Contents:
Wondering how does ransomware spread? We’re not surprised.
There is no doubt that cybercriminals are constantly looking for new ways to hold your data hostage.
As a result, ransomware has emerged as one of the most serious cybersecurity threats to businesses in recent years. Because it’s so dangerous, understanding how ransomware spreads it’s the first step to preventing it.
In this article, we’ll discuss how ransomware spreads and split it into two categories: how it spreads over the internet and within your company’s network.
So let’s get right into it!
How Does Ransomware Spread Over the Internet?
In most cases, ransomware is spread through phishing emails containing malicious attachments, portable computers, exposure to public WiFi, Zero-Day vulnerabilities, and drive-by downloading.
Drive-by downloading occurs when a user unknowingly visits an infected website, and then malware is downloaded and installed without their knowledge.
For example, a malware variant known as crypto-ransomware encrypts files and has been spreading through social media platforms such as Web-based instant messaging apps and similar methods.
Additionally, newer methods of ransomware infection have been observed. For example, vulnerable Web servers have been used to gain access to an organization’s network.
Here are 12 common ways ransomware spreads:
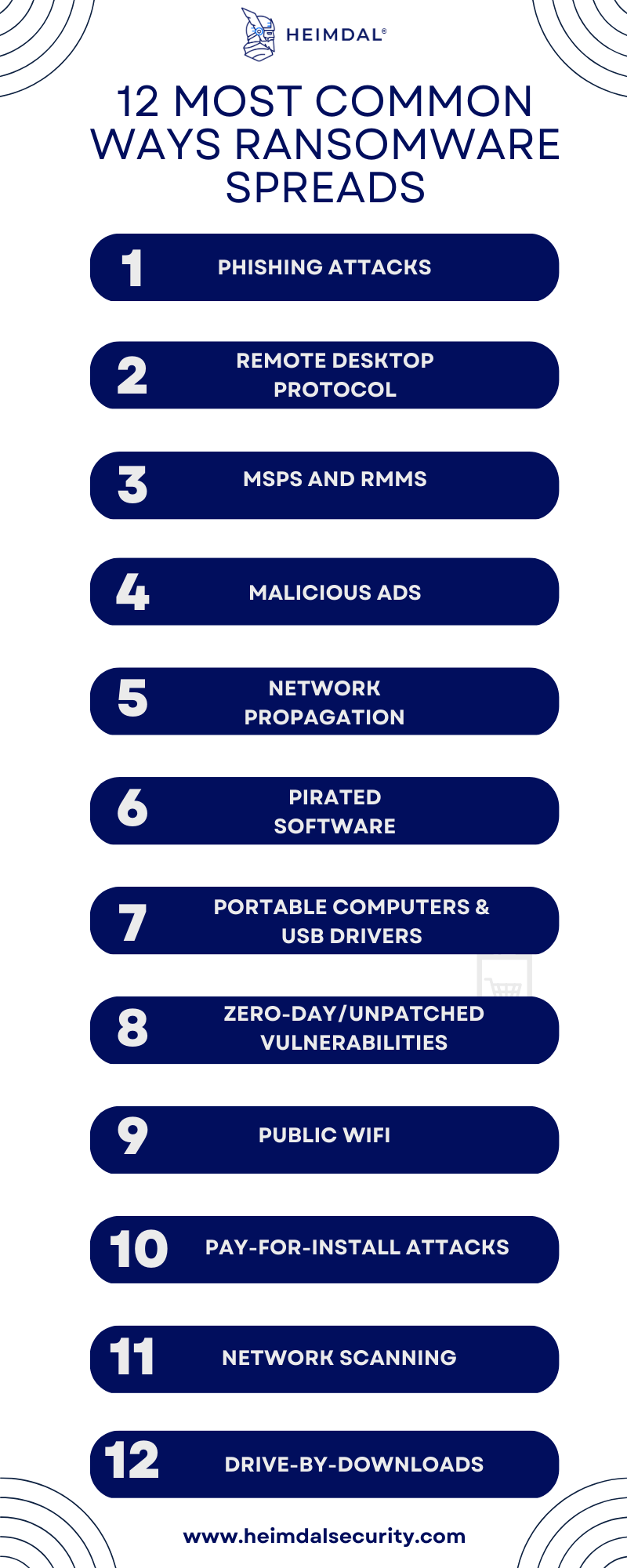
Let’s go through them all one by one, so you can better understand what they mean:
1.Phishing Attacks
In 2020, researchers found that 91% of all cyberattacks begin with phishing and spear phishing emails. Hackers use phishing and spear phishing techniques to plant ransomware into a victim’s computer system.
It is common for hackers to conduct extensive research before sending convincing emails that include dangerous attachments (like ZIP files, PDFs, and spreadsheets) or links to malicious websites. These malicious websites are designed to trick you into installing ransomware that can infect your entire network.
2. Remote Desktop Protocol (RDP)
Remote Desktop Protocol (RDP) is a protocol or technical standard for remotely accessing a desktop computer. RDP, Independent Computing Architecture (ICA), and virtual network computing (VNC) are all protocols that remote desktop software can use, but RDP is the most commonly used.
Microsoft developed RDP, which is available for most Windows operating systems but can also be used with Mac operating systems.
However, ransomware frequently attacks other network nodes via Remote Desktop Protocol (RDP). RDP is a communications protocol that allows you to connect to multiple computers via a network connection, allowing ransomware infection to spread laterally.
3. MSPs and RMMs
RMM is a process that allows managed IT service providers (MSPs) to monitor client endpoints, networks, and computers remotely and proactively. Other names, such as remote IT or network management, are known as RMM.
In supply chain attacks, hackers frequently target managed service providers (MSPs) by exploiting the MSP’s remote monitoring and management (RMM) software.
This attack allows hackers to distribute ransomware to the MSP’s entire customer base, increasing the pressure on the MSP to pay the ransom.
4. Malicious Ads
Malvertising, or malicious advertising, is becoming more popular as a ransomware delivery method.
Hackers buy legitimate internet advertising space and connect it to an exploit kit.
The exploit kit scans your system for information when you click the ad (including your operating system, software, browser details, and more). If a vulnerability is discovered, it will attempt to install ransomware on your computer.
5. Network Propagation
Network propagation in cybersecurity is how malware is inserted into a target network or system, such as an infected USB stick or email carrying a compromised attachment. NP comes with self-propagating mechanisms that allow ransomware infections to spread laterally to other network devices, potentially crippling entire organizations.
It’s important to note that the first few ransomware variants lacked network propagation capabilities, whereas newer variants do. This is because they were restricted to only attacking infected devices. However, ransomware variants are becoming more complex, with self-propagating mechanisms allowing lateral movement to other network-connected devices.
6. Pirated Software
Ransomware can be introduced through pirated software and software bundled with adware. Furthermore, websites hosting pirated software may be more vulnerable to malware or drive-by downloads.
Using pirated software may increase the risk of infection with ransomware. In addition, unlicensed software users may not receive security patches because they do not receive software updates, increasing the risk of zero-day exploitation by hackers.
7. Portable Computers & USB Drivers
Laptops are particularly vulnerable to ransomware attacks, as they are often used for work and storing large amounts of sensitive data.
USB drives are also commonly used to deliver ransomware, as they are easy to transport and can be plugged into multiple computers. Once plugged in, the malware on the USB drive will automatically execute and infect the computer. This can then spread ransomware throughout the network, encrypting all connected devices.
Training your staff on recognizing and preventing potential risks is essential to avoid falling victim to a ransomware attack. For example, they should be aware of the dangers of opening email attachments from unknown sources and never plug in a USB drive from an untrusted source.
8. Zero-Day/Unpatched Vulnerabilities
Zero-day vulnerabilities are unpatched security vulnerabilities that hackers exploit, even paying for access to weaknesses they can use to target your organization.
Zero-day vulnerabilities enable hackers to install ransomware without tricking anyone, making their jobs much more accessible. Performing regular patch management ensures that you’re running the most recently released malware protections and security patches, increasing your safety quotient.
9. Public WiFi
Unfortunately, ransomware often hides in plain sight via public WiFi.
If you have remote workers who frequently access your network in public (hello Starbucks), you must have strict policies to protect your data and network from the dangers of public WiFi.
Consider prohibiting public WiFi usage altogether, providing secure 4G/5G access, or using VPN services if working in public spaces cannot be avoided.
10.Pay-For-Install Attacks
The next time you think you’re safe from your employees, you may want to rethink it. While that might sound harsh, prevention is better than cure.
Cybercriminals have bribed individuals in critical positions through an infected memory stick to install ransomware directly on a computer network. This method bypasses almost any security protocols you’ve implemented. Don’t let employees use USB devices; put it in writing for them to sign off on.
11. Network Scanning
Once attackers identify a vulnerability, they’ll use it to identify other vulnerabilities they can exploit, such as:
- ARP scanning: Mapping physical addresses to logical (IP) addresses;
- Vertical scans: Scanning a single IP for multiple ports;
- Horizontal scans: Scanning various IPs for a single port;
- Box scanning: Both vertical and horizontal scans;
- Port scanning: Scanning to discover a network’s open doors or weak points.
12. Drive-by-Downloads
And last but not least, drive-by-downloads. The most disturbing of all are drive-by downloads, which occur without your knowledge.
There are several ways in which this can occur:
- Viewing a website specifically created to host malicious software;
- Visiting a legitimate website with known vulnerabilities that have been injected with malware;
- Regardless, the malicious content scans your device for vulnerabilities and executes ransomware.
Now that you know how does ransomware spread over the internet, let’s find out how it can spread within your company’s networks too!
How Does Ransomware Spread Within a Company’s Network
Did you know that from January to July 31, 2021, the FBI’s Internet Crime Complaint Center received 2,084 ransomware reports, up 62% over last year?
Moreover, in 2021, ransomware was used to steal critical infrastructure from schools, hospitals, retail businesses, professional services firms, manufacturing companies, and government agencies.
For example, the ransomware attack on Colonial Pipeline disrupted oil flow across the eastern United States. Cybercriminals had also moved from targeting just single organizations to supply chains, such as when remote management software vendor Kaseya was affected by the REvil ransomware, which involved 1,500 companies.
And you’re probably reading this to ensure that your company isn’t next on the ransomware list, right?
So here’s how ransomware spreads within company networks:
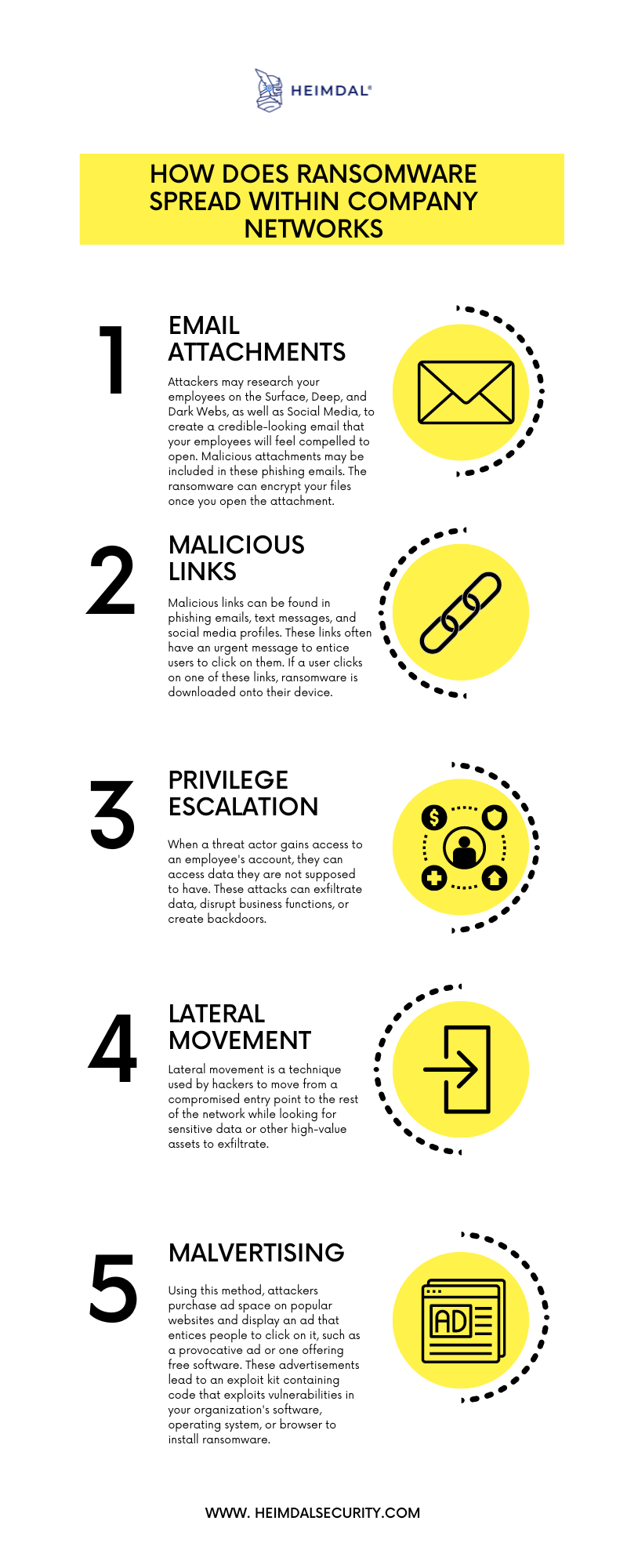
The Lateral Spread of Ransomware
So, what are the steps involved in a typical ransomware attack?
According to postmortem analyses of successful ransomware attacks, poor network segmentation practices were often the most significant security gap that prevented an organization from stopping or containing the attack.
Organizations that have been infected with ransomware may find restoration difficult. Backups are often discovered and encrypted fast, making them an unreliable option for recovery. To maximize the assets they can encrypt, attackers move laterally from the entry point to other places to get credentials with administrator privileges.
This can include a domain controller, an IT professional’s laptop, or plenty of other systems used by privileged users. When ransom demands are issued, the attack is usually rapidly extended to other essential systems; this process can be completed within 24 hours.
Here’s an example of how a user can infect their local computer by clicking on a malicious link. With nothing holding them back, ransomware can be dropped across the environment without restriction. The malware is a jumping-off point for lateral movement toward more sensitive systems.
Here’s an illustration of how a ransomware actually happens without proper network segmentation:
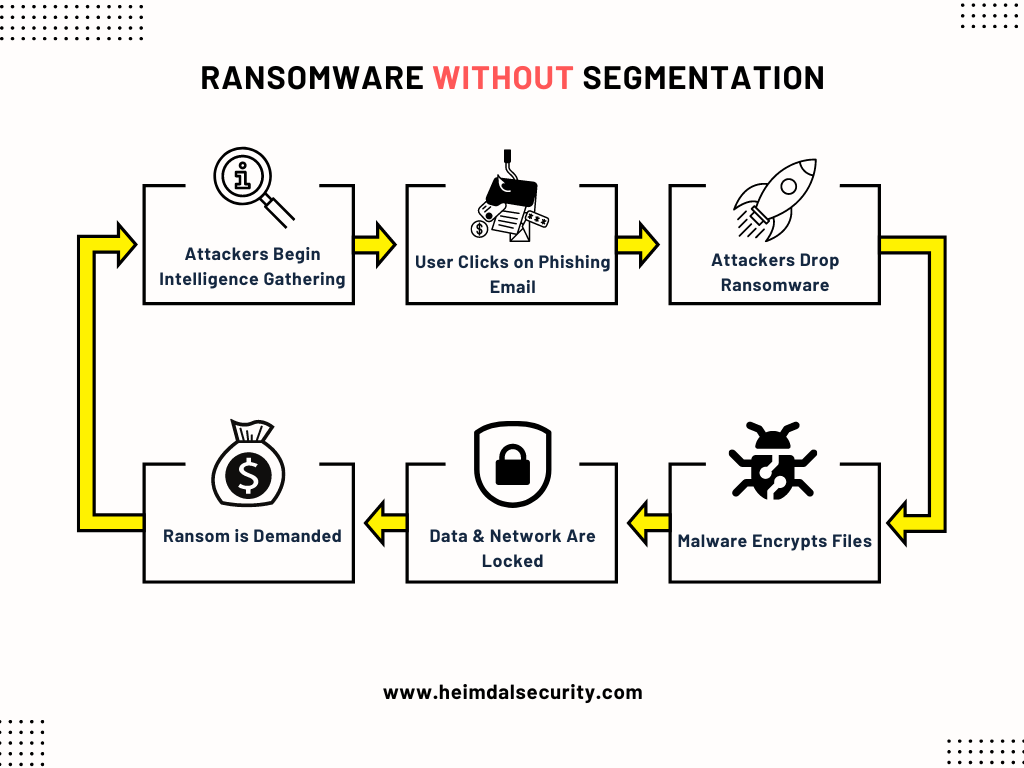
In contrast, even with good segmentation boundaries, there may be a point of compromise. Nonetheless, an attacker’s ability to move laterally is restricted, preventing them from progressing the attack.
Finally, preventing malware from spreading beyond its initial landing point significantly reduces the impact of a breach, allowing you to avoid the massive clean-up efforts and business downtime that can result from a successful ransomware attack.
How Can Heimdal® Protect You From Ransomware?
Assuming you fully understand how ransomware spreads, the next logical thing you might want to do is to make sure you prevent it from happening. Heimdal ® offers Ransomware Encryption Protection as part of its outstanding integrated cybersecurity suite, which is universally compatible with any antivirus solution and 100% signature-free, ensuring superior detection and remediation of all types of ransomware.

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;
Furthermore, Heimdal ® Patch & Asset Management secures and updates hundreds of thousands of enterprise endpoints. We keep our data updated much faster than industry benchmarks due to our quick response and implementation times, but it still yields fascinating insights.
See for yourself by booking a demo!
Wrap Up
The above mentioned methods are just a few examples of how ransomware can spread across networks. Unfortunately, as ransomware becomes more sophisticated, we can expect cybercriminals to devise new ways to distribute ransomware.
The good news is that you can take precautions to reduce your risk of infection. Read our previous articles on how to prevent ransomware and how to mitigate ransomware to learn more.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










