Contents:
Authentication and authorization are two concepts of access management that make for the perfect combo when speaking of ensuring a thorough cybersecurity strategy for a company.
Read on to gain more knowledge on authentication and authorization definitions, the difference between authentication and authorization, and how our solutions can help you in this case.
What Is Authentication?
The authentication process refers to verifying someone’s identity or determining that they are who they claim to be.
For instance, if you need to gain access to a system and you are required to fill out your username and password, these are checked against a specific database following your input. After this step, if the submitted data matches, you are granted system access.
Another example of authentication would be when two devices are set in different locations and initiate communication. Through authentication, these basically establish a trust level.
What Is Authorization?
Authorization is the process of granting someone permission to do something or access a certain resource after checking their level of access and after the authentication process is completed. This permission can be granted by a person or an automated system. Authorization is usually done with the goal of preventing unauthorized access to resources.
For instance, you may be authorized to use standard apps at your job, but you might not be authorized to use some applications reserved only for admins. To gain access to restricted areas you should be authorized through a privileged access management system for example, that assigns you limited privileged permissions.
Authentication vs Authorization
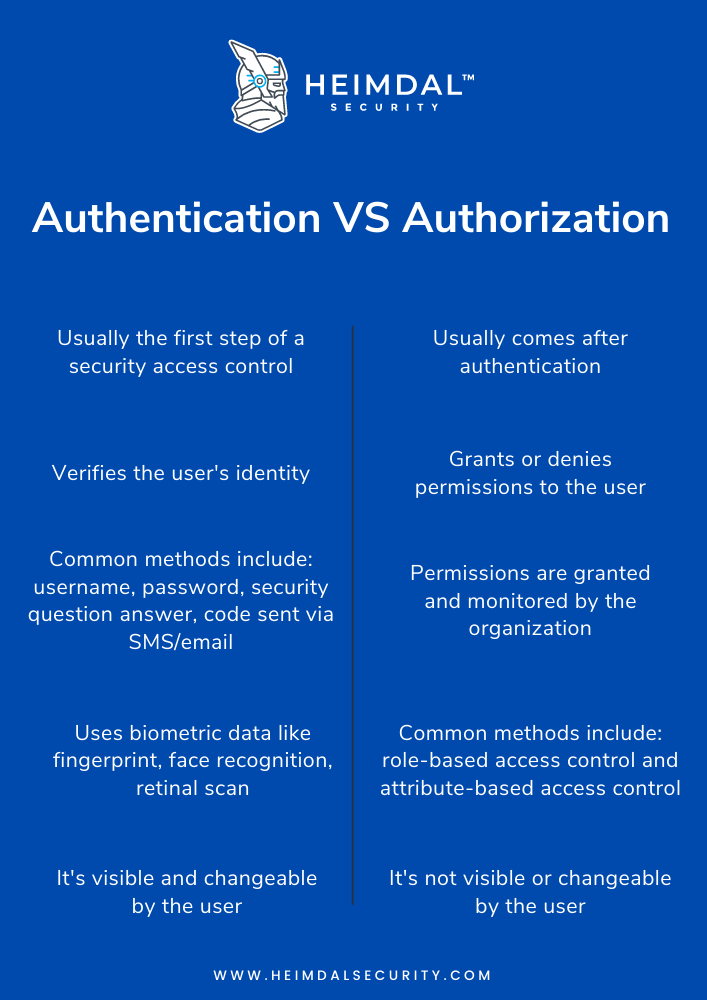
Authentication and authorization are pretty straightforward: user authentication checks the identity of an individual, followed by authorization which authorizes what apps, files, or data the user who had previously authenticated has access to.
The difference between authentication and authorization can also be explained in that authentication uses passwords or biometric data to validate the identity of the user, while authorization follows some settings established and managed by the company. So, obviously, when speaking of an access management process the authentication phase comes first, then authorization follows.
The authentication process is visible to the user, while authorization is not, because it consists of a set of settings already established within the company that are not visible to the user and upon which the user has no power in terms of modifying or altering them.
Another difference between the two concepts is when speaking of authentication, data is transmitted via ID tokens, and when talking about authorization information is transmitted via an access token. An authentication process verifies the user, while an authorization process validates the user’s access.
It’s worth mentioning that both processes should function in synergy, because if one fails, then the door is left open to security gaps.
Why Are Authentication and Authorization Important?
The main goal of authentication and authorization working together is to prevent cyberattacks that involve data breaches. Thus, authentication and authorization combined are important because:
- limits data breaches by securing the organization’s network at a granular level through centralized access controls (especially through authorization);
- has a focus on privileged access and its scope;
- prevents financial and reputational damage;
- permissions limit the activities and the information a user can have access to and limits thus lateral movement across the network if a hacker had gained access to a compromised account;
- helps detect unauthorized activity on a network;
- user productivity is managed and enhanced;
- helps you meet compliance.
Authentication Methods
Authentication methods usually rely upon the three “w”: what you know, what you own, and what you are. Therefore, among the most common authentication methods we can mention:
“What You Know” Authentication Methods or Knowledge Authentication Factors
- Password-based authentication: it will require the user’s username and password. However, weak passwords can be easily hacked through brute force attacks, so it’s not always the best authentication method.
- Security questions;
- Personal identification number (PIN);
- Date of birth;
- Social Security number;
- Or other personally identifiable information (PII).
“What You Have” Authentication Methods or Possession Factors
- Hardware access token;
- Software token;
- Digital ID card;
- Keys;
- Swipe card;
- Authentication applications on your phone: I’m sure you’re familiar with these kinds of apps that generate security codes to let you authenticate;
- Security certificates;
- Single sign-on: large enterprises with various systems and platforms utilize this authentication process to give users instant access to all of their apps;
- Paswordless authentication: this method works through one-time PINs. These are mechanisms that ensure that the access is granted for one session at a time through a one-time password or the user will receive a link they should access to complete the authentication phase. This technique is also frequently met under OTP-based authentication.
“What You Are” Authentication Methods or Inherence Factors
- IAM-driven biometric data: this method asks for user biometric info like a fingerprint, retinal scan, facial recognition, and voice recognition.
As we can see from all these examples, the authentication process falls under the Identity and Access Management area we’ve talked about thoroughly in a previous article. And of, course, authentication can happen via single-factor authentication when only one authentication factor is required to assess the identity of the user, or two-factor authentication and multi-factor authentication that uses two, respectively multiple authenticator factors to check the user’s identity.
Authorization Methods
Once the authentication step is completed, users naturally need to gain access to specific data to perform their tasks. Thus, they need authorization and among the most encountered authorization methods we can mention:
Role-Based Access Control
Role-based access controls (RBAC) is an authorization method that restricts access to particular resources based on the role assigned to a user or group and adheres to the idea of least privilege access, which asserts that a system should provide each user with only the limited resources they require to complete their job. Role-based access control has become more popular in recent years as it provides better security than other methods of restricting network or system access. It also offers more flexibility for managing privileges and resources, as well as for assigning different levels of privilege to different roles. Thus an HR employee will only have access to HR-related resources, and not to those from the finance department let’s say.
Attribute-Based Access Control (ABAC)
Attribute-based access control (ABAC) is a type of access control that is more granular than RBAC and allows the owner of an object to assign security attributes to it, and then use those attributes to define who should be granted access to it. An attribute can be data about the user (name, role, ID), data about the environment (access time, data location), etc. The main advantage of attribute-based access control is that it can be applied without the need for complex rule sets. It also has the advantage of being able to be applied at different levels in an organization. This type of security also has some disadvantages, for example, it can be difficult to enforce since it relies on accurate and up-to-date attribute information about both subjects and objects.
JSON Web Token
JSON web token or JWT stands for an open standard that allows the secure transmission of data between parties. In this case, users are authorized by means of a public/private key combination. Metadata is included in JWTs, permitting admins to restrict a user’s access to certain resources.
Security Assertion Markup Language (SAML)
SAML stands for an XML-based protocol, basically a mechanism that allows Single Sign-On format (SSO) for web apps, in which authentication information is communicated via digitally signed XML documents. In terms of authorization, SAML can be employed by admins to establish which resources users can access.
OpenID Authorization
OpenID authorization checks a user’s identity via authentication from an authorization server. The fundamental benefit of OpenID authorization is that it is based on standards, therefore it works consistently across systems and platforms.
OAuth Authorization
When we talk about OAuth we refer to an open-standard authorization framework that enables secure designated access within applications. OAuth usually relies on permission tokens to establish a connection between users and service providers.
Access Control Lists (ACLs)
Access Control Lists (ACLs): these specify which people or services have access to a certain digital environment, an access control achieved through the establishment of allowing/denying rules in relation to the authorization level of the user. To put it simply, standard user accounts will not have the same authorization as admin user accounts that have privileged permissions.
Device Permissions
Device permissions involve that the permission will be given in relation to the device that is trying to establish a connection with a resource.
Location Permissions
Location permissions consider the location of the user or the entity and provide permission accordingly.
Discretionary Access Control (DAC)
Privileges are assigned by DAC based on the user and their access groups. A DAC model allows a specific group or identity to access every object in a system. Once a user has been granted access to an object they can grant access to other users as needed.
Mandatory Access Control (MAC)
At the operating system level, MAC determines entity authorization. Permissions for threads and processes are often controlled by MAC, which establishes which files and memory objects they can access. Individual users cannot set, amend, or remove permissions in a way that is not in accordance with current policies as these policies are managed by an admin.

Heimdal® Privileged Access Management
- Automate the elevation of admin rights on request;
- Approve or reject escalations with one click;
- Provide a full audit trail into user behavior;
- Automatically de-escalate on infection;
How to Implement Authentication and Authorization with Heimdal
Within the organizational architecture, centralized privileged access management systems can play a significant role in providing robust user authentication and authorization.
Since authorization implies firstly user authentication and then granting permissions or privileges, and because those privileges can be enforced and managed through a privileged access management strategy for instance, here is where a PAM solution comes into play allowing you to control the big number of the privileged accounts you have within your organization and assure the right people have the right authorization to perform their tasks.
In this case, for granting privileged access, authorization comes in the form of privileged access management. To properly implement a PAM strategy, you need, of course, an automated PAM tool. If you choose Heimdal Privileged and Access Management you will benefit from:
- a smooth approval/denial flow for privileged access from anywhere;
- automate de-escalation of rights on threat detection;
- a zero-trust component, that is an essential element in implementing a proper authorization strategy;
- just-in-time access: this limits the timeframe a user with privileged access has to perform what they need to do during an elevated session;
- it supports Privilege Elevation and Delegation Management eliminating the risk of over-privileged accounts through its non-privileged user account curation capabilities for AD (Active Directory), Azure AD, or hybrid setups.
All of these features of privileged access management help ensure a proper authorization strategy that limits insider threats through the control over privileged access and thus dramatically reduces security risks for an organization.
Wrapping Up
Now you understand what authentication vs authorization means, what the main differences between the two concepts are, and how a privileged access management strategy can help you ensure a proper user authentication and authorization strategy in your company. And if you want to try out our products, feel free to contact us at sales.inquiries@heimdalsecurity.com or BOOK a DEMO.
Did you enjoy this article? Follow us on LinkedIn, Twitter, Facebook, Youtube, or Instagram to keep up to date with everything we post!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










