Contents:
My parents are bright, intelligent people, curious to explore how modern stuff works. They quickly adopted all kind of new technologies into their lifestyle. They have more than 20 years of experience working on PCs, they own top of the line smartphones and smart TVs. They started using Facebook, Twitter and Instagram than most of my (same-age) friends. They aren’t scared of ordering stuff online, or using services like Uber and AirBnB. However, when it comes to privacy and security they have huge gaps. They are aware that the digital world has its risks, but they can be easily deceived. It’s difficult for them to realize how close they are to losing money or sensitive data. They can’t tell the difference between important and optional security steps. They also can’t distinguish between essential information and one that only has a commercial purpose. And I completely get it: with the avalanche of existent information, I often feel overwhelmed myself. My guess would be that your parents fall under the same vulnerable category. It’s important that we help them understand the basics of online security and create healthy digital habits. 
Our parents have poor basic security habits
1. They think they have nothing worth the cybercrooks’ interest.
No? Really? What about any work documents? No contracts attached to past emails? Any information they wouldn’t want to be public? No credit cards pins saved in text drafts on desktop? No online shopping on websites that stored credit card details? How you can help: Open their eyes. Compile together a list of all their online information assets. Take every account they have: emails (both work and personal), social network profiles, financial accounts, etc. List everything they have on those accounts, from work documents, photos, personal messages or sensitive information, such as credit cards PINs, passwords or social security number. Ask them to imagine how much it would cost if they lost that information, was deleted, stolen or leaked online. According to this, have them note how valuable each information is. You can also have them follow our free, action-ready security plan.
2. They have bad passwords habits.
They set passwords that are easy to guess – it’s usually their kids’ names, birth dates or pets names. Most likely, this kind of information can be found on social networks, such as Facebook profiles, where they are willingly sharing it. This makes cyber criminals’ jobs easier: they only need to glance over the social accounts profiles to find out possible passwords combinations or answers to security questions. They use the same password everywhere. They don’t take their time to create different passwords for each and every account, they only recycle the same password. And they don’t even think about changing it every few months. They write their passwords and PIN codes on a paper that they keep in their office desk or in a mail draft. Or worse, in their wallet, next to their credit / debit cards. They use some of the worst passwords: 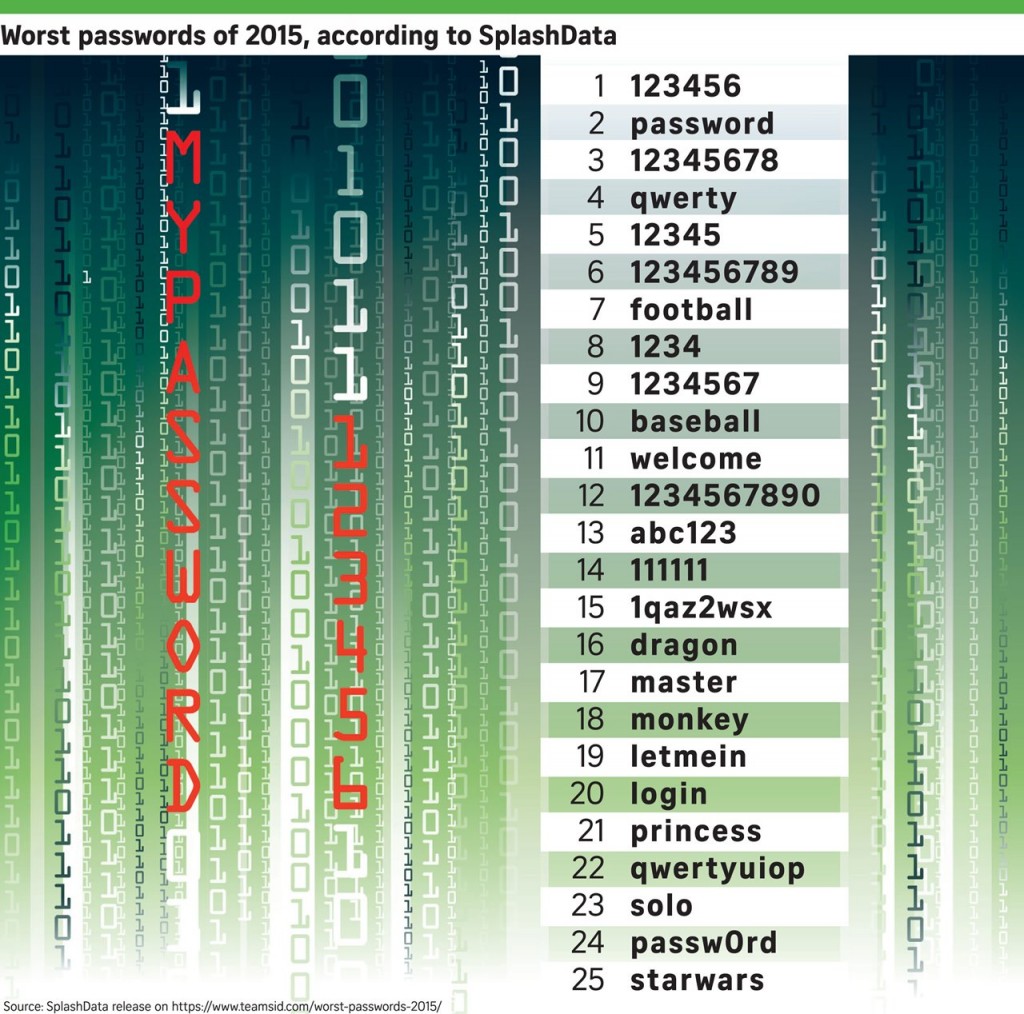 How you can help: Discuss together the importance of passwords, about why and how much they matter. Only a few people really comprehend how easy it is for cyber attackers to crack a password. [tweet “A password cracking server can try out more than 100 billion passwords every second.”] An 8 letter random password means 200 billion passwords combinations. How long would it take to break that password? We’ll let you do the math. Also let them understand why it’s important to have unique passwords for each and every account. Just like they don’t use the same keys for their car and house and bank safe deposit, they shouldn’t be using the same password everywhere. If one of them is breached, then the attacker will have access to all other accounts. And it doesn’t necessarily have to be your parents fault for a password to be leaked, the employees of the companies that manage those accounts can be equally responsible. Let them know that a good password needs to be at least 14 characters long, random, use non dictionary words, mix uppercase with lowercase, digits and punctuation. You can also forward them our password security guide 101.
How you can help: Discuss together the importance of passwords, about why and how much they matter. Only a few people really comprehend how easy it is for cyber attackers to crack a password. [tweet “A password cracking server can try out more than 100 billion passwords every second.”] An 8 letter random password means 200 billion passwords combinations. How long would it take to break that password? We’ll let you do the math. Also let them understand why it’s important to have unique passwords for each and every account. Just like they don’t use the same keys for their car and house and bank safe deposit, they shouldn’t be using the same password everywhere. If one of them is breached, then the attacker will have access to all other accounts. And it doesn’t necessarily have to be your parents fault for a password to be leaked, the employees of the companies that manage those accounts can be equally responsible. Let them know that a good password needs to be at least 14 characters long, random, use non dictionary words, mix uppercase with lowercase, digits and punctuation. You can also forward them our password security guide 101. 
3. They don’t understand what two-factor authentication is or why it’s so important to set it up everywhere possible.
What’s even worse, chances are they haven’t even heard about it until your bring it up. 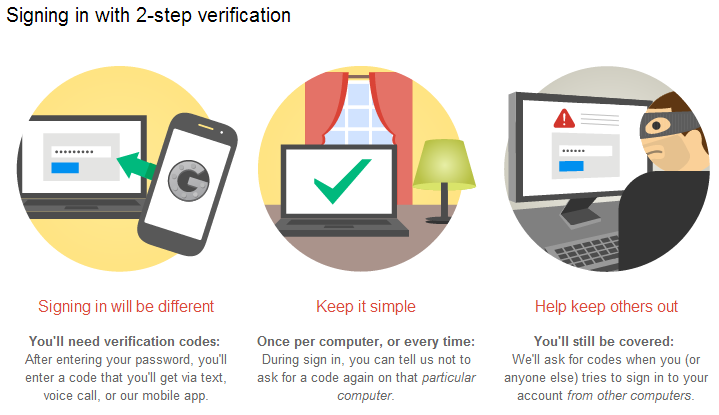 How you can help: Ideally, two-factor authentication would be a default setting for all major accounts. But until that happens, you’ll just have to help them set it up wherever it’s currently available. Let them know how easy it is to use it: they just have to log into the account with their usual password, then they’ll receive a text message on their phone with a unique code, they’ll have to put code in and that’s it – safe login! Start with setting it up for their banking accounts, put in place a second verification for online payments. Move on to the email accounts, as most likely those are the central piece of their online activity and they are linked to all other accounts. Social networks shouldn’t be neglected either – Facebook, LinkedIn, Instagram, Twitter, they all offer the possibility to activate 2FA. Help them understand how interconnected our online accounts are. If a cyber attacker manages to breach into one of them, then all accounts will be compromised. You can also send them our complete guide to what two-factor authentication is and why they should use it.
How you can help: Ideally, two-factor authentication would be a default setting for all major accounts. But until that happens, you’ll just have to help them set it up wherever it’s currently available. Let them know how easy it is to use it: they just have to log into the account with their usual password, then they’ll receive a text message on their phone with a unique code, they’ll have to put code in and that’s it – safe login! Start with setting it up for their banking accounts, put in place a second verification for online payments. Move on to the email accounts, as most likely those are the central piece of their online activity and they are linked to all other accounts. Social networks shouldn’t be neglected either – Facebook, LinkedIn, Instagram, Twitter, they all offer the possibility to activate 2FA. Help them understand how interconnected our online accounts are. If a cyber attacker manages to breach into one of them, then all accounts will be compromised. You can also send them our complete guide to what two-factor authentication is and why they should use it. 
4. They leave their mobile phones and computers unattended and with no security barrier set in place.
This way, they could be easily accessed by someone with bad intentions. It could be a thief that stole their mobile phone and thus gained access to other sensitive data. Or, even more likely, a vengeful work colleague that installs a keylogger or Trojan horse on their PC, to spy on them.  How you can help: Teach them how to set up their phone to lock after a short time, if it’s been idle, and how to set it to require authenticating in order to unlock. If available, use something stronger than a four digit PIN (that’s the easiest one to breach).
How you can help: Teach them how to set up their phone to lock after a short time, if it’s been idle, and how to set it to require authenticating in order to unlock. If available, use something stronger than a four digit PIN (that’s the easiest one to breach). 
Our parents can easily fall for scams & social engineering
5. They can’t identify cyber threats delivered via email.
They fall for all the contests and lotteries that announced them they’ve won. They will click on any email they receive, without second thinking that they might not be from who they think they are.They are willing to cooperate and give away their personal data. What’s even worse, they’ll click on links or download attachments without giving it any extra thought. Here’s a popular scam example: 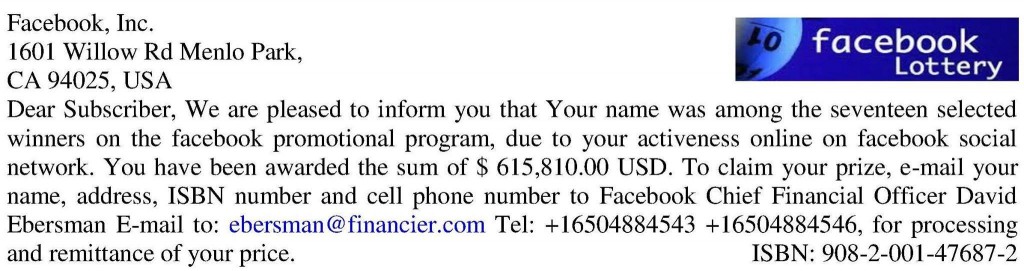 (source) How you can help: Encourage them to second guess any email they receive before opening it, replying or clicking on any link or attachment. Let them know that just because an email says it comes from the bank or the IRS and uses the company’s logo, it doesn’t mean it really was sent by their representative. If they still aren’t sure of its authenticity, ask them to forward the email and have you check it. We are aware that this is not a long-term solution
(source) How you can help: Encourage them to second guess any email they receive before opening it, replying or clicking on any link or attachment. Let them know that just because an email says it comes from the bank or the IRS and uses the company’s logo, it doesn’t mean it really was sent by their representative. If they still aren’t sure of its authenticity, ask them to forward the email and have you check it. We are aware that this is not a long-term solution 
6. They don’t understand how social media platforms work or what their impact is.
They don’t know how to set up their privacy settings on social networks. They aren’t aware of the possible consequences that might arise from this. They freely allow any third-apps to connect and access their online accounts, without giving any second thoughts to it. Most of their friends also lack technical knowledge, so the odds are that one of them will get infected with a Facebook worm and further infect his / her network. They aren’t aware that they shouldn’t click on short links, links that they don’t know where they lead, not even when those links were sent by their friends.  (source) How you can help: This kind of scams rely on shocking news, use celebrities names or even emotional extortion. Ask them to be patient and don’t rush into clicking on any links or opening attachments. Before doing any action they should ask their friends what those links are about. We also recently published an extended guide on social scams, you can forward it to them.
(source) How you can help: This kind of scams rely on shocking news, use celebrities names or even emotional extortion. Ask them to be patient and don’t rush into clicking on any links or opening attachments. Before doing any action they should ask their friends what those links are about. We also recently published an extended guide on social scams, you can forward it to them. 
7. They share too much information.
They post on social networks photos of their homes, photos from their vacations, so the criminals know how their places look like and when they are gone. They also post tons of photos of babies and children – nephews, cousins, and so on. They aren’t aware that the net is dark and full of terrors – including groups where pedophiles are sharing photos like the ones posted by them + digging for any kind of information on how to locate the kids. Other potential risks:
Stories of oversharing gone wrong have been rampant in the news, with one of the most extreme examples including a phenomenon called ‘digital kidnapping’ reported on earlier this year. Parents were shocked to learn that strangers were ‘stealing’ their kids’ online photos and re-sharing them as if the children were their own. In other cases, children’s photos have become the target of cruel jokes and cyber bullying. Among the most notorious cases in recent years was that of a Facebook group that made fun of ‘ugly’ babies.
(source)  How you can help: Ask them to be more aware of what they share online. While it could be tempting to do what everyone else is doing, as a way to fit in the new modern world, they should also be aware of the dangers of oversharing. Go together through the privacy settings for each social network account and adjust them to their needs. Have them turn off their location settings – they wouldn’t want others to know where they live, right?
How you can help: Ask them to be more aware of what they share online. While it could be tempting to do what everyone else is doing, as a way to fit in the new modern world, they should also be aware of the dangers of oversharing. Go together through the privacy settings for each social network account and adjust them to their needs. Have them turn off their location settings – they wouldn’t want others to know where they live, right? 
8. They can be easily manipulated by online media.
They think that just because it’s on the internet, then it must be true. They are willing to believe in conspiracies and fake news. They don’t know how to discern between what’s true and what’s exaggerated because of a commercial purpose.  (source) How you can help: Ask them to always be vigilant. Have them check from three trustworthy sources (legitimate websites) before they believe anything they read. If unsure, ask them to email you so you can help them out.
(source) How you can help: Ask them to always be vigilant. Have them check from three trustworthy sources (legitimate websites) before they believe anything they read. If unsure, ask them to email you so you can help them out.
Our parents don’t realize how vulnerable software & hardware really are
9. They place too much trust in an antivirus product.
They believe that just because they installed it and are paying for it, then it will save them from any potential cyber threat. They believe that their Apple device can’t be hacked. Actually, that’s not true. Last year, MAC and iPhone OS made it to the top of softwares with most vulnerabilities. And since we brought up this subject, Linux users aren’t safer than Windows ones. Take a look over 2015’s list of most vulnerable software: 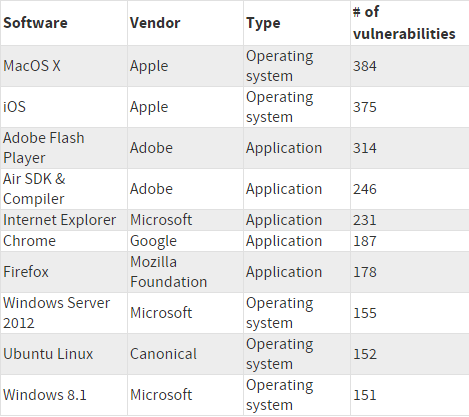 How you can help: Help them realize that it’s not enough to have an antivirus (or only use iOS / Linux) and it won’t protect them from all evils that exist out there. Help them install security software they can trust, such as a traffic-filtering solutions (that sanitize Internet traffic) and automatic software patching solutions that keep their apps up to date.
How you can help: Help them realize that it’s not enough to have an antivirus (or only use iOS / Linux) and it won’t protect them from all evils that exist out there. Help them install security software they can trust, such as a traffic-filtering solutions (that sanitize Internet traffic) and automatic software patching solutions that keep their apps up to date.
10. Parents rarely understand the interconnectedness in software and / or hardware.
They have no idea how sophisticated and frequent cyber attacks are. They don’t realize how easy it is to get malware. You don’t even have to click on anything or enter a suspicious website in order to compromise your computer – all it takes is an infected banner on a perfectly legit website. Here’s how ransomware works, for example: ![Dangers of outdated software & potential for malware infections [Heimdal Security]](https://heimdalsecurity.com/blog/wp-content/uploads/Dangers-of-outdated-software-potential-for-malware-infections-Heimdal-Security.png) How you can help: Let them know that even legit websites can be compromised. Explain how plenty of attacks can happen without their action – they don’t need to click or download anything for their PC to get infected with malware or Trojans. Malicious codes injected in ads will search for vulnerabilities in their system and exploit them. 8 software apps make 99% of computers around the world vulnerable to cyber attacks, so make sure that your parents keep their software updated and patched all the time. This includes: browsers, browsers plugins and add-ons (Flash, Java) or any other kind of desktop apps (Adobe Reader, VLC player). Go to the software settings and change them all on Auto-Update.
How you can help: Let them know that even legit websites can be compromised. Explain how plenty of attacks can happen without their action – they don’t need to click or download anything for their PC to get infected with malware or Trojans. Malicious codes injected in ads will search for vulnerabilities in their system and exploit them. 8 software apps make 99% of computers around the world vulnerable to cyber attacks, so make sure that your parents keep their software updated and patched all the time. This includes: browsers, browsers plugins and add-ons (Flash, Java) or any other kind of desktop apps (Adobe Reader, VLC player). Go to the software settings and change them all on Auto-Update.  (more details here)
(more details here)
Conclusion
Parents are a vulnerable category and cyber criminals won’t shy away from taking advantage of this. As the population is getting older and technology makes huge strides, cyber security education becomes an essential necessity.

INSTALL IT, FORGET IT AND BE PROTECTED
Download Heimdal™ FREE

 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










