Contents:
In the current communication environment where time is essential and everybody needs to be as efficient as possible, messaging has become an important component of our daily life. Common to both individuals and businesses, the habit of using all sorts of apps for sending and receiving messages can sometimes become a threat as not all apps implement end-to-end encryption.
In this article, I am going to talk about end-to-end encryption and how it works, why it became essential, its advantages and downsides, and, of course, its applicability.
What Is End-to-end Encryption?
End-to-end encryption, also known as E2EE is a method to secure data communication between 2 parties by applying encryption in such a way that only the targeted recipient can decrypt/read it.
As it moves to its destination, it is impossible for third parties such as internet or app service providers, cybercriminals, or even governments to read or interfere in any way with the message. Simply put, by encrypting communication for both ends (sender and recipient), end-to-end encryption stops anyone who is not involved in the discussion from reading personal conversations.
This way, third parties will not be able to access the cryptographic keys required to decrypt the conversation.
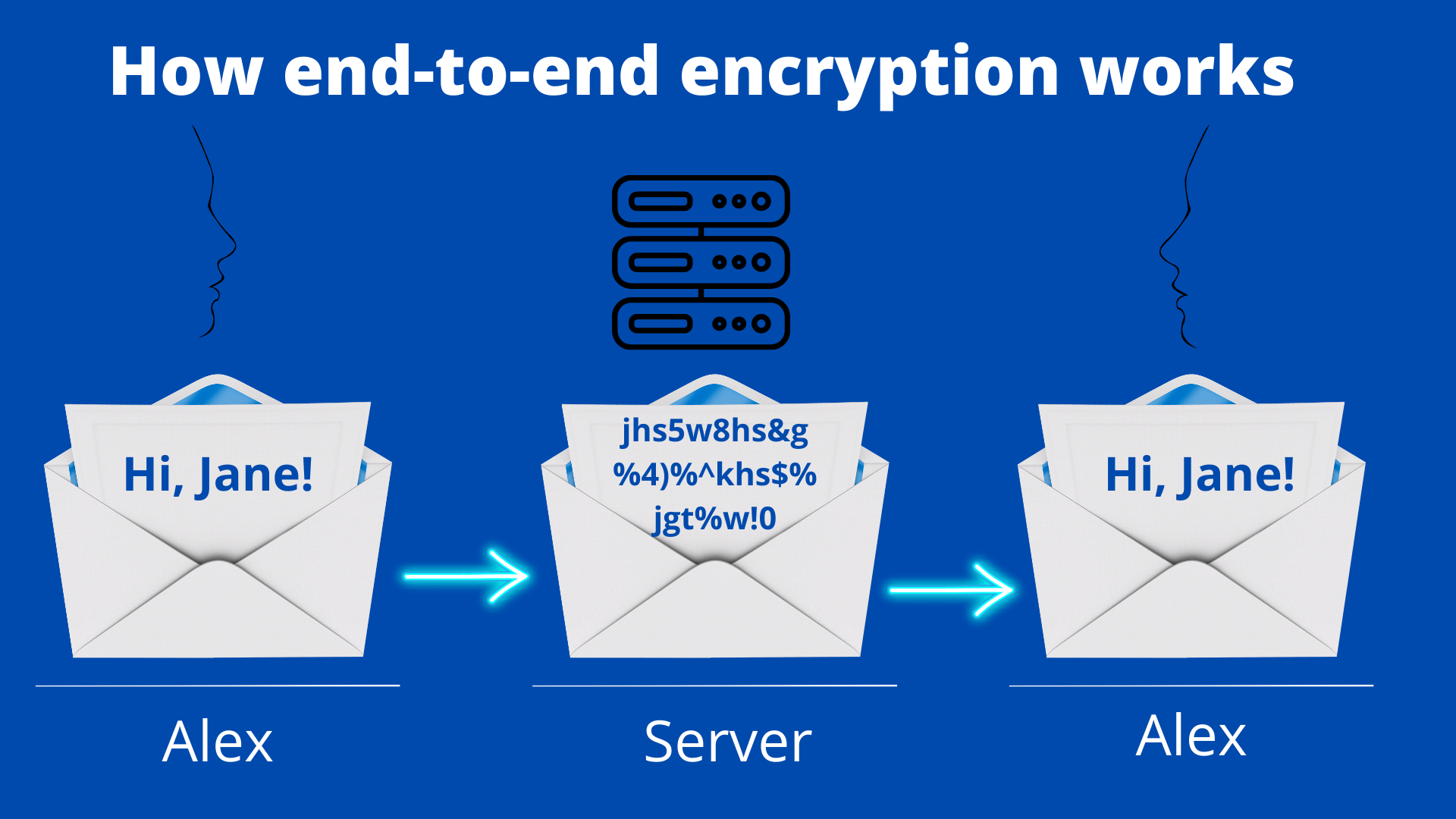
How Does End-to-end Encryption Work?
In essence, end-to-end encryption (E2EE) changes human-readable plaintext to incoherent text, also known as ciphertext. In other words, it takes a legible message and changes it so that it appears haphazard.
There are two types of encryption – asymmetric and symmetric:
Asymmetric Encryption (Public-key Cryptography) uses two distinct keys that are connected with a mathematical algorithm in order to encrypt and decrypt the transferred data. This is known as “Public and Private Key Pair”. The Public-key is used for encryption and the Private Key is used for decryption. As the name indicates, the Private Key is designed to be private and unique so that only the targeted recipient can decode the data.
Some examples of asymmetric encryption algorithms include:
- RSA (Rivest, Shamir, and Adleman)
- Diffie-Hellman
- ECC (Elliptic-curve cryptography)
- El Gamal
- DSA (Digital Signature Algorithm)
Symmetric encryption is a type of encryption where only one key is used to encrypt and decrypt the information. In this situation, both sender and recipient share the same encryption key.
Some examples of symmetric encryption algorithms include:
- AES (Advanced Encryption Standard)
- DES (Data Encryption Standard)
- IDEA (International Data Encryption Algorithm)
- Blowfish (Drop-in replacement for DES or IDEA)
- RC4 (Rivest Cipher 4)
- RC5 (Rivest Cipher 5)
- RC6 (Rivest Cipher 6)
Asymmetric Encryption is newer and more secure but needs a lot more processing power, making it much slower than Symmetric Encryption.
Benefits of End-to-end Encryption
Private data is protected against hacking campaigns. When using end-to-end encryption, only the sender and the intended recipient have access to unencrypted data. For example, if the email service that stores your data happens to be compromised, cybercriminals will not be able to decrypt the data within as they lack the decryption keys.
Everyone has the right to keep their personal data private. E2EE protects free speech and safeguards oppressed individuals.
Complete control. The end-to-end encryption method gives the sender full control of the process. No matter where the information moves, the data owner can change controls, revoke access, or restrict sharing.
Great flexibility. The user can decide what data to encrypt, usually highly sensitive data.
No one can change the message. End-to-end encrypted messages can’t be undecrypted by anyone other than the intended receiver. If someone alters the encrypted data, the message becomes mixed up on decryption, and the recipient will know what happened.
Compliance. Nowadays, almost all the fields are limited by regulatory compliance meaning that they have to conform to a rule such as a specification, policy, standard or law so here is where end-to-end encryption comes into play. Thanks to the E2EE method, businesses everywhere can protect their data by making it impossible to read by an unauthorized individual.
Device protection is better than server protection. Unlike other encryption types that encrypt information on the server where cybercriminals or other outsiders can easily obtain access and decrypt it, with end-to-end decryption attackers have to hack the device to get the data. Most threat actors don’t carry out these types of attacks as they are difficult and take a lot of time.
Disadvantages of End-to-end Encryption
E2EE is not enough. If a device gets stolen or lost and it is not protected, even if only with a PIN code, the person who gains access to it will be able to read, and even send messages on the owner’s behalf. End-to-end encryption goes hand in hand with device protection and app permissions.
Illegal activity. Government and law enforcement agencies are worried that end-to-end encryption is allowing individuals to share illicit content and not be caught. Law enforcement officers are not able to find proof and service providers can’t cooperate in an official investigation if they are asked to.
Not everything is private. Even if the data that is being transferred is encrypted hence indecipherable, information about the sender is still visible.
It takes two to tango. No matter how careful one might be when it comes to the security of their devices, they can’t control what the other one is doing with their mobiles or laptops and who might have access to their messages.
End-to-end Encryption Applicability
Instant messaging
There are plenty of chat apps offering messaging services that have upped their game on the security and privacy fronts by using end-to-end encryption. Without end-to-end encryption, our private conversations most likely will get into the hands of hackers, and other malicious actors focused on accessing them.
My colleague Miriam compiled a list of the most secure encrypted messaging apps that will help you find the application that suits you best.
Email communication
Communicating via emails has become an essential and effective habit that allows us to stay in touch with our families, friends, or coworkers. So, if email communication is so popular why wouldn’t cyber criminals try to read our messages and steal our information?
This is the main reason why you should use encrypted emails services. So that all the messages, attachments, and information you share via email stay private and are only opened by the intended recipients.
My colleague Cezarina has put together a list of user-friendly web-based encrypted email services that will help you increase your level of online anonymity. The end-to-end email encryption method is a must because it provides the highest level of confidentiality and security to your email communication.
End-to-end encryption is used by all sorts of software applications
End-to-end encryption is currently being used in the healthcare, communications, or finance sectors every time when it comes to data protection. It is frequently used by organizations in order to act in accordance with data privacy and security regulations and laws.
Wrapping Up…
End-to-end encryption makes you feel confident and safe when transferring and handling confidential data, whether it’s banking information, healthcare-related records, official documents, legal proceedings, or just private discussions with your friends you don’t want anyone else to see.
Regardless of its weak points, end-to-end encryption is currently the most secure method to send sensitive data, and that’s why more and more communication services are starting to embrace it.
Heimdal Security offers the latest in cybersecurity protection against advanced cyberattacks. Our security solutions are designed to work with your company’s needs and budget.

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










