Contents:
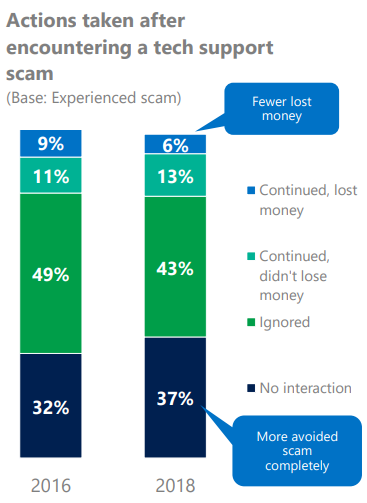
Scam phone calls are anything but new. You may even think they’ve almost become extinct. Even if it’s great to watch them decrease year by year, we hate to admit they are still happening.
One day you may get a call from a friendly and overly-polite support technician, who claims your computer has been infected with malware. This person will promise to fix your PC in exchange for an amount of money, or may purposely install malware without your knowledge. Or in most cases, both.
Source: Global Tech Support Scam Research
Scam phone calls are one of the most frequent scams. You could always be the next victim, so in this article, we explain how they happen and give you some actionable tips on how to stay safe.
Who gets targeted and why?
Scammers mostly try to take advantage of novice computer users.
At the same time, they pretend to be representatives of authority figures, such as well-known and reputable brand names. This way they make sure you will trust them.
More than that, scammers use fear to limit your ability to think clearly. While being frightened and in a vulnerable state, you are the perfect target and most likely to react the way they want you to.
Our experience with scam phone calls
One of our colleagues recently received a scam phone call. He played along, just to see where it will take him.
This isn’t the first time we’ve come across this type of incident. A few months ago, we witnessed a similar event – a fake tech support specialist called a Heimdal team member and tried to remotely access his computer.
So what happened?
Suddenly the phone rings, displaying a standard Danish number. Our colleague answers, and on the other side of the line, there is a lady with a strong Indian accent, who pretends to be from the “Computer Messages” department (they could have at least tried to come up with a more genuine name).
She warns him that his PC has been infected with malware, and reassures him this is the reason the computer is malfunctioning. Next, the tech support “specialist” tries to trick our colleague into pressing the Window + R keys and typing the “EVENTVWR” command.
When you press this key combination the Event Viewer window comes up on the screen. Almost anyone will have some warnings or errors showing up in here, and they may look scary to non-technical computer users.
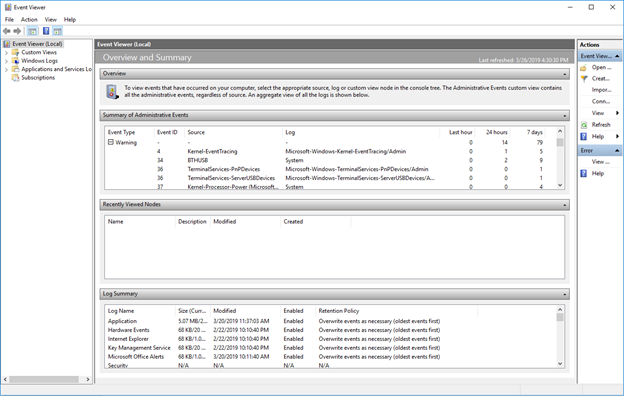
“What can you see on your computer screen?”, the tech support lady keeps asking, just to be sure her instructions are being followed. Our colleague answers “What should be on the screen?” and avoids to respond, only for the caller to mechanically continue the script. “That’s good sir, that’s absolutely right”, she replies cheerfully, simply ignoring the lack of logic behind the conversation.
Next, she tries to persuade him to download and install AnyDesk. This a remote desktop access software, which would have allowed her to connect to his computer and be able to access everything on it. This is the point where our colleague admits he is aware of her ill intentions and interrupts the call.
Eventually, we traced down the number the scammer was using and found out it was a real number. It belonged to someone from Denmark who was unaware the number had been spoofed.
Here you can listen to the scam phone call recording:
What should you do if you receive a scam phone call?
Your phone rings, you see a familiar number from your local area and assume you should take the call. This might be important. The next moment, you find yourself having a conversation with a benevolent “tech support technician” who wants to save your cyber life.
Here is how you can protect yourself in this situation:
1. Hang up the minute you suspect this might be a scam.
Our colleague played along just for the sake of finding out how far this scam can go.
Yet, what you should do is decline the offer the scammer is making and immediately hang up the phone. It’s advisable not to make any decisions while feeling under pressure. Especially when someone pretending to be from tech support who wants to fix your PC is on the line.
Microsoft tech support or other providers will never proactively contact you to try to fix your problem. It’s you who should report any security issues.
2. Never provide personal information or any details required to grant access to your computer.
The scam artists may already have your personal details, such as your email or your exact location, which is frightening enough. Do not give them any further information about yourself or any other details associated with your PC.
3. Do not download any software they ask you to
They will ask you to download and install applications that give them full control over your computer so they can access files and install malware applications to infect you. Do not get fooled and do not play their game!
Fortunately, there are methods that help you dramatically decrease the number of spam calls received, so we recommend you check out this highly effective guide.
We also encourage you to explore our resources that specifically address online scams:
- Here are the Top Online Scams You Need to Avoid Today
- Social Scams – The Full Breakdown and Protection Plan
- Airline Scams: Here Are 3 Valuable Tips On How To Avoid Them
- How To Avoid Christmas Scams? Here’s 10+ Valuable Expert Advice
- Beware of Scams Using Fake Facebook Profiles

What should you do if you have fallen prey to a scam phone call?
Let’s say the scammer somehow managed to fool you. The damage is done, so now the best thing to do is be proactive and act quickly. We recommend you to apply these key security measures to remain safe and don’t become an easy target:
1. Delete the software you were asked to download
Remove all the software the scammer may have asked you to download and install. They could now be able to access your data, track your activity, and install malware applications.
2. Raise a flag to all the parties involved
If you transferred money to the scammer, report the incident to your bank. Ask them to remove the transaction, and cancel your credit card immediately. Also, try to find out if the number is actually owned by someone and alert the person whose number was spoofed. You can also report the incident to your local authority and to the company the scammer was impersonating.
3. Change your passwords
If the malicious actor got the chance to connect to your computer, change all your passwords immediately. And make sure you always use strong and unique passwords, and never reuse passwords for multiple accounts. Instead, download a password manager and you’ll never even have to worry about remembering them all.
4. Share your experience
Let your friends, relatives, and coworkers know that phone scammers are targeting your local area. Share what happened on social media and in person. It’s always a good idea to spread the word so fewer people are taken by surprise.
It’s also critical to teach your children not to interact with strangers, as they might also be tricked into following the fraudsters’ directions.
Here are some resources to help your loved ones defend themselves from online threats and scams:
- 10 Ways to Help Our Parents With Online Security
- How to Keep Your Kids Safe on the Internet (10 Actionable Tips)
5. Clean your PC and install an anti-malware solution
For even more protection, add multiple layers of security with a proactive security solution, which will stop even the most advanced online threats.
Also, make sure you go through our step-by-step malware removal guide:
To Sum Up
Even though measures are actively being taken to eliminate this type of incident, as long as people keep engaging with these fraudsters, the harsh reality is that the scam phone calls industry will not come to an end anytime soon.
Have you ever been affected by scam phone calls? How did you react? Share your experience in the comments section below, so together we can raise more awareness around this subject.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security