting (XSS) vulnerability in Yahoo Mail that affects more than 300 million email accounts globally was patched earlier this month, bagging a $10,000 bug bounty for the researcher who discovered it. The flaw allowed malicious JavaScript code to be embedded in a specially formatted email message. The code would be automatically evaluated when the message was viewed. The JavaScript could be used to then compromise the account, change its settings, and forward or send email without the user’s consent.
Source: InfoSecurity Magazine
2. Hidden iFrames – that load JavaScript malware from compromised sites, malware which then tries to execute code in the browser to infect the PC.
3. Malicious JavaScript code injections in online advertising networks – which appears in online banner ads and also silently redirect users to malicious web locations.
4. Drive-by downloads – which use infected JavaScript files to launch malware infections.
5. Malicious JavaScript attachments – which are ran through a Windows program and can trigger insidious infections outside the browser.
Unfortunately, once a .JS file has been saved to your hard disk, Windows will run it by default outside your browser, using a system component called WSH, short for Windows Script Host. A standard system program called WScript.exe (or its companion, CScript.exe, for command-line scripts with no graphical interface) will load your script, feed it into WSH, and then run it with all the power that a regular executable program would enjoy.
Source: Naked Security blog by Sophos
6. Infected downloads triggered through compromised JavaScript code injects – such as fake antivirus products, which are one of the most common scams on the Internet. These can compromise your system beyond the point of no return.
7. Browser add-ons and plugins – these can be either infected or they can load external content loaded with malware from external sources.
8. Fake software pop-up messages – that cyber crooks can easily forge to look real and convincing. Statistically, online attacks are the number one vector for malware infections right now. As you can see, cyber criminals don’t lack methods of carrying out their compromise attempts. But we, as users, don’t lack in defensive methods either. So keep reading for the must-have protection solutions against JavaScript malware. [Tweet “How JavaScript #malware works and what you can do about it:”]
5. Learn about the types of malware that target JavaScript for distribution
As widely used as JavaScript is, there’s plenty of malware to be scattered through it. Online criminals are very good with keeping up with the times. They quickly created the first ransomware developed 100% in JavaScript, called Ransom32:
However, a new strain called Ransom32 has a twist: it was fully developed in JavaScript, HTML and CSS which potentially allows for multi-platform infections after repackaging for Linux and MacOS X. Using JavaScript brings us one step closer to the “write-once-infect-all” threat, which is something to be aware of.
Source: IT Portal Six months later, a new ransomware strain called RAA appeared. It featured a dumfounding feature:
The JavaScript doesn’t download the ransomware, it is the ransomware. […] No additional software is downloaded, so once the JS/Ransom-DDL malware file is inside your network, it’s ready to scramble your data and pop up a ransom message all on its own.
Source: Naked Security blog by Sophos But ransomware isn’t the only type of malware that infected JavaScript files can spread. Other types of malicious software distributed via this vector include financial malware (Shylock, for example) or malware that ties affected PCs into botnets. Once the attackers manage to inject their code into a website or manipulate existing code to their intent, they can feed victims’ PCs with any malware they want.
6. Find out how to protect yourself from malware that uses JavaScript
Every day users can apply some simple rules to be safer against JavaScript malware as well as other threats. These rules include:
- Keep your software updated at all times (your browsers, apps, operating system, etc.)
- Use a strong antivirus product with extensive capabilities
- Install a traffic filtering solution that can ensure proactive security
- Never click on links in unsolicited emails (spam)
- Never download and opening attachments in spam emails
- Keep away from suspicious websites.
And if you want to go the extra mile, here’s a setting you can adjust in your Chrome browser:
If you’d like to turn JavaScript off or on for all sites:
- Click the Chrome menu Chrome menu in the top right hand corner of your browser
- Select Settings
- Click Show advanced settings
- Under the “Privacy” section, click the Content settings button.
- In the “Javascript” section, select “Do not allow any site to run JavaScript” or “Allow all sites to run JavaScript (recommended)”
Source: Chrome Help 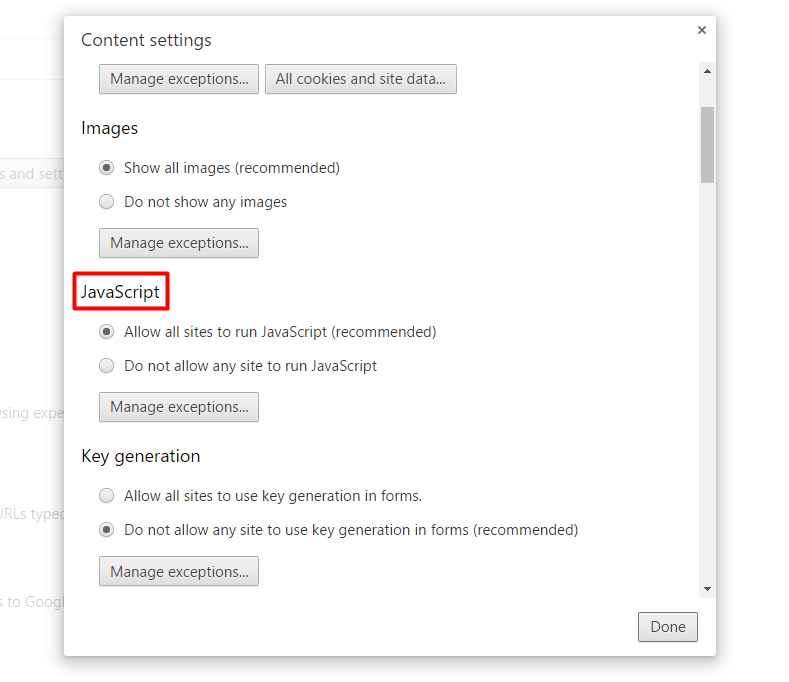 If you choose “Do not allow any site to run JavaScript”, you’ll be able to set some exceptions for trusted websites, so you can enjoy those to the fullest. If you’re a Firefox user, you can try the NoScript extension: The NoScript Firefox extension provides extra protection for Firefox, Seamonkey and other mozilla-based browsers: this free, open source add-on allows JavaScript, Java, Flash and other plugins to be executed only by trusted web sites of your choice (e.g. your online bank).
If you choose “Do not allow any site to run JavaScript”, you’ll be able to set some exceptions for trusted websites, so you can enjoy those to the fullest. If you’re a Firefox user, you can try the NoScript extension: The NoScript Firefox extension provides extra protection for Firefox, Seamonkey and other mozilla-based browsers: this free, open source add-on allows JavaScript, Java, Flash and other plugins to be executed only by trusted web sites of your choice (e.g. your online bank).
Conclusion
If malware attacks such as the ones I mentioned ever made you feel helpless, there’s no reason to feel this way. The entire process may be complicated for cyber criminals, but there are plenty of protection methods available. You should be unwilling to succumb to fear and adopt the “there’s nothing I can do about it” attitude. Educate yourself, build a multi-layered security system and you’ll be safer than most Internet users will ever be. You’re not alone in this! Our team as well as many other security researchers and vendors are working constantly to build a safer web. Get on board!



 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security