Contents:
On April 26 I’ll be “celebrating” 6 years since I got hacked.
It was Monday, a beautiful spring day, when I woke up and realized that all my online accounts, my most precious work and personal assets, were gone.
Back then, at only 22 years old, I was running the most popular music blog in my country (also the first local blog to be sold). I had a team of 10 editors and contributors, we were all working from a small central office. With almost 10.000 unique visitors per day that were leaving thousand of comments, that blog was the most precious thing I had, and also my main source of income.
The number of hate comments and emails I was receiving was directly proportional to that. Articles attacking me were being published all the time. Trolls and DDoS attacks were the norm.
All that attention caused me to be a bit paranoid about my digital security and privacy. Friends were even making fun of me because of that. I thought I was doing everything right:
- I never logged in from other people’s computers.
- I only worked from my laptop, my home desktop and my Nokia E72 mobile phone (back then, Nokia was still one of the top mobile phone brands – yeah, I’m *that* old).
- All my passwords were strong and had more than 30 characters, both lower and upper cases + symbols and digits. I changed them almost monthly.
- Nobody knew the answers to my security questions.
- I had a top-notch antivirus installed on my device, that I was counting on for my protection.
But no matter how many security measures I had in place, I missed one. An essential one. I wasn’t “paranoid” enough to protect myself from the vengeful employee I had just fired.
At 2:44 AM, he managed to break into my main Gmail account. He deleted all the emails. I had been using that account since 2003, so it had lots of important documents on it, but also emails with sentimental value.
From there, he hacked into three other accounts that were linked to it: two more Gmail accounts and one Yahoo mail.
He also used my credit card, that was linked to Gmail for buying extra storage. He ordered a mobile phone from the U.S. to Europe: a $500 Nokia N97 + delivery taxes worth $97.
My website, my precious website… He deleted the entire database – more than five thousand articles and one hundred thousand comments.
But he didn’t stop there. He also breached the Twitter account used for promoting the website and had the tweets from the past couple of months erased.
How I regained access to my accounts
Yahoo was the first account that I was able to regain access to. Although the attacker changed the security question, I was also provided the option to answer my previous two security questions, that were set before the hack. This way, I reset the password.
I was using my Yahoo mail as an alternative to my main Gmail address. On it, there was a recent email from Google, saying that my Gmail will be deleted in two working days.
(Side note: Back then, if you requested to delete your Gmail account, Google would have deleted it in two days. This is no longer the case – now you can recover your data even a few weeks after your requested to delete your account. Also, deleting your Gmail address won’t free your username, so Gmail will help you recover it anytime you want it back.)
I completed a form to regain access to Gmail – had to use my Yahoo mail, give them 5 email addresses that I was frequently contacting, 5 mail labels, the date when I created that account and other such information, in order to confirm my identity.
In less than one hour, Gmail team let me know that they reset my email password and I regained access to it. However, it was too late for my emails – they were already deleted.
Afterwards, I used Gmail’s feature to see Last Account Activity, where they provide the last location (IP address) where the email was accessed from.
The hosting provider gave me the website logs, including the IP from where its database was deleted.
I alerted my bank and blocked my credit card, but I still had the contact information (name, mobile phone) and address to where the ordered phone should have been delivered.
Later that day, I discovered that my work laptop had a keylogger installed on it. The antivirus wasn’t detecting it because it was installed by someone who had direct access to it.
Armed with all this information, I went to the local police and filed a complaint. All the evidence pointed to my ex-employee’s direction.
Lessons I had to learn from this story – the hard way
It was a disturbing, unpleasant event, that caused me lots of grey hairs. It would have been a shame if I wouldn’t have learned anything out of it, right?
1. Never trust anyone: not your employees, not your buddies, not your brother or mother, nobody. You can never be too careful. You never know who’s standing right next to you. Even if you’d currently be willing to jump through fire for a person, you never know how your relationship is going to evolve in the long term.
Don’t leave your computer or mobile phone unattended, without a security password in place (a good one, too!). Don’t ever give someone else access to your devices, to your email account, to your work documents or to your passwords.
2. It’s important to activate the two-factor authentication – wherever it’s available. I didn’t get the chance to use it back then, as Google introduced it only later. I cannot help but wonder: had it been available, this whole ruckus probably never would have happened.
Check out this comprehensive guide on what two-factor authentication is and how to activate it.
3. Never recycle passwords. Just like me, most people have their digital accounts connected, linked between them. Unfortunately, that means that if one account is hacked, all others will fall down together with it, just like domino pieces.
A comparison at hand would be between our house and car keys: we don’t use the same key for both of them, right?
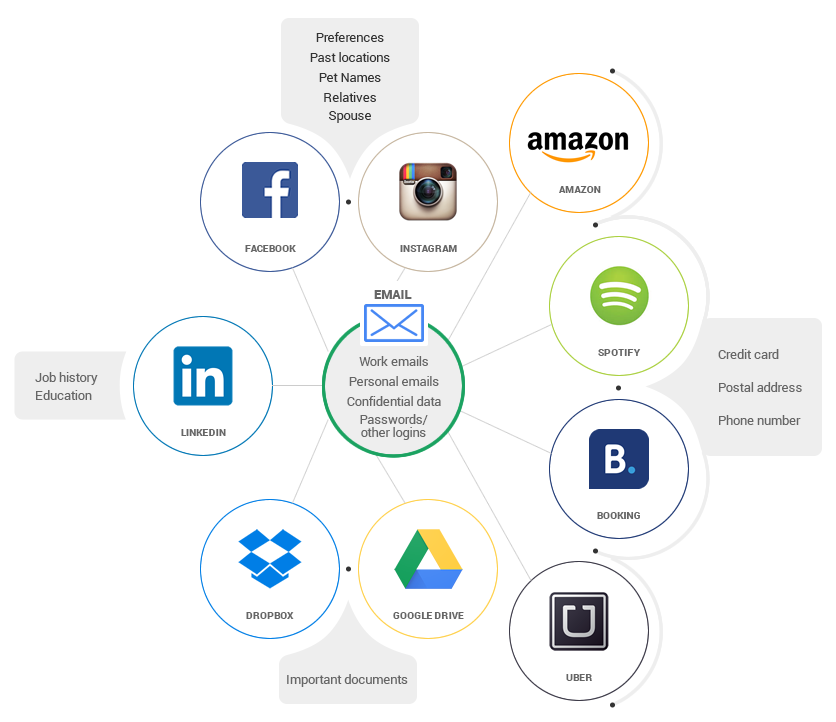
4. The importance of data backups. I had been using my Gmail account since September 2004, I had lots of important documents on it, but also emails with emotional value. Since I never backed up any of that, they were permanently gone. On the other hand, my website was up to date with its backup, so everything was back to normal in less than 12 hours.
5. Never, ever save credit cards data to any of your online accounts. Not your email provider, not your cloud provider, not your favorite e commerce retailer, nada, zip, zero, noooooo one. If you want to buy something online, take your time and fill in the credit card details every single time. It’s better to take your time and do this every time you want to buy something, instead of being lazy and risking card fraud.
It would be even better if you had a separate card, that you use only for online shopping and transfer money on it only for punctual transactions.
Bonus: Here are plenty of stories that will give you nightmares.
6. Don’t be influenced by the ones around you. Don’t let them get to you when they point out that you are exaggerating with your privacy issues or, even worse, when they mock you. Don’t pay attention to how much importance they give to their own online privacy and security. You can never be too “paranoid” about your online security and privacy.
7. That you shouldn’t rely exclusively on your antivirus for protection. No matter how good it is, it doesn’t protect you from all threats that are out there. It won’t protect you against a vengeful former employee or a disgruntled ex-boyfriend / ex-girlfriend.
Steve Anderson wrote more on this topic – in his article you’ll find more concerning facts about ex-employees and the threat they pose, but also a checklist with what to do when you fire someone, in order to protect your organization.
My story turned out ok, eventually. Nothing irreversible happened, I was able to do damage control. But I do hope that no one else will ever have to experience something similar.
However, in case that your email or website is ever breached, here are a few useful tips:
1. It’s important to make a request for data conservation. File it with your email provider, your hosting provider or any other involved parties. This will be helpful during trial, so that the data can be accessed and interpreted.
2. If you have files that contain useful data, proof, and they haven’t been modified (ex: server log), save them so that they can also be saved with the original timestamp. You can also use a free website, such as Safe Creative, where you can save them and they’ll provide you with a timestamp. This will prove to be helpful in case that the accused one will challenge the authenticity of your evidence.
3. Take print screens of the evidence in front of others. Try to take a screenshot in front of a neutral entity, such as a police investigator.
Here are more critical steps that you need to take in case one of your accounts is hacked.
***
Closure?
I never found out what happened to my ex-employee.
I remember that his mother called me and begged me to take back the police complaint I had filed. She believed her son would have never done such a thing and that everything was carefully planned by someone else.
After that, I tried to isolate myself from any kind of news related to him – I didn’t want to know anything, I didn’t care anymore. I was just furious with myself for being so naive and letting my guard down when I shouldn’t have. I should have known better.
And you should know better too.



 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










