Contents:
We spend a lot of time on social media, and for good reason. It has collapsed the communication distance between us and other people, bringing us closer.  Source However, this category of “other people” includes persons you would never want to meet: scammers, blackhat hackers, and other such online criminals. In this article, we want to show how you can identify a fake online profile, and avoid any of their scamming attempts.
Source However, this category of “other people” includes persons you would never want to meet: scammers, blackhat hackers, and other such online criminals. In this article, we want to show how you can identify a fake online profile, and avoid any of their scamming attempts.
Scams using fake Facebook, Snapchat, Instagram accounts
At the moment, Facebook has 1.7 billion users. Instagram has around 600 million. Twitter over 300 million. But a scammer only sees millions upon millions of potential victims. Because of their design, some social networks, such as Instagram, are fairly one-dimensional in the types of scams a cybercriminal can carry out on them. Others such as Facebook are more feature rich, and provide more ways for a scammer to defraud you.
Catfishing using fake Facebook, Snapchat or other online profiles
Catfishing is a well-known Internet scam, where a catfisher creates a fake online profile in order to seduce a victim into a fictitious online relationship, in order to extract money or other benefits from the victim. A logical first target are users of dating sites or apps such as Tinder, Match or eHarmony where it’s easy to make fake profiles. A catfisher scours through the user base, looking for a particularly vulnerable and eager user open to emotional manipulation. After the scammer settles on a mark, a process of trust building begins. This can take anywhere from a few days to months or even years. At some point, the catfisher promises to meet the victim, but in order to do that they need help for a last-minute problem such as visa processing fees, an inheritance stuck in customs, an unexpected bankruptcy and so on. But it’s all a ruse, just so the catfisher can manipulate the love-blind victim into giving up their money. But catfishers also target regular social networks such as Facebook and Instagram. All of these money scams work in pretty much the same way: create a fake profile, crawl the social network for vulnerable users, earn their trust and ask for money. [Tweet “Don’t get your heart broken by a catfisher with a fake profile”]  Source
Source
WhatsApp or Facebook Messenger scams
Most people usually associate phishing with emails, but another important channel is social media. A scammer creates a fake social media profile, often times a Facebook one, where he pretends to be a sales representative, bank employee or other similar position. The scammer then asks you to click a link in order to “receive the latest offer” or “reconfirm your account credentials”. Of course, the link is malicious and will either launch a malware infection or it will save all the data you type into the forms. 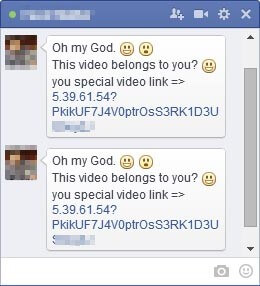
Beware of a fake Instagram, Twitter, or Facebook page
Why trick people one by one when you can just create a fake page for a business or organization and fool thousands of users? A scammer creates a fake page for a product and uses some basic psychology to create a sense of urgency. This is the case for Facebook scams with prizes and promos such as “share for a chance to win” or “weekly deals”. 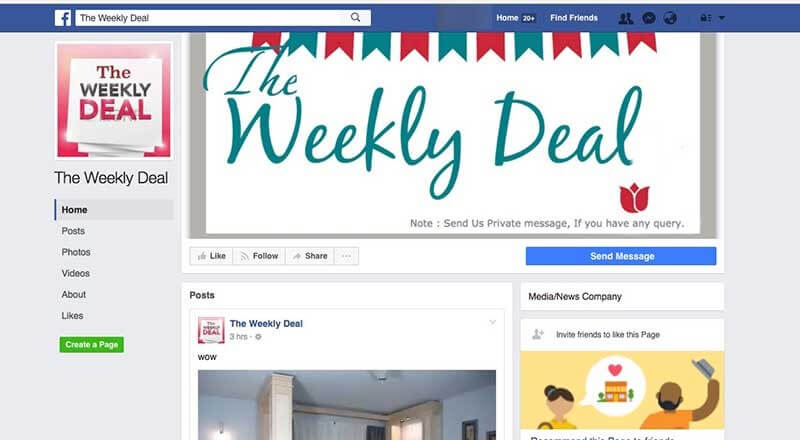 Source To boost the spread and vitality of the page, the scammer might organize “sharing contests”, where you get a chance to earn a free product if you would just share the page on your own Facebook profile. At some point, the page will do a “bait and switch”, meaning it will start to spam all the users who liked the page either with meaningless posts or with phishing links or other types of internet scams. Instagram pages work in a slightly different way since you cannot write a link in the comments and the sharing function is more limited and cumbersome than Facebook’s. Instead, Instagram pages will add a link to the bio page, and then post a photo asking you to click on it in order to get that “awesome deal” or whatever bait they choose to use.
Source To boost the spread and vitality of the page, the scammer might organize “sharing contests”, where you get a chance to earn a free product if you would just share the page on your own Facebook profile. At some point, the page will do a “bait and switch”, meaning it will start to spam all the users who liked the page either with meaningless posts or with phishing links or other types of internet scams. Instagram pages work in a slightly different way since you cannot write a link in the comments and the sharing function is more limited and cumbersome than Facebook’s. Instead, Instagram pages will add a link to the bio page, and then post a photo asking you to click on it in order to get that “awesome deal” or whatever bait they choose to use. 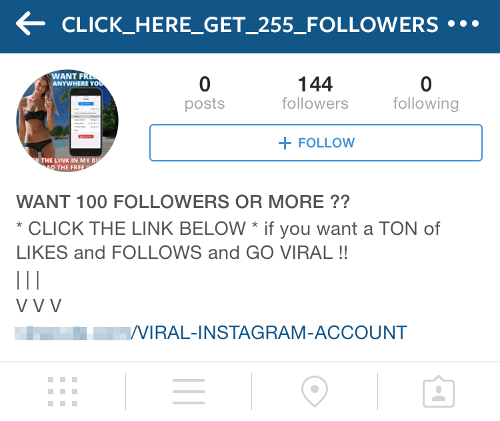 Source
Source
Like-farming campaigns and fake tweets
Likes, retweets, shares, comments and follows are all valuable currency on social media. In order to extract them, spammers will employ “like-farming” campaigns. These campaigns aim to acquire as many followers and likes as possible. The spammer will then leverage this list of likes and followers to send phishing links, spam messages, sell the information to marketers or send out scam campaigns. On Facebook, these “like-farming” posts can take many shapes and sizes such as a fake post about charity donations, contests where you might win something if you like a post or emotional baits such as “like to save this kid from cancer”.  Source
Source
Fake quizzes that extract your information
You must have seen those posts and quizzes inspired by movies or video games. Basically, you answer a set of questions and then the quiz tells you what movie character you are or some other personality assessment. Oftentimes, these quizzes are fronts for privacy scams that collect your answers and then sell them to third parties. Many of these quizzes come with a “Login with Facebook” button in order to do the quiz. This gives the website/app pretty much all of your important information such as emails, location, language, job and so on. Oftentimes, this isn’t even illegal, since the quiz developer actually tells you what he will do with the information you provide, but to read this you need to dig deep into the labyrinthine “Terms and Conditions”.
Passive fake friends and followers that monitor your account
The average Facebook user has 338 friends. Chances are, you’ve never actually met some of those people and don’t know who they are. Criminals can exploit this carelessness by befriending you and then monitor your account to collect information and see what you’re up to. In particular, they’ll be on the lookout for vacation photos outside your home city or country, which means your house is probably empty and ripe to be broken into. 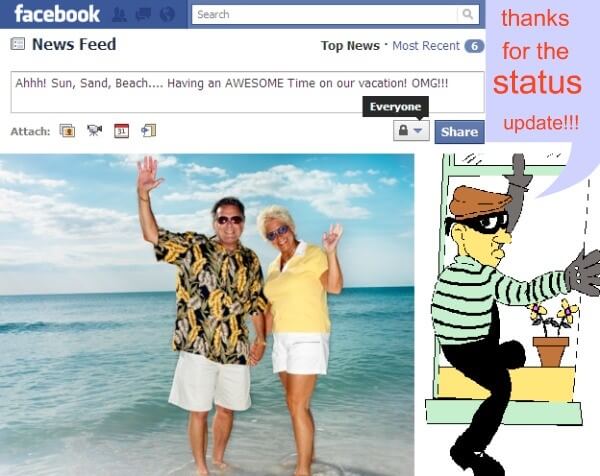 Source
Source
Active fake friends and followers that spam or impersonate you
Facebook doesn’t prevent users from having duplicate user names, so pretty much anyone can copy the name and pictures of one of your friends and pretend to be you. Depending on what they want to extract from you, a fake Facebook friend can either seek to learn valuable information about you, such as secret data from the company you work at or credit card details. In most cases, however, they will pretend to be the friend in question and ask you for a loan or some other “friendly favor”. In other cases, a fake friend will be used as a bot, sending out spam messages and bombarding the newsfeeds of friended users with promotional messages or phishing links, like those infamous porn videos that will infect you too if you make the mistake of clicking them. 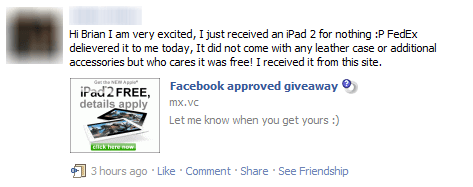 Source In other cases, it’s possible someone might actually want to steal YOUR identity. In these situations, they’d probably target your boss or other family members.
Source In other cases, it’s possible someone might actually want to steal YOUR identity. In these situations, they’d probably target your boss or other family members.
Money flipping scams
Particularly frequent on Instagram, money flipping scams work by promising a user huge returns if he would just deposit a small sum as an initial investment. The scammer claims to be a financial adviser or an Internet marketer, with inside knowledge on how to manipulate exchange rates and stock prices in order to get a 10x return on investment. And all you have to do is to simply deposit some money, usually a minimum of 100$. Here’s what a money flipping account looks like: 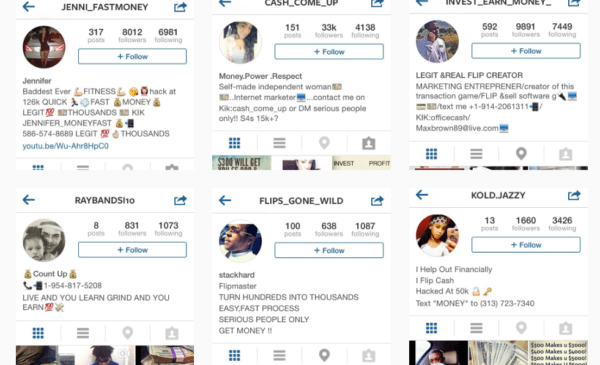
Instagram, Twitter, and Facebook ad scams
Most social networks have a vetting process for ads people want to post on them. Both the ad and the service/product it sells are reviewed to make sure they comply with the company’s guidelines and other legal requirements. However, in cases where the ad redirects a user to a website, a scammer will alter the page after the review process, injecting malicious code, add abusive content, or data-stealing forms. There’s little a social network can do against such fake ads since the linked websites are out of their control. It’s also deeply impractical, if not impossible, to monitor each and every ad created to make sure they continuously comply with the guidelines.
LinkedIn fake job offers
Users on LinkedIn are primarily there to improve their hiring prospects, so receiving a job offer isn’t something out of the ordinary. However, some LinkedIn scammers simply hire you for a few weeks, only to fire you a few days before your first paycheck. Usually, these fake job offers promise you to the opportunity to work from home, and even come with a sizeable salary package. In other cases, these might be project-based work, so you first have to do the work, and only then will you get paid. As you can imagine, however, the pay never comes. [Tweet “Don’t get tricked into working for free by fake LinkedIn job offers”] 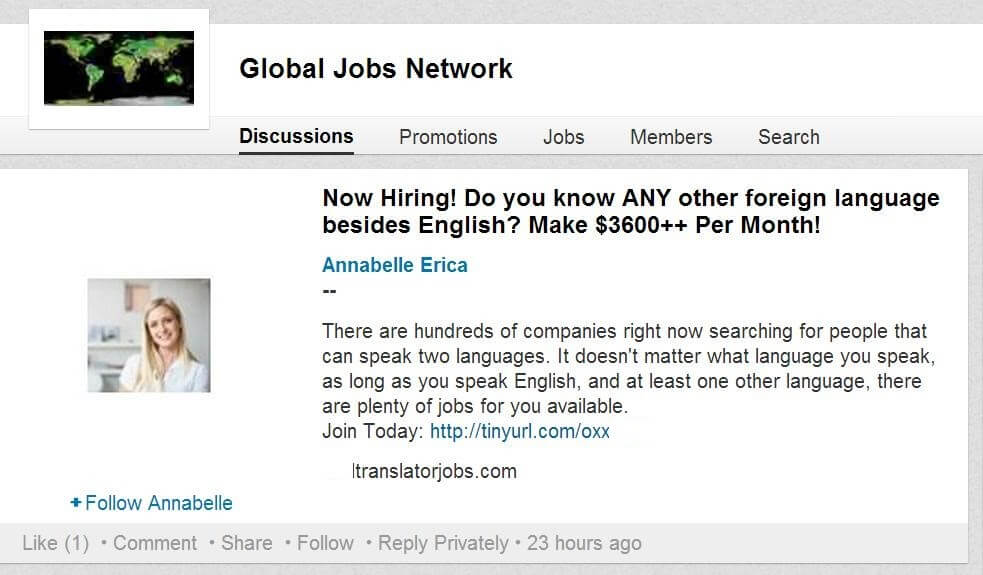 Source
Source
Twitter spammers
A fake Twitter account can be used to spam phishing links or tempt you with fake offers. A scammer simply has to write a clickbait tweet text to accompany the phishing link, and let the tweet go viral. 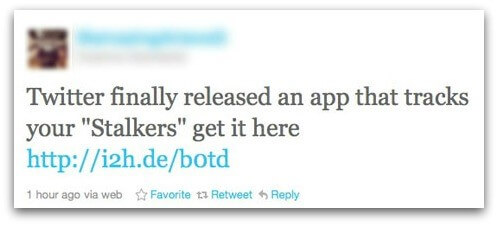 Source
Source
Information harvesting on LinkedIn
What better place to find out important information about an employee at a company if not from his LinkedIn account? Malicious scammers will build up their fake profiles in order to make them believable and then contact users and try to extract information from them such as email addresses, or even company data. This works particularly well on LinkedIn since a user expects to be contacted by potential employers and information-seeking questions aren’t that unusual.
How to spot a fake profile or friend
The best way to protect yourself against fake profiles, pages and so on is to quickly identify them. Here are some of the signs which should raise your suspicions.
How to spot fake Facebook accounts
The number of friends a Facebook user has is usually the first thing that should raise your suspicions. As we said before, the average Facebook user has 338 friends, so if someone has 2000 or 3000 friends, then that should be an eye opener. Of course, you shouldn’t take it as an absolute rule, since many users are “friend-happy” and simply accept each and every friend request, so they end up with a huge friend base. A more relevant sign is the number of tags used in a photo. As a rough average, most users use 3-4 tags, but a fake one will add tens or even hundreds of tags, in order to reach as many users as possible in those tag channels. 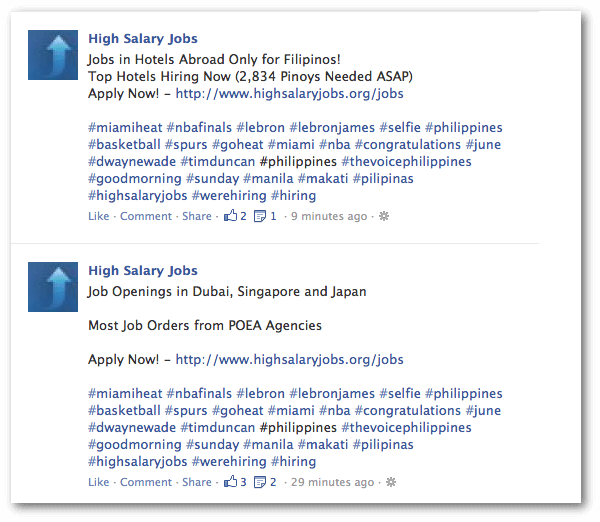 Source Next, look at the photos they have. If the account has only 2-3 photos and all of them are very professional or somehow look “too good to be true”, then there’s a very high chance the profile is fake. If you want to be sure, you can do a reverse image search to see if those profile pictures are fake. To do this, simply go to www.Google.com, and click “Images” in the top right corner.
Source Next, look at the photos they have. If the account has only 2-3 photos and all of them are very professional or somehow look “too good to be true”, then there’s a very high chance the profile is fake. If you want to be sure, you can do a reverse image search to see if those profile pictures are fake. To do this, simply go to www.Google.com, and click “Images” in the top right corner. 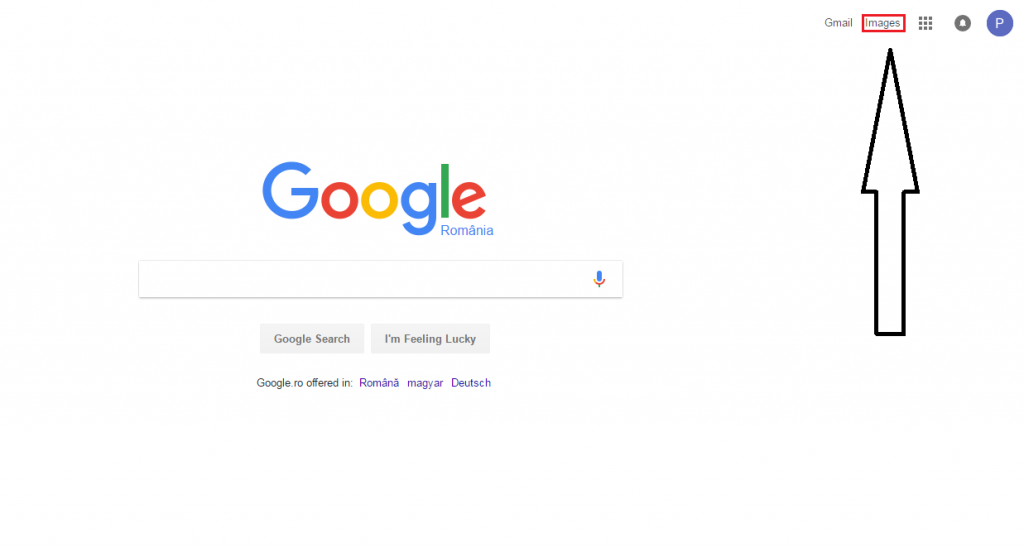 Next, simply download one or more photos from the suspicious profile, and then drag and drop the image into Google Image search. Google will analyze the contents of the photo, and then come up with a list of results. Depending on your luck, you may just find out the real person behind that photo. Another tell-tale sign is how geographically widespread the user’s friendships are. Let’s assume both of you live in Italy, but the suspicious account has an unusually high number of friends from Indonesia, India, Brazil, Russia and so on. Chances are those friendships are fake, and the scammer just randomly sent friend requests to anyone willing to accept.
Next, simply download one or more photos from the suspicious profile, and then drag and drop the image into Google Image search. Google will analyze the contents of the photo, and then come up with a list of results. Depending on your luck, you may just find out the real person behind that photo. Another tell-tale sign is how geographically widespread the user’s friendships are. Let’s assume both of you live in Italy, but the suspicious account has an unusually high number of friends from Indonesia, India, Brazil, Russia and so on. Chances are those friendships are fake, and the scammer just randomly sent friend requests to anyone willing to accept.
Is that a fake Facebook page?
It’s not just fake friends you should be on the lookout for, but also fake Facebook pages. Most big brands such as Nike and Apple have “verified” pages. This means that Facebook itself has made sure that those are indeed the real pages for those brands. You’ll know a page is “verified” if it has this sign next to its name.  As a rule of thumb, consider any big brand Facebook page without that “verified” sign to be fake. As a reference, here are the Facebook search results for “Adidas”.
As a rule of thumb, consider any big brand Facebook page without that “verified” sign to be fake. As a reference, here are the Facebook search results for “Adidas”. 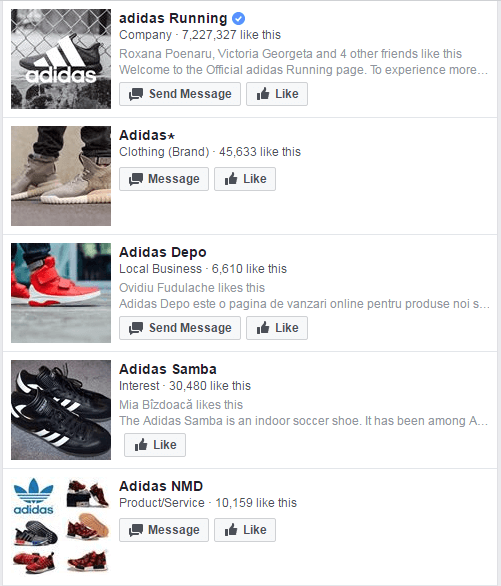 How many of these do you think are genuine? Chances are that none of them are. These cloned pages of big brands will redirect any visitor using either a phishing link or sell them counterfeit products or just scam them of their money. Next, you should look at the number of likes a page has, as well as its engagement, meaning how many people interact with its posts. If barely anyone likes or comments on a post, then that’s a clear sign the page isn’t what it claims to be. They might even have obtained fake likes for that page. Big brand pages should have a big following and a decent engagement, even if it’s a local page for a single country. Another thing you should do is to double-check any contact info and address you come across to make sure it’s real. Big brands such as Adidas and Apple have something called a “store finder” which you can use to find a nearby store. You can use this feature to compare the address listed in the suspicious Facebook page with the legitimate ones in the store finder. If the addresses don’t match, then it’s safe to assume the store is fake and that you should avoid it. If the suspicious page is for a smaller company, do some research using Google. Look for reviews, addresses, phone numbers and user comments. Call them if you want to be sure the company is real.
How many of these do you think are genuine? Chances are that none of them are. These cloned pages of big brands will redirect any visitor using either a phishing link or sell them counterfeit products or just scam them of their money. Next, you should look at the number of likes a page has, as well as its engagement, meaning how many people interact with its posts. If barely anyone likes or comments on a post, then that’s a clear sign the page isn’t what it claims to be. They might even have obtained fake likes for that page. Big brand pages should have a big following and a decent engagement, even if it’s a local page for a single country. Another thing you should do is to double-check any contact info and address you come across to make sure it’s real. Big brands such as Adidas and Apple have something called a “store finder” which you can use to find a nearby store. You can use this feature to compare the address listed in the suspicious Facebook page with the legitimate ones in the store finder. If the addresses don’t match, then it’s safe to assume the store is fake and that you should avoid it. If the suspicious page is for a smaller company, do some research using Google. Look for reviews, addresses, phone numbers and user comments. Call them if you want to be sure the company is real.
How to spot a fake Twitter account
Just like Facebook, Twitter also has a verified account feature that helps you spot the real account in a sea of cloned or fake ones. Accounts with only professional photos and bios filled with grammar mistakes are probably bot accounts used to send spam messages with phishing links or other nasty content. If an account barely posts anything, yet it has thousands of followers, then chances are the follower count was inflated using blackhat methods such as botting. That big follower base might act as social proof to impress a user into clicking a malicious link or purchase a fake product or service. Fortunately, there are websites out there that detect fake or inactive Twitter followers, and best of all, they’re free. Here are some websites that can do that https://fakers.statuspeople.com/ or https://www.twitteraudit.com/.
Finding fake LinkedIn profiles
LinkedIn is a more secure social network than Facebook or Twitter, but fake profiles do exist, and you might just stumble across one from time to time. Here’s how you can identify a fake LinkedIn account:
Quality of their photos
Since it’s LinkedIn, you’re kind of supposed to bring your best photos forward. But many scammers go for typical stock photos which are easily recognizable, with their big smiles, perfect exposure, and pearly white teeth. 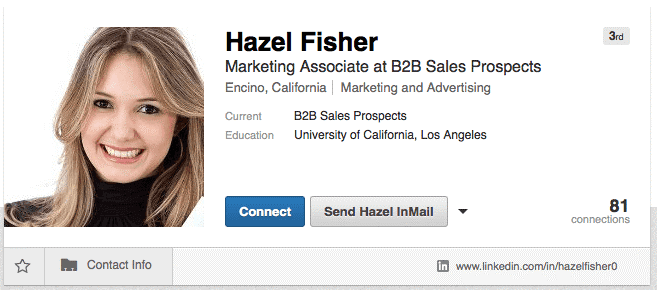 Source Dig a little deeper if you see one of these too good to be true photos, maybe even do a Facebook search for the person in question and see if the data matches. Alternatively, you can do a reverse image search, using Google Images or TinEye.
Source Dig a little deeper if you see one of these too good to be true photos, maybe even do a Facebook search for the person in question and see if the data matches. Alternatively, you can do a reverse image search, using Google Images or TinEye.
Does the information make sense?
Scammers can be lazy and cut corners. Some of them simply copy the information from two or more accounts, but this then creates a mismatch in the information. For instance, the person in the photo might be too young for the number of working years she wrote in. The suspicious profile’s work experience might not make much sense. For instance, they might say they worked 10 years as an HR representative and another 10 as a web developer. While this career turns certainly do happen, it’s not something you see all the time and warrants extra investigation.
Check out their connections
Ask any of your shared connections if they know the suspicious account in real life. If one or all of them say no, then that LinkedIn account is probably fake.
Are they premium users?
Serious recruiters will frequently use LinkedIn Premium since they need the extra functionality to be better able to find potential employees. Scammers loathe to give away their money, so the chances that one of them might use LinkedIn Premium is very small.
How to verify an Instagram account
Scammers have a harder time with Instagram compared to Facebook or Twitter since they can only post links in the chat menu or bios. This gives them fewer opportunities to lure in users to click on a phishing link. That doesn’t stop some scammers, though, so here’s how you can identify a fake Instagram account.
Look at the date the photos were posted
Fake Instagrammers want to build up their account and make it seem real as soon as possible. So one of the first things they do is to fill up their account with photos in a single day. So be suspicious if you see an account with 30-40 photos posted in a single day.
The account follows a huge number of people
Usually, this number can be as high as 5000-6000 people. Chances are the account is botted, meaning the owner set up some programs to automatically follow/unfollow users in the hopes that some of them might follow back and increase his audience.
Look for an Instagram verification
Just like with Twitter and Facebook, a high profile user will most likely have a verified account, confirming their identity and separating them from any cloned pages. 
Check the link with Virus Total
Virus Total is a neat online security tool that scans files and links for any malicious malware they might contain. Use this if you’re tempted to click a link provided by an Instagram account in the bio or through direct messaging. 
Your protection checklist
 Social media is here to stay, and that’s a good thing overall. It’s changed our lives for the better, even while generating a wave of cynicism on how it has taken over our lives. But as with anything good in life, scammers have found their way around the safeguards, and now use them to harm us in more ways than one. Hopefully, by learning how they do that, you will be better able to dodge any of their attempts and keep safe on the Internet.
Social media is here to stay, and that’s a good thing overall. It’s changed our lives for the better, even while generating a wave of cynicism on how it has taken over our lives. But as with anything good in life, scammers have found their way around the safeguards, and now use them to harm us in more ways than one. Hopefully, by learning how they do that, you will be better able to dodge any of their attempts and keep safe on the Internet.



 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









