Contents:
Passwords are the keys to the digital kingdom. Even Mark Zuckerberg, Facebook’s CEO, has to log into his master account by typing one. That’s why malicious hackers pour a huge amount of time and money into hacking other people’s passwords and breaking into their accounts. And we assure you that their efforts don’t go unrewarded. In this article, you’ll explore how cybercriminals hack passwords for social media accounts such as Facebook, Instagram and Snapchat. Once you “know thy enemy” we will go over some basic steps you can follow to dodge those attack methods.
How to hack your Instagram or Snapchat account password using a keylogger
Keyloggers are malware programs designed to record everything you type on your keyboard. They’ve been around since forever, and are one of the biggest targets of antivirus programs. Unfortunately, they can be incredibly effective at finding out passwords, email accounts, credit card data and any other type of information, so malicious hackers will surely use them more in the future. The tricky part about keyloggers is that a malicious hacker has to find a way to download it onto your device. Here are just a few of the most commonly used strategies:
- Send you a phishing email with a malicious attachment, meaning the keylogger.
- Infect a website with malicious code so that it automatically downloads malicious software on your device, these are so called “drive-by-downloads”.
- Trick you into clicking a malicious link on a pop-up or website that approves a malicious download.
 Keyloggers come with many different functionalities. The main one of course is to track and record keystrokes, and then send the information back to the malicious hacker. This is how they can hack a Facebook or Instagram account password with ease. On top of that, some keyloggers can even do some or all of the following:
Keyloggers come with many different functionalities. The main one of course is to track and record keystrokes, and then send the information back to the malicious hacker. This is how they can hack a Facebook or Instagram account password with ease. On top of that, some keyloggers can even do some or all of the following:
- Take screenshots of the device.
- Track the URL’s of pages you visit.
- Record what applications you run on your device.
- Capture copies of emails in your inbox and sentbox.
- Log all of your messaging sessions, such as FB Messenger or Snapchat.
Keyloggers are designed to be invisible and difficult to track down. Chances are you can’t even find the process for it in Windows Task Manager. If you want to remove a keylogger, then you’ll need some specialized software and follow certain steps. Better yet, if you want to prevent someone downloading a keylogger on your device, we recommend you use software specifically designed to block malware from entering your device in the first place. In our opinion, our own Heimdal™ Threat Prevention can go a long way in helping you filter out the bad traffic out there.
Phishing attacks will trick you into revealing the password
Phishing is a favorite tool for cybercriminals to get a hold of your password. The bad guys will first send you a fake email that supposedly comes from a trusted website you use, such as Gmail or Yahoo. This email looks nearly identical to the real deal, and has a link inside that leads to a “Sign In” page. 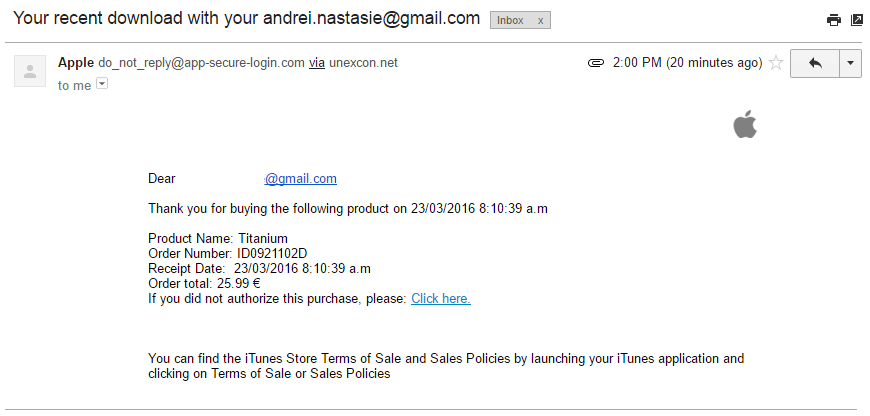 The mail might say something along the line of “Due to some security issues, we request you enter your account details again to confirm it is really you.” But you won’t really be logged in to the website. Instead, you just typed in your account and password for the malicious hacker to see. In other words, you helped him hack your Facebook or Instagram password.
The mail might say something along the line of “Due to some security issues, we request you enter your account details again to confirm it is really you.” But you won’t really be logged in to the website. Instead, you just typed in your account and password for the malicious hacker to see. In other words, you helped him hack your Facebook or Instagram password.
Steps to follow to prevent a phishing email attack
It takes little effort to detect a phishing email. The hard part is to develop a mindset that everything on the Internet is harmful until proven otherwise. With that being said, here are some basic tips to protect yourself from these nasty phishing campaigns. 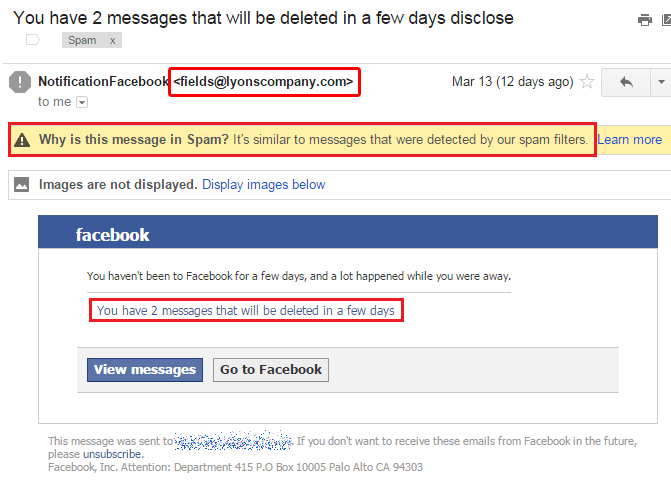 Source
Source
- The sender’s address is the first major clue the email is fake. It makes no sense for Facebook to use any other email address other than “@facebook.com”. However, it’s also possible the malicious hacker might be skilled enough to spoof the email address. Or he might have bought a web address similar to facebook.com. In this case, it’s not unheard off to have an email that looks something like this: support@facebookmail.com or xwsegsy@facebooksupport.com, both of which are fake.
- It’s safe to assume an email in the spam folder is a dangerous one you shouldn’t click. At all. In fact, don’t even open it. Or better yet, don’t even look into your spam folder. You don’t need to. Leave the garbage alone, undisturbed.
- “You have 2 messages that will be deleted in a few days”. When was the last time you saw Facebook do that? Hint: never. That text is a standard psychological tactic employed by cybercriminals to create urgency in your mind, and force you to click the link.
How cybercriminals use Wi-Fi sniffers to hack your Snapchat and Instagram password.
There are around 300,000 YouTube videos on how to hack a Wi-Fi password. Cybercriminals however, aren’t interested in free Internet, but instead they want to get their hands on the data you send and receive over the network. Once a malicious hacker breaks into a Wi-Fi network, then he can easily start hacking your Facebook or Snapchat password by intercepting all of the data you communicate over the network. Of course, this isn’t just limited to passwords. The cybercriminal will also target private information such as credit card data, addresses, date of birth, social security, emails and Internet messages. Unfortunately, it’s nearly impossible to detect a Wi-Fi sniffer attack, so you just have to avoid as best as you can. Here are some basic tips you can follow to prevent someone from hacking your Wi-Fi and personal data.
- If it’s your own Wi-Fi network, make sure it has a strong password that can’t be broken by a dictionary or brute force attack (more on these attacks later).
- Make sure your router uses the WPA2 AES encryptions method. Out of all the encryption methods out there, this one is the most secure. Even governments use the AES encryptions standard.
- If it’s a public network, such as coffee shops or shopping malls, make sure it too is also encrypted with WPA2 AES. Here’s a more in-depth article as to why u>public Wi-Fi’s are such a cybersecurity hazard.
- If the public Wi-Fi is open or uses the ancient and obsolete WEP encryption method, then avoid it altogether. Whatever you do, do not use an open wireless network to log in to your Facebook or Instagram account, do financial transactions or any other sensitive operation.
Password hacking software
The most frequent cybersecurity advice you’ll ever hear is “use a strong password”. And there’s a very good reason for this. Far too many people use weak passwords for their social media account such as: 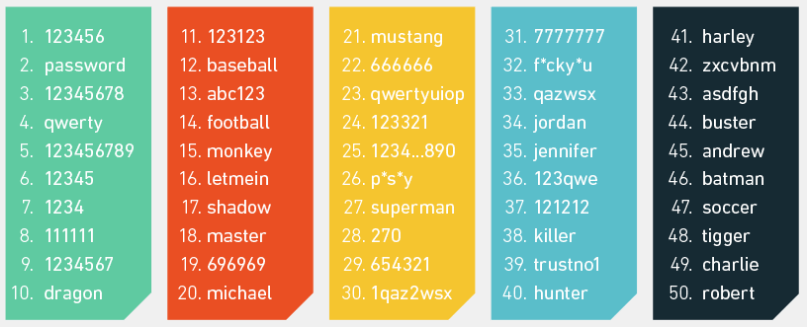 Source. As we’ll see, even basic hacking software will guess these weak attempts almost instantly.
Source. As we’ll see, even basic hacking software will guess these weak attempts almost instantly.
Brute force attacks
These sort of weak passwords are vulnerable to a so-called brute force attack. This is a password hacking method that bombards a login page with thousands upon thousands of passwords until it gets the right one and logs into your account. Passwords such as “123456” are among the first to be tried out, so they are cracked in around 0.2 seconds. In other words, a brute force attack can hack a weak Facebook password instantly. [Tweet “It takes just a few seconds to crack a 6 character password.”] Here’s how long it will take a brute force attack to hack any of these passwords:
- London = 6 seconds.
- Londoner = 5 hours, 13 minutes.
- Londoner- = 2 years, 4 months.
- Londonerse = 1 year, 7 months
- Londoner-* = 198 years, 26 days.
- londoner-* = 1 month, 6 days.
Source As you can see, it’s not just the number of characters in a password that matters, but also what type of characters you use. “Londoner-“ is shorter than “Londonerse” but it’s harder to crack thanks to the special character “-“. It’s not just special characters that make a difference. Capitalizing a letter can turn a junk password such as “londoner-*” into a heavyweight that takes nearly 2 centuries to crack. And all you did was to capitalize the “l” so it’s now “Londoner-*”.
Dictionary attacks
Dictionary attacks rely on guessing a password just like brute-force ones. The main difference is that dictionary attacks first try out the most likely password variations, and then work from there. To come back to our previous example, if the cybercriminal knows you are a huge fan of the city of London (so much so that you have a tattoo of the Queen on your arm), then he will set the software to first try out all combinations related to the word “London”, such as “london134” or “london88%”. So the hacking time of “Londoner-*” will go down from nearly 2 centuries to just a few hours or days at most. The more information an attacker knows about you, the higher his chances of hacking your password.
How malicious hackers use brute force/dictionary attacks
Brute force and dictionary attacks cannot be directly used to hack to your Facebook or Snapchat password since these are highly secure websites that use extensive security measures to prevent this type of attacks. Instead, malicious hackers exploit another common Internet user mistake: reusing the same password. A smart cybercriminal will simply target other sites and services the victim uses. Some of these will surely have weak security measures that allow the hacker to launch a brute force attack on the login page. If the attack is successful, then it’s safe to assume the cybercriminal can hack into the victim’s other accounts, including the ones made at banks or shopping sites. 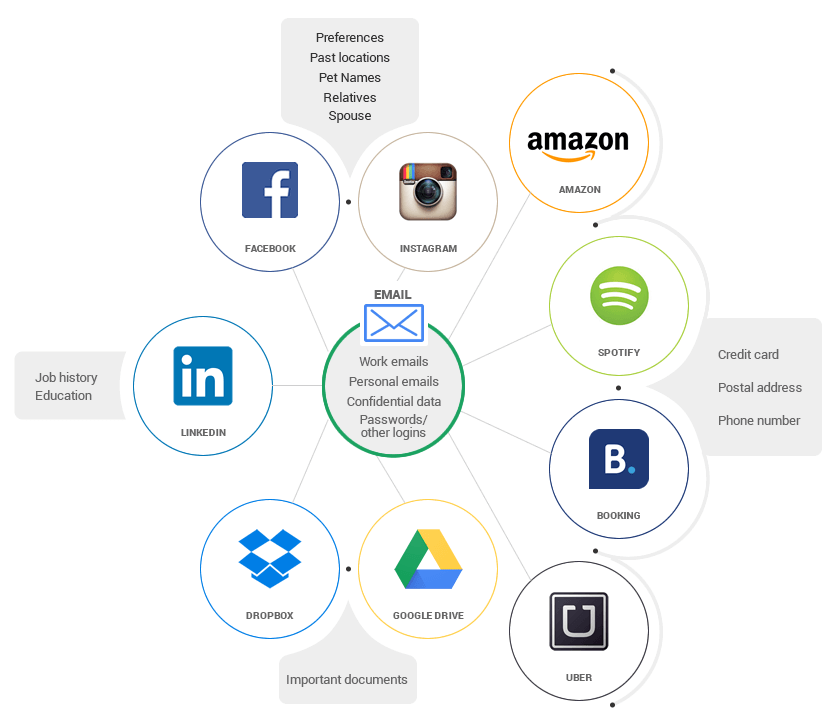 All because he used the same password over and over again.
All because he used the same password over and over again.
How to prevent a dictionary/brute force hacking attack
Thankfully, it’s easy to protect yourself against a password-guessing attack. Here are some basic tips you should when it comes to managing your password:
- Make sure you have a strong password. This means you should include a capital letter, a number and a special character. Make sure it’s at least 10 characters long.
- Don’t reuse the same password for all of your accounts. To cut down on the amount of effort involved in remembering and creating such passwords, we strongly recommend you use a password manager such as Dashlane and LastPass.
- Make sure your passwords are as unpredictable as possible. Don’t let the attacker guess the “theme” of your password, like in our “Londoner-*” example. In fact, make sure your password is as random as possible such as “27fj30dr8&)*LL”.
- Activate two-factor authentication to prevent an attacker from logging into your account, even if he guesses your passwords.
Social engineering attempts that request your login information (and password)
Like phishing emails, social engineering scams tries to trick you into willingly revealing your data. What’s more, these types of attacks are becoming more and more frequent. For instance, the cybercriminal might pretend to be an employee for the main bank you use. He then calls you in order to “clarify some minor account issues”. During the phone call, he asks that you provide him the username and password for your bank account. You’d be surprised how often people get hacked with this type of trick. It doesn’t even have to be a bank employee. They might pretend to be a utility company, asking you to give them username and password so they can recover your “lost account”. Since most victims reuse the same password, the bad guys now have access to all their other accounts as well, even the more important ones, on sites such as eBay or Amazon.
Shoulder surfing, the low tech method to hack someone’s Facebook or Instagram password
Sometimes, the best way to hack someone’s password is to physically see him type it. There’s even a word for it: shoulder surfing. Thanks to the smartphone era, this practice has become more widespread, with people looking over your shoulder to find out not just your Facebook or Instagram password, but other types of personal information, such as browsing sessions or messenger conversations. The last thing you need is for a thief to see you talking about your next vacation. If he’s a good one, he can track down your home address and burglarize you. To prevent shoulder surfing, Android users should keep the “Make Password Visible” field turned off (you can find this in Settings -> Security). iOS users don’t have to worry about this since it’s a default setting and you can’t change it. However, some apps will briefly flash the last character you typed. So you will see something like this if you want to write in Londoner-*: “****o”. A keen eyed observer can remember those taps, and reconstruct your password. [Tweet “Cybercriminals will look into your smartphone to learn your passwords.”] Another possible fix for this, is to use a privacy screen protector that makes the screen harder to see for others.
Technical attacks that have nothing to do with the user.
Some passwords are hacked due to technical issues related to the website or service, and without any fault on the user’s part. In such situations, the security minded user can only the website is properly secured.
Hash attacks
Computers don’t store your password in plaintext, meaning you will never find a file on a PC with a password written down letter by letter. Instead, the password will be hashed. So instead of “Londoner-*” the password will look something like this: 5206b8b8a996cf5320cb12ca91c7b790fba9f030408efe83ebb83548dc3007bd. That long string of random gibberish is called a hash. A malicious hacker can obtain the hash file through a malware attack on the device that stores the hash, such as a server or your PC. To decrypt the hash, the cybercriminal will use several methods such as: lookup tables, rainbow tables and reverse lookup tables.
OAuth attacks
Most online login and authentication methods rely on a technology framework called OAuth 2. What this technology does is to bypass the need to create a new user account and password for a website, and just login with a predetermined account. You’re probably familiar with this technology if you’ve used the “Login with Facebook” or “Login with Google” buttons. Basically, Facebook or Google will send an identification token to the website you want to log in, confirming your identity. However, many websites and apps poorly implement OAuth, so instead of actually receiving the token from Google or Facebook, they just check if the provider of the information is Google or Facebook. In other words, they log you in the account without a confirmation that it’s actually you. A malicious hacker with good technical knowledge can disguise the token provider, so he fools the login page into believing the user is genuine, and then gives him access. Unfortunately, a huge amount of apps and websites don’t implement OAuth properly. By some estimates, such poorly secured apps account for nearly 2.4 billion downloads all over the world, putting a huge amount of users at risk. To avoid any potential problems, we recommend you create separate usernames and password and even avoid using the “Login with Facebook/Google” button altogether.
Conclusion
A safe and secure password is the first and most important step in keeping your online life secure. Steps such as long passwords, two factor authentication and password managers are a very small inconvenience compared to the security boosts they can provide you.

INSTALL IT, FORGET IT AND BE PROTECTED
Download Heimdal™ FREE

 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









