Contents:
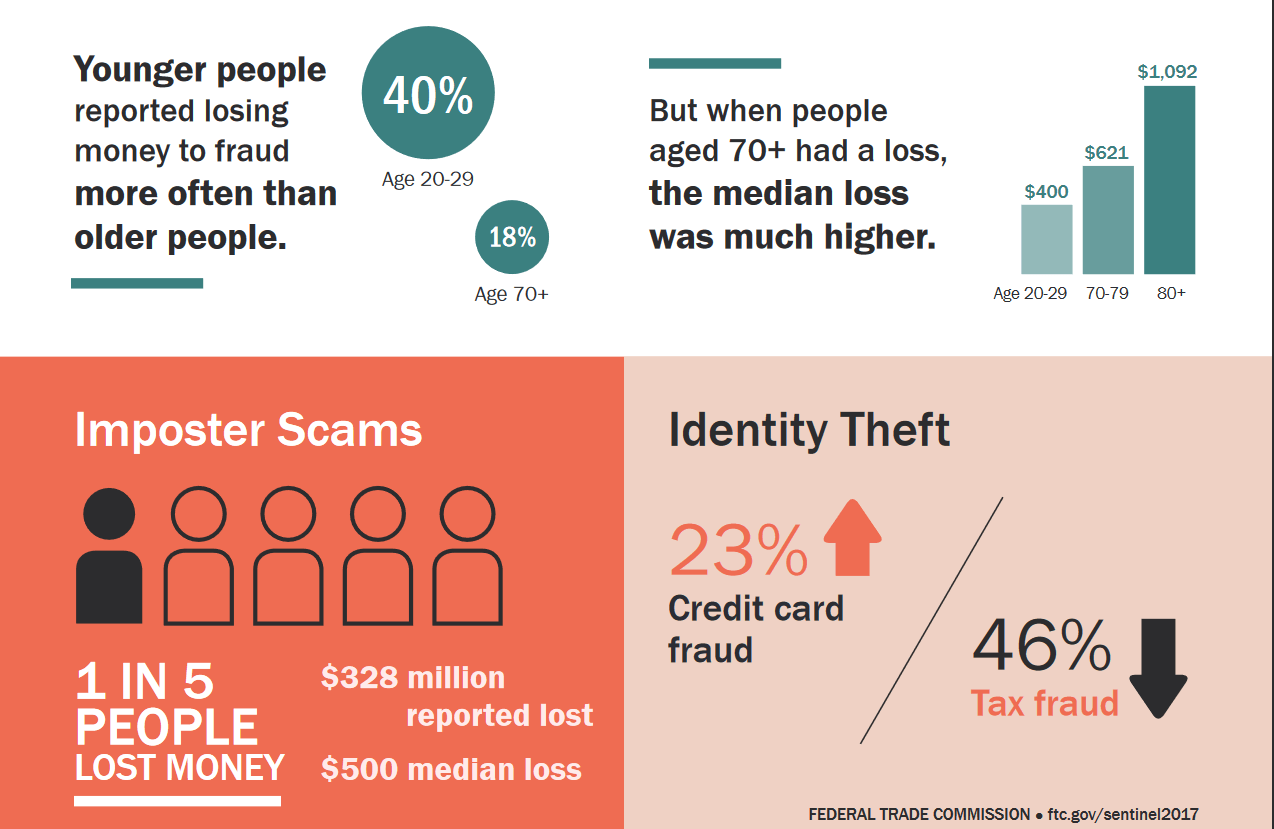
We truly want to believe that the Internet is a safe place where you can’t fall for all types of online scams, but it’s always a good reminder to do a “reality check”. We, humans, can become an easy target for malicious actors who want to steal our most valuable personal data. Criminal minds can reach these days further than before, into our private lives, our homes and work offices. And there is little we can do about it. Attack tactics and tools vary from traditional attack vectors, which use malicious software and vulnerabilities present in almost all the programs and apps (even in the popular Windows operating systems), to ingenious phishing scams deployed from unexpected regions of the world, where justice can’t easily reach out to catch the eventual perpetrators. According to a report from the Federal Trade Commission (FTC), millennials are particularly more vulnerable to online scams than seniors, as shocking as it may seem. The research finds that “40 percent of adults age 20-29 who have reported fraud ended up losing money in a fraud case”.
Source: Federal Trade Commision
For this reason, we need to know what are the most popular techniques malicious actors are using to get unauthorized access to our private information and financial data. We must not forget their final target is always our money and there is nothing they won’t do to accomplish their mission. Use the links below to quickly navigate the list of online scams you need to stay away from right now.
- Phishing email scams
- The Nigerian scam
- Greeting card scams
- Bank loan or credit card scam
- Lottery scam
- Hitman scam
- Romance scams
- Fake antivirus software
- Facebook impersonation scam (hijacked profile scam)
- Make money fast scams (Economic scams)
- Travel scams
- Bitcoin scams
- Fake news scam
- Fake shopping websites
- Loyalty points phishing scam
- Job offer scams
- SMS Scaming(Smshing)
- Overpayment Online Scam
- Tech Support Online Scams
1. Phishing email scams
More than one third of all security incidents start with phishing emails or malicious attachments sent to company employees, according to a new report from F-Secure. Phishing scams continue to evolve and be a significant online threat for both users and organizations that could see their valuable data in the hands of malicious actors. The effects of phishing attacks can be daunting, so it is essential to stay safe and learn how to detect and prevent these attacks.
Phishing scams are based on communication made via email or on social networks. In many cases, cyber criminals will send users messages/emails by trying to trick them into providing them valuable and sensitive data ( login credentials – from bank account, social network, work account, cloud storage) that can prove to be valuable for them. Moreover, these emails will seem to come from an official source (like bank institutions or any other financial authority, legitime companies or social networks representatives for users.) This way, they’ll use social engineering techniques by convincing you to click on a specific (and) malicious link and access a website that looks legit, but it’s actually controlled by them. You will be redirect to a fake login access page that resembles the real website.
If you’re not paying attention, you might end up giving your login credentials and other personal information. We’ve seen many spam email campaigns in which phishing were the main attack vector for malicious criminals used to spread financial and data stealing malware. In order for their success rate to grow, scammers create a sense of urgency. They’ll tell you a frightening story of how your bank account is under threat and how you really need to access as soon as possible a site where you must insert your credentials in order to confirm your identity or your account. After you fill in your online banking credentials, cyber criminals use them to breach your real bank account or to sell them on the dark web to other interested parties. Here’s an example of a sophisticated email scam making the rounds that you should be very careful.  Source: News.com.au
Source: News.com.au
Use this complete guide on how to detect and prevent phishing attacks (filled with screenshots and actionable tips) to better fight these attacks.
2. The Nigerian scam
Probably one of the oldest and most popular Internet scams used mostly by a member of a Nigerian family with wealth to trick different people. It is also known as “Nigerian 419”, and named after the section of Nigeria’s Criminal Code that banned the practice. A typical Nigerian scam involves an emotional email, letter, text message or social networking message coming from a scammer (which can be an official government member, a businessman or a member of a very wealthy family member – usually a woman) who asks you to give help in retrieving a large sum of money from a bank, paying initially small fees for papers and legal matters. In exchange for your help, they promise you a very large sum of money. They will be persistent and ask you to pay more and more money for additional services, such as transactions or transfer costs. You’ll even receive papers that are supposed to make you believe that it’s all for real. In the end, you are left broke and without any of the promised money. Here’s how a Nigerian scam could look like:
 Source: MotherJones.com
Source: MotherJones.com
3. Greeting card scams
Whether it’s Christmas or Easter, we all get all kind of holiday greeting cards in our email inbox that seem to be coming from a friend or someone we care. Greeting card scams are another old Internet scams used by malicious actors to inject malware and harvest users’ most valuable data. If you open such an email and click on the card, you usually end up with malicious software that is being downloaded and installed on your operating system. The malware may be an annoying program that will launch pop-ups with ads, unexpected windows all over the screen. If your system becomes infected with such dangerous malware, you will become one of the bots which are part of a larger network of affected computers. If this happens, your computer will start sending private data and financial information to a fraudulent server controlled by IT criminals. To keep yourself safe from identity theft and data breach, we recommend using a specialized security program against this type of online threats. To find out more information about financial malware, read this article. And here’s how you can tell if your computer was infected with malware.
 Source: The Beacon Bulletin
Source: The Beacon Bulletin
4. Bank loan or credit card scam
People can be easily scammed by “too good to be true” bank offers that might guarantee large amounts of money and have already been pre-approved by the bank. If such an incredible pre-approved loan is offered to you, ask yourself: “How is it possible for a bank to offer you such a large sum of money without even checking and analyzing your financial situation?” Though it may seem unlikely for people to get trapped by this scam, there’s still a big number of people who lost money by paying the “mandatory” processing fees required by the scammers. Here are 9 warning signs and sneaky tactics to watch out and avoid becoming a business loan scam. As regards to credit card scams, a recent report from the Identity Theft Resources Center said that the number of credit and debit card breaches have been on the rise last year. To better safeguard your data and prevent thieves from getting access to your payment card details, consider:
- Watching your accounts closely and monitor your online transactions;
- Taking advantage of free consumer protection services;
- Signing up for free credit monitoring.
 Source: ChaffeurDriven.com
Source: ChaffeurDriven.com
5. Lottery scam
This is another classic Internet scam which doesn’t seem to get old. A lottery scam comes as an email message informing you that you won a huge amount of money and, in order to claim your prize or winnings, you need to pay some small fees. Lucky you, right?! It doesn’t even matter that you don’t recall ever purchasing lottery tickets. Since it addresses some of our wildest fantasies, such as quitting our jobs and living off the fortune for the rest of our lives, without ever having to work again, our imagination falls prey easily to amazing scenarios someone can only dream of. But the dream ends as soon as you realize you have been just another scam victim. DO NOT fall for this online scam and have a look at this checklist to see if you are getting scammed. 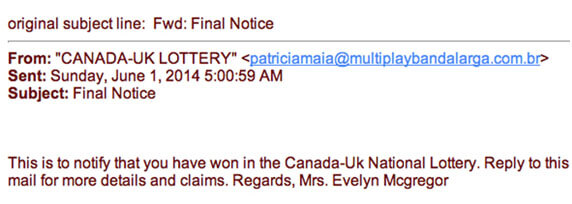 Source: Ripandscam.com
Source: Ripandscam.com
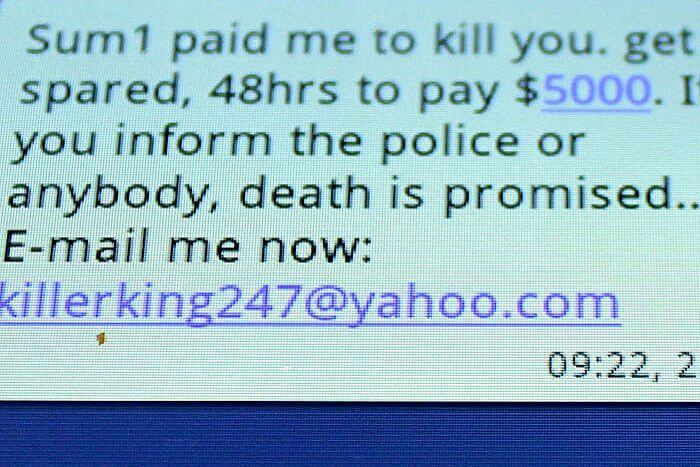
6. Hitman scam
One of the most frequent Internet scams you can meet online is the “hitman” extortion attempt. Cybercriminals will send you an email threatening to extort money from you. This type of online scam may come in various forms, such as the one threatening that they will kidnap a family member unless a ransom is paid in a time frame provided by the scammers. To create the appearance of real danger, the message is filled with details from the victim’s life, collected from an online account, a personal blog or from a social network account. That’s why it’s not safe to provide any sensitive or personal information about you on social media channels. It might seem like a safe and private place, where you’re only surrounded by friends, but in reality, you can never know for sure who’s watching you. Also, it’s better to be a little bit paranoid and protect all your digital assets like everyone is watching. Here’s how a Hitman scam looks like:
7. Online dating (romance) scams
As the Internet plays an important role in our social lives, with apps like Facebook or Instagram we access every day, it’s inevitable to use apps to look for love as well. Online dating apps are very popular these days and they are a great way to meet your future life partners. I have actually an example with a friend of mine who was lucky enough to find her future husband on a dating site. But not all scenarios have a “happy end” like this one, and you need to be very careful because you never know who can you meet.
A romance scam usually takes place on social dating networks, like Facebook, or by sending a simple email to the potential target, and affects thousands of victims from all over the world. The male scammers are often located in West Africa, while the female scammers are mostly from the eastern parts of Europe. Cybercriminals have abused this scamming method for years by using online dating services. They improved their approach just by testing the potential victims’ reactions. According to research published in the British Journal of Criminology last month, the techniques (and psychological methods) used by scammers in online romance scams are similar to those used in domestic violence cases. To avoid becoming a victim of these Internet scams, you need to learn how to better protect yourself.
Knowing that hundreds of women and men from all over the globe are victims of these online scams, we recommend using these security tips for defensive online dating, including warning signs that could help you from becoming an easy target. I would also recommend reading these real stories and learn from them, so you don’t fall for these online scams:
- A woman lost £1.6 million after she met two conmen on a dating site
- A Perth woman has lost $300,000 after falling in love with a fake Facebook profile
- US woman lost her $50.000 life savings by becoming victim of a cyber-dating scam artist
8. Fake antivirus software
We all saw at least once this message on our screens: “You have been infected! Download antivirus X right now to protect your computer!” Many of these pop-ups were very well created to look like legitimate messages that you might get from Windows or any other security product. If you are lucky, there is nothing more than an innocent hoax that will bother you by displaying unwanted pop-ups on your screen while you browse online. In this case, to get rid of the annoying pop-ups, we recommend scanning your system using a good antivirus product.
If you are not so lucky, your system can end up getting infected with malware, such as a Trojan or a keylogger. This kind of message could also come from one of the most dangerous ransomware threats around, such as CryptoLocker, which is capable of blocking and encrypting your operating system and requesting you a sum of money in exchange for the decryption key. To avoid this situation, we recommend enhancing your online protection with a specialized security product against financial malware and complement your traditional antivirus program. Also, make sure you do not click on pop-up windows that annoyingly warn you’ve been infected with a virus. Remember to always apply the existing updates for your software products, and install only legitimate software programs from verified websites.
9. Facebook impersonation scam (hijacked profile scam)
Facebook. Everyone is talking about it these days and the scandal about Cambridge Analytica firm harvesting personal data taken from millions of this social media channel without users’ consent. It’s still the most popular social media network where everyone is active and uses it on a daily basis to keep in touch with friends and colleagues. Unfortunately, it has become also the perfect place for online scammers to find their victims.
Just imagine your account being hacked by a cybercriminal and gaining access to your close friends and family. Nobody wants that! Since it is so important for your privacy and online security, you should be very careful in protecting your personal online accounts just the way you protect your banking or email account. Facebook security wise, these tips might help you stay away from these online scams:
- Do not accept friend requests from people you don’t know
- Do not share your password with others
- When logging in, use two-factor authentication
- Avoid connecting to public and free Wi-Fi networks
- Keep your browser and apps updated
- Add an additional layer of security and use proactive cybersecurity software.
To enhance your online privacy, I recommend reading our full guide on Facebook security and privacy.
10. Make money fast scams (Economic scams)
Cybercriminals will lure you into believing you can make money easy and fast on the internet. They’ll promise you non-existent jobs, including plans and methods of getting rich quickly. It is a quite simple and effective approach, because it addresses a basic need for money, especially when someone is in a difficult financial situation. This scamming method is similar to the romance scam mentioned above, where the cyber attackers address the emotional side of victims.
The fraudulent posting of non-existent jobs for a variety of positions is part of the online criminals’ arsenal. Using various job types, such as work-at-home scams, the victim is lured into giving away personal information and financial data with the promise of a well-paid job that will bring lots of money in a very short period of time. Read and apply these ten tips that can help you avoid some of the most common financial scams.
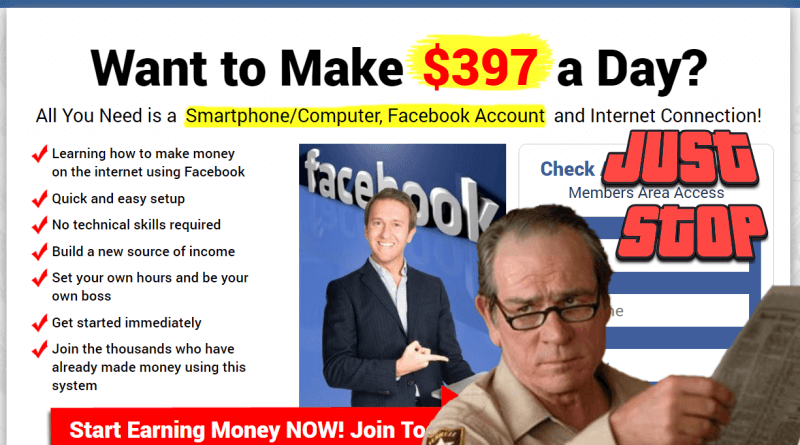 Source: Makerealmoneyonlinefree.com
Source: Makerealmoneyonlinefree.com
11. Travel scams
These scams are commonly used during hot summer months or before the short winter vacations, for Christmas or New Year’s Day. Here’s how it happens: you receive an email containing an amazing offer for an exceptional and hard to refuse destination (usually an exotic place) that expires in a short period of time which you can’t miss. If it sounds too good to be true, it might look like a travel scam, so don’t fall for it! The problem is that some of these offers actually hide some necessary costs until you pay for the initial offer. Others just take your money without sending you anywhere. In such cases, we suggest that you study carefully the travel offer and look for hidden costs, such as: airport taxes, tickets that you need to pay to access a local attraction, check if the meals are included or not, other local transportation fees between your airport and the hotel or between the hotel and the main attractions mentioned in the initial offer, etc. As a general rule, we suggest that you go with the trustworthy, well-known travel agencies. You can also check if by paying individually for plane tickets and for accommodation you receive the same results as in the received offer. If you love to travel, you can easily fall prey to airline scams by simply looking for free airline tickets. Airline scams are some of the most popular travel scams, and we recommend applying these valuable tips.
12. Bitcoin scams
If you (want to) invest in Bitcoin technology, we advise you to be aware of online scams. Digital wallets can be open to hacking and scammers take advantage of this new technology to steal sensitive data. Bitcoin transactions should be safe, but these five examples of Bitcoin scams show how they happen and how you can lose your money. The most common online scams to watch out for:
- Fake Bitcoin exchanges
- Ponzi schemes
- Everyday scam attempts
- Malware
Here’s how you can spot a Bitcoin scam and how to stay safe online.
 Source: Express.co.uk
Source: Express.co.uk
13. Fake news scam
The spread of fake news on the Internet is a danger to all of us because it has an impact on the way we filter all the information we found and read on social media. It’s a serious problem that should concern our society, mostly for the misleading resources and content found online, making it impossible for people to distinguish between what’s real and what is not. We recommend accessing/reading only reliable sources of information coming from friends or people you know read regular feeds from trusted sources: bloggers, industry experts, in order to avoid fake news. [Tweet “If it seems too good to be true, it’s most likely a scam.
Take a look over these online scams”] This type of scam could come in the form of a trustworthy website you know and often visit, but being a fake one created by scammers with the main purpose to rip you off. It could be a spoofing attack which is also involved in fake news and refers to fake websites that might link you to a buy page for a specific product, where you can place an order using your credit card. To avoid becoming a victim of online scams, you can use tech tools such as Fact Check from Google or Facebook’s tool aimed at detecting whether a site is legitimate or not, analyzing its reputation and data. Cybersecurity experts believe that these Internet scams represent a threat for both organizations and employees, exposing and infecting their computers with potential malware.
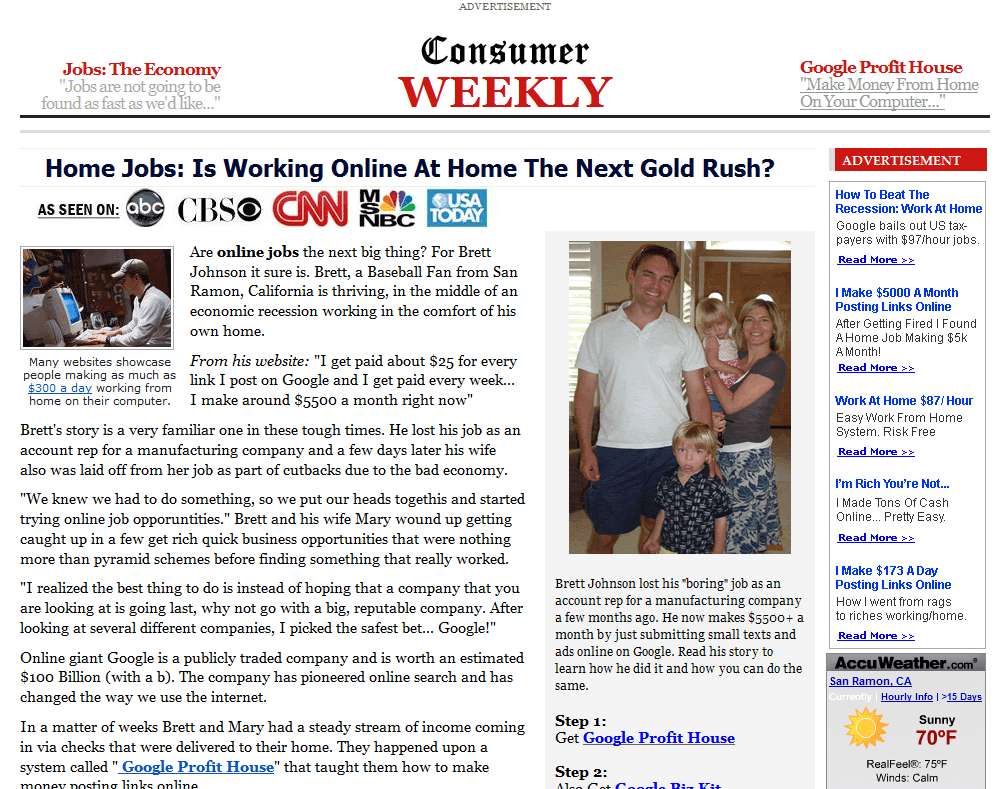 Source: Opportunitychecker.com
Source: Opportunitychecker.com
14. Fake shopping websites
We all love shopping and it’s easier and more convenient to do it on the Internet with a few clicks. But for your online safety, be cautious about the sites you visit. There are thousands of websites out there that provide false information and might redirect you to malicious links, giving hackers access to your most valuable data. If you spot a great online offer which is “too good to be true”, you might be tempted to say “yes” instantly, but you need to learn how to spot a fake shopping site so you don’t get scammed. We strongly recommend reading these online shopping security tips to keep yourself safe from data breaches, phishing attacks or other online threats. 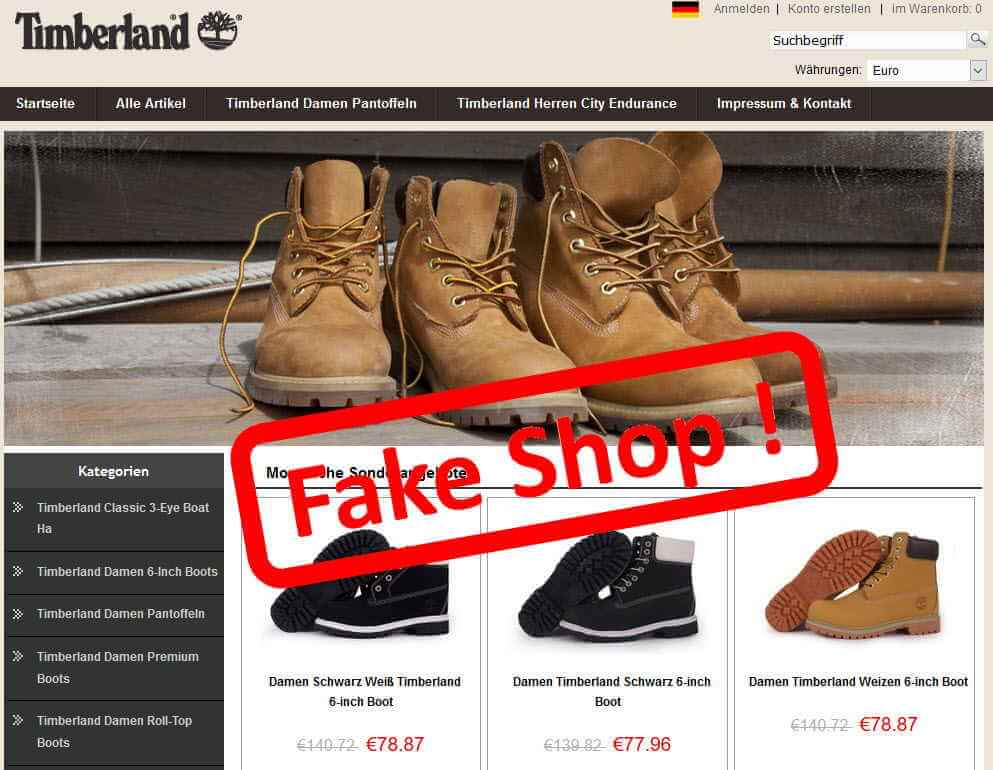 Source: Originalo.de
Source: Originalo.de
15. Loyalty points phishing scam
Many websites have a loyalty program to reward their customers for making different purchases, by offering points or coupons. This is subject to another online scam because cybercriminals can target them and steal your sensitive data. If you think anyone wouldn’t want to access them, think again. The most common attack is a phishing scam that looks like a real email coming from your loyalty program, but it’s not. Malicious hackers are everywhere, and it takes only one click for malware to be installed on your PC and for hackers to have access to your data. As it might be difficult to detect these phishing scams, you may find useful this example of a current phishing campaign targets holders of Payback couponing cards, as well as some useful tips and tricks to avoid being phished.
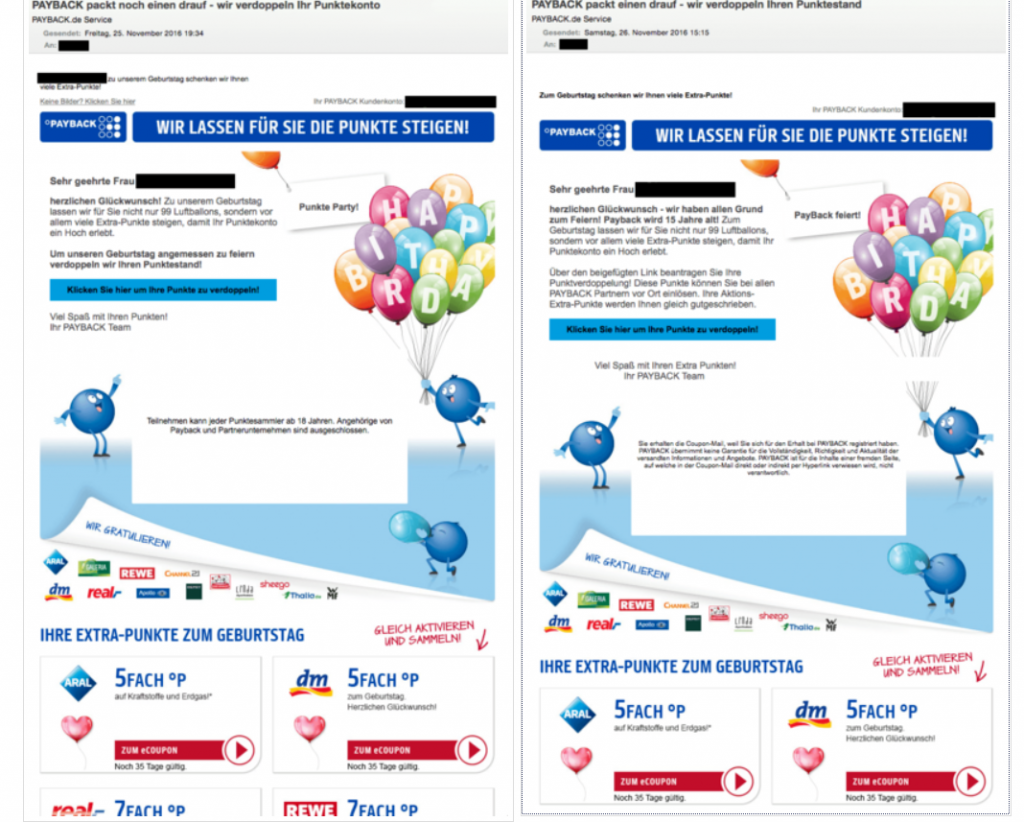
Source: G Data Security Blog
16. Job offer scams
Sadly, there are scammers everywhere – even when you are looking for a job – posing as recruiters or employers. They use fake and “attractive” job opportunities to trick people. It starts with a phone call (or a direct message on LinkedIn) from someone claiming to be a recruiter from a well-known company who saw your CV and saying they are interested in hiring you. Whether you’ve applied or not, the offer might be very appealing, but don’t fall into this trap. To protect yourself from job offer scams, it’s very important to:
- Do thorough research about the company and see what information you can find about it;
- Check the person who’s been contacted you on social media channels;
- Ask for many details and references and check them out;
- Ask your friends or trustworthy people if they know or interacted with the potential employer.
To avoid these types of online job scams, check this article.
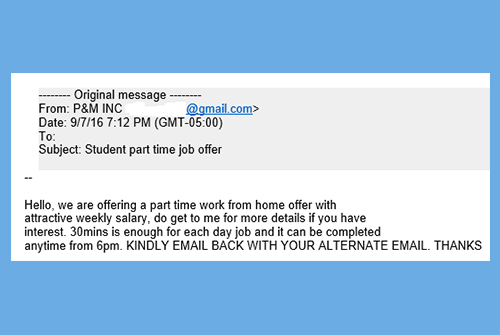 Source: Drexel.edu
Source: Drexel.edu
17. SMS Scamming (Smshing)
Smartphones. You can’t live without them in the era of the Internet. They’ve become essential for communication, online shopping, banking or any other online activity. Needless to say the amount of data we store on our personal devices which make them vulnerable to cybercriminals, always prepared to steal our online identities or empty our bank accounts. Smishing (using SMS text messages) is a similar technique to phishing, but, instead of sending emails, malicious hackers send text messages to their potential victims. How does this happen? You receive an urgent text message on your smartphone with a link attached saying that it’s from your bank and you need to access it in order to update your bank information or other online banking information. Be careful about these SMS you receive and don’t click on suspicious links that could redirect to malicious sites trying to steal your valuable data. These useful tips can help you easily spot these types of online scams. 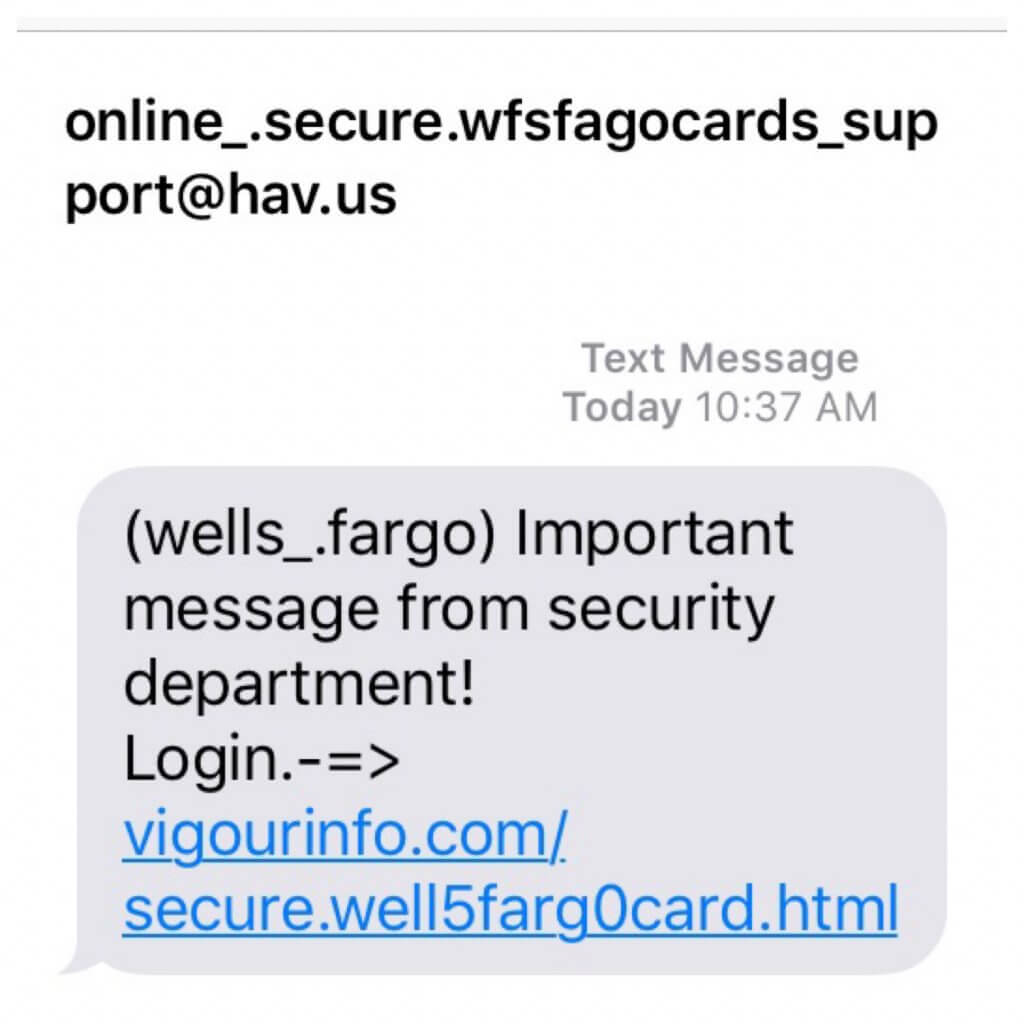 Source: Malwarebytes Labs
Source: Malwarebytes Labs
18. Overpayment Online Scam
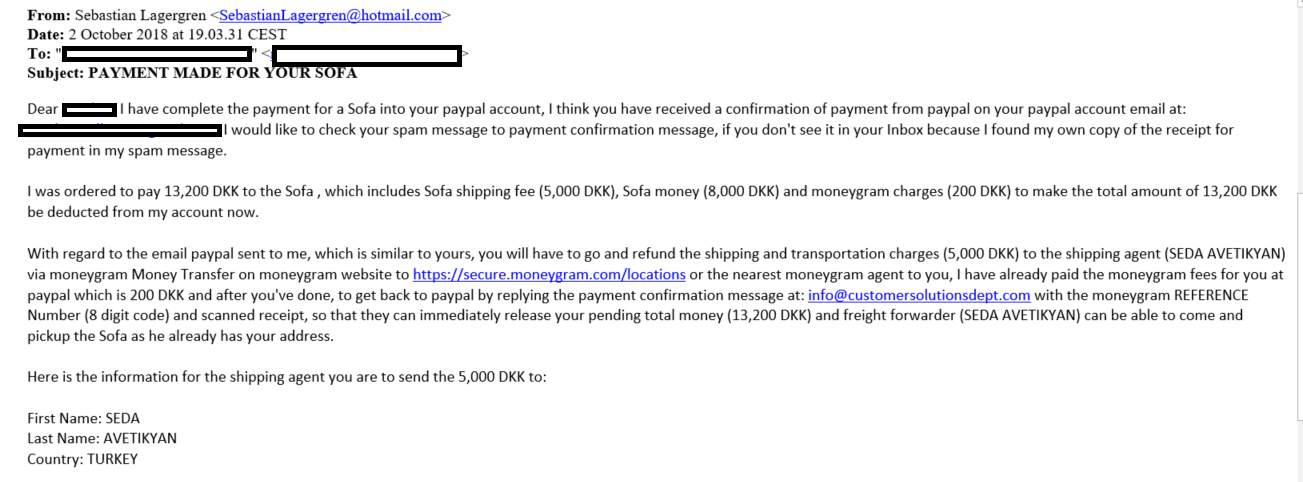
If you are considering selling different items on specialized online sites, we strongly recommend watching out for overpayment scam. A typically overpayment online scam like this works by getting the potential victim “to refund” the scammer an extra amount of money because he/she send too much money. The offer will often be quite generous and bigger than the agreed price. The overpay (extra money) is to cover the costs of shipping or certain custom fees. One such story can unfold right now and can happen to each of you. This happened to one of our Heimdal Security team members.
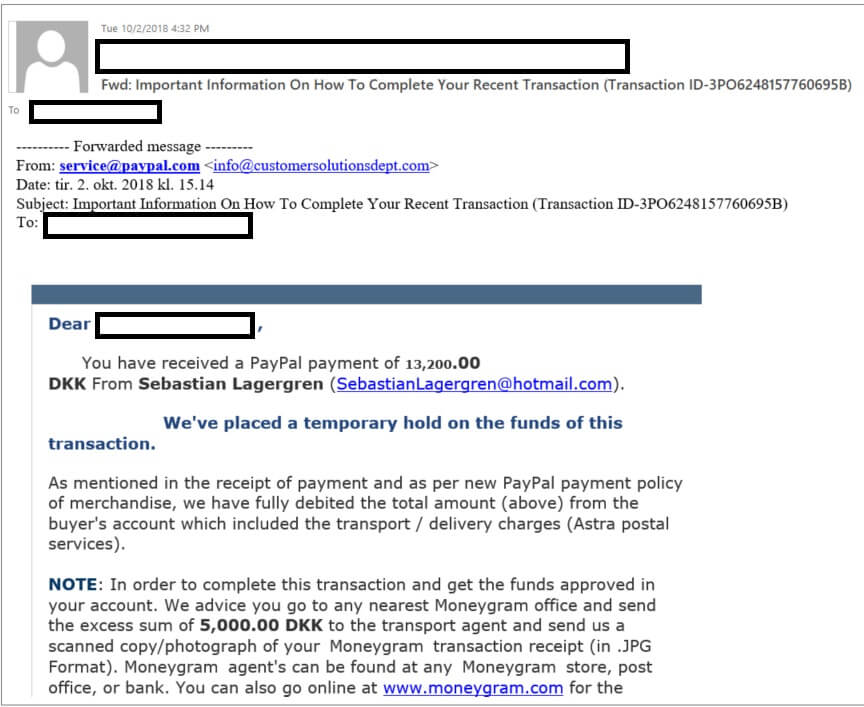
After smiling a bit and seeing the method, we did realize that’s a common online scam and we had to share it with you. Also, we included a few security tips and actionable advice to prevent falling prey to overpayment online scam. Our colleague posted a sofa for sale on a Danish site called dba.dk which is a sort of a flea market online. After a few days, he received a message from a person claiming to be interested in the item and willing to pay more than the price offered, via PayPal account. Here’s how a scam email looks like in which the malicious person asks for personal information to transfer the money.
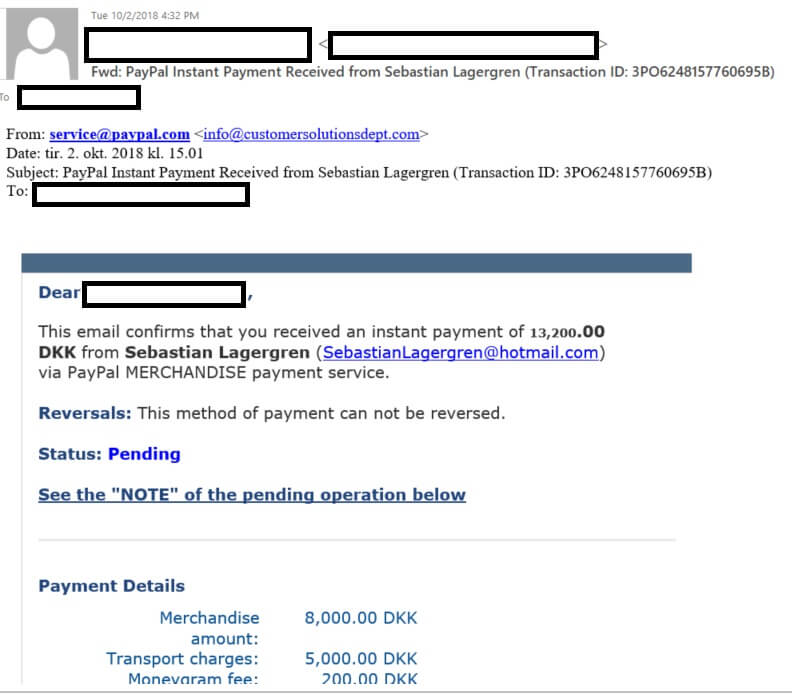
Also, here’s the confirmation email coming from the scammer which shows that he paid an extra amount for the sofa, including extra shipping fees and MoneyGram charges the extra fee for transportation.
After that, he also got another email saying that he needs to refund the extra amount of money, including the shipping and transportation charges to a certain shipping agent via MoneyGram transfer. Here’s how the phishing email looks like that you should be very careful and don’t fall for it:
Follow these security tips to protect yourself from overpayment online scams:
- If you notice a suspicious email coming from an untrusted source or something out of ordinary, you should report it as soon as possible.
- If you receive a similar email like the one our colleague got, do not transfer extra money to someone you don’t know, especially if he/she wants to overpay. A legitimate buyer won’t do that.
- Also, do not transfer money to a fake shipping company or some private shipping agent, because it’s part of a scam and you need to be very careful.
- Do not provide personal information to people who don’t show a genuine interest in buying your item.
- Do not send the product to the buyer until the payment was completed and received in your bank account.
19. Tech Support Online Scams
Here’s another online scam that is common and you need to be extra careful. The next time your smartphone rings and you don’t know the number, think twice before answering. Maybe it’s not your friend on the other end of the phone, maybe it’s the scammer! According to a recent report “nearly half of all cellphone calls next year will come from scammers”, so we need to learn how to better detect and prevent such malicious actions coming from skilled persons. Tech support scams are very common and widespread these days. Scammers use various social engineering techniques to trick potential victims into giving their sensitive information. Even worst, they try to convince potential victims to pay for unnecessary technical support services.
These tech “experts” pretend to know everything about your computer, how it got hacked and many other details that help them gain your trust and convince victims to fall prey to their scams. A scenario like this can happen as we write this, and one of our Heimdal Security team members recently got a phone scam call. While we got amused by the conversation he had with the person pretending to work for an Indian tech support company, we realized it can happen to anyone who can become an easy target.
What happened? The person, pretending to be the representative of a software company and experienced one, is informing our colleague that his computer got hacked by cybercriminals, and offers to guide him and solve this urgent problem. With poor English skills, he gives details about the serial number of the computer, and provides guidance to access the unique computer ID, trying to misrepresent a normal system as having serious issues. After a few minutes, the call is transferred to another tech representative who informs our colleague that they detected unusual activity going through his computer. He’s been told that multiple attempts have been seen on the PC in which hackers tried to get unauthorized access to his computer. Our colleague detected this as being a scam and didn’t go along with it, but for someone without technical knowledge, it may not be so easy to spot. You can listen to this call here:
If someone else would have fallen prey for this online scam, things would have gone even further. The so-called tech scammers could persuade the potential victim to give them remote access to the system. To “help” the victim, scammers mention about additional software that is required to be installed and victims need to pay for these software victims, hence, provide credit card details. You can find out more info here How to avoid getting scammed by tech support “specialists” To avoid becoming an easy target of these sneaky tech support scammers, we strongly recommend following these basic rules:
- Do not trust phone calls coming from people pretending to come from tech “experts”, especially if they are requesting for personal or financial information;
- DO NOT PROVIDE sensitive data to them or purchase any software services scammers may suggest you as a solution to fix your tech problem.
- DO NOT allow strangers to remotely access your computer and potentially install malicious software;
- Make sure you download software apps and services only from official vendor sites;
- Don’t take it for granted when a stranger calls you out of the blue, pretending to have a technical solution for your issues. Make sure you ask for proof of their identity and do a quick research about the company they are calling you from;
- Always have an antivirus program installed on your computer, and for more protection, consider adding multiple layers of security with a proactive security solution like Heimdal™ Premium Security Home, which will stop any type of online threats.
- Have a security-first mindset and be suspicious about everything around you. Also, consider investing in education and learn as much as possible about cybersecurity. Here’s how you can reduce spam phone calls.
Where can you report Online Scams and Frauds?
If you become a victim of an internet-related scam, you can report it to these government authorities:
- Econsumer.gov – Report international frauds. A partnership of more than 40 consumer protection agencies around the world. Accepts complaints about online shopping and e-commerce transactions with foreign companies.
- Internet Crime Complaint Center (IC3) – Report international frauds. Takes internet-related criminal complaints and forwards them to federal, state, local, and international law enforcement agencies.
- Federal Trade Commission (FTC) – US only. Consumer complaints and online scams are shared with all levels of law enforcement.
- Europol – For Europe. Several European countries listed with direct links and emails where you can report online scams.
Conclusion
Since some scams are so well organized and really convincing, and people behind them so difficult to catch, we need to always keep our guard up. Stay informed about the latest scamming strategies.
Have you met some of the above scams while browsing or in your email inbox? What were the most convincing ones?



 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security