Contents:
Also known as SIM splitting, simjacking, SIM hijacking, and port-out scamming, SIM swapping is a type of fraud that targets your personal information so that cybercriminals can pass themselves off as you and access your bank accounts. In short, the fraud takes aim at moving control of someone’s phone account from their SIM card to one controlled by the hacker. In general, most victims don’t know they’ve been compromised until they try to place a call or send a text message which doesn’t go through.
How Does It Work and Who Are the Targets
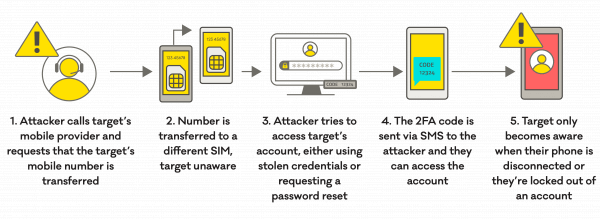
SIM swapping consists of three main phases:
#1. Social Engineering
Or most commonly the art of manipulating people into handing over sensitive information, such as passwords and personal data. Most SIM swap scams begin with a phishing email to try and manipulate you into disclosing personal information the attacker can then use to impersonate you. Cybercriminals will often follow your social network activity to get to know everything about you. And we all know that we share a lot on social media – from the street we live on, the name of our first pet, and what primary school did we attend.
#2. SIM swap
If you ever ask yourself how can someone access your SIM card, the answer is – quite easily. Remember all those Facebook posts? Hackers take their time and do their homework, gathering every piece of information they need to trick someone into thinking they’re you. Once they have enough personal insights, the attackers will call your mobile provider or use the online chat option pretending to be you. They’ll request a new SIM card in your name. And poof! – your private phone number is not so private anymore. Every PIN, every login, every verification method is now shared with the hacker.
#3. Fraud
The final phase in this process is carrying out a fraudulent act. Once they’ve gained your one-time PIN, or any other mobile-phone-related verification method, they’ll have access to all services and applications you’ve linked your phone to bank accounts, emails, pictures, call logs, text messages, etc.
Investigative journalist Brian Krebs noted:
In general, SIM swapping attacks primarily target individuals who are visibly active in the cryptocurrency space. This includes people who run or work at cryptocurrency-focused companies; those who participate as speakers at public conferences centered around Blockchain and cryptocurrency technologies; and those who like to talk openly on social media about their crypto investments.
But that doesn’t mean that the rest of us are safe. Anyone can become a target of SIM swapping.

Heimdal® Email Security
- Completely secure your infrastructure against email-delivered threats;
- Deep content scanning for malicious attachments and links;
- Block Phishing and man-in-the-email attacks;
- Complete email-based reporting for compliance & auditing requirements;
How to protect yourself from a SIM card swap attack:
- Never reply to calls, emails, or text messages that ask for your personal information. They’re most likely phishing attempts by scammers looking to get personal information to access your mobile phone, bank account, social media, or other accounts. If by any chance you get such a request, you should try to contact that particular company using through an official phone number or website.
- Mark my words: you should limit the personal information you share online as much as you can. Avoid disclosing your full name, sharing your address, or phone number on public websites. There’s nothing easier for an identity thief to track down that content, use it to answer the security questions required to authenticate your identity, and log in to your personal accounts.
- Always set up a PIN or password with your service provider to access your phone for any online or phone interactions. This way, you can help protect your account from unauthorized changes. You can always check for more details on how to do this on your provider’s website.
- Never use the same passwords/PINs/usernames over multiple accounts. Instead, create a strong, unique password for your sensitive personal/financial accounts. For more actionable tips on this subject, you can read our password security guide.
If you’re the target of a SIM swap scam
- Immediately contact your service provider to take back control of your phone number. After you re-gain access, change your account passwords.
- If you notice any unauthorized charges on your credit card, bank, and other financial accounts, immediately report them to the institution in question. Additionally, you should put a security freeze on your credit report. In case of identity theft, it will prevent any openings of new accounts in your name.
Wrapping It Up…
Never click on links or attachments in suspicious emails or text messages. Trust your gut and keep in mind that your bank will never send you an email, or call you on the phone, asking you to share personal information such as passwords, credit or debit card number, or your mother’s maiden name. You should just listen to what your intuition tells you. If something feels wrong, even if you cannot specifically explain why, or if it’s too good to be true, it’s better to stay away from it.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










