Contents:
What did ancient castle builders have to do with multi-layered security systems?
I’ll tell you all about it in today’s security guide.
The point of a multi-layered security system is to stop cyber attacks on different levels, so they never reach the core of the system and essential sensitive data.
We’ve come to a point where we need such a stratified system because malware morphs quickly into new and more aggressive threats. Because antivirus is no longer enough for your protection (because of these reasons). Because no solution can guarantee 100% protection.
Your computer system should look like an ancient castle surrounded by various walls: the treasure is kept in the center and attackers have to fight past the walls, one by one, to reach their goal. Your objective is to weaken the assailants to the point that they never affect or get their hands on the treasure.
Like I said, ancient castle builders knew how to put up a fight when attackers assaulted their fortresses. Now it’s up to you to protect your own treasure: your data (credentials, money, identity, memories, etc.).
This visual guide will explain how different types of security products provide protection on different levels.
The structure mimics an enterprise-grade cyber security system, but simpler, so you can follow it and, most of all, afford it.
As you can imagine, protection suites for companies are tremendously complex. Fortunately, we, as home users, have plenty of options to choose from as well.
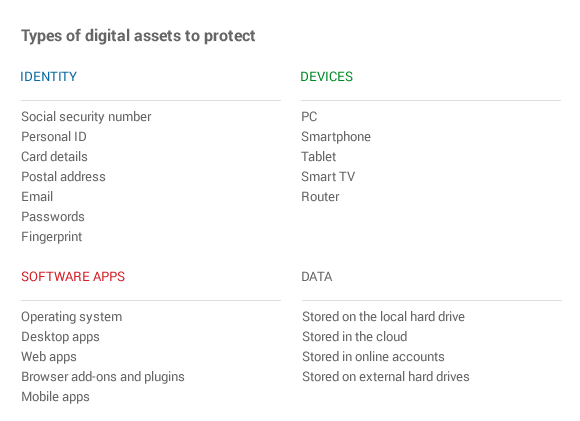
1. Start with this list of digital assets to protect
You don’t have to be obsessed to keeping things organized to get this done.
But understanding how your digital stuff is scattered across devices, apps and the Internet is key to your online protection.
So there are a few key assets that your online protection should cover:
- Your identity
- Your devices
- Your software apps (meaning the data stored in them)
- And your sensitive data.
If you’re unsure of what goes into each category, this table should help:
Bottom line: online criminals want to compromise your devices and software apps to get their hands on your identity details and data.
Of course, it only sounds simple. There’s a lot of stuff going on in the background, but now let’s focus on the types of security and privacy products you can use, according to your needs.
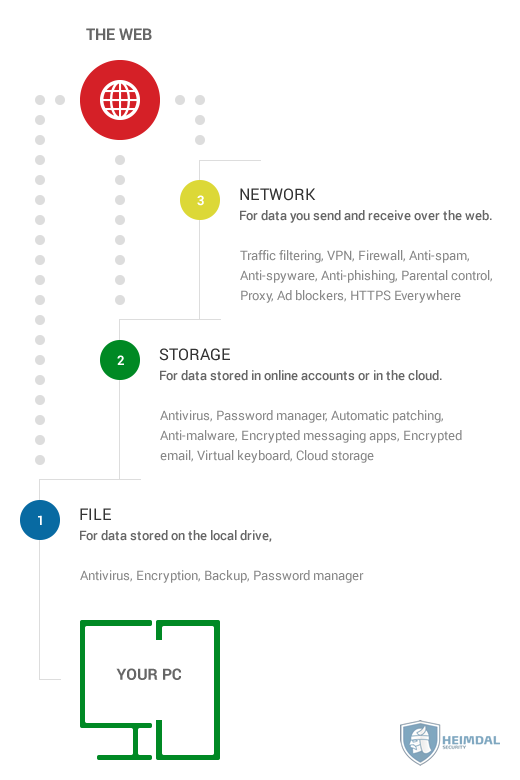
2. Choose the right security products for each layer
Your first layer of defense should protect the data you send and receive over the web.
That’s because cyber criminals use the Internet to launch and spread most of their attacks.
It’s much easier for an online criminal to send spam emails with malicious links in them than, for example, to spread USB sticks with malware on them so potential victims can plug them in and get infected.
Cyber criminals sniff, crack and break into your data exchanges over the web, if they’re not properly secured. That’s why, at this stage, prevention is the best strategy.
A couple of tools you can use to secure your Internet traffic are:
- Traffic filtering – to sanitize your Internet traffic against cyber threats and prevent data exfiltration (key for your proactive security)
- VPN – to anonymize your Internet traffic and keep attackers from pinning down your exact location
- Firewall – to prevent unauthorized access to your home network
- Anti-spam – to fight against unsolicited email, which if often loaded with malware
- Anti-spyware – to detect and block spyware attempts, which aim to monitor your online activity and send the information to malicious actors
- Anti-phishing – to block phishing attempts aimed at making you divulge sensitive data to cyber attackers
- Parental control – if you want to protect your children from accessing dangerous or inappropriate content
- Proxy – to prevent potential attackers from infecting your computer or home network directly
- Ad blockers – to eliminate the threat of malvertising
- HTTPS Everywhere – to make sure that the data you send and receive over the web is always encrypted.
This collection of tools can help you build a barrier between you and cyber criminal attempts delivered via the web.
Use these tools wisely and don’t overdo it: security and privacy tools have a lot of complexity behind them, so using more tools doesn’t mean you’ll be more protected.
Choose the right ones for your needs and always remember that no one can guarantee 100% protection. But it’s certainly an objective that everyone wants to achieve.
Your second layer of defense should aim to secure the data you stored in online accounts or in the cloud.
When you think of storage, go broad! It’s not only about the photos and videos that you have in your Dropox account. This category also includes the things you’ve shared on Facebook, your postal address details saved in your Amazon account, all those instant messages sent over WhatsApp, your hundreds of emails, etc.
All these bits and pieces of data define our identity online. And the truth is we share much more data about ourselves than we can imagine!
You can protect your online apps against intrusion by using:
- Antivirus – which works well to keep you safe against attacks that aim to compromise your desktop apps
- Password manager – an invaluable tool for keeping your credentials strong and storing them safely (even better if couple with two-factor authentication)
- Automatic patching – that will save you time and energy, while keeping your software up to date and plugging those inevitable security holes
- Anti-malware – to complete the functions or a traditional antivirus, which sometimes cannot keep up with the huge amount of malware released each day
- Encrypted messaging apps – to ensure that your communication is secure, both in terms of messages and files shared
- Encrypted email – which guarantees that no one can decode your important email exchanges
- Virtual keyboard – to keep safe from keylogging, which cyber attackers use to record your keystrokes and steal your passwords and other confidential information
- Cloud storage – a good place to keep one backup of your (previously encrypted) data, so you can prevent data loss in case of a cyber attack.
An overwhelming percentage of cyber attacks target your software, no matter if it’s your browser, your operating system or your desktop apps. If it connects to the Internet, it will be on the attackers’ radar.
And the increasing amount of security holes in the most used software apps in the world provides plenty of opportunities for online criminals to exploit.
That doesn’t mean that the responsibility for your protection is exclusively yours. But why rely on third parties when there’s so much you can do for yourself?
With the first two layers of protection, you’ve already blocked most attacks. If online criminals got this far, they’ll assume that it’s all the way downhill from here.
But you’re still the king of your castle!
Your third layer of defense should focus on keeping the data stored on your local drive safe from harm.
This is where you most likely store things like your photos, your music, work documents and so much more. It’s your digital home and you can’t help but feel protective about it (as you should).
So here’s what you can do to ensure that your data stored locally will be safe against the last attack vectors that may slip through the first two layers of protection.
Make sure you use:
- Backup – in at least two separate locations (in the cloud and on an external drive) to create redundancy (if you should lose one back-up, there’s always another one so restore your data from)
- Encryption – to protect your data from being modified, stolen or infected with malware
- Password manager – because no matter how strong the encryption program you use is, it still relies on you setting and using a strong password (also, we can’t emphasize enough how important good password management is)
- Antivirus – we’ve mentioned this one before, but it applies here as well, because it will look at your files and see if malware is present on the system.
3. Train yourself to spot their tricks
There are lots of other security products out there, each with its own specialty. In this guide, I focused on showing you the basics of what you can use for each layer of protection.
Remember this: your opponents are smart and have plenty of resources. Don’t underestimate them.
And, most of all, know that technology may help, but online attackers can still appeal to your human side to get their way. Beware of psychological manipulation (social engineering) tactics , such as phishing. Teach yourself to identify their tricks and traps and avoid them at all costs.
Mastering basic cyber security is a skill we’ll all need going forward, when the web becomes an increasingly bigger part of our personal and professional lives.
Listen to advice, test what’s right for you and keep up to date with what’s new. It all boils down to that.



 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security