Contents:
Doxxing is a type of cyber attack that involves discovering the real identity of an Internet user. The attacker then reveals that person’s details so others can target them with malicious attacks. Doxxing is analyzing information posted online by the victim in order to identify and later harass that person.
What is doxxing?
The term “doxxing” comes from the expression “dropping dox”, which was a revenge tactic used by hackers where they dropped malicious information on a rival.
Nowadays, doxxing is used to shame or punish people who would rather stay anonymous, because of their controversial beliefs or other types of non-mainstream activity.
Because most of us are careless with the information we share on the Internet, we tend to leave behind a trail of breadcrumbs a cybercriminal can use to find out our real identity, then deploy a string of malicious attacks.
This is called doxxing, and has messed up the lives of more than one person.
Famous Doxxing Cases
Violentacrez
Michael Brutsch created an online persona named violentacrez for the Internet messaging board Reddit.
Over the years, he created a reputation as a troll because of his posts on the website. For instance, he created subreddits (subforums) around misogyny or sexualized photos of underage women.
For a long while, Michael Brutsch succeeded in keeping his online identity, violentacrez, a secret.
But Gawker journalist Adrian Chen managed to connect Michael Brutsch to violentacrez, and then went public with the information. In other words, Michael Brutsch was doxxed.
Chen was able to do the doxxing because Michael Brutsch took risks with his identity. For one, he actually met Reddit users in real life, in meetups and parties. In photoshoots, he asked for his face to be blurred. Not only that, but he also hosted a podcast, which Chen used in a phone call with Michael Brutsch to see if the voices matched.
After he was doxxed, Brutsch ended up losing his job and enduring a very public shaming, which was made even worse by his decision to do a CNN interview. After this episode, there is little information to go around as to what happened next to Michael Brutsch. But his life as a notorious Reddit troll is just one search away.
Of course, what Michael Brutsch was doing was illegal and the authorities should have gotten involved to discover who he is and punish him according to the law. But public shaming and vigilantism are not the way to go.
Fake Nazi affiliation
With the current political landscape being what it is, a large number of people are fighting against Nazi and Neonazi organizations rising to attention both online and offline. In the pursuit of trying to silence dangerous agendas, the number of online vigilantes has risen alarmingly. In the past few months, we’ve seen a lot of cases of Neonazi forum users being doxxed, harassed online and even getting fired because of their opinions, as reported in this New York Times piece.
While the cause might seem worthy, doxxing is and remains online vigilantism and this is never good.
Kyle Quinn, a professor from Arkansas, was wrongly accused of participating in the neo-Nazi march in Charlottesville. Overnight, Mr. Quinn found his image being shared by thousands of people across social media and he was bombarded by messages on Twitter and Instagram. Even worse, his employers were contacted by doxxers demanding Mr. Quinn’s firing.
Swatting
Another practice related to doxxing is Swatting. Swatting means prank-calling the police or SWAT units to another person’s address. In the online area, a victim getting doxxed can also lead to swatting. Malicious hackers find someone’s address and make fake bomb threats or other serious incidents, then the police show up to the unsuspecting victims’ home.
In December 2017, such an incident lead to the death of Andrew Finch from Kansas. Finch was fatally shot by an officer responding to a false domestic violence dispute.
28-year-old Finch had previously played a Call of Duty game online and started fighting with 25-year-old Tyler Barris. Another player, going under the username “Miruhcle”, escalated the conflict to dramatic proportions. He provided Barris with Finch’s home address and dared him to do a swatting.
Barris had two prior swatting incidents, making calls to the police about fake bomb threats. This time, the doxxing and swatting took a turn for tragedy. Barris sent police at Finch’s house by falsely reporting a murder and hostage situation. Police arrived at Finch’s house and, when he opened the door, shot him dead.
Leaked photos
This user’s life was turned upside down after naked photos of her were posted on the infamous website 4chan. By the time she wrote her story, 24,000 men had seen her photos. Her Facebook inbox was filled with soliciting messages from men she never knew. Some of them physically went to see her at the address posted by the 4chan doxxer.
Instagram influencers
What happens if you take a stand against a popular Instagram page that posts sexist content? Quite a lot, as this journalist would find out.
Stef wrote a series of critical comments on the photos from a famous Instagram account. Her comments touched a nerve, so the admins retaliated by publicly revealing her name, her partner’s name, her telephone number, and address, with an explicit instruction to harass Stef.
The fans duly followed the instructions and insulted Stef with racist comments, unearthed some of her business ventures as well as threatening to reveal her Social Security Number.
The harassment eventually died out, but only after Stef went through complicated legal hoops and issued DMCA takedown notices.

Doxing methods
Cybercriminals and trolls can be very resourceful in how they doxx you. They can use a single clue, and then follow it up until they slowly unravel your online persona and reveal your identity.
Here’s what you should look out for if you want to stay anonymous on the web.
1. Revealing your identity through the information you post
The more you write on forums and message boards, the higher your chances become of accidentally revealing personal information about you. If you use social media, it’s even more dangerous.
You don’t even have to outright say where you live. Instead, it’s possible to roughly pinpoint your location by way of elimination.
For instance, you make a post saying you don’t live in the Americas. In another you said you wanted to visit a different continent, so you chose Asia.
With only two posts, the cybercriminal made an educated guess you most likely lived in Europe.
In another post, you said Walmart isn’t present in your country, but that Carrefour is the dominant retail chain.
By now, your possible location has been narrowed down to 3-4 countries.
As the doxxer keeps sifting through your information, he slowly figures out what country you live in, and even your current city.
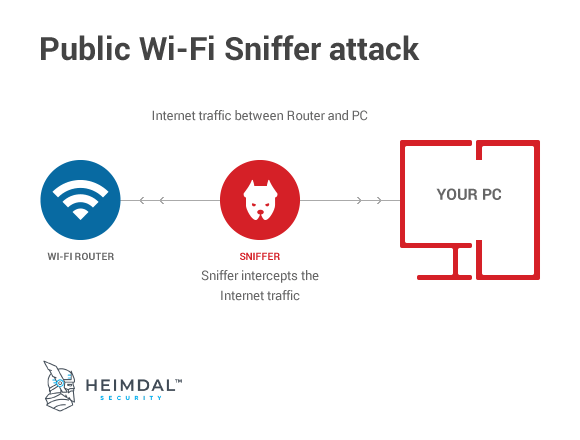
2. Packet sniffing
Packet sniffing is a hacking method where the doxxer intercepts your Internet data, looking for valuable information about you, such as emails, passwords, credit card data and so on.
Basically, the doxxer connects to a network, such as a Wi-Fi, breaks its security measures and after that, he intercepts all of the data coming in and out of the network.
What’s more, the malicious hacker has access to this data in real-time, so everything you type in a form will simultaneously show up on his screen.
Here’s a more thorough guide on how you can protect yourself from wireless sniffing.
3. Matching information between an online persona and social media profile
Ross Ulbricht was the founder of the infamous darknet website Silk Road, which traded drugs, guns and so on.
To hide his identity, he used the nickname “Dread Pirate Roberts”.
The police was able to connect Ross Ulbricht and Dread Pirate Roberts partly because both of these “personas” said they were a) libertarians b) followers of the Mises Institute c) both of them wanted to create “an economic simulation of what it would be like to live in a world without systemic use of force”.
During the trial, Ross Ulbricht built his defense claiming he gave away the Dread Pirate Roberts account, and someone else made Silk Road the Internet’s hot spot for illicit trade.
As far as coincidences go, this was a bit too much to believe. The judge threw out the defense and sentenced Ross Ulbricht to a long time in jail.
4. Doxxers analyze file metadata
Microsoft Office files such as Word or Excel documents have something called “metadata”.
This is information about the document, which you can find by right-clicking a Microsoft Office file -> Properties -> Details
This section contains data about who made the file, when, from what computer, the company who made it and even total editing time.
Simply by glancing over this metadata, a doxxer can learn a great deal about you. Here’s a guide by Microsoft on how to limit the amount of metadata you share with a document.
But it’s not just Microsoft Office files that remember metadata, even photos have something similar called EXIF data. This contains data regarding camera or smartphone model, resolution, location (if you enabled GPS) and time when it was taken.
5. Doxxing through IP logging
IP loggers are tools used on the Internet to sniff out a person’s IP address. In a nutshell, these loggers attach an invisible code to a message or email, and once the receiver opens the message, the code tracks his IP address and secretly sends it back to the IP logger.
Doxxing prevention
1. Protect your IP address with a VPN/Proxy
VPN is short for Virtual Private Network, and acts as a filter for Internet traffic. Basically, the traffic from your PC or other device goes into the VPN and acquires its identifying properties, meaning its IP address, location, and any other similar data. It even encrypts your data and makes it so that even your ISP isn’t able to figure out your IP address.
An IP logger, for instance, wouldn’t reveal your real personal IP, but the IP of the VPN.
A proxy server is a bit different than a VPN, even though it works on roughly the same principles. For one, a proxy server doesn’t encrypt your data as a VPN does, so an ISP knows your real IP address at all times. Since your Internet traffic isn’t encrypted, it’s also more vulnerable to hacking and other interception methods.
2. Don’t use the Login with Facebook/Google buttons
Most apps and websites that require you to register now use the “Login with Facebook” or “Login with Google” buttons.
These login methods register you on the website by using the email you used to create your Facebook or Google account.
But on top of that, you will automatically give the website information attached your Facebook/Google account, such as current city, job, phone number, your native language, family info and more.
Sure, it’s not as convenient, but by introducing your data manually, you can control the type of information the website has about you.
It’s especially critical to follow Facebook security best practices, to secure all of your social media accounts, including Instagram, and to be aware of how cybercriminals hack Facebook, Instagram, and Snapchat passwords.
3. Don’t use your personal email to register on forums or other similar websites.
Chances are your main email goes something like this: [firstname][lastname]@gmail.com/yahoo.com/outlook.com.
It’s a simple, professional-looking combination. However, it immediately gives away your identity if someone learns it.
In most cases, forums have weak security measures so malicious hackers can break into them and then leak the emails used to register the accounts.
But if the website publicly displays user emails, then all an attacker needs to do is to simply check out your user profile.
So as takeaway advice, use a different email than your main one when registering on forums or message boards.
4. Hide your personal data from a website’s WHOIS.
Owning a blog or website requires that you register the Internet domain with some personal information. This information is then stored in a database called WHOIS.
The problem is that this database is public, meaning everyone can see the information used to register a website, including addresses, phone numbers and so on.
However, by paying a small fee, you can hide some of your personal information from the public search.
To edit your information, simply go to your domain registrar and see what options they provide for you to make your WHOIS information private.
5. Remove yourself from data broker websites
Some websites function as a sort of Yellow Pages. They mine the Internet for data and gather it all in one place. This can include an address, social media profile, photos, phone number, email.
If you find this hard to believe, then simply check out http://www.peoplefinder.com or www.whitepages.com. We warn you though, the amount of information stored in this sort of database can be downright creepy.
Fortunately, most of these companies offer a way for you to opt-out and remove any information they have about you. Unfortunately, this is bad for business, so they make it as difficult and time-consuming as possible.
The service we previously recommended, DeleteMe, cleans up all this information for you, so you don’t have to. As soon as the European General Data Protection Regulation kicks in, companies will be forced to make it easier for you to delete your information. Until that happens, you have to rely on this guide to avoid getting doxxed.
6. Make sure Google doesn’t have any personal information about you
This can be a pretty tough undertaking since you would have to go up against one of the world’s biggest corporations.
Simply google your name, and see if you’ve revealed who you are on internet forums, Reddit, niche social networks, messaging boards or any other similar websites.
Delete any information you find, including the accounts if they aren’t valuable to you anymore. If you don’t have access, ask the web administrator to do it for you.
Just how much info does Google have on you? Check out your Google History by typing https://myactivity.google.com/myactivity in your browser when logged in to a Google account. Google knows your location as well – you can find your personal Google map with all the places you visited at the https://www.google.com/maps/timeline URL.
Moreover, secure any account you have with Google by following the rules outlined in the ultimate cybersecurity guide. Make sure you follow the password security best practices. Lastly, don’t reveal too much about yourself when using your smartphone. You need to check your app permissions and follow close the smartphone security guide.
You can also check out DeleteMe, a service that removes your personal data from the Internet.
7. Knowing your rights
If you live within the EU or Argentina, then you benefit from a so-called “right to be forgotten”. This allows you to petition a search engine to remove search results concerning you.
The legal options available in the United States are more limited, but Google for one does offer an option for you to remove content about you.
Conclusion
Reading this, you might say you’re safe from doxxing because you don’t have anything to hide. Is that really true?
We’re not implying that you might do anything immoral or illegal,. We’re saying everyone has some aspects of their lives that they would rather keep private. Those aspects may be harmless but they should remain private. They can range from hiding a surprise or a possibly insensitive comment from your spouse to keeping a political opinion from your coworkers and so on. Everyone has something they want to keep for themselves or share with a specific community.
Moreover, there are a lot of angry people on the internet who rely on doxxing to “win” an argument. Any seemingly innocuous comment of yours has the potential to draw the anger of an internet mob.
Avoid getting doxxed. Follow the steps outlined in this anti-doxxing guide to stay safe and anonymous. For an added layer of security, here’s a guide to online privacy you can implement in under 1 hour.
Have you ever had to deal with a fake social media profile? If yes, tell us your story in the comments and also what you’ve learned from the whole thing.
This article was initially published on February 2, 2017, by Paul Cucu and was updated on January 3, 2018 by Ana Dascalescu.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security