Contents:
This ongoing ransomware campaign packs a big punch against its victims, aiming for a high success rate in terms of infected systems.
Using a malware cocktail to drive infection rates
The cybercriminals behind the campaign are compromising legitimate websites by injecting malicious scripts. The injects then redirect the victims’ Internet traffic to a Cerber gateway which is known as Pseudo Darkleech (more on this below). The latter is a type of malware infection created to add a strong obfuscation layer and keep detection rates low.
The malicious script injected into these websites is the notorious Nemucod, the generic malware downloader used to transfer malicious software onto the victims’ computers.
In this case, Nemucod is used to download and run Cerber ransomware from two main websites in the execution routine (sanitized for your safety):
doomgamesoa [.] Top / read.php? F = 0.dat
http: //www.astrosean [.] Top / admin.php? F = 1.dat
The attackers are exploiting vulnerabilities in Internet Explorer, Microsoft Edge, Flash Player and Silverlight to infect unsuspecting users. The extent of these exploits is still under investigation and we will update the alert as soon as we have more details.
The extortion part of the ransomware attack is centered around the following domains, a few of which are listed below (sanitized for your safety):
fnmi62725zfti2vy.17vj7b [.] top
ftoxmpdipwobp4qy.17vj7b [.] top
pe2cku7pebkpgeko.17vj7b [.] top
avsxrcoq2q5fgrw2.1bpfr1 [.] top
ffoqr3ug7m726zou.1bpfr1 [.] top
fnmi62725zfti2vy.1bpfr1 [.] top
ftoxmpdipwobp4qy.1bpfr1 [.] top
pe2cku7pebkpgeko.1bpfr1 [.] top
avsxrcoq2q5fgrw2.1mstqg [.] top
cerberhhyed5frqa.1mstqg [.] top
ffoqr3ug7m726zou.1mstqg [.] top
fnmi62725zfti2vy.1mstqg [.] top
ftoxmpdipwobp4qy.1mstqg [.] top
In terms of antivirus detection
Here are the printscreens taken when publishing these alerts:
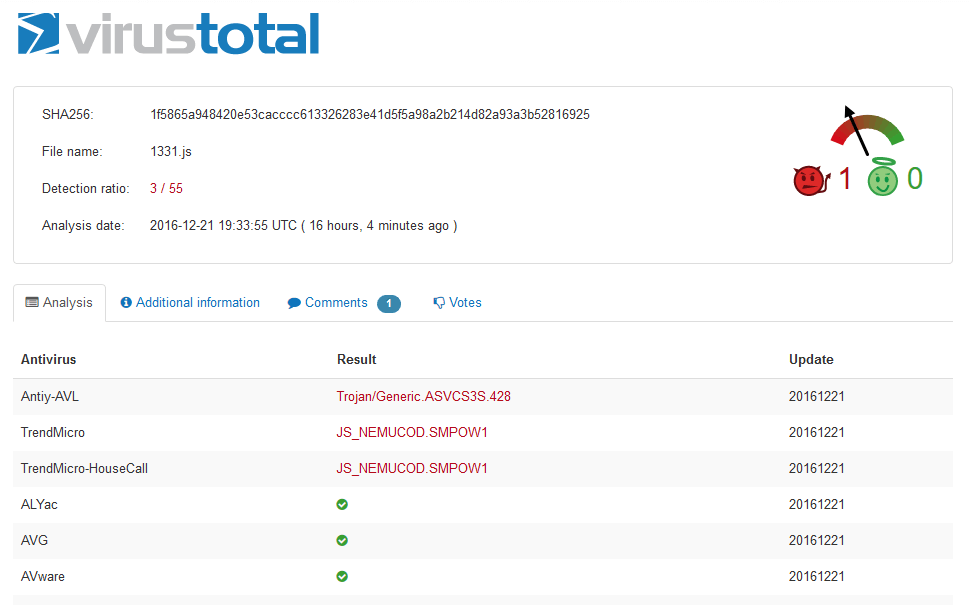
The malicious payload which supplies Cerber has a detection rate of 3/55 on VirusTotal:
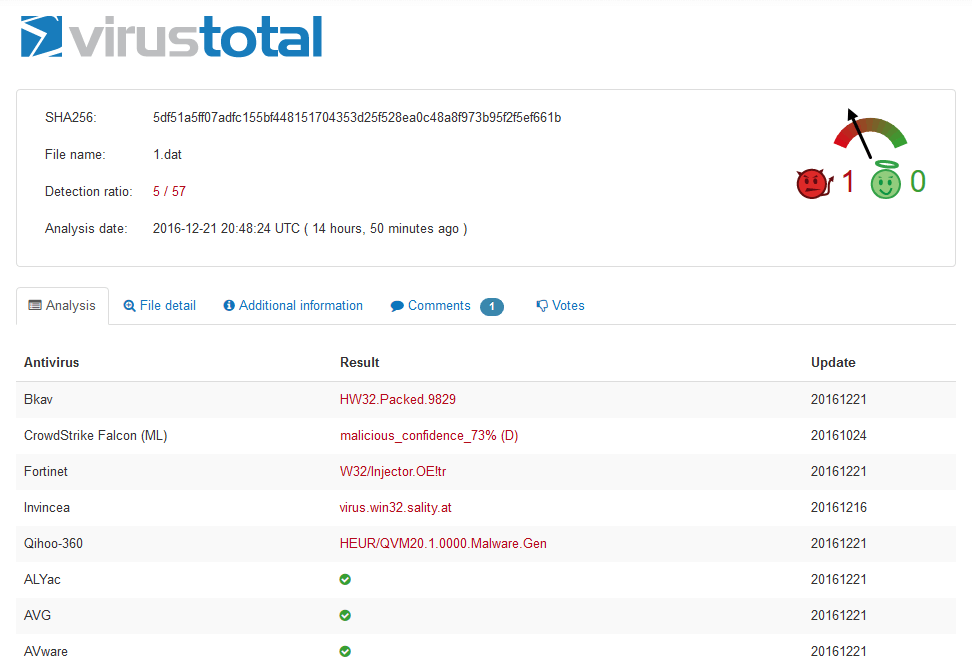
The Cerber code achieves a detection rate of 5/57 on VirusTotal:
Please keep in mind that this ransomware campaign can affect both individual Internet users and companies. What’s more, Cerber has recently started targeting companies’ databases to maximize profits from the ransom, so this is another reason to take additional precautions.
Why attackers combine multiple types of malware
You may wonder why cyber attackers choose to incorporate so many types of malware in a single attack. The answer is that, by packing multiple types of malicious software, they aim to do two things:
- Make the infection stealthy, so it can’t be detected and stopped by antivirus (which is what most people use for protection);
- And to make the infection stick (persistence) until it can encrypt all the victim’s data and get to the point where it can ask for ransom and the victim feels compelled to pay for it.
Second generation malware, such as strong ransomware strains (e.g. Cerber), uses a variety of mechanism to evade antivirus detection. We actually explained some of them in this guide.
These mechanisms are some of the attributes that we often see in advanced cyber attacks, such as the one I just described at the beginning of this alert.
So let’s see what each piece of the puzzle does:
Nemucod
Nemucod first emerged in December 2015 as a Trojan downloader. This cyber threat can download and install other programs (especially malware) on computers without the owner’s consent.
Nemucod can connect to a remote host (as we’ve seen in this alert) and perform a series of actions, including:
- Checking for an Internet connection
- Using that connection to download and run files (this includes other malware as well)
- Reporting infections to the cyber criminal behind the attack
- Receiving data such as configurations, further instructions and more
- Uploading information harvested from the infected computer and other malicious tasks.
This malware downloader recently got a ton of attention when it was used in spam IMs on Facebook Messenger to spread Locky ransomware.
Pseudo DarkLeech
We’ve mentioned Pseudo DarkLeech in a security alert published in September 2016, which involved the RIG exploit kit distributing CrypMIC ransomware (no decryption tool available for it yet).
This type of infection uses hidden iframe injections and randomizes elements to enable the malware to operate covertly. This blogpost by Sucuri Security explains its evolution in detail.
Cerber ransomware
Cerber was discovered in March 2016 and its distinguishing features include the fact that it’s professionally coded and that it provides many customization options. From the first analyses it became clear that this encrypting malware is not the work of amateurs.
Since it first appeared, Cerber has has a significant impact on victims all over the world. In Symantec’s ISTR Special Report: Ransomware and Businesses 2016, the team of researchers mentions that:
Like Locky, Cerber appears to have access to the Dridex spam network, meaning it can be pushed out quickly in large spam campaigns.
Victims whose data is encrypted with Cerber are usually extorted for amounts ranging from 1.24 bitcoins (BTC) to 2.48 BTC ($1,068 to $2,136 according to December 2016 rates).
If you’d like to read more about Cerber, this analysis by MalwareBytes is quite comprehensive.
Together, these 3 elements make for a powerful attack against unsuspecting Internet users.
Core prevention advice
Ransomware is a formidable threat that we’ve written about many times and whose intricacies we tried to unscramble in this dedicated guide.
While more and more decryption tools available for some types of ransomware, the bulk of it remains unbreakable.
To avoid becoming a victim of ransomware, try to follow these 5 steps:
- Keep your software up to date. In the case of this current campaign (as with many others), keeping your software up to date is a great layer of defense. Your browsers and software such as Flash and Java are key targets for cyber criminals. Leaving them outdated creates the security holes that attackers exploit to infect your system. Installing updates will help keep your guard up and not give a chance to ransomware infections.
- Create and maintain at least 2 backups of your data, in different locations (in the cloud + on an external drive). If you do get hit with ransomware or any other type of malware, you’ll be able to just wipe your computer clean and restore your data from a backup. No ransom paid, no further fueling cyber criminals in their malicious activities. This is a must-have plan B!
- Enhance your browser protection. Many cyber attacks nowadays start from your browser and exploit vulnerabilities in it. If you don’t know where to start, you can check out our guide on the topic.
- Use a reliable antivirus. It may not be able to catch every threat out there, but, to be honest, no security product can. That’s why you need multiple layers. Choose a sturdy AV product and use it to its full potential.
- Complement your reactive protection with a proactive security solution. The more security layers you have, the stronger your chances to resist a ransomware infection. This doesn’t mean using multiple AVs (not recommended), but using additional products that complement its functions. You can look for solutions that offer traffic filtering and can block connections to websites and servers that distribute malware, such as the ones involved in this security alert.
If you want to do even more for your protection (which i hope you do), this anti-ransomware protection plan can help guide your actions.
*This article features cyber intelligence provided by CSIS Security Group researchers.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security