Contents:
Removing admin rights prevents users from downloading unauthorized software on the company’s endpoints.
The advantage is it helps reduce the attack surface. It’s the cybersecurity equivalent of slamming the system’s door into the hackers’ noses.
So, why are companies still failing to apply this cybersecurity textbook measure? There’s a simple answer to it. Employees find the lack of access privileges annoying.
Reducing privileged access can create a sense of frustration inside the teams. If not carefully managed, it can lead to decreased productivity.
I’ll explain further how you can remove local admin rights to keep the system safe and have a minimum impact on productivity.
Key takeaways
- What are admin rights?
- Risks that local admin rights pose to an organization’s security
- Benefits of removing admin rights
- How to remove local admin rights with a privileged access management solution
What Are Admin Rights?
Admin rights are the highest permission level that a computer user can get.
IT Administrators sometimes grant administrative permissions to users to speed up certain tasks. These high-level privileges allow users to create, delete, and change items and settings.
An employee with superuser rights can:
- install any software they want on the company’s computer
- delete system or network files
- move, copy or rewrite data inside files
- reconfigure system settings
- deploy updates for applications
Why Is Removing Admin Rights Important?
Unprofessional privileged access management (PAM) poses a high-security risk for any company.
Allowing employees to install any software they want on their devices seems to reduce the pressure off the help desk team. But any software can mean any malware, so this practice can generate serious security issues.
This is why removing the local admin rights is considered a PAM best practice. By applying it, you reduce the attack surface and thus limit the spread of various forms of malware.
Removing admin privileges from your organization helps reduce both insider and outsider threats.
Impact on mitigating insider threats
De-escalating standard users’ administrative rights on the endpoints doesn’t completely eliminate insider threats risks. However, removing local administrator rights is one of the most effective mitigation measures.
Here are some risky things an employee could unintentionally do to expose their account to hackers:
- Set a weak password or share their password with other colleagues
- Reveal credentials due to phishing attack
- Insert an infected USB stick or external hard drive into the workstation
- Fall for CEO fraud and disclose to malicious third parties account credentials or other sensitive data they have access to
- Download malware when installing unauthorized software.
Sometimes insider threats can be intentional. Removing admin rights can save the day in this case too. Here’s how a disgruntled employee can use excessive privileges to harm the company:
- Delete or leak sensitive data from the company’s database
- Use personal data that they shouldn’t have access to for social engineering
- Disable security settings
- Create backdoors
- Install remote network administration tools, etc.
In all of the situations above, removing admin rights reduces the impact of an insider threat on the company’s security posture.
Impact on mitigating external threats
A successful phishing attack may give hackers access to a user account with local admin rights. In this case, the attackers could use admin privileges to:
- Gain access to sensitive data and perform a ransomware attack.
- Exploit known or zero-day vulnerabilities in common B2B software and operating systems. That could lead to lateral movement, privilege escalation and even taking over the whole system.
- Create new accounts to maintain persistence.
So, removing admin rights would limit the potential damage of an external threat. The hacker would only have access to a basic, limited privileges account.
Admin Privileges Myths
Happy employees only
As much as you might trust your colleagues’ good intentions, happy employees don’t keep hackers away. An attacker impersonating a content employee could still abuse admin rights to encrypt all data they get access to.
The almighty antivirus
We have a strong antivirus so we’re fine. The problem with this allegation is antiviruses only detects known threats. It can’t prevent an attacker who got access to a company’s device from using available local administrator privileges.
Removing admin rights reduces productivity
It is true that System Admins spend a lot of time approving admin rights requests manually. However, this time waste can be completely avoided by using an automated PAM solution.

Common Risks of Admin Rights Misuse
Granting everyone admin privileges spells trouble. Admin rights can be either misused by the employee or abused by an attacker impersonating the employee.
This year’s Verizon Data Breach Investigations Report says 74% of all breaches included the human element. The number is 8% lower than in the 2022 report, yet it’s still impressive.
Most common risks that derive from admin rights misuse are:
- Malware deployment
- Bypass and/or disable user access control (UAC)
- Creating backdoors for third parties
- Data encryption and exfiltration which lead to ransomware
- Creating changes to lock legitimate users out of the systems
Those above are only five of the reasons why security experts insist on disabling local admin privileges:
Avoid as much as you can giving local admin rights. Local admin rights are uncontrolled, unaudited and enable standard users do whatever they want on the company’s computer.
Andrei Hinodache, Cybersecurity Solutions Expert @Heimdal

Heimdal® Privileged Access Management
- Automate the elevation of admin rights on request;
- Approve or reject escalations with one click;
- Provide a full audit trail into user behavior;
- Automatically de-escalate on infection;
How to Remove Local Admin Rights with Heimdal® Privileged Access Management
Regularly reviewing the status of admin privileges within your organization is best practice. If you don’t already do it, I advise you to start right now. Also, create a map of user admin privileges and clear policies for granting them.
Further on, I’m going to show you how you can remove local admin rights using Heimdal’s Privileged Access Management solution.
- Go to your Heimdal Dashboard
- Choose Endpoint Settings
- Click on the policy you want to update
- Choose the Privileged and Access Management tab
- Check Revoke existing local admin rights.
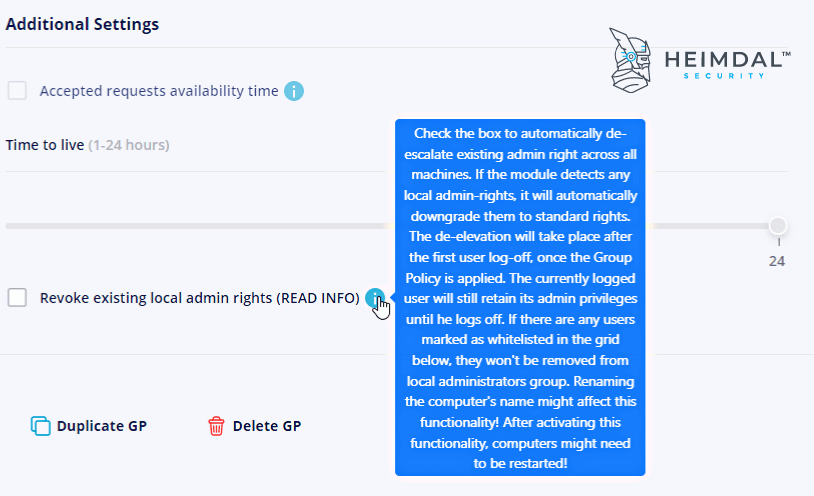
This option lets you reduce both local and domain users to standard users. What the Heimdal Agent does is take a snapshot that contains the local Administrators’ Group found on every endpoint and then erase all the group members.
The default Administrator user will be the only one that doesn’t get removed. By ticking this option, all the users in that group will de-escalate to standard permissions.
Until the first logoff/reboot happens, the logged users will keep the local admin privileges.
For domain-joined computers, however, the local Administrators’ Group members can be set to standard permissions only if the endpoint shares a communication with the domain controller.
If you disable this option, you can add back the local Admin Group members to the service stop.
Update the policy and you’re ready to go. Use the Global Option if you need to set-up multiple policies.
Wrapping It Up
While the human factor continues to have a powerful impact on the organization’s security, Gartner predicts that:
Legacy approaches delivering curriculum-based, awareness-centric programs are no longer effective.
By 2030, all widely adopted cybersecurity control frameworks will focus on measurable behavior change rather than compliance-based training as the critical measure of efficacy for human risk management.
Source – Gartner on Employee behavior
So, educating employees is important, but don’t rely on it to keep cyber threats off your digital environment. Instead, start using a professional privileged access management solution to maintain productivity while keeping the company safe.
Removing admin rights is the first step you need to do in the process of making access safer across your organization.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









