Contents:
Home users, large or small organizations, public or private institutions, everyone could be a victim of ransomware attacks. It is, by far, one of the most successful methods cybercriminals are using to encrypt users’ files and ask for a ransom in return. Online criminals (will) always look for innovative ways to infect a system or a network and targeting admin passwords through brute force attacks is an attractive method. We’ve seen cases in which attackers hack into unprotected remote desktop protocols and manually executed the ransomware. Ransomware infections continue to cause serious problems for both individuals and companies that lose access to their valuable data. The impact of ransomware is devastating and such attacks usually happen due to bad IT hygiene and a minimum of security measures taken.

Heimdal® DNS Security Solution
- Machine learning powered scans for all incoming online traffic;
- Stops data breaches before sensitive info can be exposed to the outside;
- Advanced DNS, HTTP and HTTPS filtering for all your endpoints;
- Protection against data leakage, APTs, ransomware and exploits;
An antivirus solution standalone is not enough to fully protect your data
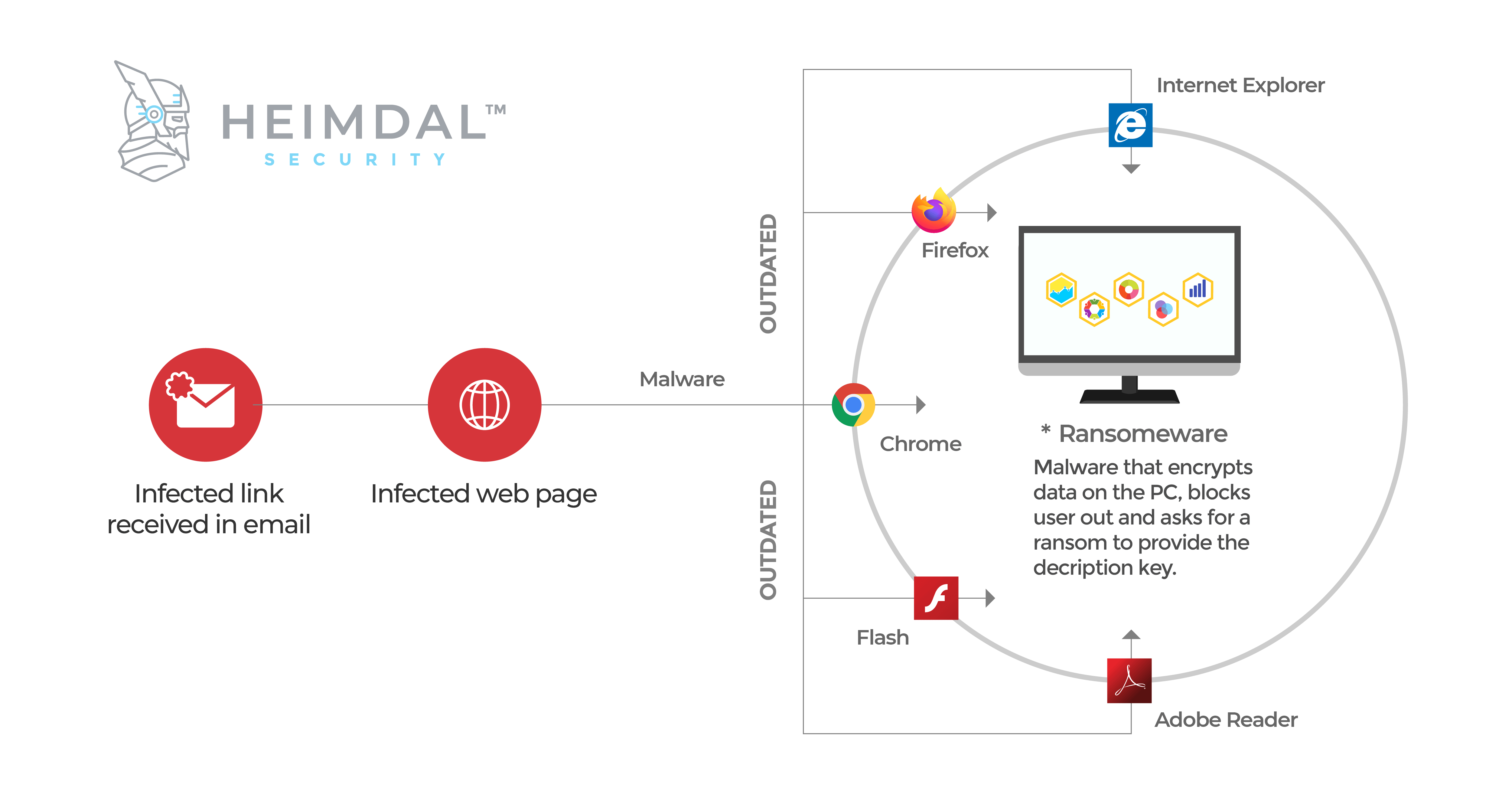
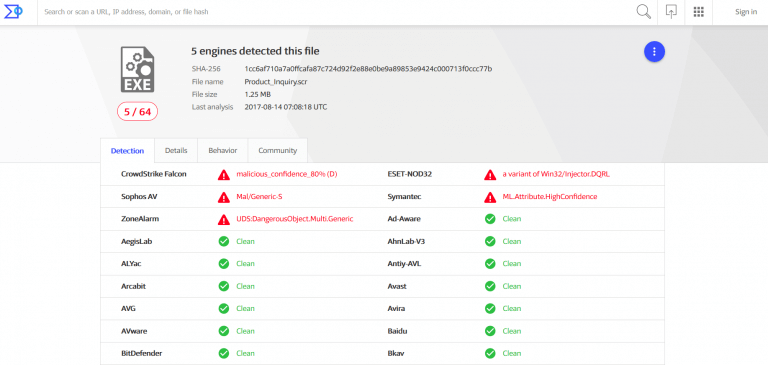
If you are currently using an antivirus solution to keep your data safe and secure, know that it can’t provide 100% protection. Online threats have evolved greatly and malicious actors became real “artists” in using creative ways to spread malware. Antivirus is only a single layer of security that you need, but can’t keep up with the increasing number of malware attacks. It does a better job at covering threats like worms, viruses, trojans, while advanced malware strains (ransomware, phishing or social engineering threats) manage to evade AV detection. Last year, massive spam campaigns like WannaCry or NonPetya could fly below the radar of antivirus software and go undetected during the first hours or days. The timing was crucial for both home users and organizations and we’ve seen the damages caused. Here’s an example of a spam campaign we monitored and analyzed to see how long it takes AV engines to detect advanced malware. During this malicious campaign, cybercriminals tried to bait victims into clicking on a malicious link to deliver the NanoCore malware on their devices. The results from VirusTotal showed that in the first day only 5 AV engines out of 64 could detect this malicious campaign. A few days later, 37 out of 64 engines could find it. This indicates a low detection rate for antivirus during the first stages of an attack. Nowadays, cyber attacks are brand new and unlisted in antivirus databases, which are designed to sneak past your AV product and compromise your computer. People rely on antivirus as their only protective layer, but it’s just not enough. Antivirus is often ineffective in blocking ransomware attacks. 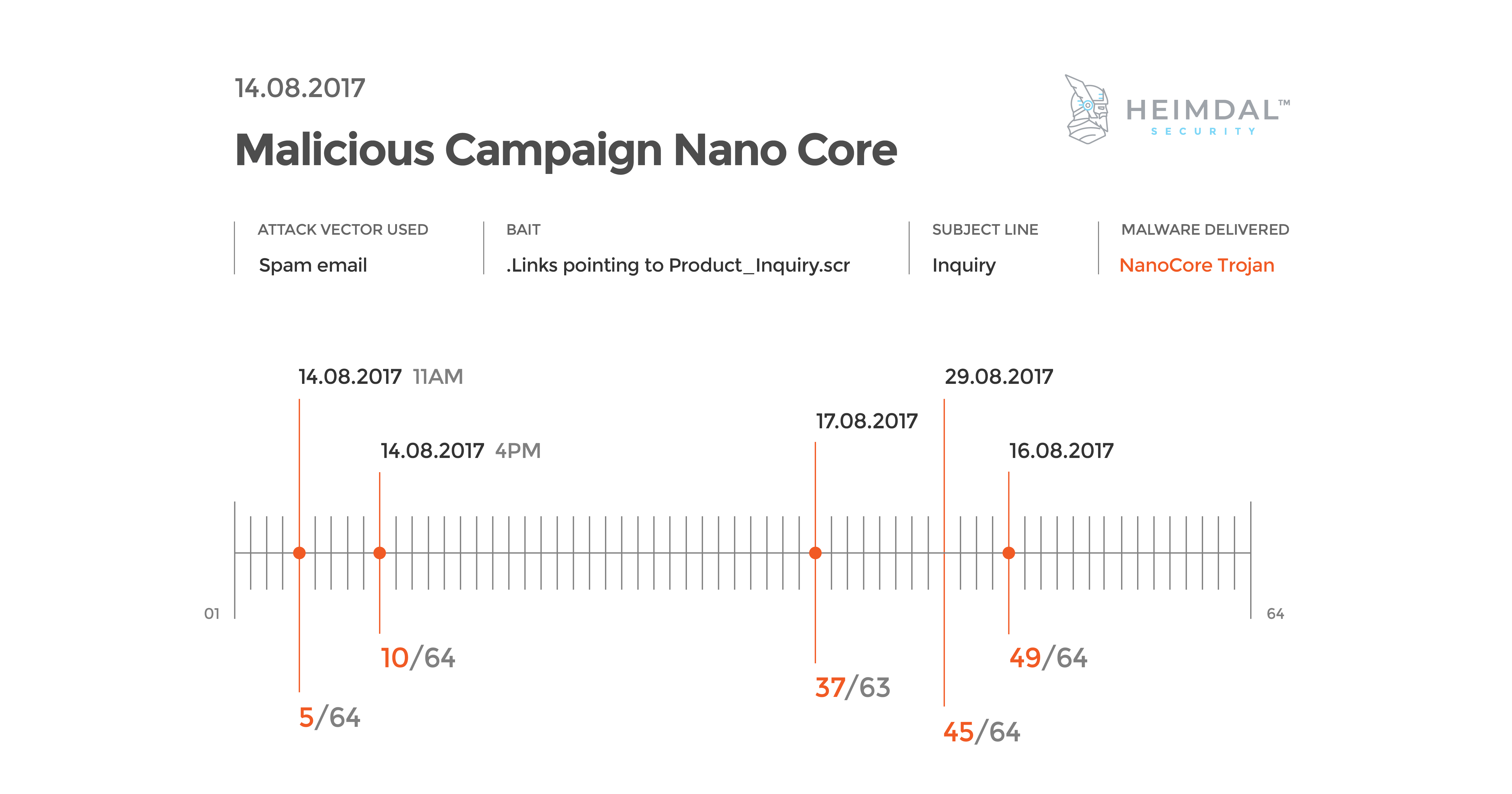
 You can see other examples of spam campaigns explaining why AV detection for new malware remains low. Why extra layers of security are needed A multi-layer approach is needed to better fight ransomware infections that can spread quickly and harvest users’ data. This happens because the malware scanning is rather reactive than proactive. The newer a malware strain is, the harder will be for AV to detect it. The purpose of a multi-layered security system is to stop cyber attacks on different levels, so they never reach the core of the system and essential information. Malicious actors can find ways to manipulate the data that flows through your Internet connection to serve their malicious purposes. We spend a large amount of time browsing the Internet, but have you thought about the danger you are exposed to? We believe that everyone should enjoy the web safely when navigating online. To do that, you will need a tool that can help you filter the Internet traffic and eliminate all the threats out there that antivirus can’t block. A tool focused on proactive cybersecurity. We believe that you shouldn’t wait for something bad to happen to improve your online safety and protect your digital assets.
You can see other examples of spam campaigns explaining why AV detection for new malware remains low. Why extra layers of security are needed A multi-layer approach is needed to better fight ransomware infections that can spread quickly and harvest users’ data. This happens because the malware scanning is rather reactive than proactive. The newer a malware strain is, the harder will be for AV to detect it. The purpose of a multi-layered security system is to stop cyber attacks on different levels, so they never reach the core of the system and essential information. Malicious actors can find ways to manipulate the data that flows through your Internet connection to serve their malicious purposes. We spend a large amount of time browsing the Internet, but have you thought about the danger you are exposed to? We believe that everyone should enjoy the web safely when navigating online. To do that, you will need a tool that can help you filter the Internet traffic and eliminate all the threats out there that antivirus can’t block. A tool focused on proactive cybersecurity. We believe that you shouldn’t wait for something bad to happen to improve your online safety and protect your digital assets.
What Heimdal™ Threat Prevention can do for you
If you didn’t know about our product, Heimdal™ Threat Prevention is built to protect its customers from attacks like ransomware traditional antivirus can’t detect. Heimdal™ Threat Prevention can block different ransomware infection sources such as malicious email attachments, infected links you may receive in your email, infected web pages or malicious web apps that appear legitimate at first, but aimed at spreading ransomware. Here’s how Heimdal™ Threat Prevention works and how it can stop a ransomware infection in 4 different stages: 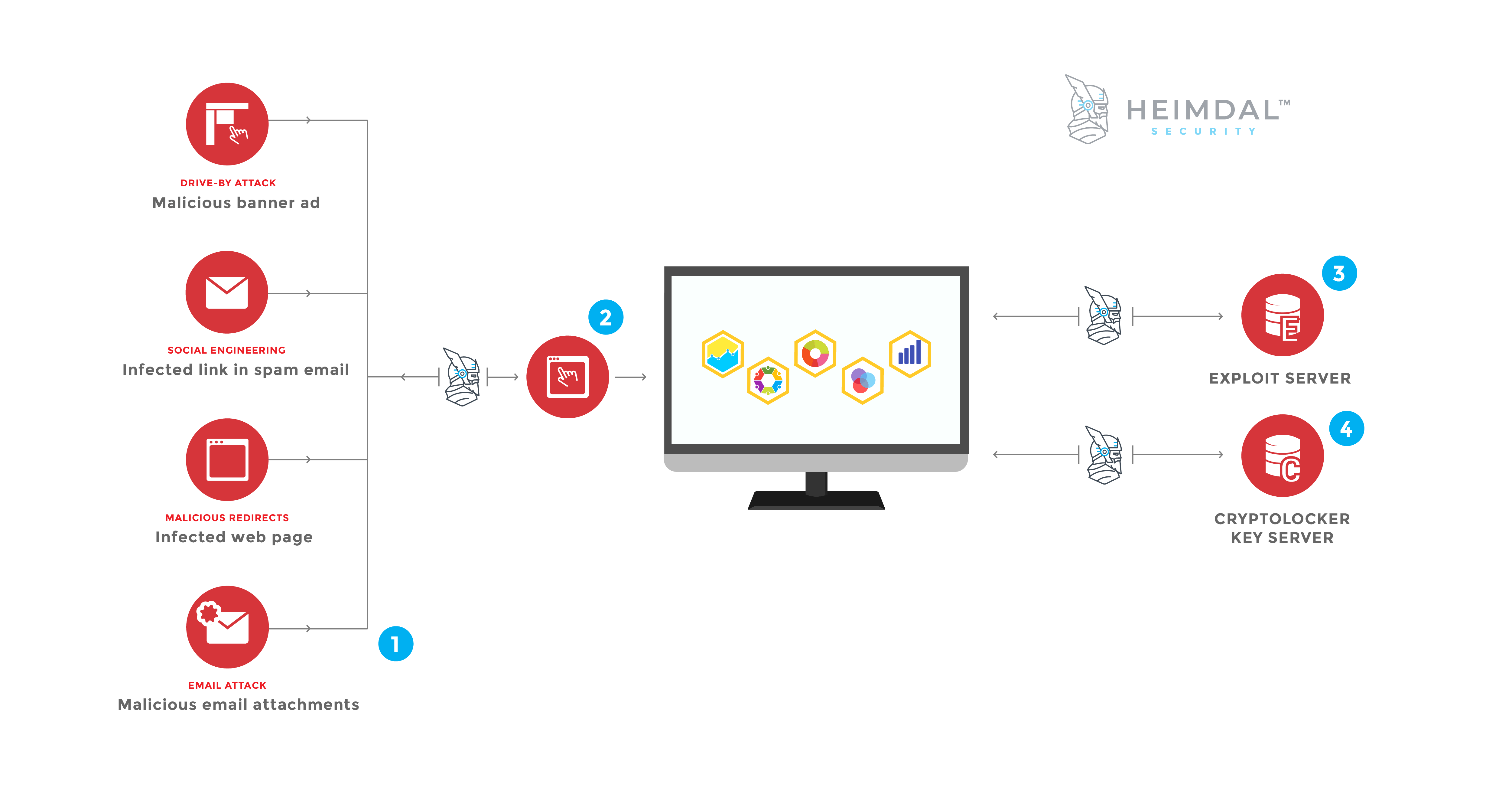 Heimdal™ Threat Prevention is an antimalware solution that includes three layers of protection against ransomware. 1. Traffic scanning and filtering With its DarLayer Guard feature, Heimdal™ Threat Prevention proactively scans for all your incoming and outcoming Internet traffic to identify all types of malicious connections. It does that by changing the DNS (Domain Name System) for IPv4 and IPv6 to a different address and block a malicious web address. When the engine is enabled, Heimdal™ Threat Prevention will apply a filter on the network adapter that will scan for infected sites and other web locations (servers, online ads, etc) with the potential to install ransomware on your devices. In the image below, on the right side, you can see how many web traffic scans Heimdal has performed on your system. You should know that all the filtering process takes place quickly and will not affect your Internet connection speed.
Heimdal™ Threat Prevention is an antimalware solution that includes three layers of protection against ransomware. 1. Traffic scanning and filtering With its DarLayer Guard feature, Heimdal™ Threat Prevention proactively scans for all your incoming and outcoming Internet traffic to identify all types of malicious connections. It does that by changing the DNS (Domain Name System) for IPv4 and IPv6 to a different address and block a malicious web address. When the engine is enabled, Heimdal™ Threat Prevention will apply a filter on the network adapter that will scan for infected sites and other web locations (servers, online ads, etc) with the potential to install ransomware on your devices. In the image below, on the right side, you can see how many web traffic scans Heimdal has performed on your system. You should know that all the filtering process takes place quickly and will not affect your Internet connection speed. 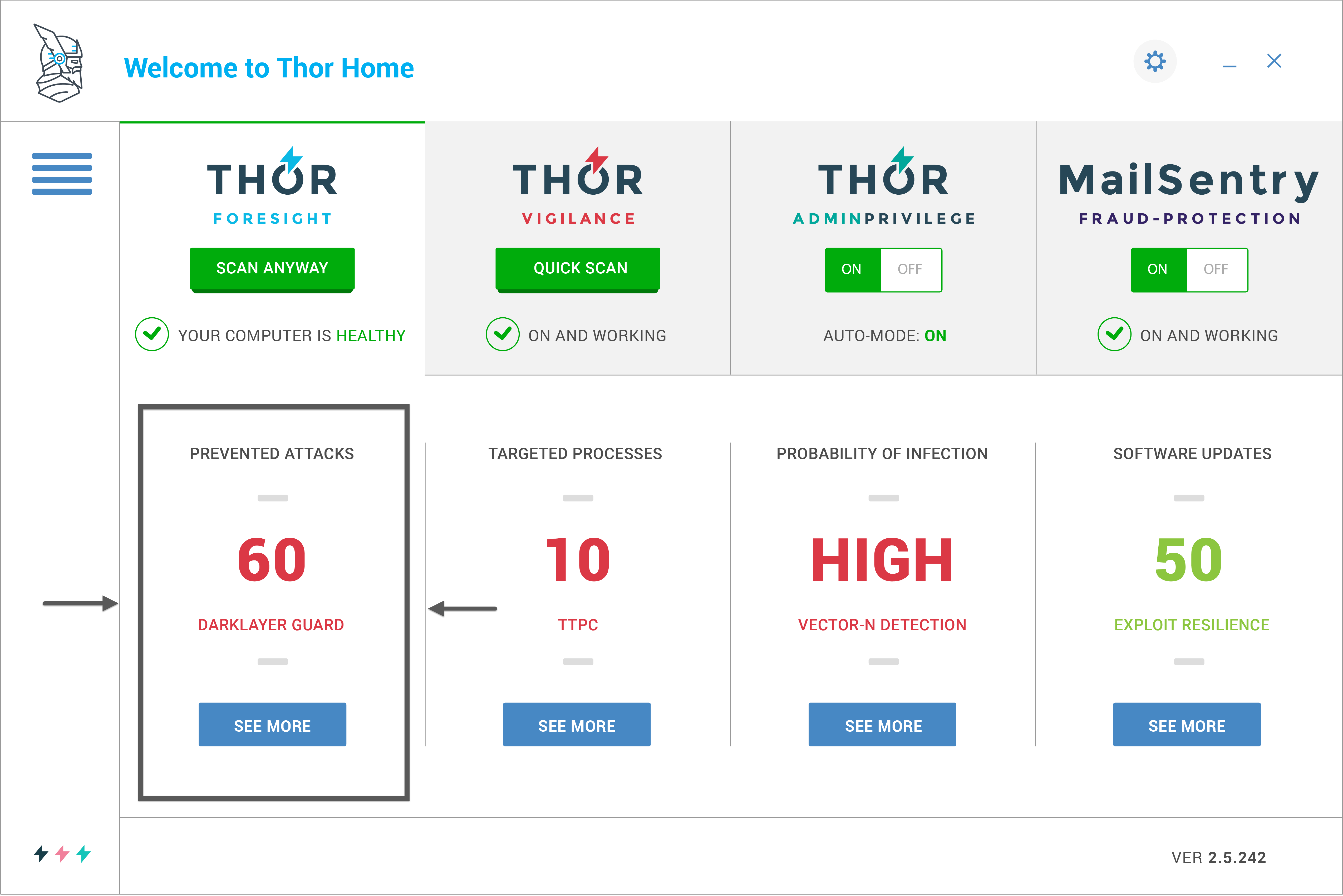 2. Detection and blocking of advanced malware (VectorN Detection) The Malware engine analyzes potentially malicious code to detect and block ransomware attacks. It compares the signatures of the files on your PC with our constantly updated database to find any matches. With the malware scanning feature, Heimdal™ Threat Prevention works proactively to detect and block second-generation malware like ransomware that tries to compromise users’ endpoints and encrypt their files. All websites you are accessing are scanned and verified in our internal database. You can choose to turn it off, but we don’t recommend doing it, because it will decrease your protection level. VectorN Detection feature works hand in hand with the DarkLayer Guard feature and tries to search and detect patterns in the number of blocks that DuarLayer Guard records. It uses Machine Learning Detection (MLD) to perform an in-depth analysis of all incoming and outgoing HTTPS, HTTPS, and DNS traffic. 3. Automatic and silent patching feature was created to silently keep your software programs and applications, including operating system, up to date and patched, without annoying you with notifications. In Heimdal™ Threat Prevention, the patching system includes two sections:
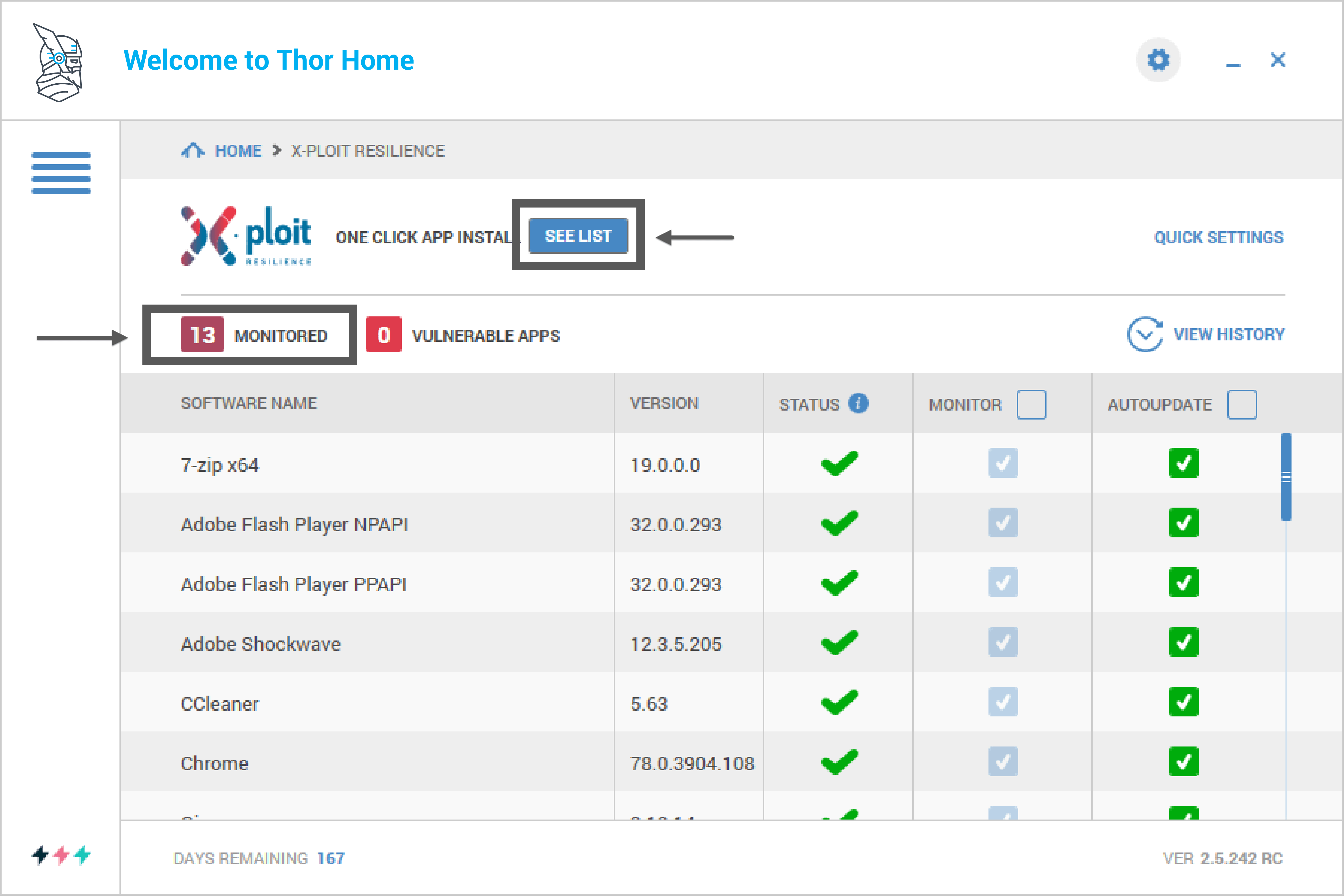
2. Detection and blocking of advanced malware (VectorN Detection) The Malware engine analyzes potentially malicious code to detect and block ransomware attacks. It compares the signatures of the files on your PC with our constantly updated database to find any matches. With the malware scanning feature, Heimdal™ Threat Prevention works proactively to detect and block second-generation malware like ransomware that tries to compromise users’ endpoints and encrypt their files. All websites you are accessing are scanned and verified in our internal database. You can choose to turn it off, but we don’t recommend doing it, because it will decrease your protection level. VectorN Detection feature works hand in hand with the DarkLayer Guard feature and tries to search and detect patterns in the number of blocks that DuarLayer Guard records. It uses Machine Learning Detection (MLD) to perform an in-depth analysis of all incoming and outgoing HTTPS, HTTPS, and DNS traffic. 3. Automatic and silent patching feature was created to silently keep your software programs and applications, including operating system, up to date and patched, without annoying you with notifications. In Heimdal™ Threat Prevention, the patching system includes two sections:
- software patching (designed to monitor and update the programs installed on your computer and details about them)
- recommended software (here you’ll find programs Heimdal recommends to install that will automatically be inserted into the software patching list).
 To better handle ransomware attacks, you need to see the bigger picture and take all the security measures to prevent these attacks. Use this anti-ransomware protection plan and better secure your endpoints against ransomware. What you should know is that Heimdal™ Threat Prevention is compatible with any antivirus product available on the market that will block threats at their root. An anti-malware solution isn’t meant to replace your AV product, but complement it, so users can benefit from multiple layers of protection to better fight against ransomware. With both software products installed on a PC, more security gaps are closed and you can enhance online safety. Please let us know what you think of our product and what other features you’d like us to include. Your feedback is important.
To better handle ransomware attacks, you need to see the bigger picture and take all the security measures to prevent these attacks. Use this anti-ransomware protection plan and better secure your endpoints against ransomware. What you should know is that Heimdal™ Threat Prevention is compatible with any antivirus product available on the market that will block threats at their root. An anti-malware solution isn’t meant to replace your AV product, but complement it, so users can benefit from multiple layers of protection to better fight against ransomware. With both software products installed on a PC, more security gaps are closed and you can enhance online safety. Please let us know what you think of our product and what other features you’d like us to include. Your feedback is important.



 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










