Contents:
RedAlert is a new ransomware operation also known as (N13V) that encrypts VMWare ESXi servers running either Windows or Linux.
What Happened?
As explained by BleepingComputer the threat actors refer to their operation as “N13V” internally, and developed The Linux encryptor specifically for the purpose of targeting VMware ESXi servers. The ransomware has command-line options that provide threat actors the ability to halt any virtual machines that are active prior to encrypting data.
When the ransomware is executed with the ‘-w’ parameter, the Linux encryptor will use the following esxcli command to force all operating VMware ESXi virtual machines to shut down.
When it comes to encrypting data, the ransomware makes use of the NTRUEncrypt public-key encryption method. This technique supports a variety of ‘Parameter Sets,’ each of which provides a unique degree of protection.
?♂️?
That’s RedAlert… pic.twitter.com/GKTwPO1vBL— MalwareHunterTeam (@malwrhunterteam) July 6, 2022
An intriguing component of RedAlert/N13V is the ‘-x’ command-line option, which carries out ‘asymmetric cryptography performance testing’ by using these various NTRUEncrypt parameter configurations, as it is not obvious if there is a method to compel the use of a certain parameter chosen during encryption or whether the ransomware will choose a more effective one on its own.
When the ransomware encrypts data, it will only target files that are connected with VMware ESXi virtual machines, and will also construct a unique ransom note for each folder, which it will label HOW TO RESTORE. This message will include a description of the material that was taken along with a link to a ransom payment site that is specific to the victim that uses the TOR anonymity network.
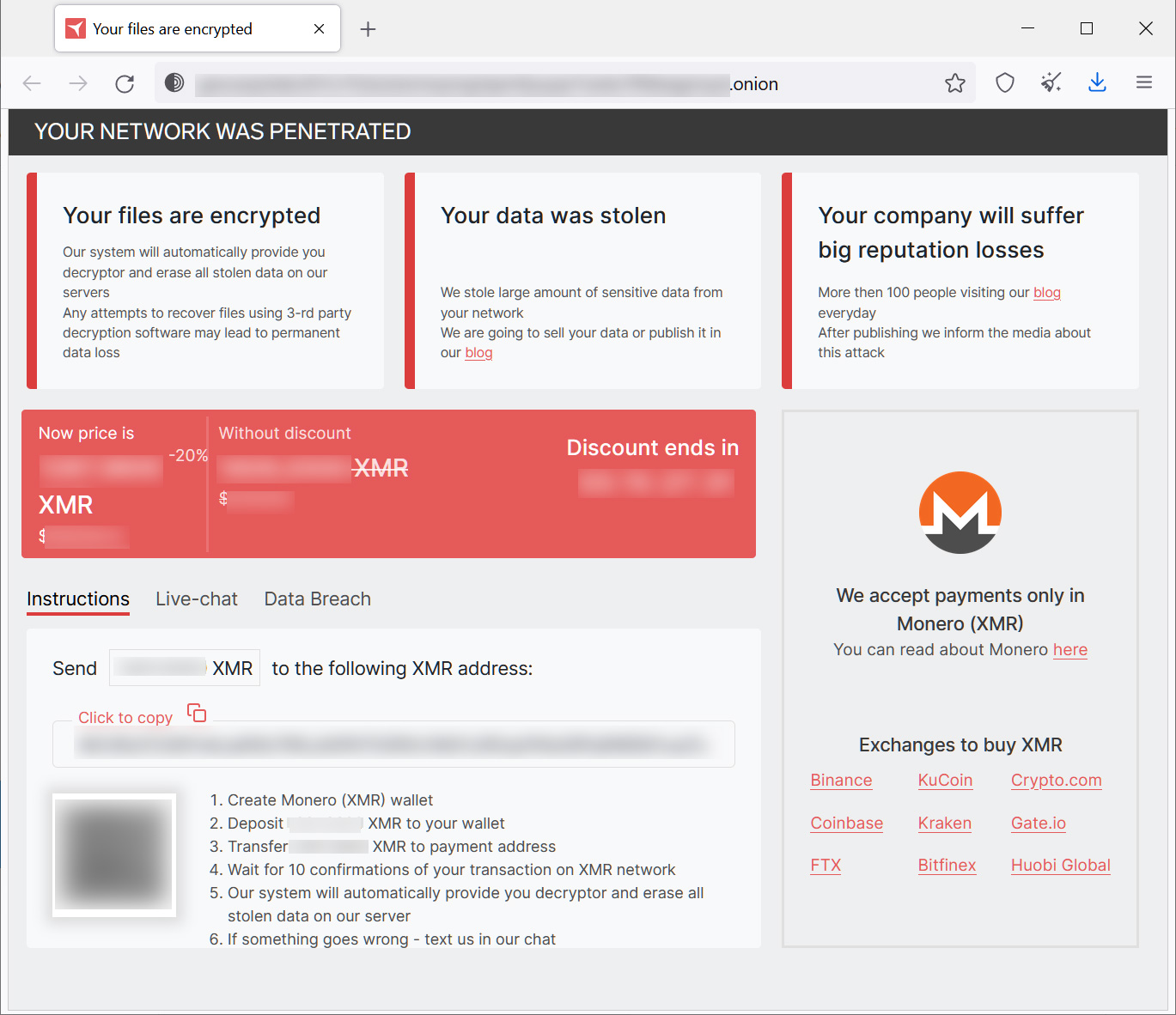
Source
The ransom demand is shown on the Tor payment site, just as it is on other sites used by ransomware operations, and it also gives a chance to bargain with the people responsible for the attack.
However, the only form of payment that RedAlert/N13V would take is the cryptocurrency known as Monero, which is a privacy coin and hence is not widely traded on cryptocurrency exchanges in the United States.
RedAlert performs double-extortion, as these attacks are designed to steal money from victims.
This strategy enables two kinds of extortion, enabling the threat actors to not only demand a ransom to acquire a decryptor but also demand one to prevent the leakage of stolen data. These two demands may be made simultaneously using this methodology.
If a victim does not comply with a ransom demand, the RedAlert gang will post the stolen information on a website known as a data breach, where it will be available for anyone to download.
The fact that the RedAlert data leak site only includes the information pertaining to one business at the moment is evidence that the operation is still in its infancy.
How Can Heimdal Help?
Ransomware is one of the most frequent and deadly cyber dangers that exist today, and it has the potential to be devastating in its repercussions. Learning how to avoid it should be a top priority for any organization that is concerned about the safety of its workers, customers, partners, assets, money, and business processes, among other things.
To combat ransomware, you can benefit from the outstanding integrated cybersecurity suite that includes the Ransomware Encryption Protection module, which is universally compatible with any antivirus solution and is completely signature-free, ensuring superior detection and remediation of any type of ransomware, whether fileless or data-based (including the most recent ones like LockFile).
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










