Contents:
Ransomware attacks affect everyone, from local governments to large corporations, therefore ransomware protection is critical. It is up to all of us to help prevent them from being jeopardized. Unfortunately, many victims are paying the ransom, and despite efforts to strengthen defenses, many organizations are still struggling with detection and response.
This article will explore how Heimdal’s unified cybersecurity platform can save you from a possible ransomware attack and teach you the best practices to implement when it comes to this type of threat.
1. Ransomware Encryption Protection to Safeguard Your Device Against Malicious Encryption Attempts
Heimdal’s Ransomware Encryption Protection module is a ground-breaking, 100% signature-free solution that protects your devices from malicious encryption attempts initiated by ransomware attacks. As you may know, ransomware is frequently spread via phishing emails containing malicious attachments or drive-by downloading. Drive-by downloading occurs when a user unknowingly visits an infected website, and malware is downloaded and installed without the user’s knowledge.
Ransomware Encryption Protection augments traditional antivirus functionality, transforming it into a solution capable of preventing and protecting your endpoints from any of these malicious vectors that lead to a ransomware attack. The module detects processes that perform malicious encryption operations on files on the endpoint. In addition, it also handles kernel events related to IO reads, writes, directory enumeration, and file execution.
After studying the same patterns created by actual ransomware, patterns are matched against the collected events. Finally, the engine will allow three files to be encrypted before concluding that the process is suspicious. When a suspicious process is flagged, details about it are gathered and sent to the Heimdal servers.
Feel free to request a demo and take it for a spin!
2. Email Security to Protect You Against Mail-Delivered Threats
Nowadays, email security risks are increasing at an alarming rate. Many businesses deal with whale phishing, spear phishing, ransomware, and other cyber threats. Did you know that spam accounts for more than 55% of all incoming emails, diverting your attention away from legitimate ones? Spam emails, aside from wasting time, are also dangerous.
Heimdal Email Security is a spam filter and malware protection system with the most email security vectors of any platform. It can protect your business email agents from spam, malicious attachments, email-delivered malware and ransomware, phishing emails, malicious URLs, botnet attacks, and email exploits.
Increased visibility into endpoint availability and health indicates a lower risk of malicious actions. In addition, Heimdal’s Email Security does more than protect your inboxes from spam.
With a false-positive rate of 0.05%, ESECT protects against phishing and botnet attempts and automatically locks your account when outbound spam is detected.
User-oriented actions such as domain blocklisting and personal quarantine for suspicious email elements are also available. Email Security by Heimdal is the only all-in-one solution that continuously scans email activity for malicious code and fraud attempts.
Feel free to request a demo and take it for a spin!
3. Software Patching to Resolve Functionality Issues & Patch Microsoft, Linux OS, and 3rd Party Software
What is software patching? A software patch or fix is a quick fix for a piece of software intended to resolve functionality issues, improve security, or add new features.
Throughout its life, the software will encounter problems known as bugs. A patch is a quick fix for these issues. Patches are frequently available for download by IT or end users from the software maker’s website.
You can view and manage your software inventory while achieving preemptive vulnerability management with Heimdal Patch & Asset Management. This scalable, adaptable, and user-friendly solution can handle both Microsoft and third-party software on the fly, from anywhere in the world, and on any schedule.
With Heimdal’s Patch & Asset Management, you will ensure that:
- The software critical to the smooth operation of your organization (internal, third-party, or Windows-related) is managed through a unified, secure interface.
- For essential resilience against cyber threats, your organization has a rapid deployment of security-critical patches and updates.
- By automating this process and granting granular control over your software environment, you free up internal resources to focus on more pressing issues.
- Administrators can install and update software automatically or grant users permission to manage their software securely based on custom-built, flexible policies.
- Vulnerability management is automated, and actionable reports are generated for risk management.
Feel free to request a demo and take it for a spin!
4. Privileged Account Management to Protect Your Network & Endpoints and Keep Threats Away
Heimdal’s Privileged Access Management (PAM) is an Infosecurity mechanism composed of people, technology, and processes designed to track, manage, and control secret accounts while assisting organizations in their efforts to protect access to sensitive data and comply with the most current legal requirements.
Privileged Access Management ensures business security by preventing external and internal threats from improper use of administrative rights.
It is based on the Principle of Least Privilege, which states that users and applications should be given the minimum access required to complete their responsibilities or tasks.
Suppose ransomware does not include code that elevates a user’s privilege. In that case, it encrypts the files that are accessible on the systems of specific users.
You can find examples of privileged accounts in one of our previous articles about Privileged Account Management.
Our Privileged Access Management tool automates the process of granting admin rights for a limited time to each user who requires them but also de-escalates those rights when a threat is detected.
As a result, a privileged access management tool manages user rights and the rapid flow of software installations, logs and audit trails, and data protection compliance.
Feel free to request a demo and take it for a spin!
5. Endpoint and Network-Level DNS-Based Security Protection
Enhanced with TTPC (Threat To Process Correlation), Heimdal’s Threat Prevention Endpoint can provide your organization with the essential threat-hunting tools to map out the security-critical points in your environment.
It comes with Predictive DNS, a revolutionary AI & ML algorithm capable of predicting whether a domain is malicious before it hosts any malicious content. In addition, advanced neural networks and AI linguistic analysis can achieve unprecedented levels of truly intelligent prevention.
With the introduction of this revolutionary feature, Threat Prevention – Endpoint becomes the world’s first cybersecurity product to support accurate DNS over HTTPS filtering, extending beyond standard DNS rerouting. The functionality bypasses all DNS queries through a Hypertext Transfer Protocol Secure encrypted session encrypts domain name system traffic.
Aside from its unique threat-hunting capabilities, Heimdal’s Threat Prevention Endpoint is notable for its integrations with the rest of our Endpoint Prevention, Detection, and Response suite, allowing you to cover all fronts of cybersecurity defenses from a single unified interface.
Feel free to request a demo and take it for a spin!
Heimdal’s Anti-Ransomware Checklist
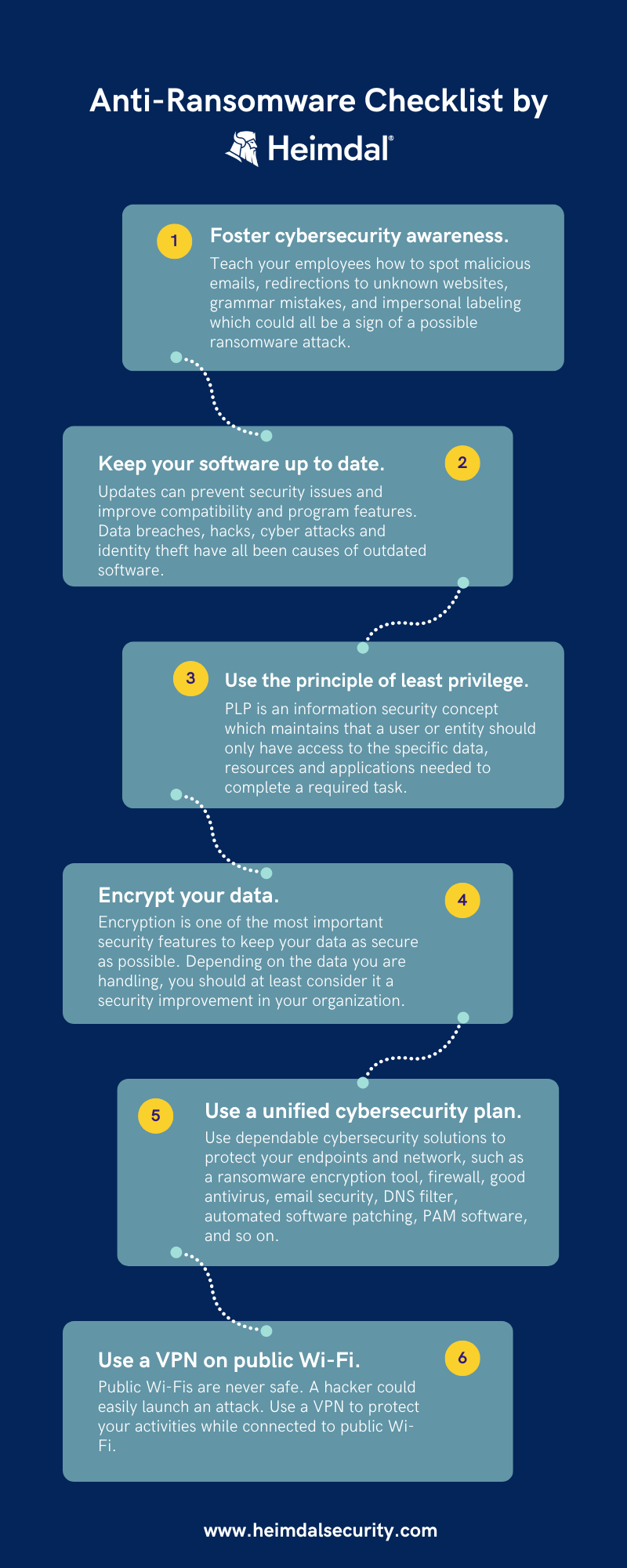
- Create a culture of cybersecurity awareness.
Teach your employees how to spot malicious emails. For example, a strange email address, hovering over redirecting to an unknown website, grammar mistakes, and impersonal addressing could all be indicators of compromised emails. In addition, invest in Security Awareness Training solutions so employees can learn how to deal with scam emails through phishing simulations.
- Maintain the most recent version of your software.
This may appear to be a very repetitive and trivial urge, but as simple as it may be, it is the fundamental solution in terms of prevention.
Because programs are not perfect, security researchers are constantly improving them by releasing patches. As a result, organizations and individuals can benefit from the most recent patches by always running updates. A Patch Management Tool will configure automatic patch deployment for you.
- Use the least privilege principle.
The principle of least privilege (POLP) is a fundamental tenet of zero trust. Users are given the bare minimum of access to applications or systems to complete their tasks successfully. As a result of the restricted access, no one will tamper with files or other sensitive data by mistake or on purpose.
- Backup and encrypt your data.
Backing up is no longer viable for organizations because advanced ransomware exfiltrated data and uses it as a double-extortion method. However, a backup should be set up if you manage it well.
Otherwise, how would you restore your data if no decryption key is available? Information in the cloud should be encrypted, and backups should be tested regularly for performance. An offline backup, such as a hard drive, may be beneficial. Immutable storage (WORM – Write-Once-Read-Many) will store your data in a bucket and lock it so it cannot be changed. Endpoint protection on your servers can also protect your backup.
- Make an inventory of your assets.
Any data, device, or another environment component that supports information-related activities” is defined as an IT asset. Hardware (e.g., servers and switches), software (e.g., mission-critical applications and support systems), and confidential information are examples of assets.
Making an inventory of your IT assets allows you to identify the most vulnerable ones and consider how an attacker could infiltrate your network, providing valuable insights into how you can improve your prevention methods.
- Employ a multi-layered cybersecurity strategy.
The key is practical cybersecurity protection. Use dependable cybersecurity solutions to protect your endpoints and network, such as a ransomware encryption tool, firewall, good antivirus, email security, DNS filter, automated software patching, and so on.

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;
Conclusion
Ransomware is a pervasive and harmful cyber threat that can have devastating effects. As a result, companies seeking to protect their employees, clients, partners, assets, money, and operations must prioritize learning how to prevent it.
Fortunately, Heimdal provides an integrated cybersecurity suite that includes the Ransomware Encryption Protection module.
This module is compatible with any antivirus solution and is 100% signature-free for superior ransomware detection and remediation. Heimdal has your back — our team stands ready to help you build a secure home or company environment as you learn about cybersecurity.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube for more cybersecurity news and topics.
Do you work for an NHS Trust? Heimdal is giving you free ransomware licenses to combat growing cyber attacks.
Get your free ransomware protection here.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










