Contents:
Heimdal™ Security has detected what appears to be the onset of a phishing campaign targeting C-level executives and, most likely, decision-makers. The recently uncovered phishing attempt employs Zoom’s videoconferencing feature. We would like to remind the reader that Zoom has been the recipient of several cyberattacks, the most recent and significant being the data leak of late April. For the time being, Zoom is the go-to solution for remote work and e-teaching, both contexts being created by the coronavirus pandemic. This phishing attempt, which was signaled to Heimdal™ Security by a tipster, can arguably be part of a larger data-mining operation. On the other hand, it could very well be the work of a single individual, bent on earning easy money.
Analyzing the incident
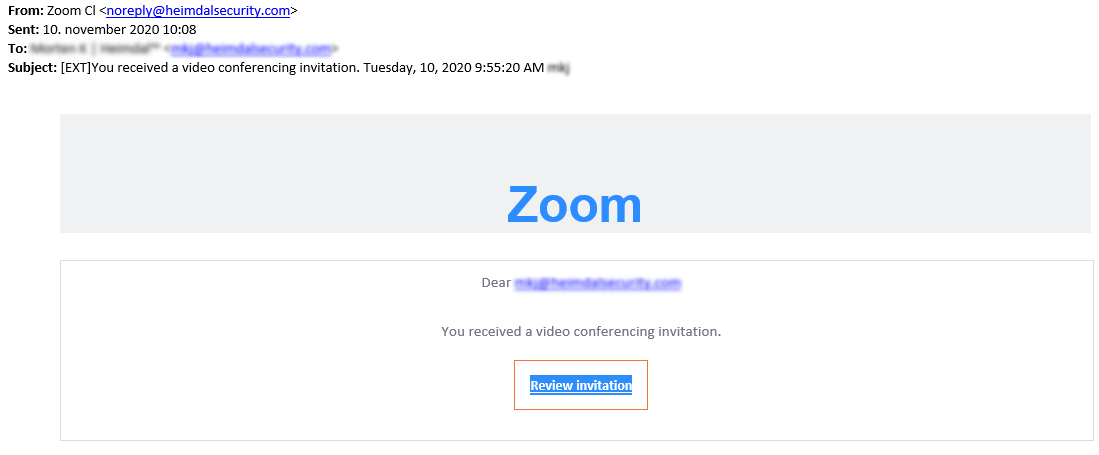
At around 9:00 AM, the victim received an email at his work address in regards to an upcoming conference hosted on Zoom. The email would later be forwarded to one of our company’s representatives. This email contained no details as to the purpose of this impromptu meeting nor the party or parties involved. In cyber-attacks, especially phishing, human psychology plays a pivotal role. Remark the timestamp in the photo below: 9:55:20 AM.
Since in most cases, work starts at 9:00 – 9:30 AM, it would only be natural to assume that between this interval, the employee is preoccupied with getting up to speed with what happened during the off-hours (e.g. checking emails, consulting the meetings calendar, etc.). It goes without saying that the attention span of an average individual is severely impaired during this time and mistakes can occur. In this particular case, the mistake could have been a costly one.
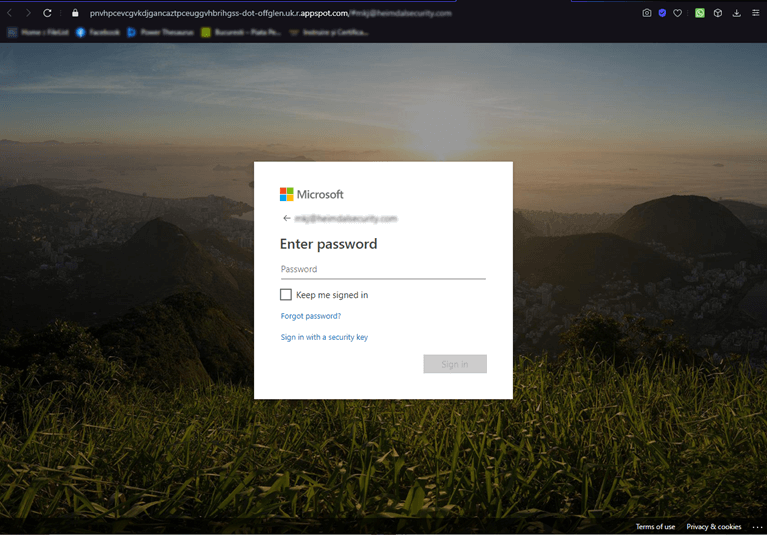
The suspicious email contained a single HTML-embedded “Review invitation” button along with the email address of the recipient. If the victim were to follow the link, the browser would be redirected to Microsoft Account sign-in page, where the user is asked to enter the credentials associated with his MS (i.e. work email address and password).
Usually, when one receives a Zoom invitation, the link embedded in the invitational email should direct the user to the virtual Zoom conference room hosting the specified event. It makes no sense to ask the user to fill in his Microsoft account credentials in order to join the event. Obviously, the login page is doctored. At a glance, it looks like a legitimate Microsoft page – same picture, login forms, and footer. However, the URL paints an entirely different picture.
A normal, unaltered MS login, should look like this: login.microsoftonline.com/<arguments>, whereas the link of this page looks something like this: <string of random letters>-dot-offglen.uk.r.appstop.com/#<email. Please see the picture below for more information.
If the user were to fill in the requested credentials, he would’ve been redirected to an error page, but this is only speculation. At this point, the credentials would have been recorded by the threat actor and used to gain access to the account.
Heimdal™ recognized this as a phishing attempt and has, subsequently, blocked the malicious domain. Efforts are underway to determine if any other subdomain was used to launch similar attacks.
-Update-
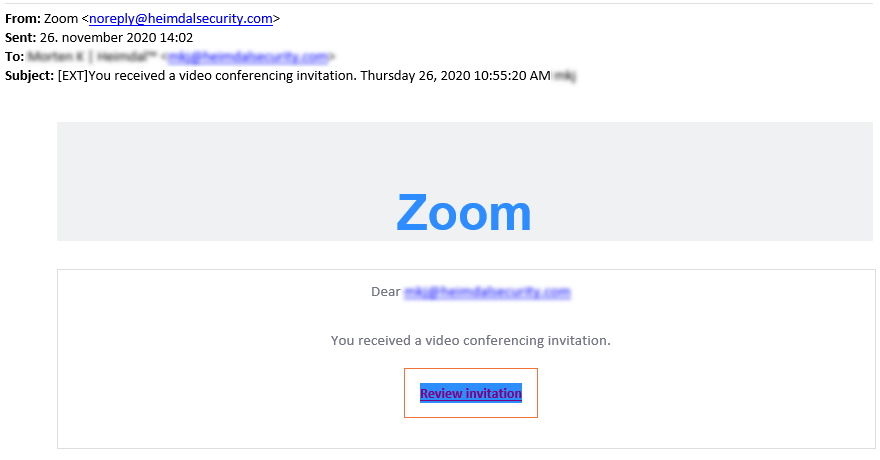
Heimdal™ Security has received yet another phishing attempt from the same source. Baffling enough, the email containing the fake Zoom link points to the same URL which was blocked and sanitized by Heimdal upon the initial note was received. I have included a picture of the latest Zoom phishing attempt.
Protecting your corporate assets from phishing attempts

Heimdal® Email Security
- Completely secure your infrastructure against email-delivered threats;
- Deep content scanning for malicious attachments and links;
- Block Phishing and man-in-the-email attacks;
- Complete email-based reporting for compliance & auditing requirements;
Heimdal™ Security recommends:
- Refrain from clicking on suspicious links. Double-check the email’s body before executing attachments or clicking on links.
- Verify the email for inconsistencies. More than often, phishing links are laden with spelling errors or information that simply doesn’t make any sense (i.e. flashing buttons, ribbons, etc.).
- Establish the meeting’s validity. An easy way to establish the invitation’s authenticity is to communicate with the sender. Ask him or her if the invitation’s valid or not.
- Deploy an email security solution. Modern threat-hunting also incorporates email security technologies. Heimdal™ Email Security uses deep attachment scanning to root out malware hidden in an email attachment or wire fraud attempts.
Conclusion
Singular phishing attempt or the beginning of a massive phishing campaign? Time will tell. As always, practice good cybersecurity habits, keep your applications up to date, and get an extra cup of coffee in the morning before going through your inbox.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security