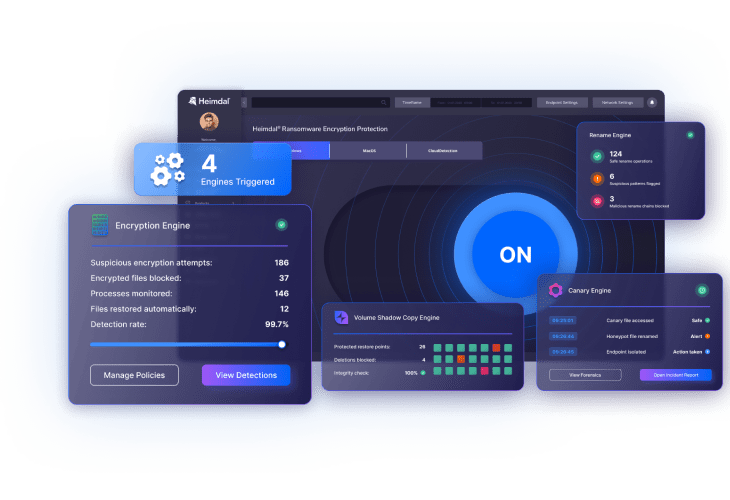
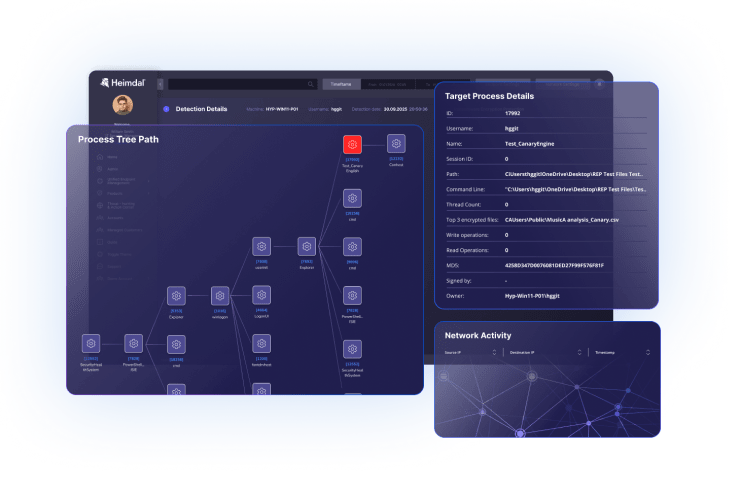
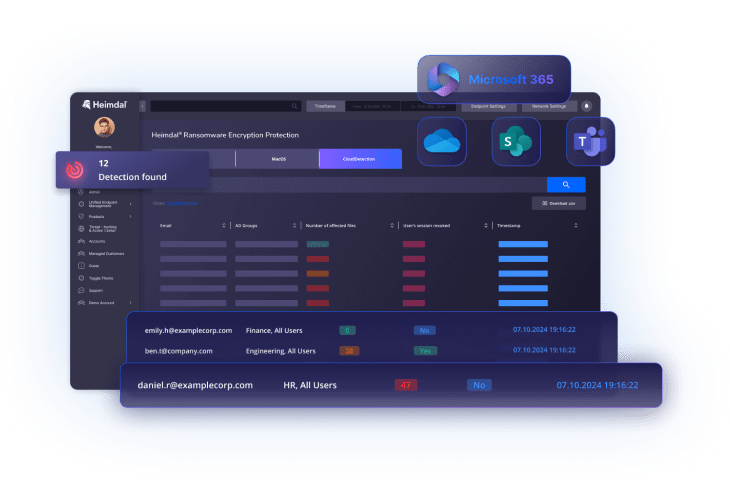
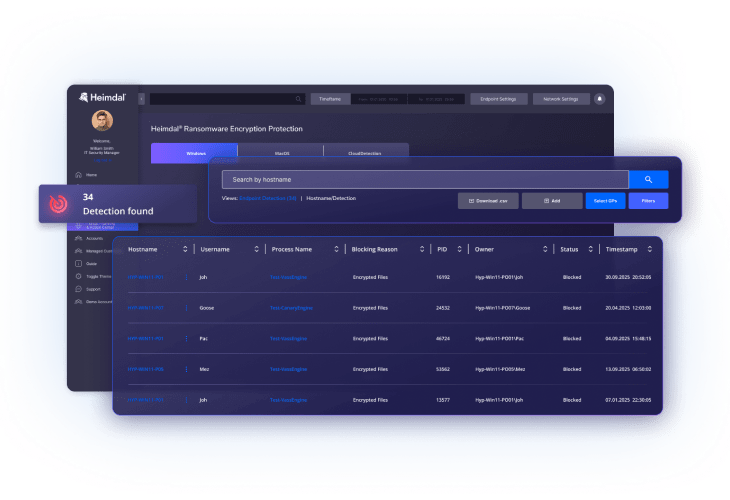
Cloud ransomware protection software extends security coverage to cloud-based platforms like Microsoft 365, Google Workspace, and various cloud storage services. These solutions integrate with cloud service APIs to monitor file activities, user behaviors, and access patterns within cloud environments.
The software tracks file modifications, sharing activities, and download patterns across cloud applications. When ransomware-like behavior is detected – such as mass file deletions, rapid encryption of cloud-stored files, or unusual API calls – the system can automatically respond by blocking suspicious processes, alerting security teams, and enabling rapid recovery from cloud backups. This cloud-native approach ensures distributed workforces and cloud assets remain protected without impacting legitimate user activities.














 Network Security
Network Security
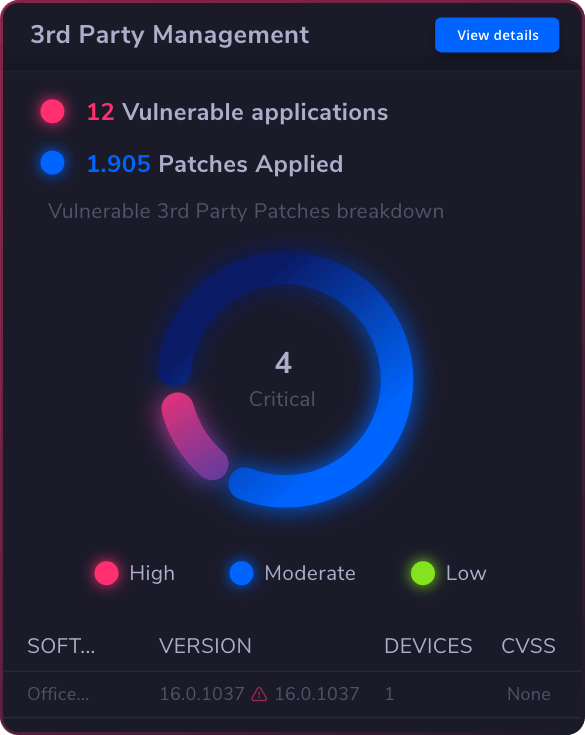
 Vulnerability Management
Vulnerability Management
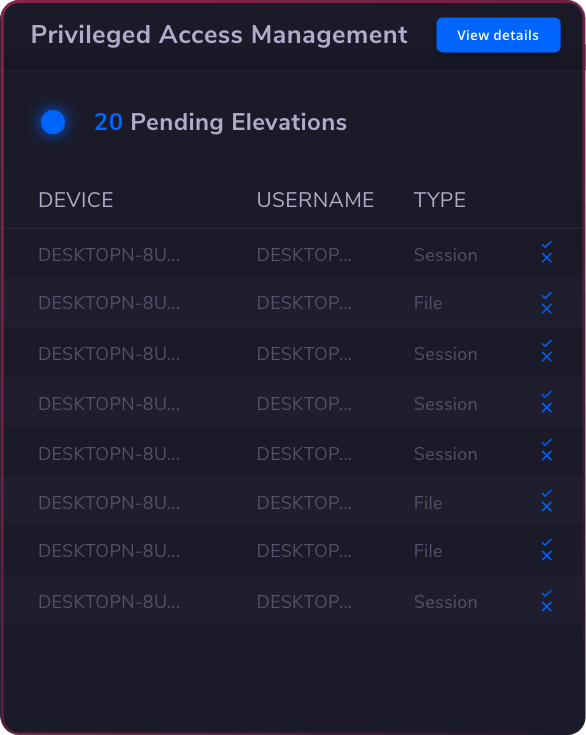
 Privileged Access Management
Privileged Access Management  Endpoint Security
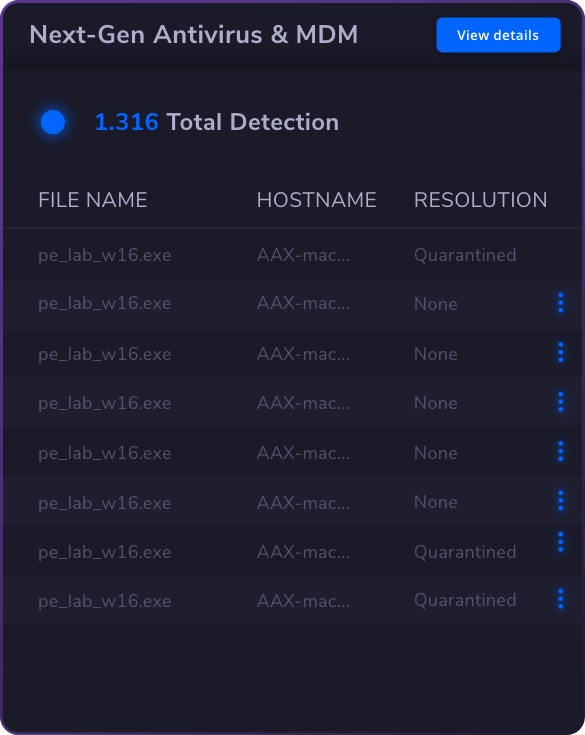
Endpoint Security
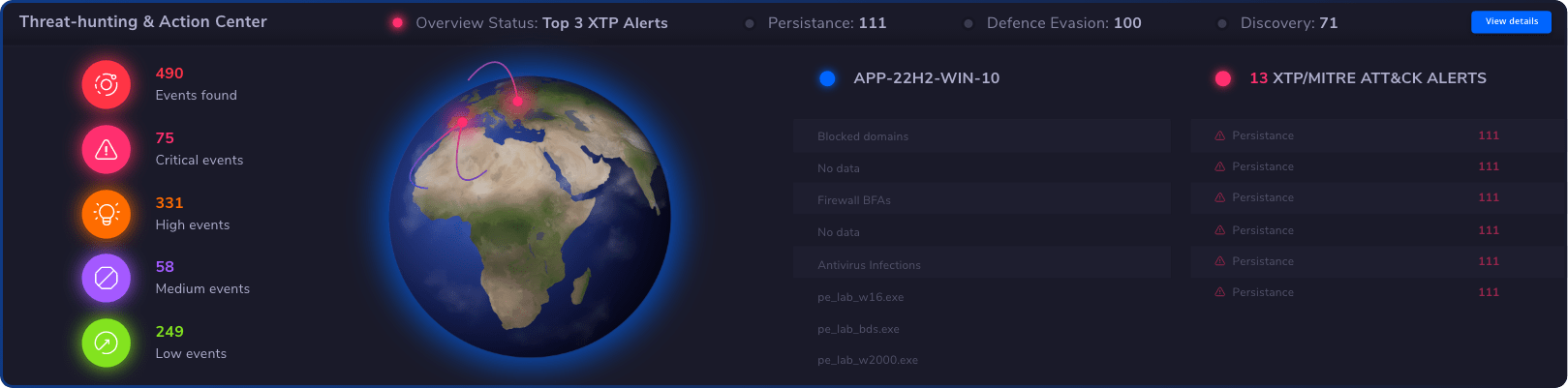
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
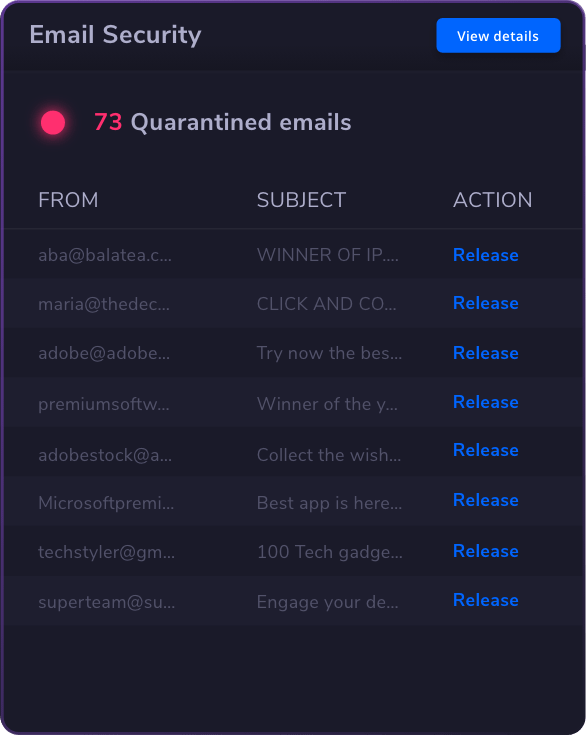
 Email & Collaboration Security
Email & Collaboration Security