Contents:
For cybercriminals, privileged user accounts are nothing more than profitable targets. Why? Because they have elevated permissions, allowing them to gain access to sensitive information and make changes to applications and systems.
Why Is It Important?
First, we need to discuss privileged accounts. As the name suggests, privileged account management is related to privileged access management. These PAM tools track and secure privileged accounts to ensure business safety.
According to Forrester,
By 2023, 70% of organizations will have PAM practices for all use cases in the enterprise, reducing the overall risk surface.
My colleague has written in detail about privileged access management. To learn more about this technology, you can also read the article on best practices in Privileged Access Management.
Privileged accounts are special because they have more control. These accounts can be in different forms and places, like on a company’s own servers or in the cloud. Sometimes, more than one person can use these accounts temporarily.
For instance, the root account on a Mac is a type of privileged account. An account owner for Microsoft Azure is another. A corporate account for the official Heimdal™ LinkedIn profile is yet another form.
These accounts are risky because they can be hacked. Hackers want to get into these accounts because they can access a lot of a company’s important information and systems.
It’s not surprising that big cyberattacks, like those on JPMorgan Chase and Home Depot, happened because hackers got into privileged accounts. Often, these important accounts aren’t handled safely. Many times, different people use the same account with the same password, and there’s no record of who did what.
This is where the management of the privileges process helps address these security risks.
How Does Privilege Management Work?
Imagine this: Special passwords are kept in a very secure place. Users with special access use a system called PAM to get into their accounts. This access is recorded and is only for certain tasks.
For safety, the PAM system often asks why someone is using the account or needs a manager’s okay. Users usually don’t see the actual passwords; they get into their accounts through PAM.
Privileged Access Management administrators can follow user activities via the PAM portal and even manage live sessions in real time if needed. Besides, new PAM systems use machine learning to track deviations and risk scoring to immediately alert the administrator of dangerous activities.
What Are the Benefits of Privilege Management?
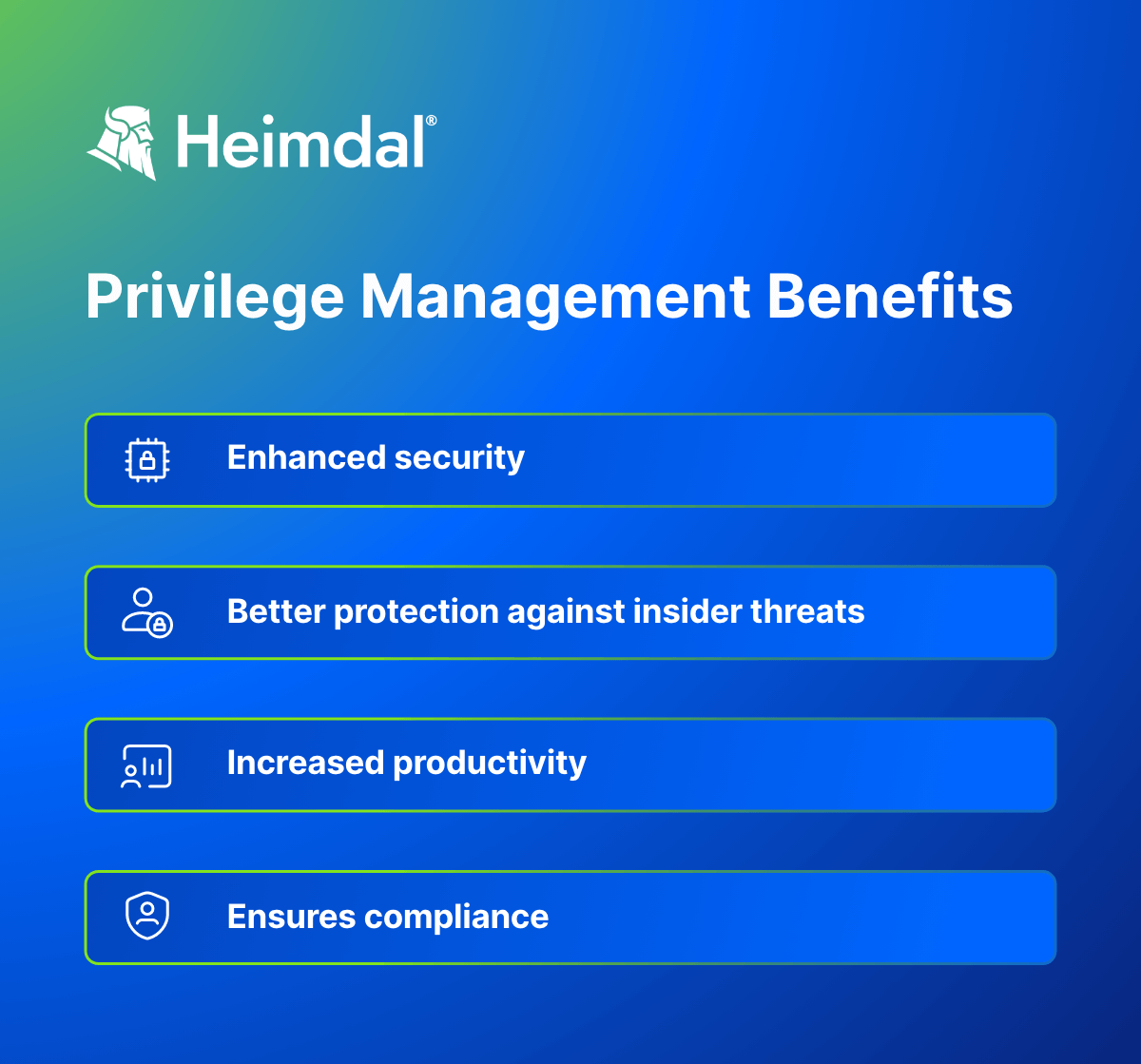
Enhanced security
Privileged Access Management (PAM) helps protect against cyberattacks. It deals with the problem of users having too many passwords or using the same password everywhere. PAM helps manage passwords better and alerts you to possible attacks.
Having a strong password management policy in place is crucial. A Privileged Access Management system can reduce the need for administrators to remember many passwords and avoid privileged users creating local/direct system passwords. Session management and alerts help you identify potential attacks in real time.
Better protection against insider threats
As surprising as it may sound, a large number of attacks come from within the organization. If it’s not an “inside job”, it’s usually former employees who haven’t been stripped of unnecessary privileges to prevent access after departure.
Increased productivity
PAM makes it easier and faster for users with special access to log into the systems they need. It reduces the hassle of remembering lots of passwords and lets users manage access from one place.
Ensures compliance
PAM helps companies follow laws by managing special access and keeping records of who accessed what. It can limit access to important systems, ask for extra approvals, and use stronger security checks.
Privileged Access Management tools offer a wide range of features. For instance, our Heimdal™ Privileged Access Management solution is a highly elaborate technology that allows for both escalation and de-escalation of user rights.
Privileged Access Management (PAM) adopts a centralized approach to managing and limiting access to critical data and systems, making sure that users after they are authorized, have just enough access required to do their job (a process known as the Principle of Least Privilege).
The principle of Least Privilege (POLP) is a key element in zero-trust strategies, as it minimizes user-system connections and safeguards privileged access to high-value assets and data. Its focus on restrictive access rights helps organizations reduce vulnerability to cyberattacks.
Heimdal’s Privilege Elevation and Delegation Management (PEDM) product could be a great fit for your organization. It gives users Just-In-Time administrative rights when they need them, in a smooth and secure manner.
Also, it includes a Zero Trust Execution Protection technology that blocks any software without a trusted certificate, reducing the chance of harmful software running on your machines.
What Is the Difference Between PAM and IAM (Identity Access Management)?

Identity Access Management (IAM) is different from Privileged Access Management (PAM). IAM is about verifying and allowing access for all kinds of users in an organization, like employees and clients. It handles access to important applications and resources, both in-house and cloud, and often works with directory systems. While PAM is for users with special access, IAM deals with a broader range of users, as explained in one of our previous blog posts, which can be a bigger security concern. For more details on IAM, you can read our article on its best practices.
Wrapping It Up…
As all businesses are prone to the risk of having their privileged accounts exploited, it’s vital not to turn a blind eye to Privileged Access Management tools. In the end, internal and external threats remain a serious danger, that shouldn’t be underestimated or ignored.

Heimdal® Privileged Access Management
- Automate the elevation of admin rights on request;
- Approve or reject escalations with one click;
- Provide a full audit trail into user behavior;
- Automatically de-escalate on infection;
If you enjoyed this article, follow us on LinkedIn, Twitter, Facebook, or YouTube to keep up to date with everything we post!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security