Contents:
In the last few years, just-in-time (JIT) access has increasingly become the gold standard of effective privileged access management (PAM). At its most basic, JIT is a feature that ensures no account has ‘always on’ admin rights – also known as standing privileges. Instead, elevated rights are granted only when they’re needed.
This may seem like a small change on the surface, but it makes a huge difference to your overall security posture. To understand why, it’s helpful to first recap some basics.
Find out more: Heimdal’s just-in-time access policies let you provide admin rights when they’re needed, and revoke it in time to stop the hackers. Find out more about our privilege elevation and delegation management suite.
What Is Just-In-Time Access?
Just-in-Time Access is the process that grants employees privileged access to applications and systems for a limited time, on an as-needed basis.
A good security plan means giving people and systems exactly the access they need to get their tasks done, and only for as long as they need it.
While organizations have made strides in implementing the “just enough” access component through privileged account management solutions, they tend to overlook the time-bound access aspect and ongoing risks associated with privileged access.
Just-In-Time (JIT) Access addresses this gap by only giving access to privileged accounts when it’s needed, based on what’s happening at the time.
This plan enhances overall company security by setting time limits based on behavior and context, giving you better access control.
For example, consider a usual always-on privileged account active for 100 hours weekly. By implementing just-in-time access management, you could cut down that active time from 100 hours to just a few dozen minutes.
Applying this change to all the access privileged accounts and user accounts in your organization will significantly decrease the risks.
The Risks And Dangers of Traditional Privileged Access Management
To understand why JIT policies are so effective, it’s helpful to explain the traditional model of privileged account management. This has effectively been the default setting for organizations for as long as they’ve been restricting access to sensitive information and data.
There are various tiers of admin access in an IT environment, including privileged business users, as well as local, domain, and root admins. Organizations generally try to reduce the number of admin accounts to a minimum – a principle known as ‘least privilege’. This states that an account should only have the minimum admin rights needed to complete its job.

The logic of least privilege is simple: The fewer admin accounts you have, the harder it is for a hacker to infiltrate them. And since privileged accounts are needed for most security attacks, this can make a significant difference to your overall security posture.
If a hacker manages to elevate privileges, they can usually then perform defense evasion, lateral movement, and access other credentials.
But if these three don’t happen, I can guarantee that the scale of their attack won’t be as big. That’s why managing privileged accounts is so important.
Andrei Hinodache, Cybersecurity Architect & Technical Product Marketing Manager, Heimdal
But there’s one crucial issue with this traditional setup: Standing privileges. This means that a single account either has privileges or it doesn’t. If it does, those admin rights can be used at any time, in any way, with virtually no restriction. This creates significant issues if your admin accounts are hacked.
To implement least privilege, it’s important to reduce the number of admin accounts in an organization as much as possible. But no company can operate entirely without admin accounts. That means there are still attractive entry points for hackers to target. Fewer privileged accounts equals less risk… but it’s not no risk at all.
Read more: Effective Privileged Access Management Implementation: A Step-by-Step Guide
How And Why Hackers Target Privileged Accounts
With a basic unprivileged account, hackers can do reconnaissance and identify what security tools you have. Then, they can see what users have logged in on that computer, what services are running, and identify what applications are being used and what versions.
This lets them work out what unpatched vulnerabilities they can use against you – all before they’ve gotten hold of local admin rights.
Andrei Hinodache, Cybersecurity Architect & Technical Product Marketing Manager, Heimdal
When a hacker first gains entry into your environment, there is a good chance they’ll first target non-privileged accounts. These are often easier to access because non-admins tend to be less security conscious, and their lower-risk accounts are subject to fewer controls.
Now the hacker has gained a foothold in your environment, they can start to laterally move. This essentially means they’re exploring your IT systems with the goal of accumulating further privileges. There are a number of techniques they can use to do this:
- Phishing: Tricking users into revealing sensitive credentials, usually via a link sent via email or SMS.
- Social engineering: Using additional tactics to trick users into revealing credentials, often impersonating trusted figures.
- Credential stuffing: Using common passwords (eg ‘Password123’) across all accounts, or using the known password of one user across all other accounts.
- Brute force: Deploying software bots to generate random password combinations until they find the right one.
- Software vulnerabilities: Exploiting weaknesses in software or endpoint codes to reveal privileged credentials or elevate permissions without needing to hack an admin account.
- Wi-Fi attacks: Creating a decoy Wi-Fi network in the hope that users attempt to sign in with their password and hand the credentials over to the hackers.
- Insider threats: A contact who already has access to the IT environment (usually a rogue employee) provides access to privileged accounts.
- Initial access brokers: Hackers can also buy credentials from other hackers, usually those who’ve already gained access and decided to sell it on the dark web.

All of these tactics are significantly easier once the hacker has a foothold – even if they don’t have privileged rights at this point.
But the real danger comes when the hacker gains some level of admin access. Even the lowest tier (local admin) gives them access to a whole range of malicious tactics, like installing malware, crawling active memory, disabling defenses, and removing evidence of their activities.
Read more: Admin Rights in Action: How Hackers Target Privileged Accounts
This is why standing privileges are such an issue. Here, there is nothing to stop the hacker performing any of these actions once they’ve accessed privileged accounts. The only option you have is to lock down the account entirely – which requires you first knowing that the hacker has accessed it, and then being able to stop them before they do any significant damage. Crucially, if they’ve hacked multiple accounts, you’ll have to lock down each one.
Just-in-Time Access (JIT Access) in Action: A Practical Demonstration
By removing standing privileges entirely, we can make life a lot more difficult for the hacker.
To understand how it works, let’s look at the example of Mark, the Head of Sales, who’s looking to install a (legitimate) new business app on their work laptop. As the head of a team, there’s a good chance Mark would have local admin rights if this was a traditional standing privileges setup, meaning he could install virtually any app onto his device, at any time.
But in a JIT access model, there are no standing privileges. Instead, Mark has to request access to install the app. Generally, he’ll provide a reason why and the request will then go to IT for approval. There are then two options for how the request is assessed and approved:
- Manually – A notification is sent to the IT team, who review the request and decide whether to allow the app installation. Since it looks like a legitimate business app, they have no issue granting permission.
- Automatically – IT teams can also configure a whole range of automated policies to govern who gets access, for what reasons, and for how long. This means simple requests like Mark’s can be automatically reviewed and access granted without IT teams needing to assess the request.
Once access is given, a notification will appear on Mark’s screen telling him that his request has been approved. Now, he has elevated permissions for a time-limited period and can install the app.
How JIT Policies Stop Hackers in Their Tracks
Now, let’s pretend that Mark’s account is being accessed by a hacker looking to plan an attack. In this example, the hacker is trying to install Mimikatz, a well-known malware application that would allow them to extract information from the device’s active memory.
In a traditional standing privileges setup, the hacker would be able to install Mimikatz as soon as they had access to Mark’s account. With just-in-time access, things are very different.
To install the malware, the hacker has to request privileges – just like Mark did when installing his new sales app. That in itself is probably enough to stop the malware, since the hacker likely doesn’t want to draw attention to themselves.
But what if the hacker did send through a request? At this point, there would be a number of protections in place to stop them from progressing:
- First and foremost, the hacker would have to provide a convincing reason to explain why they need the admin rights. If they were smart, they’d pretend they’re trying to install a legitimate business app to get the temporary admin rights. This, however, requires them already knowing the JIT system is in place and knowing enough about Mark’s activities to effectively pose as him – not an easy hurdle to clear.
- By all likelihood, the hacker has accessed Mark’s account from a remote device and location. Automated JIT workflows can be programmed to only grant admin sessions when the request comes from a trusted device or location.
- Known malware like Mimikatz can be easily blacklisted. If there is any evidence of the hacker attempting to install this malware, access can be immediately revoked or denied.
- A number of other contextual signals can give the hacker away, since the tactics they use to perform reconnaissance or remove evidence of their activities are often quite anomalous. Once detected, access can again be revoked or denied.
- The hacker may have used a software vulnerability to get access to Mark’s account. If the security system detects a known unpatched vulnerability, it can deny admin access.
This creates a number of hurdles that the hacker needs to clear in order to gain the permissions and conduct their attack.
Read more: Privileged Access Management Features: What You Need in Your PAM Solutions
… But Not All JIT Products Are the Same
JIT access can provide multiple layers of defense against hackers. If anomalous or suspicious behavior has already been detected, admin rights likely won’t be granted in the first place. If the hacker is granted admin rights and then attempts to install malware like Mimikatz, it can be immediately revoked again.
This is just one example of an activity a hacker might be looking to complete – albeit a very common one. But there is a whole range of other signals that could give them away. In order to catch them, your JIT workflows need visibility over a whole range of realtime information:
- Privileged account analytics – This will help identify when privileged accounts like Mark’s are engaged in anomalous activities like crawling active memory, deleting .log files, and more. This is generally collected through privileged account and session management (PASM) or security information and events management (SIEM)
- Malware detection – This is useful for identifying malicious installations like Mimikatz. These applications can be detected by endpoint detection and response (EDR) tools, SIEMs, or antivirus software.
- Phishing – Hackers may use this tactic to accumulate extra privileges after infiltrating the IT environment. Generally, they can be detected by email security tools, specialist anti-phishing software, or web filtering tools.
- Unpatched vulnerabilities – These are a common way for hackers to accumulate extra privileges. If a user’s device has unpatched vulnerabilities, they’re likely a more attractive target for attackers, and therefore shouldn’t be granted admin privileges. EDR tools and vulnerability scanners are the best products to identify vulnerabilities.
- DNS threats – DNS threats can also be evidence of malicious activity. This can include unpatched network vulnerabilities, as well as evidence of tampering, man-in-the-middle attacks, tunneling, spoofing, rebinding, and more. These are generally identified and prevented by specialist DNS monitoring tools, such as network intrusion detection or prevention systems (NIDS or NIPS).
By now, you’re probably starting to see the potential issue. For JIT access to be effective, it requires oversight over a whole range of information that’s traditionally collected by multiple siloed cybersecurity solutions. That includes other privileged access management tools, as well as SIEMs, EDRs, antivirus, email security, DNS monitoring tools, and much more.
So wouldn’t it be good if you could access all these insights from a single dashboard?
Heimdal: The World’s Widest Cybersecurity Platform
The problem with traditional cybersecurity platforms is this: All the insights we discussed in the last section are traditionally monitored by separate tools, with different dashboards, automated responses, and solutions.
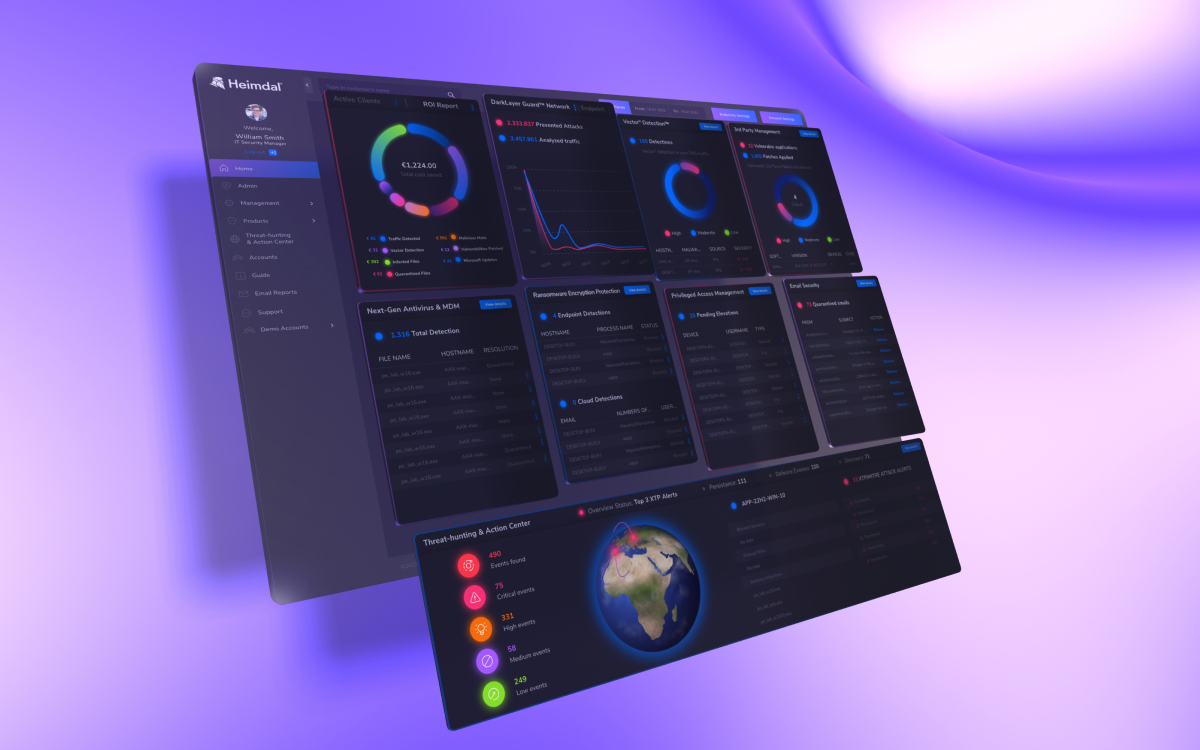
When it comes to just-in-time access, the more information you have, the stronger your policies will be. With Heimdal, you get access to a single dashboard that combines information from a whole range of cybersecurity products, including:
- Network security;
- Endpoint security;
- Vulnerability management;
- Privileged access management;
- Email and collaboration security;
- Threat hunting;
- Unified endpoint management.
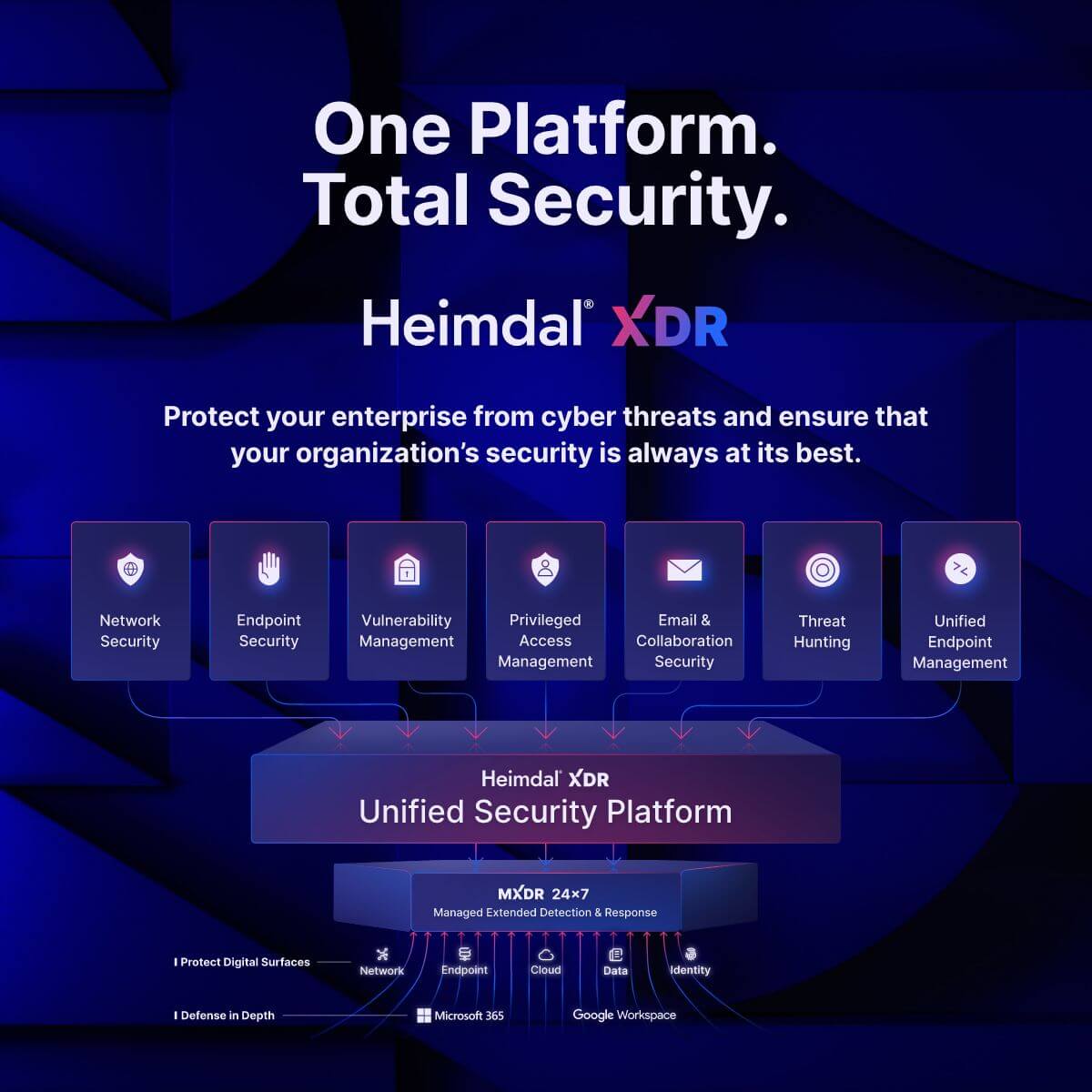
With Heimdal, your just-in-time policies can take into account information from the whole range of cybersecurity products. This makes them more informed, responsive, and, ultimately, better at stopping hackers.
Want to find out more? Check out our full XDR suite here or find out more about our just-in-time access products.
FAQs: Just-in-time access
What is just-in-time access?
Just-in-time access is a security policy that ensures admin rights are given on a case-by-case basis, rather than certain individuals always having elevated rights. When a legitimate business user requires admin rights, they simply request it and provide a reason, before being granted the rights for a time-limited period. This makes it more difficult for hackers to gain and misuse admin rights.
How do I enable just-in-time access?
Just-in-time access is an advanced cybersecurity tool that’s often purchased through specialist privileged access management (PAM) products. Generally, they’re included in privileged elevation and delegation management (PEDM) platforms, though some security providers may choose to include them in different platforms.
Why is just-in-time access better for security?
Just-in-time (JIT) access allows companies to grant admin rights for time-limited periods and for specific reasons. This avoids the trap of having ‘standing privileges’ – i.e. accounts that always have elevated permissions. Standing privileges are a gift to hackers because it lets them conduct a whole range of malicious activities if these accounts are hacked.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security











