Contents:
Internet crime stories are dime a dozen but these examples will show you why online security is essential. From ethical hacking to blackmail and car hijacking, these true stories show how you must act now to secure your well-being in the digital landscape. We carefully curated the best, most fascinating tech stories that cover the risks involved in any digital activity of device, so use the links below to navigate them.
- The mom whose laptop was locked down by a ransomware attack
- Tom was blackmailed because of his hacked Ashley Madison account
- How ethical hackers took over her PC
- They remote hacked his car
- Ransomware deletes 2 years of academic papers
- His WoW account got hacked. Twice
- Your data has been breached
- Catfish isn’t dinner, it’s lies, manipulation, and theft
- Hillary Clinton’s Aides Got Phished And Lost Her The Election
- He fell prey to the same scam twice and lost $1,350
- Who would want to be you? Some can even become You.
- When your workplace, a gaming giant, gets hit
- The casual, public Wi-Fi hack
- Customer support falls prey to a social engineering hack
- Hotel managers and clients had nightmares due to one lock hack posted
Cyber security incidents and getting hacked seem like distant, fascinating things where other people get hurt, but you stay safe. Truth is, getting hacked or scammed can happen to anyone and it might even have happened to you in the past.
The average number of devices used by you and most people have increased exponentially in the recent years. We’re surrounded by IoT devices, wear smart bracelets, have friends who are betting their savings on cryptocurrency, and we sign up to dozens of social media platforms.
This means cyber attacks have a lot of ways to get to you – either by targeting you specifically or by simply compromising your info in large-scale attacks. The best way to learn is through experience, so let’s do just that.
Here are the real stories of people who got hacked and what they learned, plus some actionable tips to enhance your security.
1. The mom whose laptop was locked down by a ransomware attack
Two days before Thanksgiving, Alina’s mother got hit by a ransomware attack. 5,726 files got locked by CryptoWall, an encryption malware so powerful it is almost impossible to recover the information.
Alina’s mom contacted the attacker through the ransomware’s communication feature.
As all ransomware creators, he told her she can either pay to get her files back or lose them forever.
Despite backing up her files 6 months ago, she decided that losing half a year’s worth of photos, documents and other files was too much, and so decided to pay the ransom. 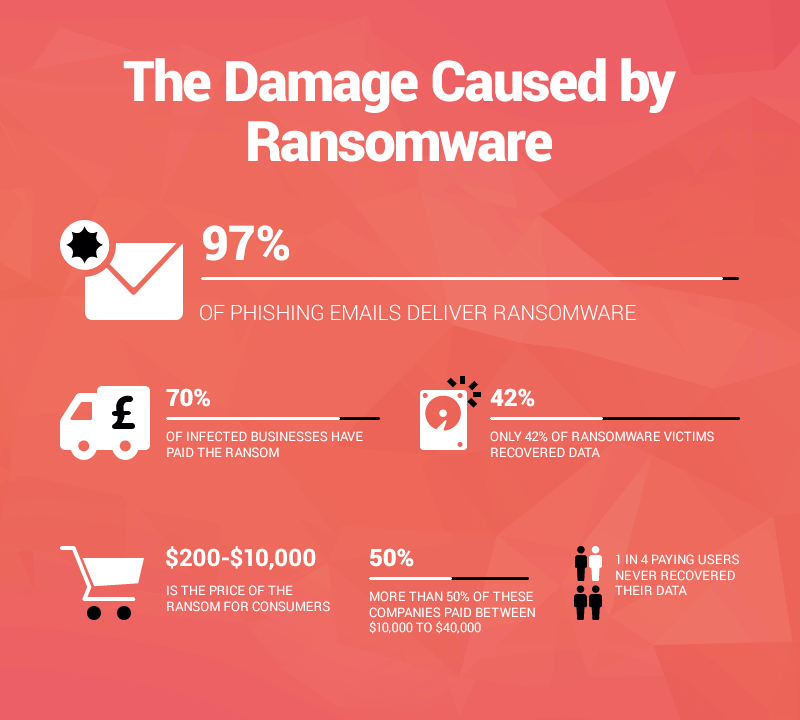
The price to unlock her files was 500$ in the first week and 1000$ in the second one, after which the files would be deleted.
Payment was to be done in Bitcoin, a complicated process which she had to learn on the fly.
Because of a major snowstorm that closed down the banks, Alina’s mom couldn’t pay the ransom in the first week, and ended up having to plead with her attacker to not increase the price to 1,000$.
Surprisingly, he accepted and gave her the key to unlock her files. However, no one should ever pay a ransom, the risks far outweigh the benefits.
The full story is here: How my mom got hacked & What I’ve learned after my mom got hacked (and her data held for ransom)
Find out what steps to take for your protection: WHAT IS RANSOMWARE AND 9 EASY STEPS TO KEEP YOUR SYSTEM PROTECTED
2. Tom was blackmailed because of his hacked Ashley Madison account
Sometimes it’s not your fault. The websites you use get hacked and your information is exposed. Your instinct will be to say: “but I don’t have anything to hide!” Well, that’s not exactly true, is it?  Tom started using Ashley Madison several years prior to it being hacked in 2015, as a way to cope with a strained marriage.
Tom started using Ashley Madison several years prior to it being hacked in 2015, as a way to cope with a strained marriage.
After the Ashley Madison hack, cyber criminals contacted him and demanded 500$ to remove his name from a publicly searchable registry.
If not, they would also send an email to his family, informing them of Tom’s affair. Tom refused, believing that if he paid them, they would know that he had something to lose and could be blackmailed further.
He was wise, but that didn’t mean he didn’t suffer. In the end, Tom had to live knowing his affairs on AM could be exposed at any time by the hackers.
Moreover, there were also people who took it up upon themselves to impart justice on people in circumstances they couldn’t, or wouldn’t, understand.
The story: In Ashley Madison’s wake, here’s one man’s story of sex, sorrow and extortion
Securing your PC doesn’t have to be expensive: 13 FREE PC SECURITY HACKS TO BUILD YOUR ONLINE PROTECTION
3. How ethical hackers took over her PC
Sophie is a technology reporter at the Daily Telegraph.
As part of an assignment, she accepted to be part of an ethical hacking experiment. Basically, a group of ethical hackers would try to compromise her system without her knowing how, when and where.
Sophie only knew that it would happen at some point. For a whole month, the hackers did an extensive research on Sophie, crawling through her Twitter and Facebook pages, Daily Telegraph articles and even found out her date of birth from a website on family trees.  Source Almost two months after the experiment began, the hackers launched their attack.
Source Almost two months after the experiment began, the hackers launched their attack.
They pretended to be whistleblowers in control of sensitive government information and sent her an email with some of the files attached.
The malware infection occurred the moment she opened the file, and the attackers got access to everything, including email address and web cam. And it wasn’t even that difficult to do.
The story: How hackers took over my computer
This is how you can protect your email address: THE COMPLETE GUIDE TO EMAIL SECURITY
4. They remote hacked his car
Andy Greenberg, a senior writer at Wired, once took part in a groundbreaking experiment which tested how car hacking could be done.
What did the experiment involve? His car would be remotely hacked while he was behind the wheel.  As Andy drove on the highway, the hackers started to progressively take control of the car. First, they activated the air vents and windshield wipers.
As Andy drove on the highway, the hackers started to progressively take control of the car. First, they activated the air vents and windshield wipers.
Next, the transmission was cut and finally, they remotely activated the breaks. And they did all of these things with Andy behind the wheel.
The experiment uncovered a massive flaw in Jeep’s cars which was later fixed. Today, this is even easier to achieve, due to the rise of electric cars and the huge push towards autonomous vehicles like trucks, taxis and more.
The story: Hackers Remotely Kill a Jeep on the Highway—With Me in It
Learn more about how software can expose you, something that works the same way whether we’re talking about computers or self-driving cars: 8 VULNERABLE SOFTWARE APPS EXPOSING YOUR COMPUTER TO CYBER ATTACKS
5. Ransomware deletes 2 years of academic papers
What’s the first thing people do when they get hit by a malware attack? They panic and ask for help in a dedicated forum: “My PC is infected.
Please, can anyone help me?”
For this user however, it was too little, too late. For 2 years he worked on his academic papers, and then they got encrypted by ransomware.
The timing was awful as well: it happened right before they were due. Antivirus didn’t help and he had no backup.
 We don’t know what happened next, or if he paid the ransom to unlock his files.
We don’t know what happened next, or if he paid the ransom to unlock his files.
We hope he didn’t pay.
What we do know is that ransomware attacks are much more frequent that you can imagine and they target individuals and businesses alike.
The story: My PC got hacked by troldesh ransomware. please is there anyone who can help.
Find out how to backup your data so ransomware does not affect you: HOW TO BACKUP YOUR COMPUTER – THE BEST ADVICE IN ONE PLACE
6. His WoW account got hacked. Twice
Gamers are favorite targets for cyber criminals, since they don’t want to lose the time and money invested in a character and are willing to pay the ransom.
As a result of a potential phishing attempt, this guy had his WoW account hacked and all his progress lost. And it happened to him not once, but twice!
To add insult to injury, the hacker created a new character named “Thanx” as a sign of appreciation for his “efforts” as a victim.  Fortunately for him, Blizzard customer service was responsive and recovered his account and all the progress it had on it.
Fortunately for him, Blizzard customer service was responsive and recovered his account and all the progress it had on it.
The same type of attack happens in most popular online games.
League of Legends phishing volumes are truly legendary, so we talked to their security team to find out how to avoid getting your account stolen.
The story: So my WoW account got hacked… twice.
Learn more about security and gaming: GAMERS, TIME TO TAKE YOUR CYBER SECURITY TO THE NEXT LEVEL
7. Your data has been breached
The Office of Personnel Management, OPM for short, can be considered the US Government’s HR Department.
Among other things, it keeps records of employee personal information, such as height, weight, hair and eye color.
In 2014, the OPM got hacked, and the information of 22 million government employees leaked, most likely in the hands of a foreign government.
Bad?
Well, the 2017 Equifax saga was a nightmare of epic proportions.  Source
Source
143 million US consumers had their sensitive personal information exposed. That’s 44% of the population and today we’re still seeing reports of more Equifax leaks.
Odds are, if you’re a US citizen, your info is floating around on the dark web, at the mercy of cyber criminals. What do you think the US government did to deal with the Equifax hack?
After less than one month since the incident, the IRS awarded Equifax a contract for fraud detection. Clearly, it’s up to you and you alone to protect your identity.
The story: OPM got hacked and all I got was this stupid e-mail
Learn how to stay as safe as possible from identity theft: HOW TO PREVENT IDENTITY THEFT IN 20 ESSENTIAL STEPS
8. Catfish isn’t dinner, it’s lies, manipulation and theft
Some people hack you not with malware or suspicious links, but by gaining your trust and love.
This journalist’s mother started using the online dating site Match.com, and eventually formed a connection with a soldier on active duty in Afghanistan.
After a while, the soldier asked for a 30,000$ loan to help him clear a sizeable inheritance of gold and jewelry from US customs.
By now, the journalist and her brother intervened, suspecting the soldier was catfishing their mother.
In online slang, catfishing means pretending to be someone else in order to extract financial gains. Or it can be a twisted way to get attention and affection.  Source
Source
In the Match.com case, the victims confronted the man with their suspicions and other evidence they had accumulated over time.
The supposed soldier revealed he was a man from Ghana trying to support his sisters, and scamming people online was the best way he knew how to do that.
The story: My mom fell for a scam artist on Match.com—and lived to tell the tale
Learn about the top online scams and how to avoid them: TOP 11 SCAMS USED BY ONLINE CRIMINALS TO TRICK YOU
9. Hillary Clinton’s Aides Got Phished And Lost Her The Election
Unless you’ve been living under a rock, you definitely know why Hillary Clinton lost the US Election to Donald Trump.
One of the biggest scandals of the decade was the Hillary Clinton leaked emails. Do you know how that happened?  John Podesta was phished. Yes, the chairman of Hillary Clinton’s campaign fell prey to a phishing attack. He received a suspicious mail and he wanted to flag it, but he made a typo.
John Podesta was phished. Yes, the chairman of Hillary Clinton’s campaign fell prey to a phishing attack. He received a suspicious mail and he wanted to flag it, but he made a typo.
When forwarding the phishing email to a computer technician, he wrote “This is a legitimate email” instead of “illegitimate”. This gave hackers from Russia access to about 60,000 emails from Podesta’s private Gmail account.
They stole all that data, gave it to Wikileaks, and the rest is actual history.
“The FBI’s laid-back approach meant that Russian hackers were able to roam inside the DNC’s computer systems for almost seven months before Democratic officials finally realised the gravity of the attack and brought in external cybersecurity experts.”
But it was too late, as the election results have shown.
The story: Top Democrat’s emails hacked by Russia after aide made typo, investigation finds
Learn why phishing is so effective and how you can avoid it: 15 STEPS TO MAXIMIZE YOUR FINANCIAL DATA PROTECTION
10. He fell prey to the same scam twice and lost $1,350
In 2007, Justin was at a difficult point in his life.
Unemployed, with a weak skill set and verging on alcoholism, Justin decided to turn his life around by moving to Italy.
Determined to find a cheap flight, Justin searched for sellers of frequent flyer miles.
He found two sellers and talked to them over the phone. One of them even sent him a photo of his driver’s license. In a twisted sequence of events, both of them scammed him for a total sum of 1350$.
Sounds unlikely?
Think again. Justin tried to find a cheap shortcut and get that ‘too good to be true’ deal and became blind to any potential scammers.
Plus, the phone conversations and photos helped dispel any suspicions he might have. This is how most scamming attempts succeed, by preying on people who give in to the fear of missing out.
The story: How I Lost $1,350 by Falling for the Same Internet Scam Twice in One Week
Learn more about how social scams work and how to avoid them: SOCIAL SCAMS – THE FULL BREAKDOWN AND PROTECTION PLAN
11. Who would want to be you? Some can even become You.
One day, Laura received a call from her credit card company, saying someone else had tried to obtain a credit card using her name, address and social security number.
Before telling the police, Laura decided to assess the damage and look over her credit card reports.  The impersonator had gotten so deep into the system, she managed to override Laura’s answers to the security questions.
The impersonator had gotten so deep into the system, she managed to override Laura’s answers to the security questions.
Eventually, she guessed the answers and saw the extent of the damage.
The impersonator had created more than 50 accounts in Laura’s name, and got credit for utilities such as heat, cable, electricity and even a newspaper subscription.
What’s more, the companies went after Laura in order to get their money back.
After notifying the police and tracking down the impersonator, Laura got a court order and managed to fix a lot of the damage, but only after a lot of sweat and stress.
While her case was a fortunate one, few people share her luck and this story should act as a reminder to always safeguard your personal information.
Another stolen identity case created a buzz on Reddit. This user had an argument with an old roommate, who then decided to take revenge.
He created social media accounts using the victim’s name, photoshopping the person with an ISIS flag and posting questionable content The story: ‘Someone had taken over my life’
While a scary and multifaceted attack, it is possible to protect yourself against these types of threats. Here are 20 SECURITY STEPS YOU SHOULD TAKE TO PREVENT IDENTITY THEFT.
12. When your workplace, a gaming giant, gets hit
In late 2014, one of the biggest and most expensive hacks ever recorded took place at Sony and one employee reveals the inside situation.
It took around a week for people who worked at Sony to get a grasp of the seriousness of the situation. Sony refused to inform them about the extent of the damage, so instead, they had to rely on news sources to get updated.  The next week after the attack, Sony employees found themselves thrown into the pre-PC age.
The next week after the attack, Sony employees found themselves thrown into the pre-PC age.
Half of the companies 6800 computers and servers were rendered dead and had ALL of their information stolen and deleted.
As a result, employees had to rewrite every single deleted file by hand. Paper became the main form of communication, used in written memos and to-do-lists, even their salaries were paid using hand-written checks.
The damage didn’t stop there.
The hackers got a hold of employee personal information. The source of the article had to change all her credit card passwords, Facebook, Amazon and eBay accounts, almost 30 accounts in total.
The story: I work at Sony Pictures. This is what it was like after we got hacked.
Because of their size and income, companies are frequent targets for hackers. Here is a LIST OF 10 CRITICAL CORPORATE CYBERSECURITY RISKS
13. The casual, public Wi-Fi hack
Maurits Martijn, a Dutch journalist at De Correspondent, entered a busy Amsterdam café with Wouter Slotboom, an ethical hacker.
Within a few minutes, Slotboom had set up his gear, consisting of a laptop and a small black device and connected to the coffeehouses Wi-Fi.
Soon enough, his laptop started to display what other people in the café were doing on their devices: what games they were playing, what apps they had installed, Google searches, password and email accounts and more.  According to Slotboom, it wasn’t even that difficult.
According to Slotboom, it wasn’t even that difficult.
All you needed was around $80-90 worth of software and equipment, an average intelligence and that was it, a few minutes was all it took to get a hold of a few dozen users personal information.
Slotboom’s small, black device could fool a phone into connecting to his own Wi-Fi network, giving him control over the entire traffic coming and going from a device.
If Slotboom wanted to, he could wait until one user wrote in his email address and password and then take it over.
With it, he could control most of the services registered on that email.
While you don’t need to be paranoid every time you connect to a public Wi-Fi, it’s best if you know the risks of doing so.
The story: Don’t use public Wi-Fi when reading this article.
There are ways in which you can stay safe on public hotspots: 11 SECURITY STEPS TO STAY SAFE ON PUBLIC WI-FI NETWORKS
14. Customer support falls prey to a social engineering hack
What happens when customer support gives away your information? This Amazon user’s tale is an insightful one.  An impersonator once found out some of Eric’s fake information he used to register a website by looking into a public WHOIS registry for website owners.
An impersonator once found out some of Eric’s fake information he used to register a website by looking into a public WHOIS registry for website owners.
The impersonator then used Eric’s fake information in a conversation with an Amazon customer support representative and found out his real address and phone number.
Using Eric’s real information, the impersonator got in touch with various services and even managed to issue a new credit card in Eric’s name.
Eric got wind of his impersonator’s efforts by reading the customer support transcripts, and also found out his real purpose: to get the last 4 digits of his credit card.
Amazon didn’t do anything to protect Eric’s account, even though he repeatedly signaled the problem, so he finally decides to switch from Amazon to Google.
As a parting note, he gets an email from Amazon implying they have provided the impersonator with the last 4 digits of his credit card.
This story about this guy’s tumultuous experience with Amazon will make you think twice about storing confidential information in your online accounts.
The fact that Amazon failed to protect his account and look into the matter shows how a lack of cyber security education can endanger users
The story: Amazon’s customer service backdoor
Here is a guide on HOW TO PROTECT YOURSELF AGAINST SOCIAL ENGINEERING ATTACKS
15. Hotel managers and clients had nightmares due to one lock hack
In this Forbes story, reporters chronicles the chaos experienced by hotel managers and the panic felt by their customers after a burglar used online hacking tools to bypass the electronic locks on the doors.
“I had dreams about it for many nights. I’d wake up and think I saw someone standing there at my desk,” says one of the victims of a burglary.  Simply put, the burglar watched a Black Hat Conference speaker demonstrating how to hack a certain type of electronic lock using only $50 worth of widely available tools.
Simply put, the burglar watched a Black Hat Conference speaker demonstrating how to hack a certain type of electronic lock using only $50 worth of widely available tools.
He then used that Onity-lock hack to do a series of break-ins. How did this cautionary tale end?
On a bittersweet note.
The original burglar is serving a prison sentence, but the electronic locks in question can still be easily hacked.
A Wired reporter tried it himself, almost 6 years after the original Onity hack, and it still worked. He managed to break into a hotel room.
His story is amazing and it follows the birth of the original hacking method, how the burglar got to it and what came out of the entire publicized event.
The story: The Hotel Room Hacker
If you rely on electronic locks and other IoT devices to secure your belongings, this guide will be very useful: IOT SECURITY – All You Need To Know And Apply
16. The Moderna Conundrum
According to Reuters and other major publications, Moderna Inc, one of the three biotech companies developing an efficient COVID-19 vaccine, has come under attack in late July. US’s Justice Department and the FBI have accused two Chinese nationals in this case.
They have been charged with spying on the American biotech company and three other targets in a bid to slow down or effectively stop the development of the COVID-19 vaccine.
Source from inside the FBI has revealed that the two arrested Chinese citizens are part of a hacking group funded by the Chinese government.
The company has emerged unscathed from the incident. No data has left Moderna’s databanks and the network remains intact.
The story: China-backed hackers ‘targeted COVID-19 vaccine firm Moderna’
Conclusion
These stories may help you realize that not protecting your information and relying on other Internet users to be nice and play fair is not a viable strategy.
Cyber criminals don’t care about the consequences of their attacks.
They only want to reach their purpose, and sometimes that purpose may have nothing to do with you.
You could just be a collateral victim, but the aftermath would be all too real for you.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









