






Access Management | QUICK READ




Access Management | INTERMEDIATE READ


Access Management | INTERMEDIATE READ

Access Management | INTERMEDIATE READ

Access Management | INTERMEDIATE READ
BeyondTrust vs. Delinea: Best Choice for PAM?
Comparing Features, Performance, and Security in PAM Solutions.

Access Management | INTERMEDIATE READ
BeyondTrust vs. CyberArk: A PAM Comparison
Exploring the Pros, Cons, and Alternatives for Managing Privileged Access
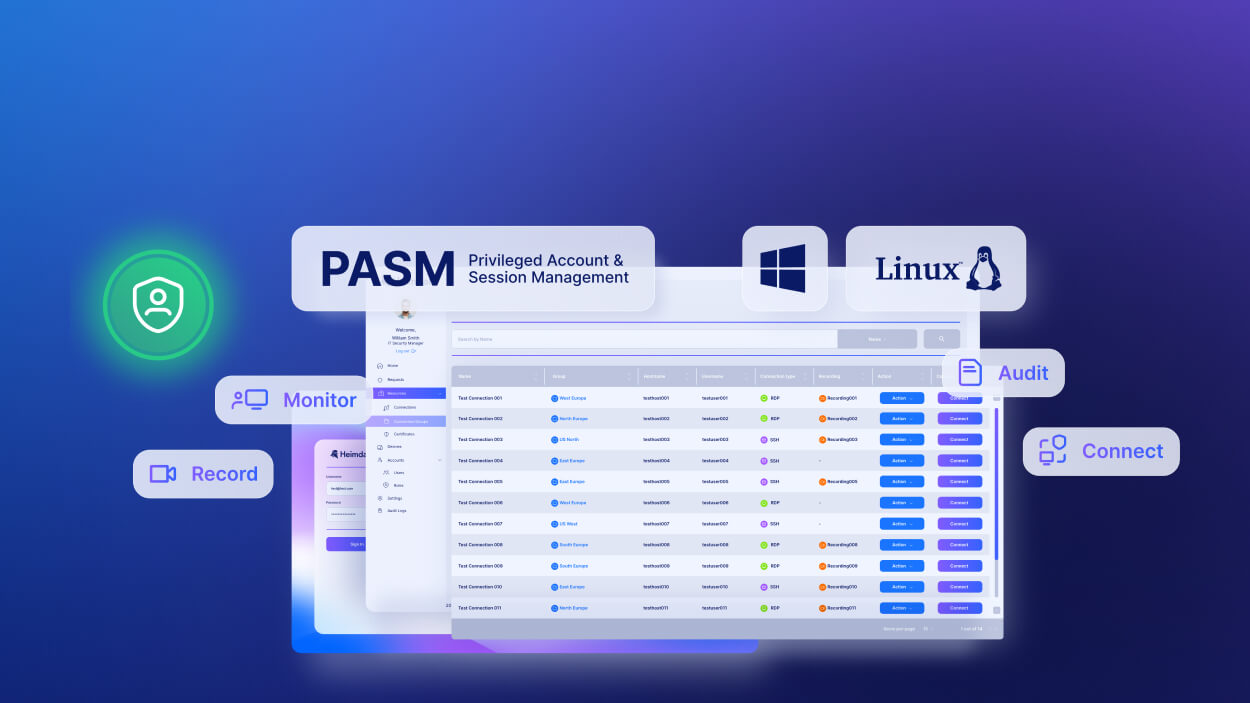


Access Management | SLOW READ

One Platform. Total Security.
Experience the Power of Heimdal XDR the Unified Security Platform that Delivers Comprehensive Protection against Next-gen Threats