Contents:
You must have heard it on the news: “Country X accuses country Y for launching a cyberattack against its infrastructure” or “Huge leak at Corporation X, account information of millions of users leak”. Sometimes, you don’t even need to hear it on the news, but instead, it is right there, plastered all over your computer screen: “Your information has been encrypted, and the only way to recover it is to pay us”. All of these are cyber attacks.
What is a cyber attack?
Cyber attacks are malicious Internet operations launched mostly by criminal organizations looking to steal money, financial data, and intellectual property, or simply disrupt the operations of a certain company. Countries also get involved in so-called state-sponsored cyberattacks, where they seek to learn classified information on a geopolitical rival, or simply to “send a message”. The global cost of cybercrime in 2015 was $500 billion. That’s 5 times Google’s yearly cash flow of 90$ billion dollars. And that number is set to grow tremendously, to around 2 trillion dollars by 2019. In this article, we want to explore the types of attacks used by cybercriminals to drive up such a huge figure, and also help you understand how they work and affect you.
Quick links for navigation
- Cyber fraud
- Malware attacks
- Social Engineering Attacks
- Technical attacks
- Vulnerability Exploitation
- Login Attacks
- Malicious content
- Groups that launch cyber attacks
Cyber fraud
Phishing attacks
During a standard phishing attack, a malicious hacker tries to trick the victim into believing he is trustworthy, for the user to do a certain action. The most famous of these is the “Nigerian prince” scam. In case you haven’t heard of it, the malicious hacker claims to be a wealthy Nigerian who requires your help in transferring tens of millions of dollars out of his home country. As a reward for your service, the “prince” will send you a hefty sum of money. All you have to do is provide him with some personal information (we’ll explain why they need this info later on) and a small fee to process the money transfer, and you’re rich for life! Of course, it’s all a scam. There is no Nigerian prince or tens of millions of dollars. The only real money in the scheme is the “processing fee” you provide. Unfortunately, the return policy for malicious hackers can be summed up like this:  Malicious hackers send out thousands, or even hundreds of thousands of phishing emails in order to maximize the number of infected users. [Tweet “Read more about the Nigerian phishing scam and others like it”]
Malicious hackers send out thousands, or even hundreds of thousands of phishing emails in order to maximize the number of infected users. [Tweet “Read more about the Nigerian phishing scam and others like it”]
Spear phishing attacks
Regular phishing attacks are massive spam campaigns, where the malicious hacker hopes that as many people as possible click the link/install the attachment. Spear phishing on the other hand is much more targeted. It involves personalizing the phishing email around the receiver. Here are some examples:
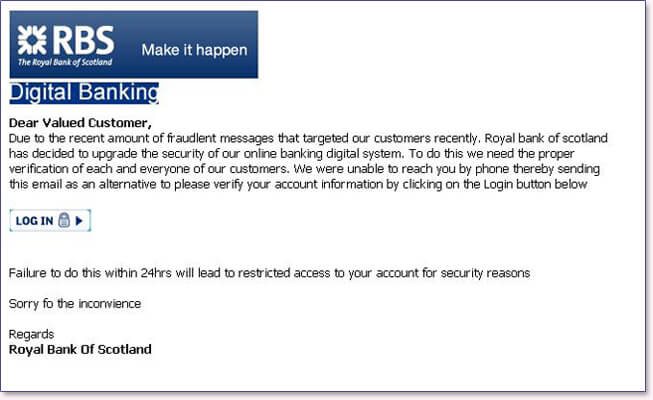
- The phishing email is designed to look like it came from a bank (or another type of trusted entity). Due to some technical issues or any other reason, they ask you to reenter your login information for your bank account. But the form you type in the login info belongs to the malicious hacker, who can now clean your bank account.
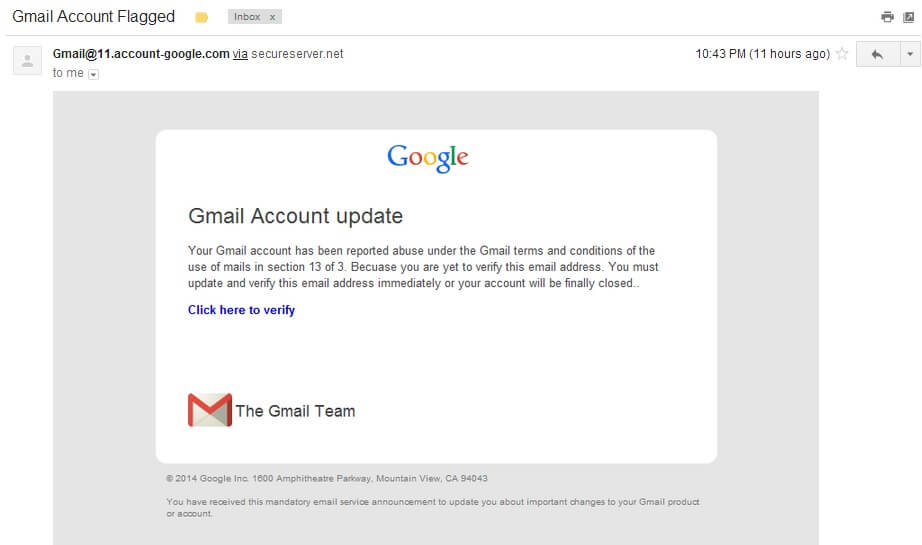
- You get a fake email disguised as a Gmail/Yahoo/Outlook email, which requires you to reenter your login information to confirm “it’s really you”. Some cheeky cybercriminals might even say someone else tried to log in to your account. This is the method used for one of the most high-profile hackings of recent years.
- A fake email from a manager/CEO about important company files. In such cases, the spear-phishing email will contain a malware-infected Excel/Word file that once opened will unleash a malware attack on your PC. In these cases, the hacker is more interested in the company’s data, not your own (that’s why it’s called CEO fraud).
Unauthorized disclosure
This happens whenever a company or organization discloses personal information about you, without asking for your authorization. This happens for instance when a medical provider leaks your personal health information.
Whaling
Whaling is a more refined version of phishing. This time around, a malicious hacker targets a specific, high-value person, such as the CEO of a company or a high-ranking politician. In orde,r to carry out a whaling attack, the malicious hacker gathers as much information about the target as possible, such as details about friends, occupation, passions, hobbies and so on, just so the victim has a higher chance of clicking the link or opening the attachment. Whaling is a niche pursuit for cybercriminals, but a highly profitable one. Companies lost nearly 2.3 billion dollars in a 3 year period due to whaling attacks targeting CEO’s.
Malware attacks and infections
Most frequently, malware attacks are delivered as malicious attachments to a phishing email or through downloads on suspicious spam websites. The infection takes place the moment you open up the attachment to see what it’s really about. In other, rarer instances, it’s possible for the malware to be downloaded on your PC without you even approving of it. These are called drive-by-downloads and are worth their own, separate discussion. 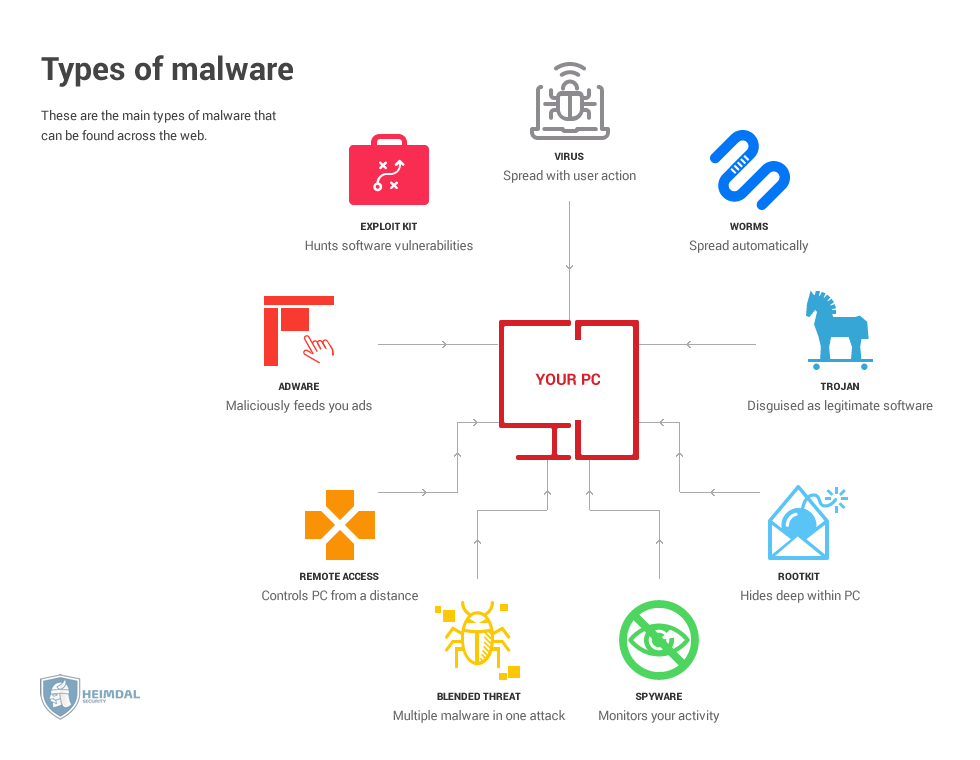 [Tweet “What are the types of malware out there and how do they work?”]
[Tweet “What are the types of malware out there and how do they work?”]
Spyware
Some types of malware try to stay as hidden as possible, while quietly collecting valuable information about you in the background. Online attackers use spyware to find out deeply personal information such as passwords, credit card data, and personal photos. Keyloggers, and form-grabbing malware are all included in this category. In order to remove them, you’ll usually require a good antivirus or malware removal software. Advertisers on the other hand, look for information related to your internet usage habits, such as location and search history, hobbies, interests in order to better target you with ads. Spyware from advertisers usually comes in free software such as browser toolbars, music programs, that come either stand-alone or bundled with another program. While not as bad as the first category, this type of spyware still limits your privacy and comes with vulnerabilities of their own. Fortunately, a simple uninstall should be sufficient to remove it from your computer.
Rootkits
Rootkits are malware that infects your PC on a deeper level, in order for them to be undetectable. Computers are structured in layers. A program can only modify other software from the same layer or above, but not from a deeper one since it doesn’t have access. For instance, a program like Excel, Photoshop or Word aren’t able to modify underlying software such as the software drivers for graphic cards or sound cards. The deepest layer is the BIOS, which controls a PC’s boot-up procedure and other software aspects. Rootkits usually target this access layer since an antivirus program has a very difficult time finding and removing the rootkit. Rootkits can enslave computers into a botnet, listen in on a user’s internet traffic, or make other types of malware undetectable. It’s safe to say they are the worst type of malware infection out there. 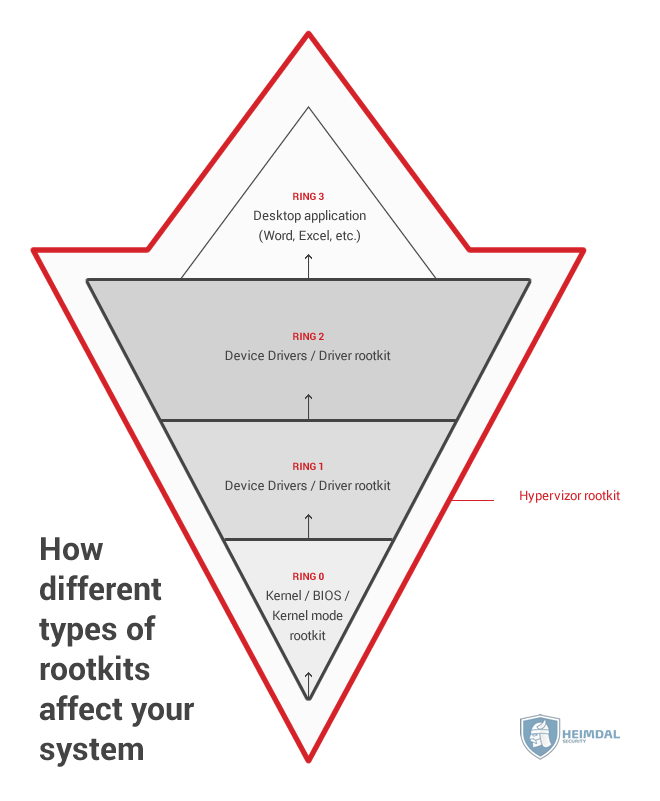
Malware virus
Most people think that virus = malware. But that’s not actually the case. A virus is a type of malware. In other words, all viruses are malware, but not all malware are viruses. A virus is a type of malware that can spread and infect other computers, hence the name virus. A single computer can spread a virus in a whole network, usually by infecting other files that are then shared to the rest of the network.
Trojan horse malware
Named after the famed wooden horse used to conquer Troy, Trojan malware infects your PC by making you think they are a completely different sort of program. For instance, the program might claim to be antivirus software but is actually a keylogger or spyware in disguise.
Drive-by-downloads
Most of the times, you need to authorize a download before it commences on your PC. Drive-by-downloads are different since these files automatically save themselves on your computer after you’ve visited a website. Drive-by-downloads are possible thanks to modern software such as JavaScript and that allow an attacker to bypass regular safety measures. Most often, these types of cyberattacks happen after a cybercriminal manages to redirect you to an infected website. Most of the times, the site is his own, but because software is imperfect, he can even infect legitimate big websites. Believe it or not, but news websites are actually more vulnerable than porn sites. According to the study in the link, in 2016 there were 22,000 thousand vulnerable news websites, compared to 18,000 thousand porn sites. 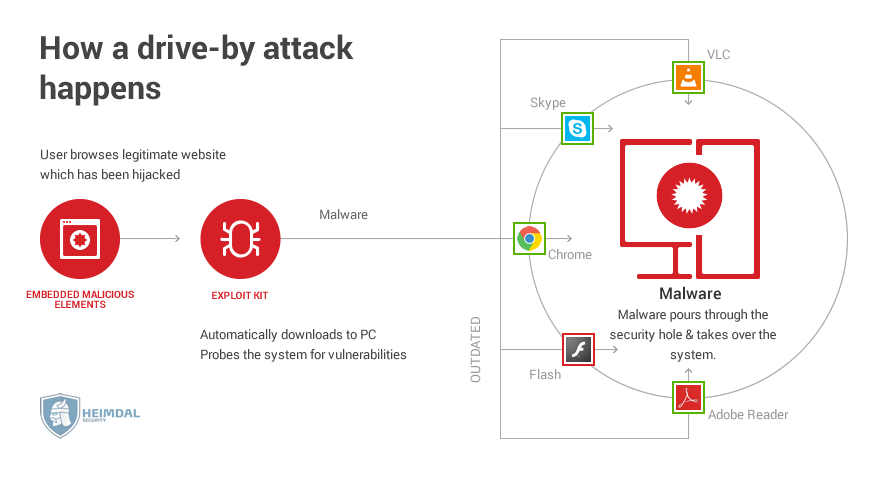
Ransomware
The most widespread types of ransomware encrypt all or some of the data on your PC, and then asks for a large payment (the ransom) in order to restore access to your data. This type of malware has experienced a wild surge in popularity, in large part thanks to anonymous cryptocurrencies, such as Bitcoin.  Source
Source
Botnet
A botnet is a network of infected computers that are enslaved to a single command & control center. The computers in a botnet act in unison, so that they all do the same thin simultaneously. Malicious hackers use botnets for some of the nefarious cybercrimes out there, such as DDoS attacks, mass farming for Bitcoin or for gathering user data.
Time bombs and logic bombs
Time bombs and logic bombs are malicious code hidden within programs or network systems. They activate and launch a malware attack either at a certain time, in case of time bombs, or when certain conditions are met, in case of logic bombs. Attackers use logic bombs in multiple ways, such as deleting databases, preventing the deletion of corrupted code, or sending valuable information about the victim back to the malicious hacker.
Blended threat
Blended threats are attacks that combine two or more malware in order to maximize their efficiency. Blended threats combine Internet worms with viruses, keyloggers, ransomware, Trojans and any other type of malware in order to improve the spread and amount of damage inflicted.
Internet worm
Worms are malware designed to self-replicate and spread on the Internet using network connections without any human interference. Unlike a computer virus, worms don’t need a host program. They are standalone pieces of software. One of the most famous worms out there was developed way back in 2005 and targeted MySpace. Nicknamed the “Samy worm” after its creator, it managed to gather 1 million friend requests for Samy within a day.
Remote Access Trojan
Remote Access Trojans, or RAT’s for short, are Trojan malware that give an attacker administrative control over the infected computer. Once a RAT installs itself, the cybercriminal can control the PC remotely, allowing him to install keyloggers, form grabbing malware, activate the webcam, format drives, create a botnet and pretty much anything else you can think of.
Exploit kit
An exploit kit hides in a web page/server and looks for vulnerabilities in your PC. It does this by analyzing the traffic sent between your PC and the web page. After it finds a vulnerability, the exploit will launch a targeted attack against it, using either malware or any other exploit method. Particularly vulnerable applications are those that communicate with the Internet, such as Flash, Chrome, Firefox, Apple Quicktime and so on.
Adware
This is malicious software used to feed you ads and track your online behavior in order to improve how advertisers can target you. Oftentimes, adware comes attached to free programs such as music players or other comparable software.
Social engineering attacks
Social engineering attacks are those in which the cybercriminal actively makes contact with you, by pretending to be someone else, and manipulating you into revealing your data.
Vishing
Short for “voice phishing”, in this sort of engineering attack, a scammer will call you either over the phone or Internet voice apps such as Skype. The pretext varies, but in almost all cases, the scammer is after your money. He can pose as a bank clerk, asking you to reconfirm your personal data, or it can be an employment agency asking you for an advance. In one of the more insidious cases of vishing we’ve heard of, the scammer might pretend to hold a loved one hostage, and claim to harm them if you won’t pay a ransom. 
Smishing
Phishing done over SMS/text messages. Like most phishing attacks, smishing targets your financial data, by pretending to come from a trusted source such as a bank. Passwords, credit card details, email accounts are all viable smishing targets. 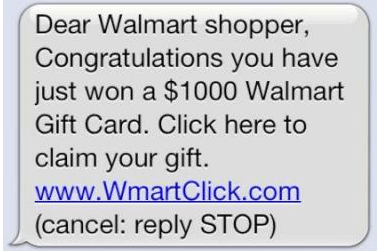
![]()
Customer support scams
A popular scam that attackers use against tech users who aren’t familiar with more advanced technical concepts. The scammer will pose as a customer support representative, and claim that your software or hardware has technical issues that need urgent fixing, otherwise he might risk a catastrophic system failure. In exchange for the kind scammer’s expertise on how to fix the issue, you have to pay a decent sum. Of course, there never was any issue, and your money is lost forever.
Catfishing
Possibly the most romantic type of scam out there. Catfishing involves creating a fake online persona in order to trick people on dating sites to break-up with their money. The catfisher will stalk social media networks or dating sites, looking for emotionally vulnerable people seeking a relationship. The scammer seduces the victim, although the relationship is carried only over the phone or text. The two never meet, since the scammer claims he is from outside the state or country, on extended business trips or military tours. At some point, the scammer brings up an urgent problem that requires a sum of money in order to resolve. The reasons vary from story to story. Some might say they need money in order to obtain a visa to join the victim in their home country, in other cases, they claim they have a large amount of gold stuck in customs that requires a fee in order to allow passage into the country. Of course, the stories are all fake. The victim gets their heartbroken, and also lose their money. 
Dumpster diving
The (literally) dirtiest form of social engineering attacks. Dumpster diving involves digging through your actual trash in order to find valuable information about you, such as credit card data, social security numbers, phone numbers, email addresses, passwords (for people who actually write down theirs on paper). That’s why a shredder is good to have in any home.
Technical attacks
These types of attacks often target cyber infrastructure such as databases, DNS, outdated software and similar techniques.
Malvertising
Malvertising is the practice of spreading malware through online ads. The attacker can either infect an already existing legitimate ad with malicious code, or he might put up his own infected one. Malvertising is very advantageous for a malicious hacker, since he doesn’t need to worry how to spread the malware. The ad network does all the hard work and exposes thousands or even millions of users to malware. On top of that, malvertising is difficult to detect, and can bypass firewalls and otherwise avoid various user safety measures.
DNS attacks
Normally, Internet pages are stored using numbers, not words. These numbers are called IP addresses. In order to make them easier to remember for humans, these IP addresses are translated into letters and names. The translation from IP addresses to names takes place on Domain Name Servers, shorted as DNS. The information is also stored there. During DNS hijacking, an online attacker will override your computer’s TCP/IP settings so that the DNS translation gets altered. For example, a typing in “cnn.com” will translate it into this IP: 157.166.226.26. A DNS hijacker however, will alter the translation so that “cnn.com” will now send you the IP address of a different website.
URL Injection
During a URL injection, a malicious hacker infects a website by creating new pages in it. These pages in turn contain malicious links, spammy words or even malicious code that forces visitors on the page to be part of a DDoS attack or redirects them to a different website. A malicious hacker can do a URL injection thanks to weaknesses in IT infrastructure, such as WordPress plugins or within any other type of HTML code.
Flooding attacks
Flooding describes the technique used in DDoS attacks, where an attacker sends a huge amount of information against a target, blocking it from processing any other information whatsoever. Depending on the attack vector they use, flooding attacks can be classified as follows: · User Datagram Protocols (UDP) flood. This UDP is in charge of sending so-called datagrams, meaning packets of information, between computers. · HTTP floods work by abusing the GET function of a website, which provides information to the browser, and the POST function, which creates content. The flood will force the server website to focus only on these functions, and divert processing power from all other aspects.
Passive attacks
Passive attacks look to acquire information about you, while limiting any other type of damage done to your system, so as to not raise any suspicion there might be something wrong with your PC. Here’s an example of a passive attack.
DoS/DDoS attacks
Short for (Distributed) Denial of Service, these sorts of cyber attacks seek to disrupt the Internet use of a user or service, by flooding its connection with useless information such as enormous amount of login attempts or excessive amount of traffic. Unlike a DoS attack, a DDoS relies on a large number of devices that can simultaneously assault the target, hence the name “Distributed” since the attacker’s resources are spread across many computers or other devices. Most cases involving DDoS attacks involve a botnet that has a sufficient amount of enslaved devices capable of launching a concerted attack. Here’s an example of a botnet attack that relies on millions of enslaved Internet of Thing devices. [Tweet “Here’s how a DDoS attack works”] 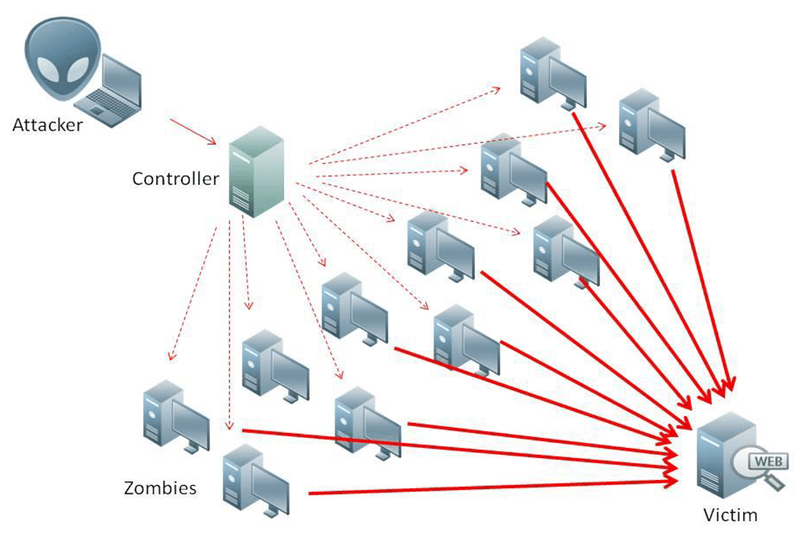
Web page defacing
As the name suggests, a malicious hacker or group will break into a website and change its visual appearance in order to send a message or warn the owner of the website. Some of the more high profile practitioners of web defacement is the Anonymous hacker group, who managed to break into the Islamic State’s website and replace it with Viagra ads. 
Internet sabotage
Cyber sabotage mostly concerns companies, corporations and nation-states rather than individual users. In most cases, the attacker or hacker group targets a vital part of the victim’s Internet infrastructure. One prime target, for instance, is a country’s electrical power grid or data regarding military installations. Probably the most famous and devastating type of cyber warfare sabotage was the Stuxnet worm that targeted Iran’s nuclear program. This worm was specifically designed to target Siemens centrifuges used to enrich uranium in Iranian nuclear power plants. By modifying the rotation patterns, Stuxnet was able to destroy a significant amount of centrifuges, and delay Iran’s nuclear program by several years.
Wi-Fi Sniffing
Snooping in on someone’s traffic is a technique malicious hackers use frequently in order to acquire data on their target. A prime target for sniffing is a wireless Internet router or Wi-Fi. Particularly vulnerable Wi-Fi are those that use a simple WEP or WPA encryption, instead of the standard WPA2. Brute-force/dictionary attacks easily break the password for WEP/WPA encryption, and using dedicated sniffing software or a hardware tool, the malicious hacker can basically see the traffic going through the router, or he might redirect all the traffic to his own, cloned Wi-Fi. Sniffing the traffic sent over a Wi-Fi gives the hacker a complete, real-time view of a user’s Internet activities. This exposes everything from passwords, email accounts and other similar types of information. Here’s a more in-depth guide on how to protect yourself from a public Wi-Fi attack.
Advanced Persistent Threats, a.k.a. APTs
Sometimes, a malicious hacker group wants to do more than just a hit and run attack. A long-term infiltration in the IT system of a government, corporation or even a high-value individual can provide a lot more information and control. These types of infiltrations are called Advanced Persistent Threats and are carried out using rootkits, Trojans, Zero-Day exploits. To successfully penetrate high-value targets, such as government or financial infrastructure, the malicious hackers might even develop their own, specialized malware.
Card skimming
A technique used to obtain the details of a person’s credit/debit card by using a specialized card reader. In most cases, the card reader is placed over a legitimate bank ATM or similar devices, and stores the magnetized data for each and every card it scans. Afterwards, the scammer imprints the magnetized data over blank cards. By then, it’s just a matter of emptying the victim’s bank account using his own credit/debit card data.
Man in the Middle attacks
Normally, Internet communication happens between two parties, meaning the sender and the receiver. During a Man-in-the-Middle attack, a malicious hacker places himself between your device and the website or app you’re communicating with. This then gives him access to both your inbound traffic, and the outbound traffic. In practice, this allows the malicious hacker to see everything you do on the Internet, such as passwords, browsing history, credit card details, email accounts. You name it. A pharming attack can target either an individual user with phishing emails or he might actually poison a DNS (domain name system) server. By poisoning a DNS system, the malicious hacker can redirect traffic from one or more addresses on the DNS server, to any other website of his choosing.
Pharming
An attack designed to harvest important data such as passwords, credit card data, emails and other such information. The attacker will first find a way to redirect traffic from a legitimate web page to a fake one he controls. If this fake web page contains any forms, then the victim will inadvertently fill out all of his private information. Pharming attacks target both individual users and DNS servers. When targeting users, malicious hackers send a phishing email that modifies a user’s files in order to redirect him from site A to site B. DNS attacks, or poisoning as they are known, targets the servers hosting a website’s DNS names. This allows a cybercriminal to redirect traffic from any website in the database to another website of his choosing.
Replay attacks
By reusing information sites use to identify you, a malicious hacker can fool a website or service into giving them access to your account. For example, in order to log in to a website using Facebook, the social network will send a string of information to the site in question in order to confirm that it is really you who wants to log in. If a malicious hacker could somehow find and reuse that string of information, he could theoretically use it to trick the site into thinking he was actually you, thus obtaining access to your account on that website.
Remote access
Remote access refers to any type of attack where the malicious hacker ends up taking control of your PC from a distance, by using his own separate PC. Remote access attacks are made possible by rootkits and types of malware which infected your PC in previous attacks. These then created a back door that allow the hacker to control your.
Spoofing attacks
During a spoofing attack, the malicious hacker tries to disguise himself as another user or Internet device, in order to trick the victim into relaxing their defenses. Spoofing has multiple variations, depending on the identification methods used: email, DNS or IP address spoofing. In an email spoofing, the attacker will forge the email in the “From” section to make it look like a genuine one you might receive from a boss or loved one. An IP address spoofing will create a fake Internet Protocol address which a computer will then use to hide the identity of his computer, or impersonate someone else’s PC. Here’s an interesting conversation on StackExchange which discusses the limitations of IP spoofing.
Vulnerability exploitation
Even the best software has its imperfections, and those are ruthlessly exploited by malicious hackers whenever possible. On a more fortunate note, software vulnerabilities are frequently patched by updates. For this reason, “update your software!!!11” is one of the most frequent types of cybersecurity advice, along “use a strong password!!!11” and “don’t click on that!!!11”
Buffer overflows
A buffer overflow takes place when a software or program tries to store more data than possible in a temporary storage space, known as a memory buffer. The excess data then spills over into other parts of the memory, overwriting the adjacent memory. A buffer overflow is frequently used to overwrite data in areas containing executable code. This replaces the existing code with a malicious one. If the attack is successful, the malicious hacker can then take complete control of the device.
Code injection
A frequently used malicious hacking technique in which the attacker exploits a vulnerability in the software in order to inject code in the program. This program then executes the code, producing the attacker’s desired result, such as shutting down the device, taking control of it or any other type of malicious intent.
Cross site scripting (XSS)
Also known as an XSS attack, cross site scripting requires a blackhat hacker inject malicious code into an otherwise trustworthy web page. Once a user does a certain action (such as leaving a comment), then the malicious code in the web page springs into action, infecting the user itself. A malicious hacker infects the web page by exploiting vulnerabilities in the page’s code or any web plugins that happed to be installed. 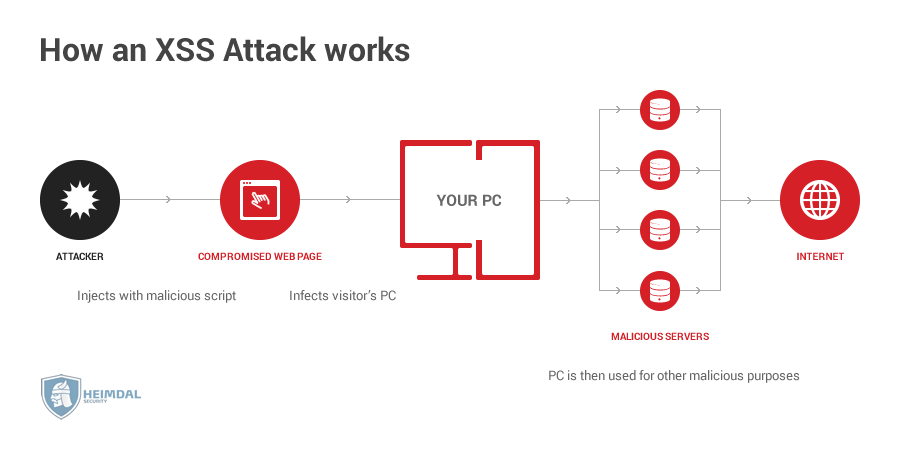
Zero-Day exploit
Zero-Day exploits are nightmare scenarios, where an attacker discovers an unpatched vulnerability in a piece of software (that even its maker doesn’t know about) and then proceeds to exploit it to the fullest. In order for a user to avoid a Zero-Day attack, he has to either avoid using the vulnerable program or wait for the developer to release a software update. For example, malicious hackers used a Zero-Day vulnerability in the Sony Entertainment hack a few years back. 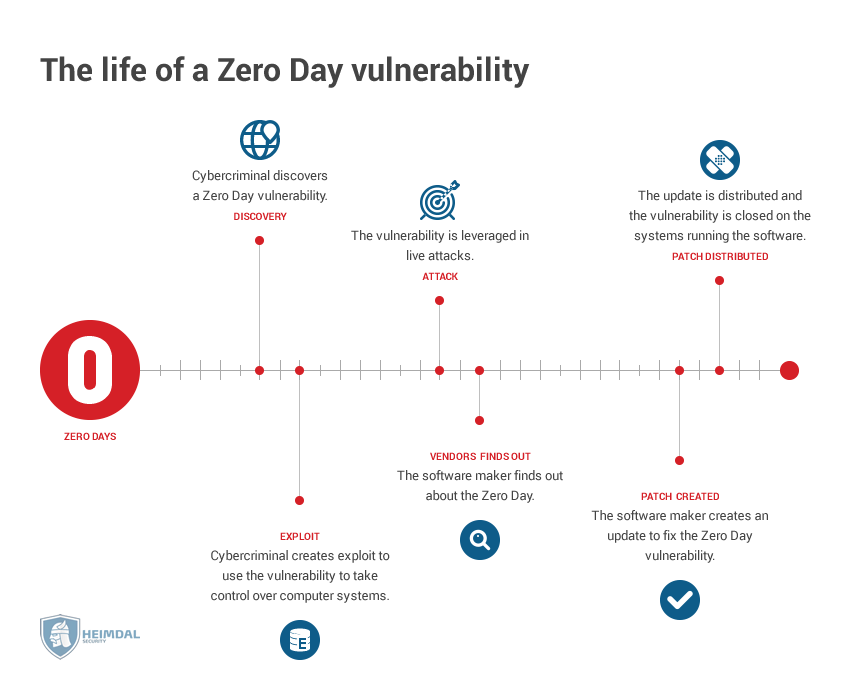
Browser hijacking
Instead of targeting websites and other types of infrastructure, browser hijackers go after individual users. By exploiting vulnerabilities in browsers, a malicious hacker can infect a user with adware, or redirect his traffic to a web page of his own choosing.
Time of check to time of use bugs
In order to do some particular things online, such as posting on Facebook, you need to go through a two-stage process. The first one is “time of check”. this means that Facebook must first verify if you are able to do said action. In most cases, verification means you must log into the social network. The second step is “time of use”, which, in our case, is the process of actually posting on Facebook. Time of check to time of use bugs allow a malicious hacker to somehow bypass “time of check” and go directly to “time of use”. Imagine the following scenario: your Facebook login information gets hacked, and a malicious hacker logs into your account and starts using it. You immediately find out about it, and change both the email and password for your account. Even though you changed the “time of check” settings, the malicious hacker is still in the “time of use” phase, messing up your social media life by sending coworkers awkward photos of you in pajamas you had originally sent to your loved one.
Privilege escalation
As a security feature, computers come with several built in security layers, commonly referred to as “rings”: 1. The top ring is the one housing applications such as games, Word, Excel, etc. 2. The middle rings control device drivers, such as graphic and sound cards. 3. Finally, the bottom ring, and also the deepest one, is the kernel. This control the boot-up process and just about anything else in the PC. Privilege escalation attacks allow a malicious hacker to exploit a flaw in a software that gives him access to other parts of the computer. For instance, he might find a vulnerability in the graphics driver, which allows him to make his way up the access rights chain and gain control of wider sections of the device. 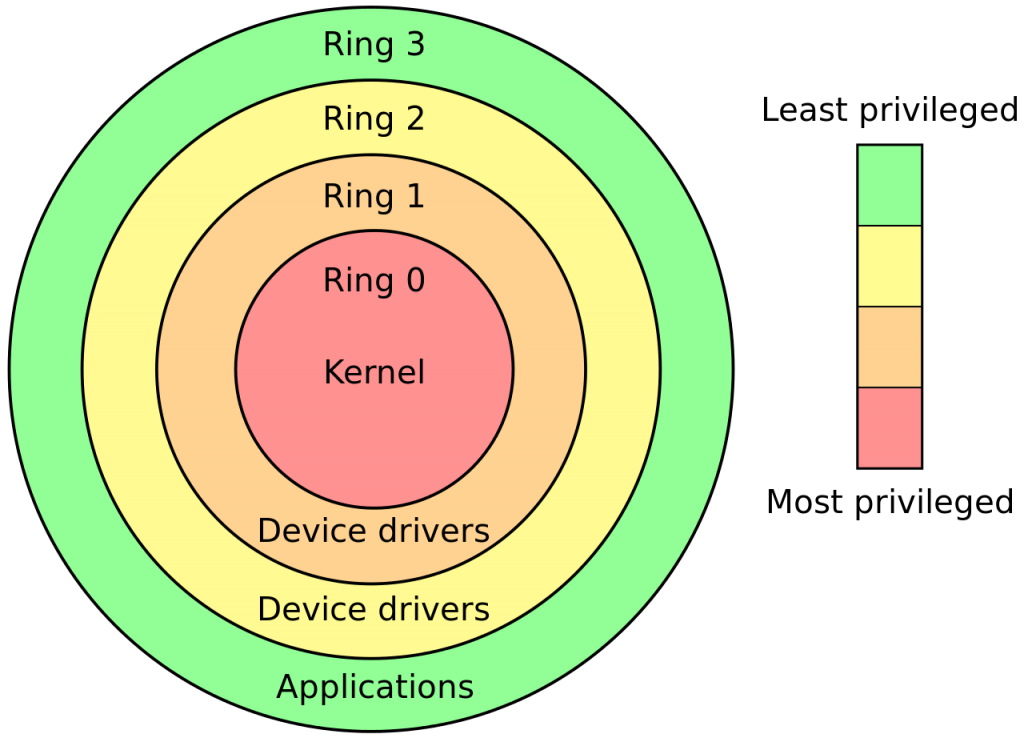
Supply chain attacks
Companies rely on other companies to provide them with the resources they need to conduct business. This creates something called a supply chain, where each company provides a component to the end product. A cybercriminal could end up hacking into the end product by compromising just one company in the supply chain. For instance, if a malicious hacker infects all the memory hard drives produced by a certain manufacturer with a rootkit, then the attacker will automatically infect all of the PCs that have those hard drives built in. 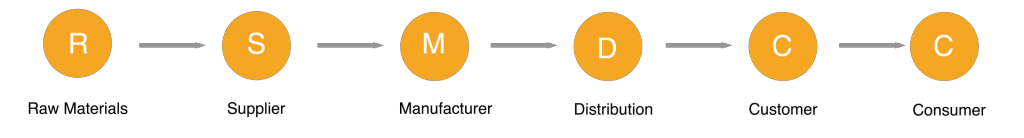
Login attacks
Cybercriminals would love to get access to your accounts and passwords. Especially if they’re email accounts, which they can then use to take control of any other associated credentials. Here’s how a malicious hacker can break into your login credentials. 
Brute force attacks
A password guessing attack that involves trying a huge amount of passwords on a login screen until the attacker finally finds the right one. A brute force attack can guess a weak password with 8 or less characters in a few hours or days at most. Adding a few special characters and making it 10 or more characters long will dramatically increase the cracking time, to the point where it would take decades or even centuries to crack. 

Dictionary attacks
Similar to a brute-force attack, except that this time, the attacker configures his software around certain letters or words he suspects you might include in the password. For instance, if you are a pizza lover, he might instruct the software to first try out password combinations that contain the word pizza such as “pizzaislifeyeah” or “wick3dpizza”.
OAuth exploits
OAuth is the technology used for “Login with Facebook” or “Login with Google” buttons. In most cases, OAuth is a very secure login protocol, but many app developers do a poor job implementing it. Normally, when you press the “Login with Facebook” button, the app asks Facebook “is this guy legit?”, the social network then answers back “yes he is, allow him to pass”. However, many apps want to shorten the time it takes for you to actually start using it, so they skip the part where Facebook confirms it’s really you, and just log you in instantly. This allows a malicious hacker to manipulate the login process and gain access to your account.
Malicious content
Some malicious hackers aren’t interested in infecting you with malware. Instead, they want you to give them money willingly.
Spam
Email is big business. Even today, most marketers consider an email list to be the best money maker out there, more so than social media networks or raw internet traffic on their site. Some unethical marketers (sometimes known as blackhat marketers) bypass the process of building a legitimate email list by buying or renting one, and then just blast the users with promotional emails they never signed up for. Spam also happens to be the top source for malware infections and phishing campaigns. It’s really easy for a spammer to target his emails to a certain country and find an email service. Here’s a more in-depth look on how spam operations function and why they won’t go away any time soon.
Hate speech/cyber bullying
Some forms of abusive content center around spreading fear, and stoking violence. Racist speech, homophobia, religious fundamentalism are all forms of hate speech, since they incite the reader to do what he otherwise wouldn’t do. Abusive content spreads through many channels: email, blogs, social media accounts even advertising in some cases. Cyber bullying fits in the same category, where the attacker seeks to humiliate the victim, blackmailing them, or picking on their defects. Cyberbullying has a real impact on the victims, with numerous stories of people driven to suicide.
Child pornography and other types of violent or sexually explicit content
One of the main reasons why the dark web exists is to spread and sell content that is otherwise illegal. Child pornography is probably on top of the list, alongside graphic videos depicting other violent acts.
Who are the people committing cyber attacks?
The vast majority of cybercriminal groups launch cyber attacks in order to make money. But, there are other groups out there who aren’t interested in money-making.
State sponsored hacks
In the constant fight for geopolitical power, cyber-attacks are a favorite tool in a nation’s arsenal. Hacking another country is a cleaner and more quiet process than sending in tanks and soldiers, while still giving tangible results. One of the most high-profile such state-sponsored hacks is the Stuxnet worm we talked about earlier. Nobody managed to conclusively identify the source of the infection, but most analysts claim the United States and Israel created Stuxnet as a joint effort.
Hacktivism
Some hackers aren’t interested in money, nor do they work for governments. Instead, they seek to advance a social cause or mission, and are not ashamed to hack into governments or organizations they deem to be standing in the way. These causes vary from group to group. Most hacktivist groups claim to protect free speech, democracy and transparency. One of the most well-known hacker groups out there is Anonymous, a loosely organized organization that has protested against tougher copyright laws, child pornography and various corporations. 
Cybercriminals
The biggest group of malicious hackers by far. Cybercriminals seek to make a quick buck by using any of the malicious methods mentioned above. Usually, a cybercriminal will specialize, such as spam messages, phishing, login attacks and so on. Another thing to take into account is that malicious hackers don’t really operate as lone wolves. There is an entire so-called “malware economy”, where cybercriminals trade and sell hacking tools, leaked email databases, phone numbers, and even DDoS as a service.
Conclusion
The Internet has spurred a huge wave of innovation and has made all of our lives so much more easier. Unfortunately, criminals have oftentimes innovated at the same speed, or even faster, coming up with newer and more powerful ways to take away your hard-earned cash, or control your information. Fortunately, there’s a lot you can do to avoid these attacks.

INSTALL IT, FORGET IT AND BE PROTECTED
Download Heimdal™ FREE

 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security