Contents:
Encryption as a Service (EaaS) is a cloud-based model that offers pay-per-use encryption services to users or organizations.
Let’s take a closer look at what EaaS can do for business.
What you’ll find in this article.
- What is Encryption as a Service (EaaS)?
- Why Is Encryption as a Service Important?
- How Does Encryption as a Service Work?
- What Are the Benefits of Encryption as a Service?
- Encryption as a Service Challenges and Limitations.
What is Encryption as a Service (EaaS)?
With EaaS, end users and companies can encrypt sensitive information stored in the cloud or transmitted over networks.
This service offers encryption keys management, ensuring only authorized users can access the encrypted data.
In addition, simplifies the implementation of encryption without users having to manage complex encryption processes themselves.
This enhances data security for both businesses and individuals.
Why Is Encryption as a Service Important?
So, if hackers can infiltrate your organization’s network, they will have the keys to the kingdom.
EaaS ensures that data is always encrypted. Even if hackers breach your network, all they’ll find is indecipherable data.
As a result, encryption as a service is critical in securing a wide range of it assets.
It includes the following features.
- Confidentiality in encoding the message’s content.
- Authentication in validating a message’s origin.
- Integrity in establishing that the contents of a message have not been altered.
- Nonrepudiation in preventing the sender from denying sending the encrypted message.
How Does Encryption as a Service Work?
EaaS prevents unauthorized parties from stealing or eavesdropping on your data.
Here’s a little visual for you on how encryption as a service works.
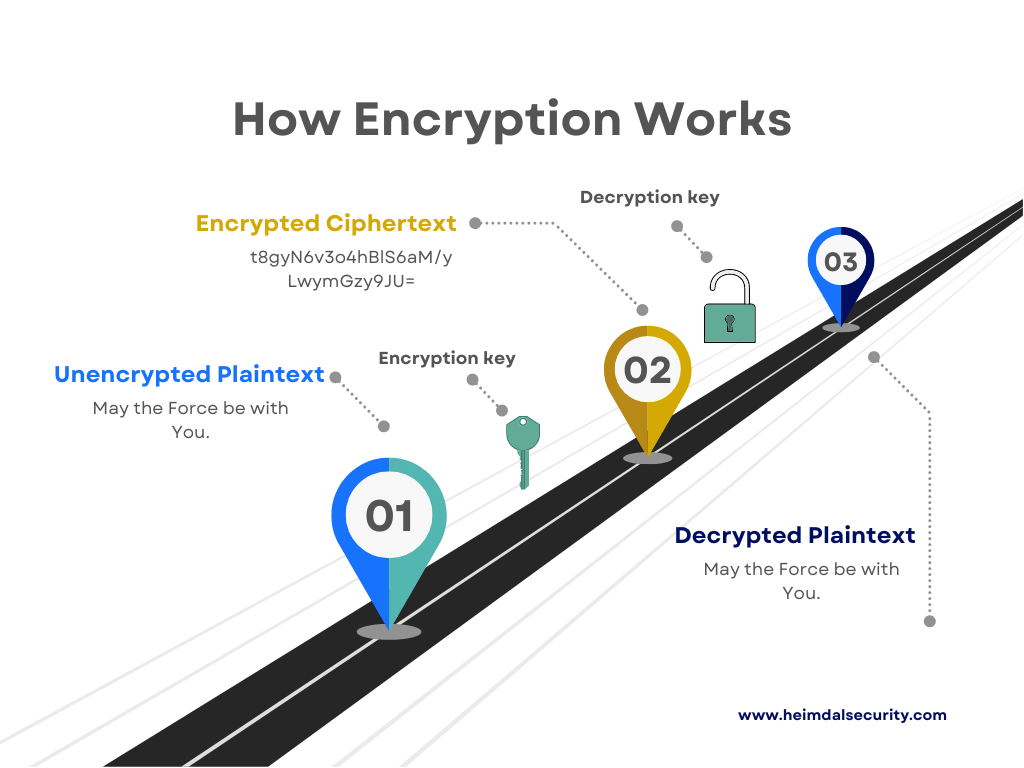
Let’s take a practical example to explain this. When you use an ATM or buy something online, encryption protects the relayed information.
In addition, encryption is used to protect data in transit and at rest.
Any encryption system has three major components.
- Data security.
- Encryption engine.
- Key management.
A machine stores and runs these components locally.
Types of encryption for sensitive data
In any architectures, these components usually run in separate locations. This reduces the possibility of any one component being compromised.
The sender must decide which cipher will best disguise the message’s meaning.
More than that, it also decides variable to use as a key to making the encoded message unique.
This happens at the start of the encryption process. The most common types of ciphers are symmetric or asymmetric.
Symmetric Ciphers
Symmetric ciphers use a single key, also known as secret key encryption. Because the sender must share the private key with all entities authorized to decrypt the message, this key is becomes a shared secret.
Asymmetric Ciphers
Asymmetric encryption is much slower than symmetric key encryption. The Advanced Encryption Standard (AES) is the most used symmetric key cipher.
Asymmetric ciphers (PKI) use two distinct but logically related keys. Because it is difficult to factor in large prime numbers and reverse-engineer the encryption, PKI uses prime numbers to generate keys.
The Rivest-Shamir-Adleman (RSA) encryption algorithm is the most widely used public key algorithm. RSA allows you to encrypt a message using the public or private key.
Whichever key is not used for encryption becomes the decryption key.
Modern crypto processes encrypt data with a symmetric algorithm and exchange the secret key with an asymmetric algorithm.
What Are the Benefits of Encryption as a Service?
Encryption’s primary goal is to protect the confidentiality of data-at-rest and in transit.
- Encryption Increases Data Integrity
Since data is changing, encryption does not guarantee the integrity of our data at rest.
Still, it can be used to verify the integrity of our backups. Additionally, we can maintain the integrity of our data using digital signatures.
This prevents hackers from intercepting and tampering with the data.
- Encryption Saves You from Regulatory Fines
Regulations such as the GDPR do not explicitly mandate encrypting data.
However, specific security measures and safeguards must be implemented to maintain the privacy of EU citizens’ information.
In contrast, HIPAA demands that all confidential data remain encrypted.
Hence why organizations which lose a portable device or drive with unencrypted ePHI may be fined.
Encryption as a Service Challenges and Limitations
While encryption has some significant advantages, there are some disadvantages too.
For example, encrypting your PII files may increase security, it will also make it nearly impossible for your employees to complete their work.
File systems are locations where employees are creating, moving, modifying, copying, and sharing data.
Adding encryption to this could result in an untidy and difficult-to-manage work environment.
Types of Encryption as a Service
Let’s take a closer look at commonly used encryption types.
Encryption as a Service (EaaS)
EaaS is a subscription model that allows cloud service customers to enjoy encryption’s security.
Customers who lack the resources to manage encryption can use this approach to protect data.
This is especially useful in a multi-tenant environment and address regulatory compliance concerns.
EaaS features
- Full disk encryption (FDE).
- Database encryption.
- File encryption .
End-to-end Encryption (E2EE)
End-to-end Encryption (E2EE) prevents an attacker from viewing data sent between two parties.
While Transport Layer Security (TLS) provides encrypted client-server communication, it does extend to the relayed content.
Several messaging apps already offer this type of encryption. WhatsApp, Signal, and Facebook have already deployed End-to-End encryption.
Field-level Encryption
A website typically uses field-level encryption.
Field-level encryption secures the following type of data
- Credit card numbers.
- Social Security numbers.
- Bank account numbers.
- Health-related information.
- Financial data.
All data in a given area will automatically be encrypted once selected.
FDE (Full-Disk Encryption)
FDE (Full-Disk Encryption) is encryption at the hardware level.
FDE automatically converts data on a hard drive into an incomprehensible format.
In this case, decryption without the key to undoing the conversion becomes impossible.
It’s still possible to access the data even when the hard drive has been placed in another machine with the necessary authentication key.
FDE can be installed during manufacture or added later.
Homomorphic Encryption
The conversion of data into ciphertext that can be analyzed and worked with as if it were still in its original form. This is known as homomorphic encryption.
This encryption method allows complex mathematical operations on encrypted data without damaging it.
HTTPS Encryption
Using HTTPS enables website encryption by running HTTP over the TLS protocol. A public key certificate must be installed to allow a web server to encrypt all the content it sends.
Link-level Encryption
In link-level encryption, data is encrypted when it leaves a host. It is then decrypted at the following link, which may be a host or relay point.
After that it is re-encrypted before sending it to the following link.
Encrypting the data is repeated until it reaches the recipient with a different key or algorithm.
Network-level Encryption
It applies crypto services at the network transfer layer, above the data link level but below the application layer. Network encryption is implemented through Internet Protocol Security (IPsec), a set of open Internet Engineering Task Force (IETF) standards that, when combined, create a framework for private communication over IP networks.
Quantum Cryptography
Quantum cryptography relies on particles’ inherently quantum mechanical properties for data protection.
For example, the Heisenberg uncertainty principle suggests that the two main aspects of a particle, its momentum and location, cannot be calculated without shifting their values.
This makes it impossible to replicate quantum-encrypted data, as any attempt to look at the content will cause a modification in the information. Thus unapproved parties trying to copy or gain access to the data will be revealed upon any alteration of said data.
Encryption Algorithms
EaaS frequently employs these algorithms.
AES
AES is a symmetric block cipher chosen by the US government to protect classified information; it is used to encrypt sensitive data in software and hardware worldwide.
The National Institute of Standards and Technology (NIST) began developing AES in 1997 when it announced the need for a successor algorithm to the Data Encryption Standard (DES), which was becoming vulnerable to brute-force attacks.
DES
DES is an outmoded symmetric key data encryption method.
Because DES encrypts and decrypts messages with the same key, both the sender and the receiver must know and use the same private key. The more secure AES algorithm has replaced the DES algorithm.
Diffie Hellman
Diffie-Hellman key exchange, also known as exponential key exchange, is a method of digital encryption that uses numbers raised to specific powers to generate decryption keys based on components that are never directly transmitted, making a would-be code breaker’s task mathematically impossible.
Elliptical Curve Cryptography (ECC)
Elliptical Curve Cryptography (ECC) generates security between key pairs by utilizing algebraic functions.
The resulting cryptographic algorithms may be faster and more efficient, with comparable levels of protection using shorter cryptographic keys.
ECC algorithms are thus an excellent choice for the internet of things (IoT) devices and other products with limited computing resources.
Quantum Key Distribution (QKD)
Quantum key distribution (QKD) is an encrypted messaging method in which encryption keys are generated using a pair of entangled photons transmitted separately to the message.
Quantum entanglement allows the sender and receiver to determine whether the encryption key has been intercepted or changed before the transmission occurs.
This is because, in the quantum realm, observing the transmitted information changes it.
Once it has been determined that the encryption is secure and has not been intercepted, the encrypted message is permitted to be sent over a public internet channel.
RSA
Many protocols rely on RSA for encryption and digital signature functions, including Secure Shell (SSH), OpenPGP, Secure/Multipurpose Internet Mail Extensions (S/MIME), and Secure Sockets Layer (SSL)/TLS.
How Can Heimdal Help with Encryption?
With Heimdal’s Ransomware Encryption Protection module, you can take complete control of every process running on your endpoint – the encryption protection is the only security solution on the market that can map out the previously unknown malicious activity and prevent it from DoS-ing your sensitive files.
Furthermore, Ransomware Encryption Protection is a revolutionary 100% signature-free solution that protects your devices from malicious encryption attempts initiated during ransomware attacks.

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;
Wrapping Up
Now, if you’ve made it to this point, make sure you give yourself a big pat on the back because this wasn’t easy to digest.
As you can see, EaaS enables cloud service customers to benefit from encryption’s security without installing and managing encryption independently.
It’s a new concept, but it’s important because it improves security by eliminating gaps when data must be decrypted in the cloud or at the database level. EaaS makes encryption more accessible without sacrificing performance – an idea whose time has come as businesses expand into the cloud.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security











