Contents:
Free encryption software has become more important than ever to keep our information safe.
Whether it’s personal or work-related, our sensitive data is always at risk of falling into the wrong hands, all the more reason to choose the best free encryption software.
In this article, you’ll discover the top encryption software tools to protect your sensitive data, along with insights on:
- What Is Data Encryption?
- The Top Free Encryption Tools in 2025
- 4 Steps to Enhance Online Security
- Keep Your Most Valuable Data Safe and Secure with Heimdal®
What Is Data Encryption?
On a basic level, encryption is one of the best protection methods available to keep all your digital assets safe.
The process uses encryption keys and an algorithm to transform the accessible data into an encoded piece of information that can only be deciphered by authorized users.
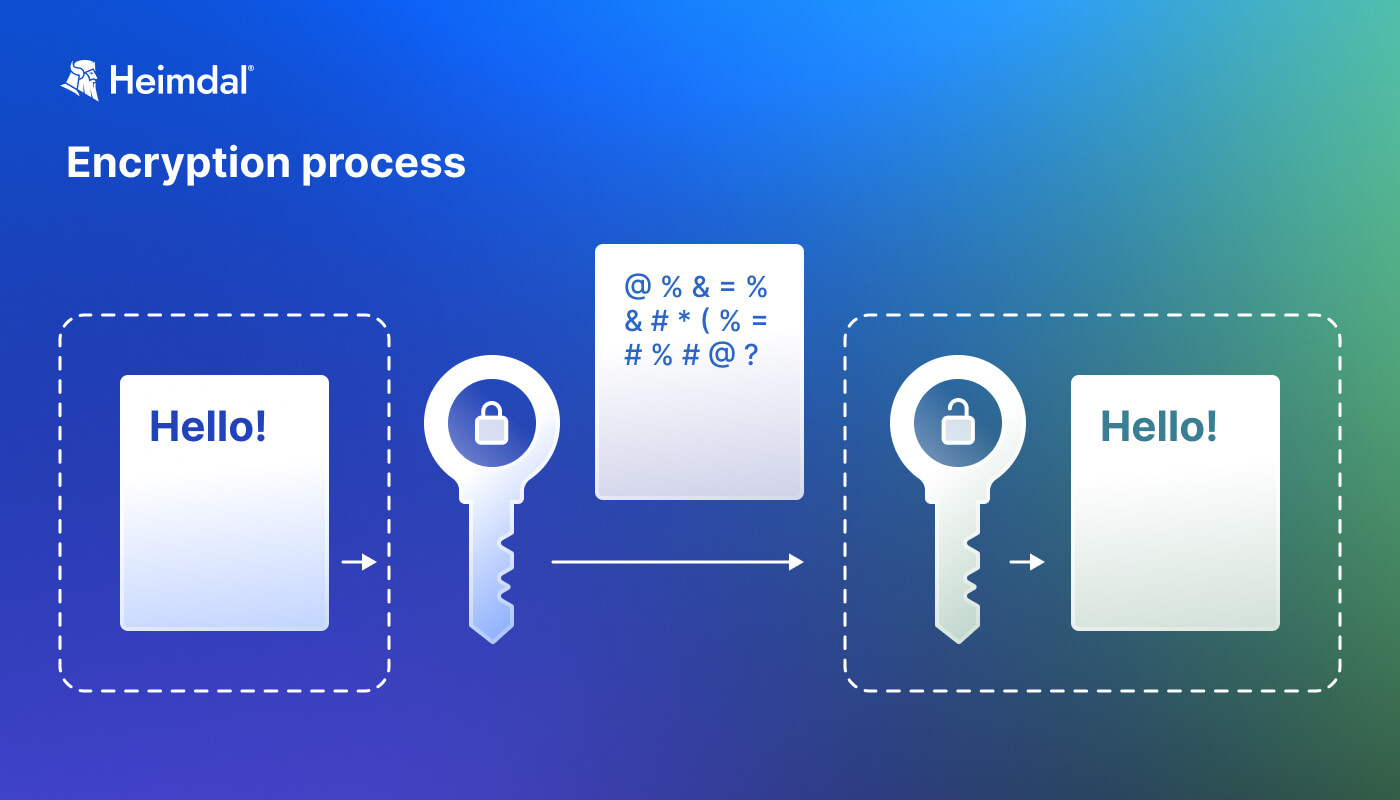
The Encryption Process Explained
Encryption protects your private information from hackers and other cyber threats, making it difficult for them to get access. It also helps you safely store large amounts of data or keep private conversations secure on the Internet.
According to “The 2022 Global Encryption Trends Study” released by the Ponemon Institute,
…62% of organizations have an encryption strategy in place – the sharpest increase in adoption in nearly two decades.
Internet users and organizations alike can use free encryption tools to increase security. These tools help keep important information safe from hackers. You should use encryption tools to protect critical data, whether it’s stored on your computer or transmitted through the Internet.
So which are these encryption tools? We’ve put together this list of encryption software to choose from.
Before we explore free encryption tools, let’s highlight why it’s crucial to always use strong and unique passwords for all your online accounts. When setting up your encryption process, you’ll be asked to choose a password as your decryption key. Before you do that, remember to use these practical security tips to handle your passwords like an expert, making them stronger and harder for hackers to compromise.
- Set unique and strong passwords that contain different characters, like uppercase and lowercase letters and numbers, and are more than 15 characters long. You can use several tools to test if your passwords are strong enough.
- Also, you’ll need to set passwords that are hard to remember or guess and aren’t used for multiple accounts.
- To enhance your online security, you should not keep your passwords saved in text files or browsers.
- Never use/reuse the same password for more than one account.
- Do not share your passwords in emails, instant messages, or other online platforms.
To learn more about the different types of password attacks, make sure you watch the video below:
The Top Free Encryption Software Tools in 2024
We carefully curated and put together some of the best free-of-charge encryption software tools you can use to keep your most valuable data safe and secure.
1. LastPass
LastPass is a popular password manager. It has a free version with limited features. But it still keeps your passwords and personal data safe. With encryption tools like this, you won’t need to remember passwords or write them down. LastPass is easy to use and simplifies things. It has extensions for the main web browsers, like Firefox and Chrome. Also, you can use the mobile app available for both Android and Apple.

When you create a new online account, it offers the option to save the new credentials. This tool encourages you to set a unique and hard-to-break password and discourages users from reusing it. If you’re using the same password for multiple accounts, it simply recommends selecting a different password. Other password management tools you can use Sticky Password or RoboForm come with an intuitive and easy-to-use interface and can provide good password security. To safely manage passwords, we encourage users to follow the security steps included in this guide. Use a two-factor authentication or multi-factor authentication system, whenever possible.
2.BitLocker
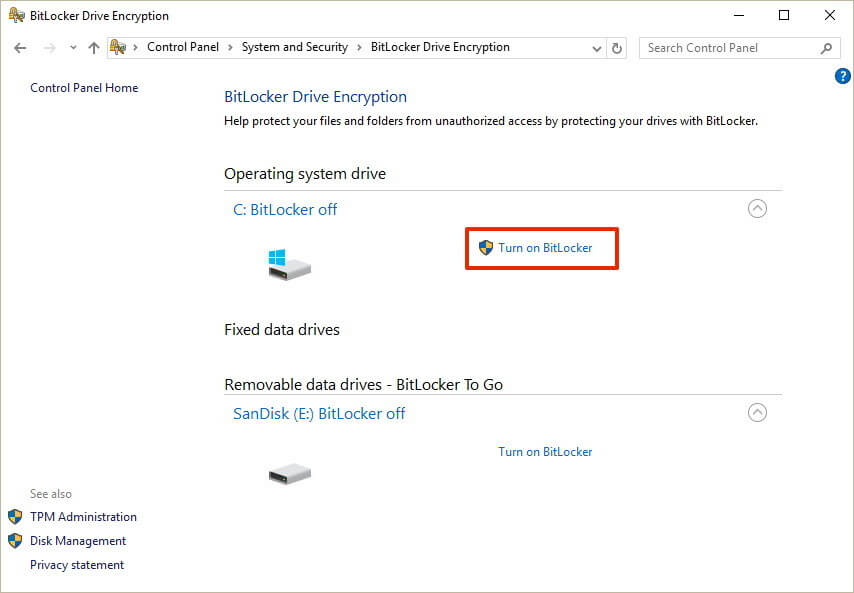
Source: Windows Central
While there are many encryption tools available you can use to encrypt your data locally, most users prefer to use Microsoft’s BitLocker software. You can either use it to encrypt a particular disk partition or the entire hard disk.
BitLocker is a full-disk encryption software built-in in the latest Windows operating systems (Windows 10), which uses AES (128 and 256-bit) encryption to encrypt data on the drives. The Advanced Encryption Standard (AES) is widely used by most security vendors around the world. It’s known for its high security and efficiency. Why you should choose BitLocker:
- Easy to use and it’s already integrated into your Windows operating system, so there’s no need to add another encryption software;
- It’s a free data encryption software tool you can use to prevent data breaches and data exfiltration from your hard disk.
- It encrypts your entire drive, which makes it impossible for malicious actors stealing your laptop to remove the hard drive and access your sensitive files.
- When BitLocker Drive Encryption is activated, and you add new files, BitLocker will encrypt them automatically.
3. VeraCrypt
Another free tool you can use and is available for Windows, OS X, and Linux operating systems. Just like BitLocker, it supports Advanced Encryption Standard (AES) and can hide encrypted data within other data. It is an open-source program which means developers and researchers can download and use the source code.
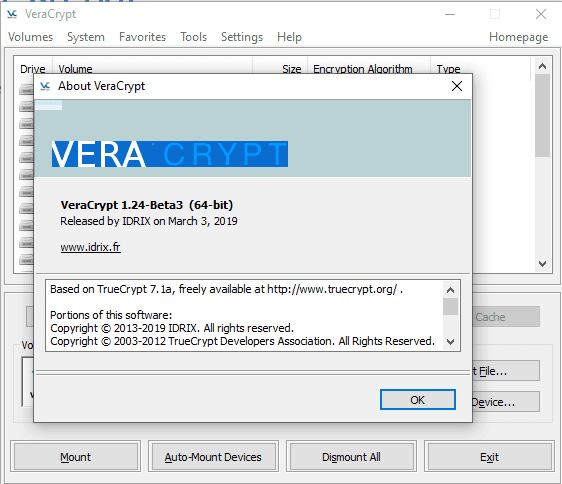
Source: GHacks.net
This encryption software is a great alternative to TrueCrypt tool and is constantly getting improvements and security enhancements. VeraCrypt 1.24, the upcoming next version of VeraCrypt is currently available for beta tests and can be downloaded from here. The new version is expected to come with lots of security and functionality improvements to better secure users’ data.
4. FileVault 2
Looking to encrypt your data stored on devices featuring macOS and Mac hardware? FileVault 2 is an encryption software tool we recommend checking out. Just like BitLocker and VeraCrypt tools, FileVault 2 (FileVault full-disk encryption) uses XTS-AES-128 encryption with a 256-bit key “to help prevent unauthorized access to the information on your startup disk”. If you’re interested in installing it on your Mac computer, this guide will come in handy.
5. DiskCryptor
Yet another open-source and free encryption software you can use to secure your internal and external drive, including system partition, and even ISO images, or USB flash drives, or any other storage devices. Just like BitLocker, it is a full-disk encryption tool for Windows OS and includes multiple encryption algorithms such as AES, Twofish, and Serpent. The interface is simple and intuitive, all you need to do is select the drive and click on “Encrypt” to protect your data.
6. 7-Zip
Many users are not interested in encrypting the entire hard disk, but only specific files and documents that store sensitive information. It’s a free and open-source encryption software, as well as a lightweight solution known for its simplicity. This software tool can extract most archives and features strong AES-256 encryption.
Source: GHack.net
After the critical security vulnerability that affected all WinRAR versions and other programs, a stable version of 7-Zip 19.00 has been released and can be downloaded from the 7-Zip site.
7. AxCrypt
Similar to 7-Zip, AxCrypt is an open-source file encryption software offering both a free solution and a premium version for Windows, macOS, Android, and iOS. It features AES-256 file encryption and can efficiently encrypt one file, an entire folder, or a group of files with a simple right-click. Files can be encrypted for a specific period or can be auto-decrypted later on when that file reaches the destination. So, how can I increase my online security without creating too many barriers that may slow down my access to the information posted online? See below a few simple tools you can use to access online content and stay safe from data breaches at the same time.
8. HTTPS Everywhere
Encrypting your sensitive files is not enough. To stay ahead of cybercriminals, you must improve your online protection. This means ensuring no one can spy on your internet communication. We suggest using a browser extension like HTTPS Everywhere to ensure you always access secure web pages that use encryption mechanisms. It works with Firefox, Opera, and Chrome. This tool, made by EFF and the Tor Project, automatically changes unsecured “HTTP” sites to secure “HTTPS” sites.
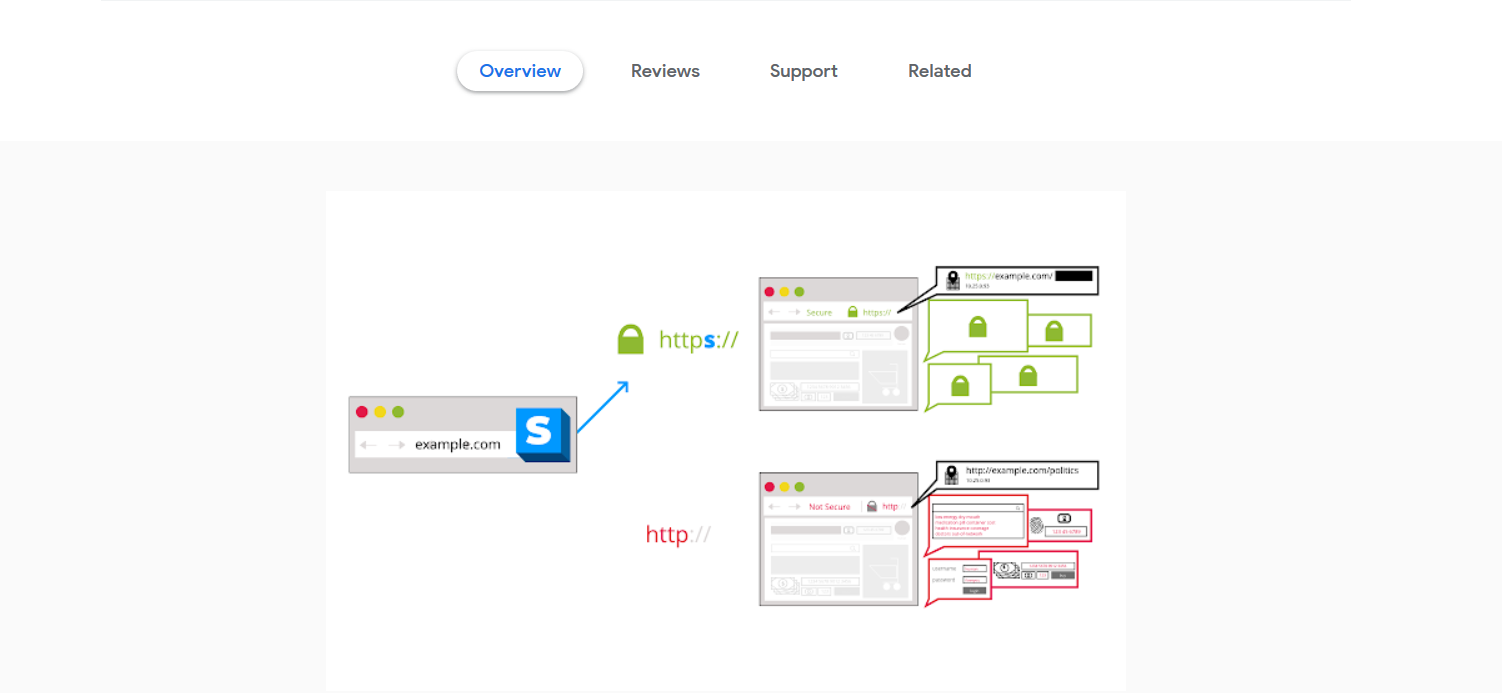
Using an extension like HTTPS Everywhere, which encrypts your communication with major websites you access daily, will make your online activities more secure from multiple online threats.
9. Tor Browser
If you want to browse the Internet without being tracked, the Tor browser is a good choice. It encrypts your online activities to hide them. The Tor Browser also blocks plugins like Flash, RealPlayer, and Quicktime. These plugins can reveal your IP address.
Avoid installing additional add-ons or plugins in Tor Browser, as they can bypass Tor and compromise your privacy and security. The specially designed Tor Browser allows anyone to conceal their browsing activity from prying eyes.
The most recent version of this browser, Tor Browser 0.4.0.4, is in the release candidate available for download, and it fixes several bugs from previous versions. Remember this is not a stable release yet, but “packages should be available over the coming weeks, with a new alpha Tor Browser release by early next week.” For those who don’t know, Tor is the short version of “The Onion Router” and directs your Internet traffic by encrypting the IP address from where it came from.
Encryption software like Tor makes it harder for malicious actors to trace your online activities.
10. CyberGhost
A VPN (Virtual Private Network) is another way to keep your online identity private. It encrypts your communication, protecting it from being intercepted. A VPN stretches over the Internet to form a secure channel. This keeps your sensitive data safe from hackers and nosy people. It hides your IP address and secures your online banking and Wi-Fi use. You can use VPN software, like Cyberghost, for safe browsing on public networks or to access content limited to specific areas. You can browse in a private mode from another country and get access to more than 1,000 servers across 50+ countries.
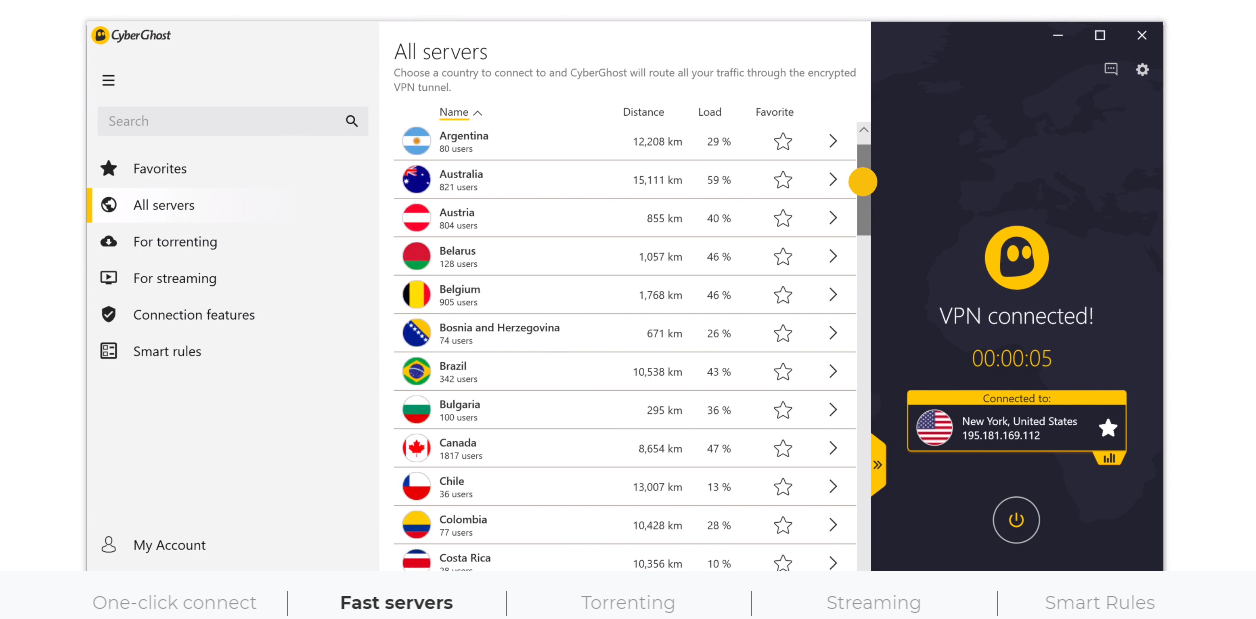
CyberGhost is a popular VPN solution to ensure your web traffic and valuable information remain encrypted. It is the winner of the “Best Value” category at the BestVPN.com Awards 2019. It includes a 30-day money-back guarantee for everything else and friendly support. A VPN service provider like Cyberghost helps you keep your data protected and secure your digital assets. Cyberghost works with Windows, macOS, iOS, Android, Linux, or routers. If you’re a noob and want to learn more about the VPN industry, this beginner’s guide will help you learn more about its basics, how to choose a VPN, and more.
11. ExpressVPN
For privacy enthusiasts, here’s another VPN service you can use to encrypt your data and keep cybercriminals at bay. Similar to CyberGhost, this one uses 256-bit AES encryption technology and the setup is simple. Simply download, install, and connect to ExpressVPN with a few clicks. Compatible with multiple devices, it works on Windows, Mac, iOS, Android, or Linux and connects to more than 148 locations in 90+ countries. It’s not entirely free, but you can use it free of charge for up to one month and get a 30-day money-back guarantee.  Source: VPNMentor.com
Source: VPNMentor.com
4 Steps to Enhance Online Security
It’s essential to implement comprehensive security measures, not just encryption, to fight threats like ransomware. Our blog posts and guides always emphasize that you should have multiple layers of security to stay ahead of hackers. There are lots of online threats, and malicious actors keep changing their attack tactics. Hence, we suggest these practical steps to make your online security better:

4 Steps to Enhance Online Security
- Keep your browser and operating system updated with the latest security patches. Make sure you have the latest versions running on your system. Cybercriminals spread malicious tools by using security exploits to take advantage of your system’s vulnerabilities. Patching is key, as the experts said again and again. Check out our article and discover 8+ free and open-source patch management tools for your company.
- Install a trusted antivirus program. Also, add extra layers of security. Our Endpoint Security Suite offers comprehensive, proactive protection for your online activities. Check out our article and discover ten open-source EDR tools to enhance your cyber-resilience factor.
- Be very careful when connecting to public and free wireless networks. One of the favorite methods used by online criminals to retrieve your credentials is to use wireless sniffers to access data you send over unprotected networks.
- Education is the best way to protect your online information. We suggest looking at our free educational resources and signing up for a course to learn more about online safety.
Keep Your Most Valuable Data Safe and Secure with Heimdal®
When you encrypt files and data, you’re using cryptographic methods to secure it, making it unreadable without the correct decryption key or password. This is a fundamental security practice to protect data confidentiality.
The issue is when attackers deploy ransomware to encrypt files that you already encrypted or unencrypted data on your system.
They don’t decrypt your encrypted data but instead encrypt your files again with their own encryption, effectively locking you out until you pay a ransom for the decryption key. What can you do?
Heimdal’s Ransomware Encryption Protection module empowers you to defend your entire digital estate against one of the most dangerous cyber threats of the decade – ransomware.
Heimdal employs outstanding technology to solve outstanding problems. Ransomware Encryption Protection is the only practical approach to malicious encryption associated with ransomware attacks. Prevent and protect, not just mitigate, both in the cloud & on-premises.

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;
Installing a good anti-ransomware solution could save you a lot of time and money. Heimdal® is offering its customers an incredible integrated cybersecurity suite including the Ransomware Encryption Protection module, that is universally compatible with any antivirus solution, and is 100% signature-free, ensuring superior detection and remediation of any type of ransomware, whether fileless or file-based (including the most recent ones like LockFile).
Heimdal offers the latest in cybersecurity protection against advanced cyberattacks. Our security solutions are designed to work with your company’s needs and budget.
If you liked this article, make sure you follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










