Contents:
Ransomware is one of the most vicious cyber threats out there right now. A dangerous form of malware, it encrypts files and holds them hostage in exchange for payment. Luckily for you, there are plenty of ransomware decryption tools that you can use to get access to your files without needing to pay the ransom.
If your network gets infected with ransomware, follow the mitigation steps below and use this list with over 200 ransomware decryption tools.
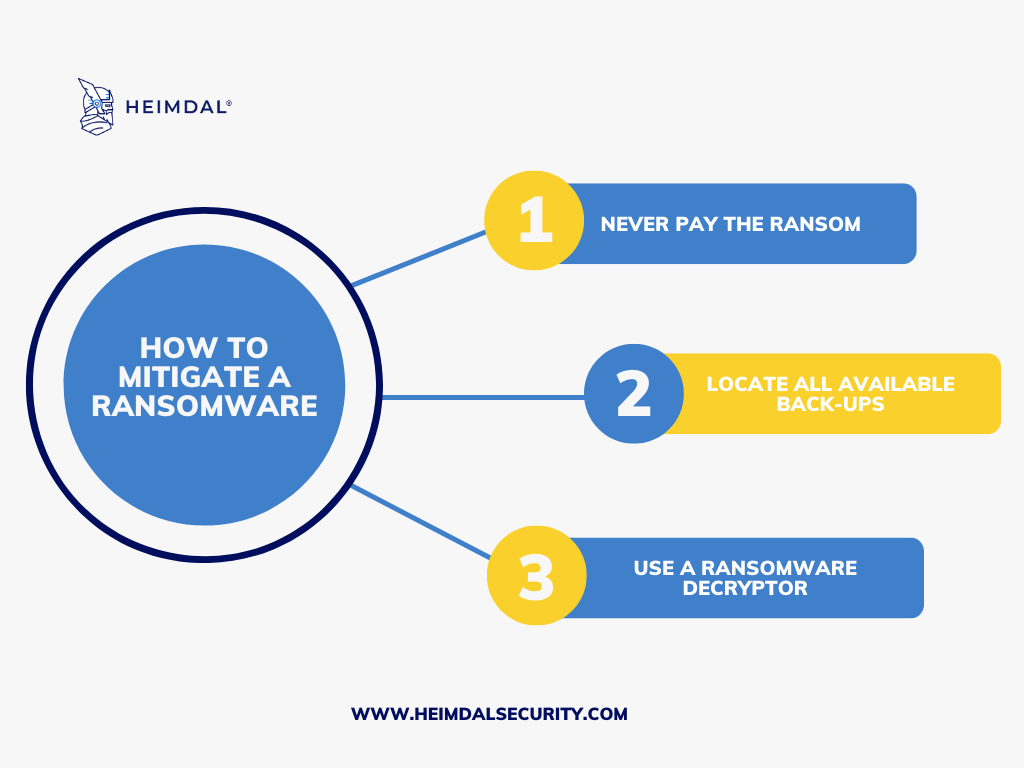
Steps to Recover Your Data:
Step 1: Do not pay the ransom because there is no guarantee that the ransomware creators will give you access to your data.
Step 2: Find any available backups you have, and consider keeping your data backups in secure, off-site locations.
Step 3: If there are no backups, you have to try decrypting the data locked by ransomware using these ransomware decryptors.
Navigate through these links to learn more.
- How to identify the ransomware you’ve been infected with;
- Ransomware decryption tools;
- Ransomware families vs tools for decryption;
- How to avoid ransomware in the future.
How to Identify Your Ransomware Infection
There are a few ways to identify what type of ransomware you have been infected with to find the right ransomware decryption tool.
The first way is to look at the extension of the encrypted files. This will usually be something like .locked, .encrypt, or. ransom. If you see one of these extensions, you will likely be infected with ransomware.
Another way to identify the type of ransomware is to look at the ransom note. Again, this will give you a clue as to which type of ransomware you are dealing with.
Oftentimes, the ransom note provides details about the type of ransomware your files have been encrypted with, but it can happen that you don’t have this information at hand.
Readers have asked us to include a list of ransomware extensions and their associated malware families. Updates to this list are available on our blog page.
If you find yourself looking for a ransomware decryption tool, two options could help you out:
How to Decrypt Encrypted Files without Paying the Ransom
If you’re infected with ransomware, there are a few tips you can use to make sure you get back on track quickly. As soon as you detect a ransomware infection, you must act fast.
First, note that only some tools can fix what every variant does. In addition, the tools are designed for a specific type of ransomware, so it’s up to you to identify what ransomware variant caused your infection. Once identified, the right tool will be able to decrypt your files.
Second, before sterilizing and decrypting your system and files, make sure to remove the original file or the ransomware itself. Otherwise, the data will still be encrypted again once you finish the recovery process.
Most decryptors can unlock a variety of ransomware, including WannaCry, Petya, NotPetya, TeslaCrypt, DarkSide, REvil, Alcatraz Locker, Apocalypse, BadBlock, Bart, BTCWare, EncrypTile, and Globe.
Unfortunately, ransomware developers quickly push the latest updates and patches to make their malware harder to decrypt. This arms race is why most decryptors don’t come with guarantees because they have to update and adapt theirs.
Below we’ll list some free ransomware decryption tools that will help you unlock your encrypted files.
The Growing List of Ransomware Decryption Tools
Disclaimer:
There are currently many free ransomware decryption tools for some of the most common types. However, the list below is incomplete and will probably never be as more ransomware decryption tools emerge as we speak. So it would help if you documented research as well. Safely decrypting your data can be nerve-wracking, so try to be as thorough as possible.
If you’ve got a suggestion for us or something’s missing from the list, we’ll be happy to hear from you. Just submit your requests, and we’ll get back to you with an answer as to whether or not it will be included in our blog post.
Some of the ransomware decryption tools mentioned below are easy to use, while others require a bit more tech knowledge to decipher. If you don’t have technical skills, you can always ask for help on one of these malware removal forums, which feature tons of information and helpful communities.
Below we’ll show you the top 10 ransomware decryption tools, each with a specific description:
1. 777 ransomware decrypting tool
If you find yourself in a situation where your files have been encrypted and renamed to *.777, don’t panic! We have the solution you need to regain control over your valuable data. The 777 decrypter tool is explicitly designed to tackle these encryption challenges head-on.
This tool is meticulously crafted to unravel even the most complex encryption algorithms, providing you with a ray of hope to recover your cherished files. The process is straightforward, but selecting the appropriate version of the malware from the options tab is essential to ensure seamless functionality.
2. 7even-HONE$T decrypting tool
When 7ev3n-HONE$T encrypts your data, it will rename your files with the.R5A extension to consecutive numbers. For example, the files in a folder might be called 1.R5A, 2.R5A, 3.R5A, and so on. 7ev3n-HONE$T will add the encrypted file’s name to the C: UsersPublicfiles file.
Once your data has been encrypted, it will connect to the Command & Control server and upload a variety of facts and statistics. The data sent includes:
- Your given bitcoin address.
- The total number of encrypted files.
- The number of each sort of file extension.
- Your unique ID.
Use this decrypter if your files have been encrypted and renamed *.777. For the decrypter to function effectively, it may be required to pick the correct malware version on the settings tab.
3. 8lock8 ransomware decrypting tool + explanations
A new ransomware variant based on HiddenTear has been discovered, encrypting files with AES-256 and appending “.8lock8” to encrypted files, for example, “file.jpg.8lock8.” The file “READ_IT.txt” is added to the desktop and the root of each accessed drive. Encrypting files requires traversing all drive letters. The good news is that this malware can be unlocked.
To decrypt, first, obtain the key with my HiddenTear Bruteforcer. This requires a PNG file that has been encrypted (*.png.8lock8); the smaller the file, the better. Load the encrypted PNG file, then click the “EightLockEight” button at the bottom. Then, press the “Start Bruteforce” button.
4. 7ev3n decrypting tool
7ev3n ransomware infiltrates PCs through malicious e-mail attachments, peer-to-peer networks, and bogus software upgrades. Following system infection, 7ev3n encrypts computer files and appends the.r5a (or.r4a) extension to compromised files. A pop-up notification with encryption information is presented when files are successfully encrypted.
A ransom is requested in exchange for a private key that can be used to decrypt the files. If the ransom is not paid within the specified time range, the private key is destroyed, and all data are permanently encrypted.
7even-HONE$T ransomware decryptor restores the original file name
retrieves R4A file content if feasible, recovers R5A file content (requires other settings, which are detailed further)
For R5A, You must prepare additional parameters (A or B) depending on the variety that attacked you:
A. The path to the directory where the file was placed when encrypted.
B. A unique ID, as specified in your ransom note.
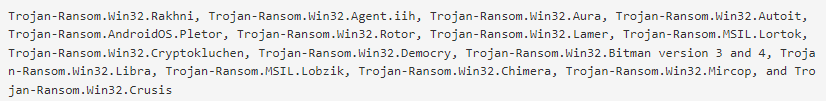
5. AES_NI Rakhni decryptor tool
Kaspersky Labs developed RakhniDecryptor, a general-purpose ransomware decryptor. Instead of creating a separate decryptor for each ransomware outbreak, they created a single decryptor that can handle a wide range of ransomware families. RakhniDecryptor can now decrypt the following ransomware families:
BleepingComputer
To decrypt files, first download RakhniDecryptor.zip and unzip the contents.
- Open the extracted files folder.
- RakhniDecryptor.exe should be launched.
- If you agree to all of the conditions of the License Agreement, click Accept.
- Change the parameters by clicking the link.
6. Alcatraz ransom decryptor tool
Avast Ransomware Decryption Tools includes all 31 accessible Avast ransomware decryptors. The Alcatraz Locker ransomware, which employs AES 256 encryption and Base64 encoding, can be removed using Avast Decryption Tool for Alcatraz Locker.
The “.Alcatraz” extension will be used for encrypted files.
A similar notice occurs after encrypting your data (stored on the user’s desktop in the file “ransomed.html”). All decryptors can be found here.
7. Alma ransomware decryption tool
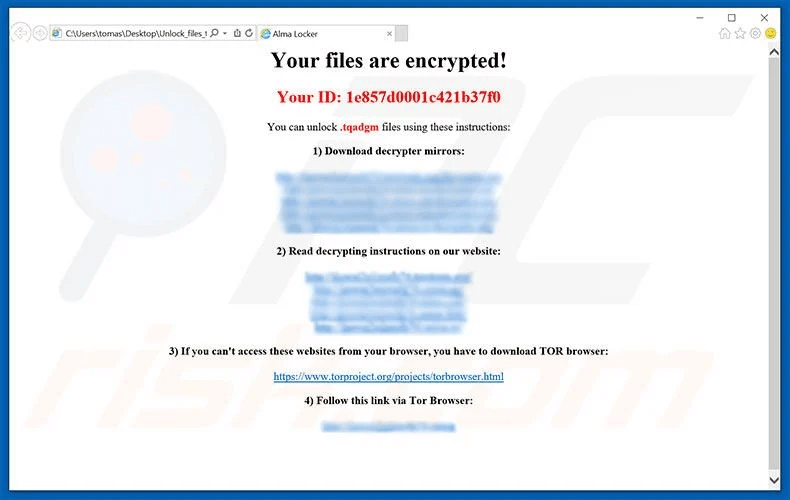
Alma Locker is a dangerous malware that encrypts files with AES-128 encryption. The name of each encrypted file is appended with six random characters by this virus (for example, “sample.jpg” may be renamed “sample.jpg.tqadgm”). As a result, determining whether files are encrypted is simple.
Following successful encryption, Alma Locker creates two ransom-demand files titled “Unlock_files_(6 random characters).html” and “Unlock_files_(6 random characters).txt” and saves them to the desktop as well as each folder containing the encrypted files.
Both files contain text informing victims about the highly similar encryption. Victims are given a private ID and many Tor network connections to download Alma Locker’s decryptor. These files also provide links to Alma Locker’s websites offering payment instructions.
Here’s an example of a message asking users to contact the Alma Locker ransomware developers in order to decrypt their affected data:
PCRisk
Download your files/apps from reputable sources (official download websites) and use a direct download link – third-party download tools frequently include malicious applications. It is also critical to use a legitimate anti-virus/anti-spyware suite.
Remember that cyber criminals frequently use software bugs/flaws to enter systems, so make sure your installed apps are up to date. We also strongly advise you to keep regular backups of your data. Caution is the cornerstone of computer security.
8. Al-Namrood decrypting tool
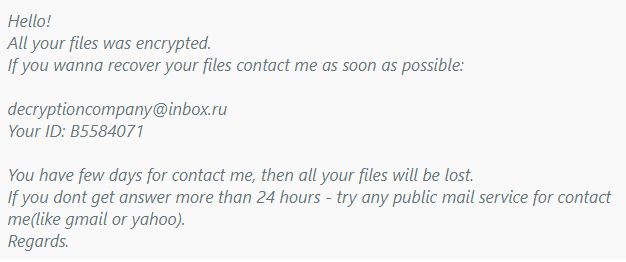
Al-Namrood is a variant of the Apocalypse ransomware. It is typically used to attack servers that have remote desktop services enabled.
Encrypted files are renamed *.unavailable or *.disappeared, and a ransom letter with the name * is written for each file.Read_Me.Txt. The ransomware instructs the victim to contact “decryptioncompany@inbox.ru” or “fabianwosar@inbox.ru.”
Here’s an example:
Emisoft
The decrypter requires your ID to decrypt your files. The ID can be changed under the “Options” tab. By default, the decrypter will set the ID to the system’s ID on which it is running. However, if it is not the same machine where the malware infection and encryption occurred, provide the ID specified in the ransom note.
9. Amnesia ransom decryptor tool
Amnesia is a ransomware tool built in Delphi that encrypts your files with the AES-256 encryption technique. Encrypted files are renamed *.amnesia, and a ransom note with the title “HOW TO RECOVER ENCRYPTED FILES.TXT” instructs you to contact “s1an1er111@protonmail.com.” It is located on your desktop.
The following text appears on the ransom note:
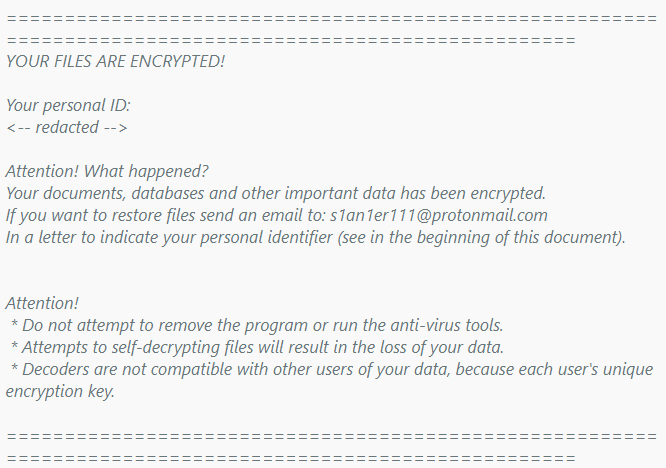
Emisoft
You will need an encrypted file and an unencrypted version to utilize the decryptor. Drag and drop the encrypted and unencrypted files into the decrypter executable to launch the decrypter.
10. Anabelle ransom decryptor tool
ANNABELLE is a ransomware-type malware found by Bart that infiltrates the system and encrypts most saved files. During encryption, this malware appends the “.ANNABELLE” extension to filenames (for example, “sample.jpg” becomes “sample.jpg.ANNABELLE”).
Using files becomes difficult beyond this point. According to research findings, after successfully encrypting files, ANNABELLE undertakes a variety of duties to corrupt the system and, after rebooting, locks the entire screen.
Here’s an example of ANNABELLE ransomware-encrypted files:
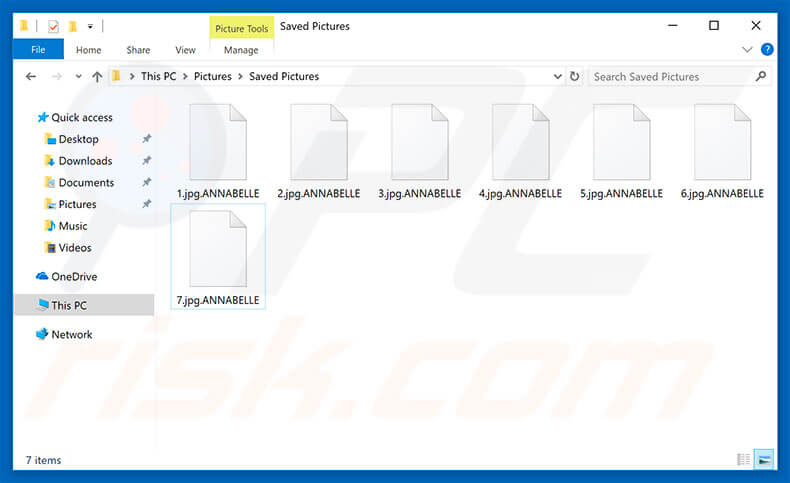
PCRisk
You can decrypt your files with the Bitdefender Anabelle decryptor program. We strongly advise you to also pick “Backup files” before beginning the decryption process, in case something goes wrong during decrypting. Then press the “Scan” button. Here’s a step-by-step guide for decrypting Anabelle ransomware.
- Apocalypse decrypting tool
- ApocalypseVM decrypting tool+ alternative
- AtomSilo ransom decryptor tool
- Aura decrypting tool (decrypted by the Rakhni Decryptor)
- Aurora ransom decryptor tool + alternative
- AutoIt ransom decrypting tool (decrypted by the Rannoh Decryptor) + alternative 1 (decrypted by Rakhni Decryptor)
- Autolocky decrypting tool
- Avaddon ransom decryption tool
- Avest ransom decryption tool
- Babuk ransomware decryptor
- Badblock decrypting tool+ alternative 1
- BarRax Ransom decryption tool
- Bart decrypting tool
- BigBobRoss decrypting tool
- BitCryptor decrypting tool
- Bitman ransomware versions 2 & 3 (decrypted by the Rakhni Decryptor)
- BitStak decrypting tool
- BTCWare ransom decryptor
- Cerber V1 ransomware decryption tool + alternative
- Chimera decrypting tool+ alternative 1+ alternative 2
- CheckMail7 ransomware decryption tool
- ChernoLocker ransom decryption tool
- CoinVault ransom decrypting tool
- Cry128 decrypting tool
- Cry9 Ransom decrypting tool
- Cryakl decrypting tool (decrypted by the Rannoh Decryptor)
- Crybola decrypting tool (decrypted by the Rannoh Decryptor)
- CrypBoss ransomware decrypting tool
- CryCryptor ransomware decrypting tool
- Crypren ransomware decrypting tool
- Crypt32 ransom decryptor
- Crypt38 ransomware decrypting tool
- Crypt888 (see also Mircop) decrypting tool
- CryptInfinite decrypting tool
- CryptoDefense decrypting tool
- CryptFile2 decrypting tool (decrypted by the CryptoMix Decryptor)
- CryptoHost (a.k.a. Manamecrypt) decrypting tool
- Cryptokluchen decrypting tool (decrypted by the Rakhni Decryptor)
- Cryptolocker ransomware decryption tool
- CryptoMix Ransom decrypting tool + offline alternative
- CryptON decryption tool
- CryptoTorLocker decrypting tool
- CryptXXX Ransom decryptor (V1, V2, V3) (decrypted by Rannoh Decryptor) + alternative (V1, V2, V3, V4, V5)
- CrySIS ransomware decryption tool (decrypted by the Rakhni Decryptor – additional details)
- CTB-LockerWeb decrypting tool
- CuteRansomware decrypting tool(decrypted by the my-Little-Ransomware Decryptor)
- Cyborg ransomware decryption tool
- Damage ransom decrypting tool
- Darkside ransomware decryption tool
- DemoTool decrypting tool
- DeCrypt Protect decrypting tool
- Democry decrypting tool (decrypted by the Rakhni Decryptor)
- Derialock ransom decryptor tool
- Dharma ransomware decrypt tool (decrypted by Rakhni Decryptor) (.wallet extension ransomware decrypt tool)
- Diavol ransomware decryption tool + guide
- DMA Locker decrypting tool+ DMA2 Locker decoding tool
- DragonCyber ransomware decryption tool
- DXXD ransomware decryption tool
- Egregor ransomware decryption tool
- Encryptile decrypting tool
- ElvisPresley ransomware decryption tool (decrypted by the Jigsaw Decryptor)
- Everbe Ransomware decrypting tool
- Fabiansomware decrypting tool
- FenixLocker – decrypting tool
- FilesLocker (V1 and V2) decrypting tool
- FindZip decrypting tool
- FortuneCrypt decrypting tool (decrypted by the Rakhni Decryptor)
- Fonix ransomware decryption tool
- Fury decrypting tool (decrypted by the Rannoh Decryptor)
- GalactiCryper ransom decryptor
- GandCrab ransomware decryption tool (V1, V4, V5) + gandcrab 5.2 ransomware decryption tool
- Gerosan ransomware decrypt tool
- GetCrypt decryption tool
- GhostCrypt decrypting tool
- Globe / Purge decrypting tool+ alternative
- Globe2 decryption tool
- Globe3 decryption tool
- GlobeImpostor decryption tool
- Gomasom decrypting tool
- GoGoogle decryption tool
- Hacked decrypting tool
- Hakbit decryptor
- Harasom decrypting tool
- HydraCrypt decrypting tool
- HiddenTear decrypting tool
- HildraCrypt decryptor
- HKCrypt ransom decryptor
- Iams00rry decryptor
- InsaneCrypt ransomware decryptor
- Iwanttits ransomware decryptor
- Jaff decrypter tool
- JavaLocker decryptor
- Jigsaw decrypting tool+ alternative 1 + alternative 2 + alternative 3
- JS WORM 2.0 decryptor
- JS WORM 4.0 decryptor
- Judge ransomware decryptor
- KeRanger decrypting tool
- KeyBTC decrypting tool
- KimcilWare decrypting tool
- KokoKrypt decryptor
- Lamer decrypting tool (decrypted by the Rakhni Decryptor)
- LambdaLocker decryption tool
- LeChiffre decrypting tool+ alternative
- Legion decrypting tool
- Linux.Encoder decrypting tool
- Linux.Encoder.3 ransom decryption tool
- Lobzik decrypting tool(decrypted by the Rakhni Decryptor)
- LockFile ransomware decryptor tool
- Lock Screen ransomware decrypting tool
- Locker decrypting tool
- Loocipher decryptor
- Lorenz ransomware decryptor
- Lortok decrypting tool (decrypted by the Rakhni Decryptor)
- MacRansom decrypting tool
- Magniber decryptor
- MaMoCrypt ransomware decryption tool
- Mapo ransomware decryptor
- Marlboro ransom decryption tool
- MarsJoke decryption tool
- Manamecrypt decrypting tool (a.k.a. CryptoHost)
- Maze ransomware decryption tool
- MegaLocker ransomware decrypting tool
- Merry Christmas / MRCR decryptor + alternative
- Mira ransom decryptor
- Mircop decrypting tool+ alternative
- Mole decryptor tool
- MoneroPay ransomware decrypting tool
- muhstik ransomware decryptor
- my-Little-Ransomware decrypting tool
- Nanolocker decrypting tool
- Nemty ransomware decryptor
- Nemucod decrypting tool + alternative
- NemucodAES ransom decryption tool
- NMoreira ransomware decryption tool
- Noobcrypt decryption tool
- ODCODC decrypting tool
- OpenToYou decryption tools
- Operation Global III Ransomware decrypting tool
- Ouroboros ransomware decryptor
- Ozozalocker ransomware decryptor
- Paradise ransomware decryptor
- PClock decrypting tool
- Petya ransomware decryption tool+ alternative
- PewCrypt ransom decryptor
- Philadelphia decrypting tool
- PizzaCrypts decrypting tool
- Planetary ransomware decrypting tool
- Pletor decrypting tool (decrypted by the Rakhni Decryptor)
- Polyglot decrypting tool (decrypted by the Rannoh Decryptor)
- Pompous decrypting tool
- PowerWare / PoshCoder decrypting tool
- Popcorn ransom decrypting tool
- Professeur ransomware decryptor (decrypted by the Jigsaw Decryptor)
- Puma ransomware decryption tool
- PyLocky ransomware decrypting tool + alternative
- Radamant decrypting tool
- RAGNAROK decrypting tool
- Rakhni decrypting tool
- Rannoh decrypting tool
- Ransomwared decryptor
- Rector decrypting tool
- RedRum ransomware decryptor
- REvil/Sodinokibi ransomware decrypt tool
- Rotor decrypting tool (decrypted by the Rakhni Decryptor)
- Scraper decrypting tool
- Sekhmet ransomware decryption tool
- SimpleLocker ransomware decryptor
- Simplocker ransomware decryptor
- Shade / Troldesh ransomware decryption tool + alternative + alternative 2
- SNSLocker decrypting tool
- SpartCrypt decryptor
- Stampadodecrypting tool + alternative
- STOP Djvu ransomware decrypt tool
- SynAck ransom decryptor
- Syrk ransomware decryptor
- SZFlocker decrypting tool
- Teamxrat / Xpan decryption tool
- TeleCrypt decrypting tool (additional details)
- TeslaCrypt decrypting tool+ alternative 1 + alternative 2
- TeslaCrypt V2 ransom decryption tool + alternative
- TeslaCrypt V3 ransom decryption tool + alternative 1 + alternative 2 + alternative 3
- TeslaCrypt V4 ransom decryption tool + alternative 1 + alternative 2 + alternative 3
- Thanatos decryption tool
- ThunderX decryptor
- Trustezeb.A decryptor
- TurkStatic decryptor
- TorrentLocker decrypting tool
- Umbrecrypt decrypting tool
- VCRYPTOR decryptor
- WannaCry ransomware decryption tool+ Guide
- WannaCryFake Ransom decryption tool
- WannaRen decryption tool
- Wildfire decrypting tool + alternative 1 + alternative 2
- XData Ransom decryption tool (decrypted by Rakhni Decryptor)
- XORBAT decrypting tool
- XORIST decrypting tool+ alternative
- Yatron decrypting tool (decrypted by the Rakhni Decryptor)
- ZeroFucks decryptor
- Zeta decrypting tool (decrypted by the CryptoMix Decryptor)
- Ziggy ransomware decryptor
- Zorab ransomware decryptor
- ZQ ransomware decryptor
Decryption tool for Muse, DarkRace and DoNex Released
This is a decryptor tool specifically designed for the DoNex ransomware and its predecessors. Here are the key details about this decryptor:
The first step is download the hyperlink.
Then, run the executable file, preferably with administrator privileges. To make things easier, follow a wizard-style setup to configure the decryption process.
- Now, here are the steps for using the decryptor:
- Start by selecting the list of locations (drives, folders, files) that need decryption.
- Provide a pair of files: one in its original form and one encrypted by the ransomware.
- Initiate the password cracking process, which is designed to be quick but requires substantial system memory.
- Opt to back up the encrypted files before starting the decryption, which is recommended as a safety measure.
- Complete the decryption by letting the tool decrypt all affected files.
The decryptor supports all brands of the DoNex ransomware, including Muse, Fake LockBit 3.0, DarkRace, and DoNex itself, and it works by exploiting a flaw in the ransomware’s cryptographic schema revealed at Recon 2024.
Ransomware Families Vs. Ransomware Decryption Tools
As you may have noticed, some of these ransomware decryptors work for multiple ransomware families, while certain strains have more than one solution (although this is rarely the case).
From a practical perspective, some decryptors are easy to use, but some require technical know-how. So as much as we’d want this process to be more straightforward, it doesn’t always happen.
No matter how much work and time researchers put into reverse engineering cryptoware, the truth is that we’ll never have a solution to all of these infections. It would take an army of cybersecurity specialists working around the clock to get something like this done.
Seven Best Ransomware Decryption Tools to Use
So now that we have a thorough list of ransomware decryption tools, we’ve narrowed it down to seven of the finest. Each one of them will get an in-depth review of their features.
1. No More Ransomware Project
The software’s primary goal is to protect users against ransomware attacks. It has over 100 encryption keys, which serve as defense mechanisms, so it’s effective at detecting and eliminating the many different kinds of files that may be encrypted.
Experts from law enforcement agencies and cybersecurity companies have come together to eradicate ransomware. In fact, this project has become a valuable resource for anyone affected by ransomware.
Key features:
- It includes decryption keys for more than one hundred ransomware types discovered just in the last year.
- There are detailed instructions for decrypting files that have been encrypted by ransomware.
- It informs users about ransomware infections and the countermeasures available to them.
- New ransomware decryption keys are regularly added to the website and regularly updated.
- Includes a special box for reporting criminal activity, including ransomware.
- The service is available in over 25 different languages.
2. Trend Micro Ransomware File Decryptor
It’s a relatively new software designed to prevent malware from getting into your system. Additionally, the ransomware decryption tool can operate on systems that have been infected and assist you in successfully unlocking a file that Virus has locked.
In addition, Trend Micro Ransom File Decryptor is an easy-to-use program that is light on data usage. Despite all this, Trend Micro has helped to win against ransomware in the past. Its decrypting tool will keep you safe and won’t impact your phone’s performance.
Key features:
- Each decryption utility has been combined into a single application.
- It includes decryption keys for more than 25 different types of ransomware.
- Trend Micro’s website contains information that can help determine the type of ransomware.
- New ransomware signatures will be added to the tool as it receives updates as new threats emerge.
- Trend Micro has a dedicated support line for victims of ransomware.
3. Emsisoft Ransomware Decryption Tool
It is widely considered to be among the best ransomware decryption programs that can be installed on Windows. A vital tool like this has never failed to restore access to files encrypted by major ransomware like Apocalypse, Xorist, Stampado, and BadBlock.
Key features:
- Emsisoft provides over sixty decryption tools to combat a wide range of ransomware strains.
- Analyzing the encrypted file helps to determine the type of ransomware present.
- It provides step-by-step instructions for decrypting ransomware-encrypted files and recovering your data.
- Existing decryption tools are frequently updated with new functionality.
4. McAfee Ransomware Recover
McAfee Ransomware Recover is another excellent decryption tool that you can use to recover your encrypted files. Files, software, databases, and other files affected by ransomware can be retrieved with the help of McAfee Ransomware Recover.
In addition, regular updates are made available for the tool that contains additional decrypting keys so you can always have access to them.
Key features:
- In the field of computer security, McAfee is something of a warhorse. For example, they are actively developing decryption tools in response to the constant emergence of new ransomware attacks.
- McAfee Ransomware Recover, also known as Mr2, is a highly sophisticated decryption software.
- It can unlock a user’s files, apps, databases, and applets, among other things.
- Their decryption architecture may be modified and improved upon by anyone in the security community, and it is publicly available.
- It provides extensive information on ransomware.
5. AVG Ransomware Decryption Tool
AVG Ransomware Decryption Tools can be a good option for ransomware that encrypts files using different algorithms. On the other hand, it can only decode files encrypted by Apocalypse, Bart, Crypt888, Legion, or TeslaCrypt.
Key features:
- The antivirus software’s user interface is streamlined and uncomplicated, including all automatic features that save you time.
- It protects its users from threats that can be downloaded as well as links that may be malicious.
- It is possible to perform a remote computer scan using AVG Antivirus on your mobile device.
6. 360 Ransomware
You can remove ransomware from your PC without having to pay the ransom by using a tool developed by the folks at 360 Ransomware Decryption Tool. This was created to help people remove Petya; however, it can also retrieve the decryption key for other types of ransomware.
Key features:
- A single piece of software comes packaged with several different decryption keys.
- It offers decryption services for a wide range of new specialized ransomware.
- Their website contains several useful ransomware resources.
- It’s a ransomware removal program that’s simple to operate.
7. Quick Heal – Free Ransomware Decryption Tool
Once you authorize your computer to be scanned, Quickheal can eradicate the infection quickly and efficiently while keeping your documents safe as ransom.
Quickheal has software that boots to scan for infected files and removes them before the Operating System kicks in. The software is supposed to be installed on a flash drive and then booted off. If it detects ransomware, Quickheal will remove it automatically.
Key features:
- A single tool bundled with multiple decryption keys.
- It provides decryption for some of the more unusual ransomware out there.
- Their website contains valuable ransomware information.
- It’s a simple ransomware removal tool.
How to Avoid Ransomware in the Future
One of the most efficient ways to prevent the threat of ransomware from wreaking havoc and locking your sensitive data is to remain vigilant and be proactive.
In fact, we strongly recommend you to apply these basic and simple steps we outlined in the anti-ransomware security plan, that can help you prevent this type of cyber attack.
Safely keeping copies of vital information offline and equipping your company with cyber-insurance should be included in your enterprise’s cybersecurity strategy. Even if cybercriminals get access to your computers and infect them with ransomware, you can wipe the system clean and restore your latest backup. Of course, this won’t solve the double extortion ransomware situation but at least you can restore your systems to a working state. So, please, do not postpone the process of doing a secure backup of your data.
As new types of ransomware emerge, researchers decrypt some strains, but others get new variants, and it may look like a cat and mouse game, in which proactivity is vital. Paying the ransom never guarantees you actually get your data back, as it might still end up for sale on the Dark Web.
Therefore, prevention remains the best medicine as always.
How Heimdal can Protect your Business from Ransomware
Heimdal offers a comprehensive suite of cybersecurity products that cover various aspects of cyber protection, such as endpoint security, network security, email security, access management, patch management, threat hunting, and more. A flexible and comprehensive method for modern cybersecurity that can work as independent modules to improve and fortify your current security configuration or combined in an XDR platform.

- End-to-end consolidated cybersecurity;
- Complete visibility across your entire IT infrastructure;
- Faster and more accurate threat detection and response;
- Efficient one-click automated and assisted actioning
Check out our YouTube video series that delves deep into ransomware fundamentals, providing invaluable insights into the inner workings of these malicious threats and covering everything from prevention strategies to understanding encryption algorithms.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










