Contents:
Most people are already aware of the risks associated with clicking links in emails, but only a few acknowledge the dangers of clicking links in text messages. Because users are more inclined to trust text messages, the smishing technique is often profitable for threat actors looking to steal credentials, financial information, and personal data.
Smishing has also become a serious challenge to enterprise cybersecurity as the use of mobile devices for business becomes more widespread as a result of remote work and BYOD (Bring Your Own Device) policies. Therefore, it is not surprising at all that smishing has become the most common type of malicious text message.
So, What Exactly Is Smishing?
Smishing is a type of phishing attack in which scammers use text messages to persuade victims into opening malicious attachments or clicking on malicious links. So, rather than sending phishing content via email, this type of cybercriminals delivers their messages using SMS or MMS text messages.
This kind of cyberattack involves tricking victims into disclosing sensitive information to a disguised hacker who can then use it to commit fraud or other malicious activities. Occasionally, SMS phishing can be assisted by malware or fraudulent websites.
The texts usually purport to be from a legitimate organization, such as the user’s bank, card issuer, a service provider like a mobile phone company, or even a government agency.
To conclude the definition part, smishing, a combination of the terms “SMS” (short message services) and phishing, is referred to as a type of social engineering attack that is based on human trust exploitation rather than technical exploits to try and fool potential victims into disclosing private data.
How Does Smishing Work?
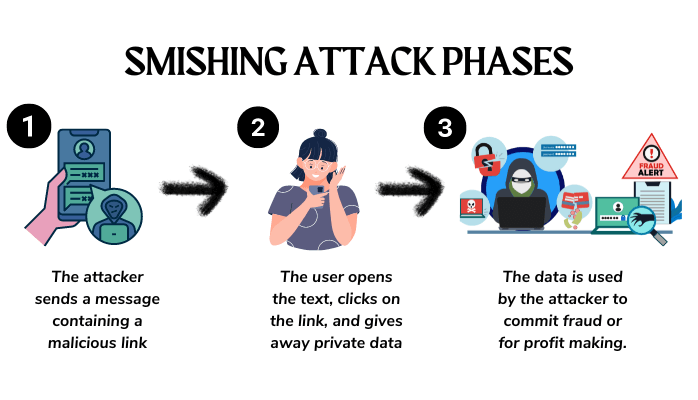
Smishing attacks frequently combine two or more actions to accomplish their goal of snatching your personal information.
The first step is to make you feel compelled to respond. It can be something related to money, like making more money or methods to protect the money you already have.
The second step is to persuade you to click on a link contained in the message that takes you to a website that appears to be genuine and was created to resemble the site you expect to see. For instance, if it is a bank, you may see on the website fonts, logos, and color combinations that you would typically find on a site managed by that particular institution.
The following step will be to have you enter your personal information. The request can be as simple as asking for your account username and password.
The smisher’s scheme is complete once they have used your personal information to commit the theft they intended. Among others, this objective could include stealing directly from a bank account, carrying out identity fraud to open credit cards illegally, or making private corporate data public.
This type of phishing attack can also be conducted in fewer steps. For example, the original text could include a link that, when clicked, downloads malware that can be employed to snatch your private data.
Types of Attacks
Smishing attacks, just like conventional phishing attacks targeting email, deceive users into clicking a link that is included in the SMS message using various pretexts. Some of them are:
- COVID-19 smishing scams
- Financial services smishing scams
- Gift smishing scams
- Customer support smishing scams
- Invoice or order confirmation smishing scams
How to Recognize Smishing
Smishing is easy to recognize once you are aware of its signs. Here’s how to determine whether you are the target of a smishing attack:
Credentials Request
Your account username and password may be requested by a smisher in an effort to gain access to the website they are impersonating or a different type of account. The reasons offered by the intruder for needing your information differ from person to person, but keep in mind that you should be suspicious anytime someone asks for logins via a text message.
Links and Attachments from Numbers You Don’t Know
Most often, smishing messages include links to phony websites that can collect your personal information. Therefore, if you see one, never click it. But if it does and you click on it, look out for indications of a risky website, like a URL without a “http” in it.
Money Requests
It is recommended to be extremely vigilant every time you receive requests for money via text messages. Remember that that not all scams are obvious. A key element of many smishing attacks is gaining trust by posing as someone you know well or someone you trust.
The Phone Number Looks Suspicious
Smishing texts may come from phone numbers that don’t look normal. If you see numbers that look suspicious to you accompanied by a message that is even more suspicious, don’t text back and delete it as rapidly as possible.
‘You Won!’ Type of Message
No, you didn’t! Especially because you didn’t participate in the contest in the first place. You need to think about this the next time you receive a message saying that you won a prize. I know it can be exciting, but it’s important to avoid clicking on any links attached and delete the message.
Urgent Requests
The majority of phishing emails and text messages contain urgent requests intended to scare the recipient. However, any trustworthy organization will notify customers in advance of any urgent matters. Delete the texts, and if you’re still worried, get in touch with the company that allegedly sent them.
Smishing Attack Prevention
There are some measures you can take in order to avoid falling victim to this type of attack:
- Never trust text messages you receive out of the blue that purport to be from a legitimate company, like a financial institution or credit/debit card issuer.
- Be cautious of SMSs that instruct you to call a phone number or go to a webpage to solve a problem or confirm your information urgently.
- Avoid replying to texts that ask for private information, like bank account details, before confirming that the sender is legitimate.
- Never respond to messages asking for your PIN, password for online banking, or any other password.
- Download apps from trustworthy app stores. Some attacks using smishing may be intended to fool targets into installing malicious apps onto their mobile devices. Install apps only from trusted app stores.
- Verify the sender’s number. Phone numbers that seem unusual, such as 4-digit ones, may indicate the use of email-to-text services. This is one of many strategies a malicious actor can employ to hide their real phone number.
- Use two-factor authentication. Two-factor authentication can serve as an additional layer of security in the event that you do fall victim to a smishing attack and give away one of your passwords. Biometric authentication uses fingerprint technology and facial recognition to validate your identity when you try to log in.
How to Mitigate a Smishing Attack?
- Notify any institutions that may be able to help with the suspected attack. Get in touch with your bank or service provider as soon as possible.
- Freeze your credit to avoid future or ongoing fraudulent activity.
- Change all passwords and account PINs.
- Keep an eye on your finances, credit, and different online accounts for unusual login locations and other activity.
Conclusion
As I mentioned at the beginning of this article, with the rise of remote and hybrid work frameworks, as well as BYOD policies, mobile devices are becoming an integral part of business operations, making mobile security more essential than ever. It’s important to acknowledge that smishing attacks pose a serious risk to both organizations and individuals and act accordingly.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










