Contents:
When you log into your online accounts (a process known as authentication), you are demonstrating to the service you want to use that you are who you claim to be. Historically, this has been done through the use of username and password.
Unfortunately, nowadays, this simple authentication method is just not enough anymore. Usernames are frequently easy to track down, and in many instances, they are just the user’s email address. Additionally, individuals frequently choose easy-to-remember passwords or use the same one for multiple different websites and services.
These are the reasons why practically all online services, including those offered by banks, social media, shops, and others, have added an additional method to boost the security of your online accounts. It may be referred to as Two-Step Verification or Multi-Factor Authentication, but both have the same principle. When you sign into your account on a new device or app, you are required to provide more than just username and password. You need a second, third, or even fourth verification factor to validate your identity.
Since two-factor authentication was already discussed in a previous article, this one focuses on multi-factor authentication, what it is, how it works, pros and cons, and much more. Let’s begin!
Definition of Multi-Factor Authentication
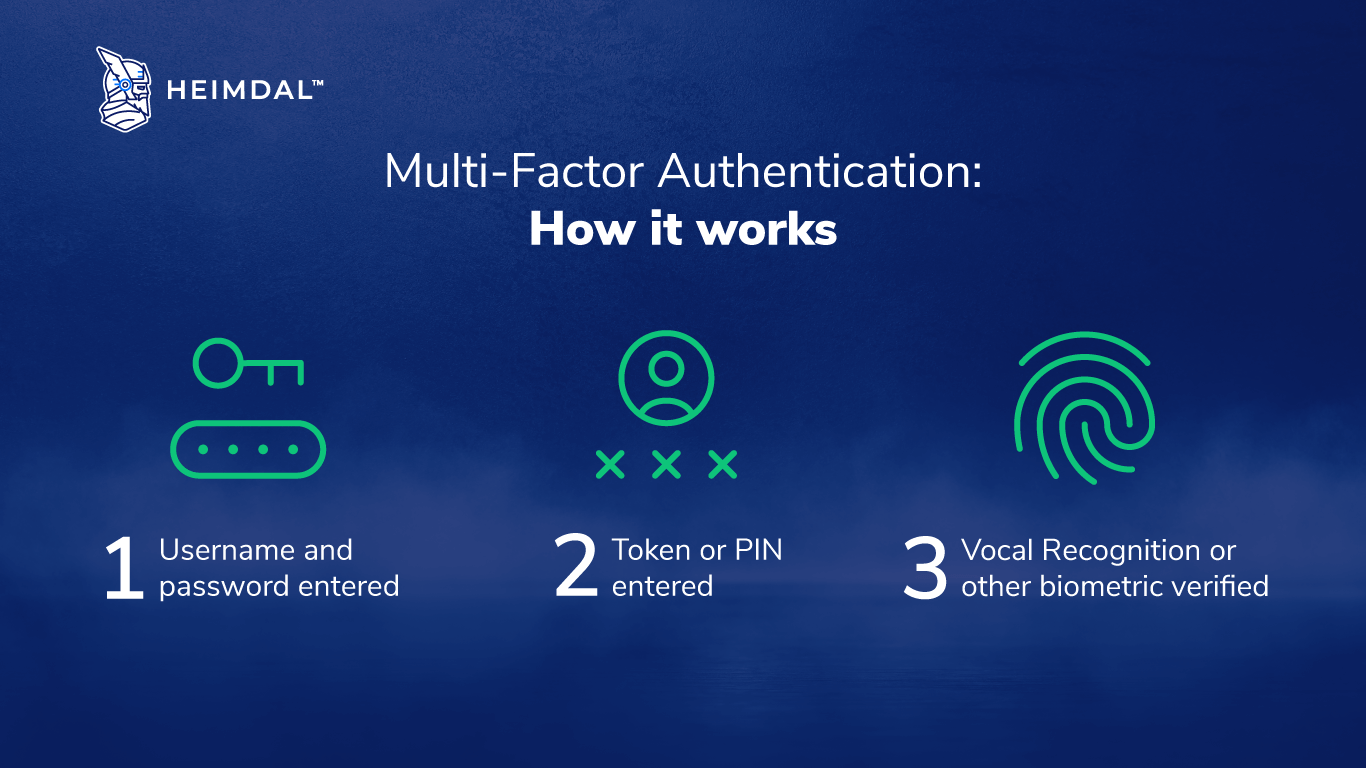
Multi-Factor Authentication (also known as MFA) is a security technology that requires users to confirm their identities by providing several proofs before obtaining access to a resource such as an application, online account, website, or VPN. So, rather than relying solely on traditional verification factors such as username and password, MFA necessitates authenticators from at least two or three categories.
The three basic factors of authentication are:
- Knowledge Factor – something you know, like a password, pin, or answers to personal security questions such as what is your first pet’s name.
- Possession Factor – something you have, OTPs (one-time passwords) generated by smartphone apps or sent via text or email
- Inherence Factor – something you are, such as biometrics like fingerprints, vocal or facial recognition
MFA is a critical component of a robust Identity and Access Management (IAM) strategy that boosts security. Think of a scenario when one authenticator becomes compromised. Unauthorized parties won’t be able to access the targeted computer system because of the MFA approach’s capability to prevent them from meeting the second authentication step. Thus, requiring additional verification factors minimizes the possibility of a successful cyberattack.
In essence, this multi-layered security system prevents unauthorized third parties (who may have discovered a password or a username) from accessing user information such as confidential personal or financial details.
MFA vs. 2FA
Because malicious actors discovered efficient methods to bypass single-factor verification, Multi-Factor Authentication (MFA) and Two-Factor Authentication (2FA) have become essential for enterprises to safeguard user accounts, assets, and data, as well as to keep users safe. But how do 2FA and MFA differ from one another?
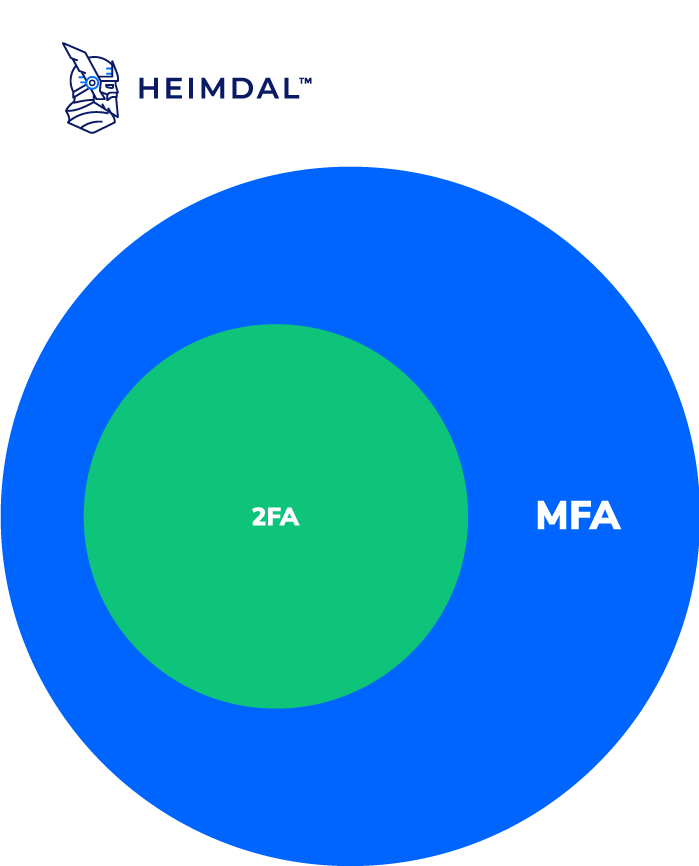
As explained previously, Multi-Factor Authentication (MFA) is a method of authentication that requires two or more verification factors, whereas Two-Factor Authentication (2FA), as the name suggests, requires only two.
So we can say that Two-Factor Authentication is a subset of Multi-Factor Authentication, meaning that every Two-Factor Authentication is also a Multi-Factor Authentication, however not every Multi-Factor Authentication is Two-Factor Authentication.
How Secure Is MFA?
Although implementing MFA is recommended for all enterprises worldwide and is unquestionably more secure than using just a login name and password, how safe is it really?
Unfortunately, more and more common MFA methods, such as one-time passwords (also known as one-time authorization codes or dynamic passwords) and voice calls or push notifications sent to mobile phones, are being targeted by threat actors. This includes specialized services that rent out bots that collect OTPs to assist cybercriminals in circumventing certain MFA mechanisms.
Other operations, such as those carried out by the Lapsus$ hacking group, which recently compromised Samsung, Microsoft, and Okta, get through MFA security by employing approaches such as social engineering, SIM-swapping scams, and escalating attacks using hacked secondary accounts. The fact that malicious actors can bypass MFA so easily has shown that, unfortunately, most MFA solutions are vulnerable to attacks, although some solutions provide significantly stronger protection than others.
Common Methods Used to Bypass MFA
According to the FBI, there are several known methods used to bypass Multi-Factor Authentication:
- The first is known as SIM switching or SIM swapping. In this situation, cybercriminals can get your phone number reassigned to their SIM. The intruder will essentially disconnect your phone number and assign it to their SIM card, which they have inserted into their device. They can then change account passwords and take control of any factor authentication method that goes to your device via SMS. They can start logging into multiple accounts, including email, online payment systems, social media platforms, shopping, and more.
- Technical loopholes are another threat mentioned by the FBI. In this case, a threat actor might manipulate the MFA to accept a fake PIN. The MFA system is “misled” into believing the hacker provided the correct PIN.
- Another MFA workaround is called social engineering. This type of attack exploits people’s genuine sociable character to deceive or manipulate them into disclosing personal information that could be used in fraudulent operations, malware distribution, or gaining access to restricted systems.
- Man-in-the-Middle attacks. A Man-in-the-Middle (MitM) attack occurs when a threat actor deliberately intercepts or listens to communications between two parties, often two users or, sometimes, a user and a server or app. By doing so, they are able to collect data sent by users, including login information, payment details, and credit card numbers.
- And, of course, phishing: an attack in which threat actors use bogus emails or text messages to trick a victim into replying with their credentials.
Benefits of Multi-Factor Authentication
Here are some of the advantages of implementing MFA in your organization:
- Increased protection: It provides extra defense for both clients and personnel across numerous security layers. Your overall cybersecurity plan is strengthened every time you add a new layer of security. For instance, if a malicious actor manages to obtain access to an employee’s credentials using a brute-force attack, having an additional verification factor will prevent them from proceeding with the attack.
- Security of valuable data. Fundamentally, when you implement multi-factor authentication, you’re safeguarding sensitive data.
- Device loss or theft. If one of your employees misplaces a device or has it stolen, which is a very real and increasing chance because of remote work, you don’t have to worry as much about compromised information or access.
- Increased customer trust and loyalty. Clients and employees can feel more secure about their data thanks to additional security checks.
- Lower operational costs. The risk of intrusions from data breaches is lowered in direct proportion to the number of layers, which results in reduced investment.
- Achieve compliance When it comes to adhering to certain industry guidelines, implementing multi-factor authentication may be an important requirement.
- Better flexibility and productivity. The ability to eliminate the stress of having to remember so many passwords results in increased productivity.
Multi-Factor Authentication Downsides
While the benefits of MFA outweigh the drawbacks, you must evaluate both before making any cybersecurity decision or investment for your firm. Potential disadvantages of multi-factor authentication can include:
- Having to deal with a second, third, or fourth verification factor might be stressful for employees.
- Multi-factor authentication setup can be costly and take too much time.
- A phone is needed to receive a text message code.
- Hardware tokens can be misplaced or stolen by malicious actors.
- Phones can get lost or stolen.
- The biometric data generated by MFA algorithms for personal IDs, such as fingerprints, are not always precise and can result in false positives or negatives.
- Network or internet outages could lead to MFA verification failure.
- MFA systems must be continuously updated to safeguard against hackers who are working diligently to compromise them.
Wrapping Up…
The main takeaway of this article is that while Multi-Factor Authentication(MFA) is a great security measure and an important one in the continuing era of remote work and BYOD policies, it’s not enough. The emphasis right now needs to be on strong, all-encompassing cybersecurity strategies. One of the best options is zero trust (“never trust and always verify”), which considers any individual and device attempting to connect to a network as a possible threat. MFA can be one component of the zero trust security model, but definitely not the only one.

Heimdal® Privileged Access Management
- Automate the elevation of admin rights on request;
- Approve or reject escalations with one click;
- Provide a full audit trail into user behavior;
- Automatically de-escalate on infection;
Implement Zero-Trust in Your Organization. Get Started with Heimdal ®
Heimdal has a product that facilitates zero-trust implementation effortlessly: it’s called Privileged Access Management and supports a zero-trust function.
PAM is an automated tool that permits you to escalate and de-escalate user rights, giving you full control and protection over privileged permissions within your organization.
In the Privileges & App Control – Privileged Access Management view, you can find the Zero – Trust Execution Protection display that includes many details like the processes (non-signed executable files) that the zero trust execution protection engine intercepted with data on Hostname, Username, Process Name, MD5 Hash, Timestamp, and Status.
The Zero trust execution process within the Heimdal Privileged and Access Management allows you to safeguard your environment from zero-hour threats (it can be enabled/disabled from the Endpoint Detection -> Next-Gen Antivirus module as well as the Privileges & App Control -> Application Control module).
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










