Contents:
In today’s information age, it is absolutely critical to enforce policies that protect the quality of gathered data, since more pieces of information are stored and analyzed now than ever.
The first move towards maintaining your data safe is to learn the basics of data integrity.
What Is Data Integrity?
As explained in our Cybersecurity Glossary, data integrity refers to information property that has not been altered or modified by an unauthorized person. The term is used to refer to information quality in a database, data warehouse, or other online locations.
By the usage of standard protocols and guidelines, data integrity is typically imposed during the design and creation process of a data repository. It is preserved by the use of different methods and validation protocols for error-checking.
Data integrity is assessed by its authenticity, completeness, and transparency. In addition, the integrity of data also requires ensuring that organizations comply with the regulations in place and identify security lapses. This status is attained by enforcing a series of protocols, instructions, and criteria. Fundamentally, data integrity is maintained by designing a framework where data cannot be tinkered with or manipulated.
Data Integrity vs Data Quality
Data can be the most important resource for a company – but only if it’s data you can actually rely on.
Inaccurate insights, biased observations, and ill-advised suggestions may be the outcomes of unreliable data.
As I previously mentioned, data integrity is a basic feature of information security and relates to the quality and durability of data contained in a database, data center, etc. The concept of data integrity may be used to define a state, a procedure, or a feature and is sometimes used interchangeably with “data quality”.
However, “data integrity” and “data quality” are two different terms.
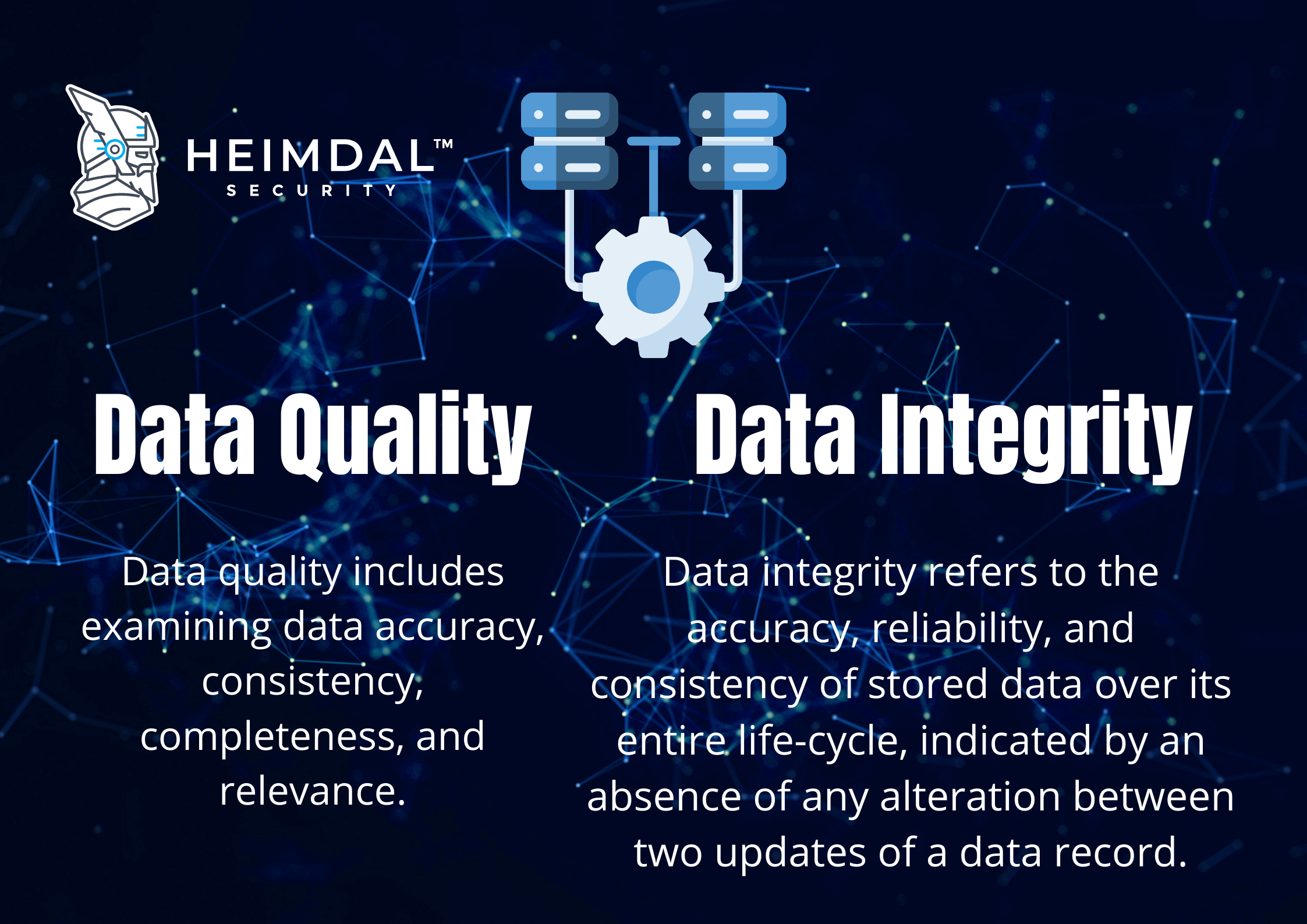
To make informed decisions, any business trying to improve the quality, consistency, and validity of its data needs to grasp the difference between data integrity and data quality.
Data Quality
The reliability of data relates to data quality. The quality of data is a component of the integrity of data. For data to be considered as having quality, it must be characterized by:
- Accuracy: Data must be sufficiently accurate for the intended usage and, while it could have many applications, should be collected only once.
- Validity: Data must be collected and used in accordance with the applicable conditions, including the proper application of the laws or standards. This aspect will maintain consistency, assessing what is meant to be measured, across times and among affiliated groups.
- Reliability: Data must demonstrate stable and transparent processes when gathering it through points of collection and over time.
- Timeliness: Data must be collected as soon as possible after a certain activity and accessible within a reasonable amount of time for its planned use. In order to support requirements and not affect service or management decisions, data must be easily and quickly accessible.
- Relevance: Throughout a database, data must be continuously relevant.
- Completeness: The data requirements should be specifically defined on the basis of the organization’s information needs and also on the data processing procedures relating to those requirements.
Data quality ought to fulfill all the above conditions – otherwise, the data quality aspect would be missing.
Nevertheless, merely dealing with data quality does not mean that it would be valuable to an enterprise. For example, you could keep a reliable and relevant database of user contact details, but if you may lack sufficient supporting information that provides you the background for certain customers and their interaction with your business, that registry may not be that helpful.
This is where data integrity starts to matter.
Data Integrity
Although data quality relates to whether the information is correct and trustworthy, data integrity transcends the quality of data. The integrity of data must ensure data is complete, reliable, clear, and relevant.
Data integrity is what really renders the data valuable to its operator. A part of it is data quality, but this is not its sole component.
Data integrity is built on four central principles:
- Integration: Independent of its primary source, data must be merged effortlessly into legacy structures, database systems, or cloud data centers in order to achieve prompt insight.
- Quality: To be valuable for decision-making, data must be complete, relevant, accurate, timely, and reliable.
- Location intelligence ensures the identification of location-based data by organizations and increases data transparency by ensuring better precision and continuity.
- Enrichment: By augmenting your internal data with information from multiple sources, it adds more meaning, depth, and significance to it. Incorporating different information such as company, customer, or location data offers you a more complete and proper perspective over your organization’s results.
Data is an invaluable business commodity, and for companies seeking to make data-driven choices, both data accuracy and data integrity are critical. The quality of data is a strong initial step, however, data integrity increases the degree of relevance and intelligence within an enterprise and eventually leads to better strategies.
One must first fix data quality issues to be able to successfully move towards data integrity. Businesses that make a systematic attempt to address data quality and data integrity challenges will certainly experience higher performance.
Types of Data Integrity
Physical integrity
When discussing the physical integrity of data, we refer to the protection of the wholeness and accuracy of that data as it’s stored and recovered. In case of natural disasters, blackouts, or cyberattacks, physical integrity is compromised. Additionally, human error, storage erosion, and a whole host of issues can also make it impossible to obtain precise data.
Logical integrity
Whenever data is managed and processed, there is a possibility that it might get damaged – maliciously or inadvertently. Preserving the integrity of data helps ensure that the information stays unchanged and unaltered during its entire lifespan. For instance, a user might mistakenly insert a phone number into a date section. Should the database uphold data integrity, it would prevent these errors from happening.
Maintaining data integrity should become a priority when building databases. For this reason, whenever feasible, a proper database will impose data integrity.
In relation to databases, there are four categories of logical integrity:
#1. Entity Integrity
The entity integrity ensures each row inside a table is unique (two rows can never be identical). A primary key value can be established to accomplish this. There will be a unique identifier in the primary key field, and two rows will not have the same unique identifier.
#2. Referential Integrity
Referential integrity is associated with relationships, which suggests we have to guarantee the foreign key value matches the primary key value at all times when two or more tables have a relationship. Coming across a scenario where, in the primary table, a foreign key value has no matching primary key value is to be avoided, as this will lead to the record becoming orphaned.
Referential integrity will prohibit users from attaching records to a related table if the primary table does not have an associated record, changing values that result in orphaned records in a related table in the primary table, or erasing records from a primary table if similar records are matched.
#3. Domain Integrity
The integrity of the domain involves the authenticity of entries for a certain column. The very first step in preserving domain integrity is choosing the suitable data type for a column. Additional actions could include creating relevant restrictions and rules to determine the format of the data and/or limiting the number of potential values.
#4. User-Defined Integrity
User-defined integrity enables the user to apply rules which are not protected by either of the other three forms of data integrity of the database.
Data Integrity Threats
- Security failures are a frequent risk to data integrity faced by many organizations. Since the effects of data vulnerabilities are highly critical, companies will also have to apply extra security protection measures. For example, Equifax invested in identity protection packages for its clients following their notorious data breach.
- Regulations nonconformity. Another typical data integrity risk is non-compliance with data regulations. Significant fines are given to organizations failing to abide by certain legislation such as the GDPR. In certain cases, on top of these large payments, they may also be prosecuted.
- Unreliable data – reduces an organization’s competitiveness and performance. It refers to record redundancies, incomplete data, and unidentifiable data sources, which restrict organizations from conducting precise assessments, thus leading to additional operating expenses.
- Human error (entering incorrect details, duplicating data, accidentally deleting it, etc.) is also one of the most common data integrity threats.
How to Preserve Your Data Integrity
Since the danger of data integrity has become so detrimental to organizations and information systems, a range of tactical steps to minimize these risks needs to be introduced. Nevertheless, since it would be impossible to eradicate all risks in a single blow, we recommend using a mix of various strategies and tools.
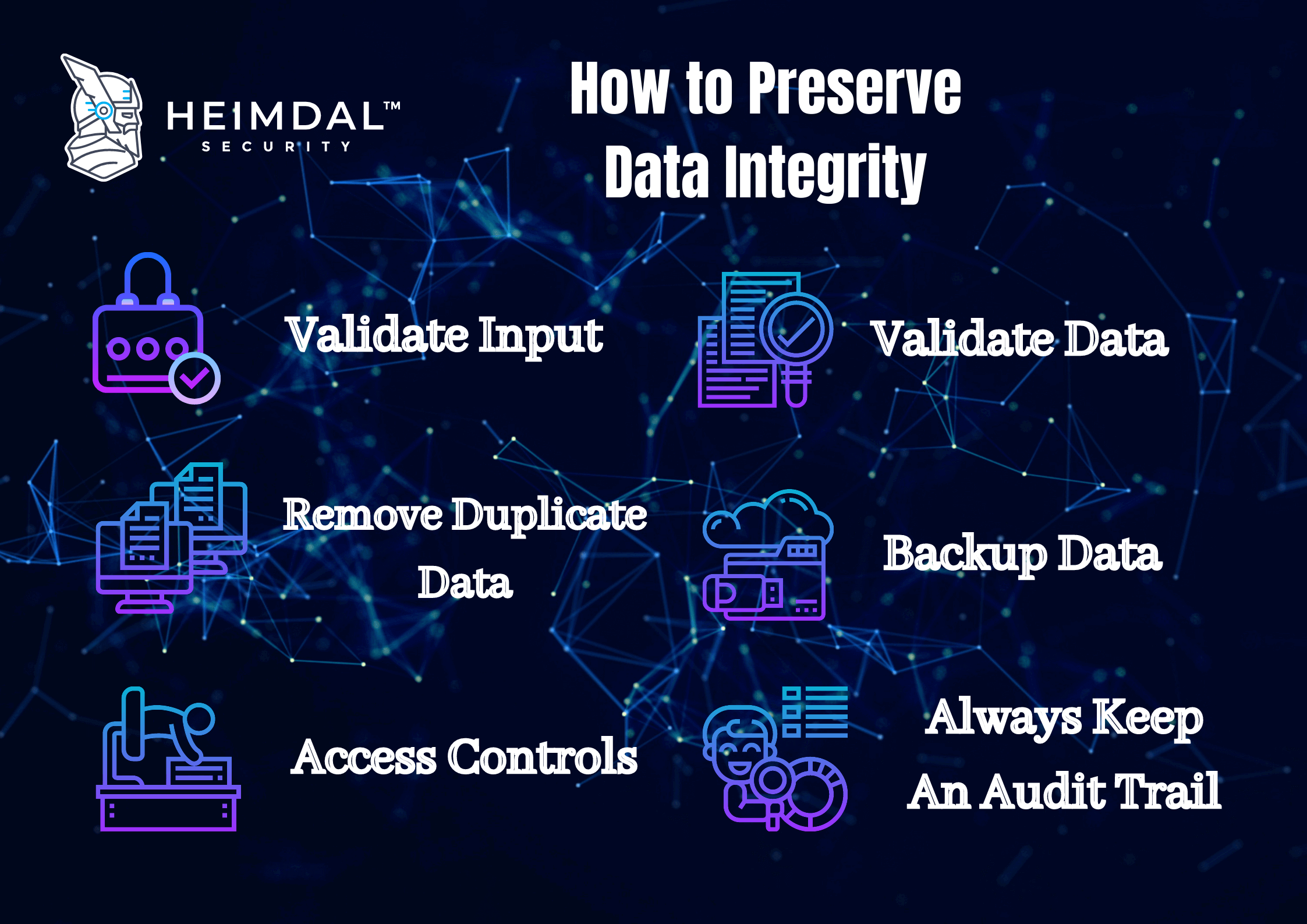
Below you will find the top 10 measures that reduce the threats to data integrity.
#1. Educating your employees and promoting a culture of Integrity
Supporting an environment of integrity mitigates in many ways the risk of data integrity. It helps by encouraging employees to be honest about their own jobs as well as about the endeavors of their colleagues. Staff in a data integrity-based community is often more prone to disclose cases when people are acting irresponsibly or do not perform their tasks in accordance with data integrity policies.
#2. Introducing measures for quality assurance
Quality control mechanisms require individuals and procedures to verify that workers operate with data in compliance, with confidentiality, and in accordance with data governance policies.
#3. Having an audit trail
An audit trail is an especially powerful way to minimize the danger of losing data integrity. Throughout the various stages of their lifecycle, audit trails are essential to understand what happened to data, namely where it originated from and how it was transformed and used.
#4. Mapping processes for your data
Organizations have better control over their assets by mapping them – preferably before any data is used. These maps are essential for the implementation of effective security and regulatory enforcement measures.
#5. Removing vulnerabilities
To help mitigate data integrity threats related to securing data, it is required to remove security vulnerabilities. This risk reduction approach involves identifying known security vulnerabilities and enforcing steps to remove them, for instance by installing security patches in a timely manner.
With automated updates activated, our customers who use Heimdal™ Patch & Asset Management can rest assured knowing that they are safe and compliant at all times. Every month, almost 50% of our users install their security patches within 3 days upon release, while the rest tend to pause the process of patching according to their own schedule.
#6. Having a data backup process in place
We suggest a data backup and restoration plan to be implemented in the event of a device failure, program error, or data erasure. With a backup, the recovery and restoration of missing data files can take place more smoothly, helping to preserve the data integrity of restored records.
#7. Encrypting your data
Encryption is the most powerful way of maintaining the security of your files. This way, even if your data is breached, it would become inaccessible for malicious actors.
#8. Implementing multifactor authentication
In an age in which simple password protection is no longer adequate, we are continually exposed to password threats such as credential stuffing attacks or key loggers. Therefore, besides implementing a strong password policy to avoid common password security mistakes, multifactor authentication is critical for today’s enterprise security.
#9. Enforcing the Principle of Least Privilege and Privileged Access Management
The accounts that intruders wish to access the most are privileged accounts. Many IT professionals don’t fully understand the dangers involved with privileged account compromise and abuse, which makes them (and thus the organizations they work in) more susceptible to attacks.
Due to the unrestricted access they offer, privileged accounts are the focus of malicious hackers and sadly, many businesses have made the attackers’ jobs easy by granting local admin rights to most staff members. To learn more about this threat, I suggest you also check out the article where my colleague explained what the Principle of Least Privilege is.
Heimdal™ Privileged Access Management eliminates the burden of managing admin rights and ensures scalability, data protection compliance, and more. When used in tandem with Heimdal™ Next-gen Endpoint Antivirus or Heimdal™ Threat Prevention, it becomes the only PAM tool on the market that automatically removes admin rights once threats are detected on a machine.
#10. Proactively hunting, detecting, and blocking known and unknown threats
Cyber threat hunting should be performed by organizations confronting the growing amount of potential threats. Not only that, but businesses should also choose the appropriate detection and response mechanisms to react to emerging threats. This is where EPDR comes into play.
EPDR (Endpoint Prevention, Detection, and Response) is one of the most recent developments in cybersecurity and one of the best security methods you can rely on for proactive, real-time security. Heimdal’s EPDR offering features Machine Learning-driven security, HIPS/HIDS and IOAs/IOCs, integration with various tools, automatic vulnerability patching, and admin rights management to safeguard your organization from multiple angles and maintain your data integrity.
Conclusion
Indisputably, we operate in a data-driven world, where data is the cornerstone of today’s economy and business environment. Organizations are constantly dependent on data in relation to their operations, clients, financial activity, and so on. This growing trend has been led by the exponential growth of technology. Nonetheless, as the volume of data we receive and use has risen incredibly fast, the integrity of data is not taken into consideration all too frequently.
Organizations must ensure that their data integrity policies are properly implemented, understood, and accepted throughout the company. Since data has turned into an invaluable organizational resource, it must be your priority to ensure its integrity. In the end, the better you preserve your data integrity, the more it will positively impact your business.
How do you maintain data integrity in your organization? Share your best practices in the comments section below!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










