Contents:
Malicious software (malware) can severely impact your machine, whether you’re using a work or home computer. This guide will show you how to remove malware from an affected machine and, of course, what needs to be done in order to prevent future occurrences.
What should I do to remove malware?
Depending on the type of malware rooted into your machine, you may experience negative changes such as slowdowns, freezes, denial of service, malvertising, high resource consumption, random messages appearing on the screen, browser redirection, and so on. If you experience one or more of these signs, chances are that there’s an infection rampaging through your machine.
Malware Removal Process
To remove malware from your machine, please follow the instructions below.
- Disconnect your machine from the Internet
- Back up your machine
- Enter Safe Mode (with networking)
- Delete temp files
- Reset browser settings
- Verify proxy settings
Step 1. Disconnect your machine from the Internet.
Ensure that your machine has been disconnected from the Internet. If you’re running on Wi-Fi, switch off the connection from the Wi-Fi menu (Settings –> Wi-Fi). Some types of infectors may prevent you from tampering with network controllers. In this case, consider shutting down or even unplugging your WAP (Wireless Access Point).
For wired connections, sever the connection from the Ethernet menu, under Settings or unplug the cable. Disconnecting your machine from the Internet servers several functions.
For instance, if your computer is part of a larger network, severing the connection prevents malware from infecting other machines. In ransomware attacks, disconnecting the machine may hinder the malware from communicating with the C2 (Command and Control) server.
Step 2. Back up all your documents and files
Regardless of your malware infection, the first thing to do is to backup all your important files and documents. You can do that by saving your essential data on external sources such as DVD/CDs, free cloud storage services, USB sticks or external drives. Use this guide to better back up your online data. By performing a backup process, you can save your essential data on an external source to keep it safe.
Step 3. Reboot in Safe Mode with Networking
Here’s what you should do:
- Unplug DVDs, CDs or other USB drives from your PC and then shut it down.
- Restart by pressing F8 key over and over again until it takes you to the Safe Mode with Networking.
This will make your system boot up only critical processes and prevent certain malware infections from starting up.
If you are using Windows 8 and/or Windows 10, here’s how you can start your PC in Safe Mode. For older versions of Windows, such as Windows 7 or XP, follow these steps.
Step 4. Delete temporary files.
To make the scanning process smoother and simpler, you should delete all unessential temporary files from your computer.
To do this, right-click on a Windows drive, go to Properties, and click on Disk Cleanup. From the menu, choose which files you want to delete and remove.
Step 5. Reset your browser settings
In many cases, malware will change your browser settings in order to re-infect your computer, show advertisements, or facilitate any other malicious downloads. This is why you need to review some of your browser settings.
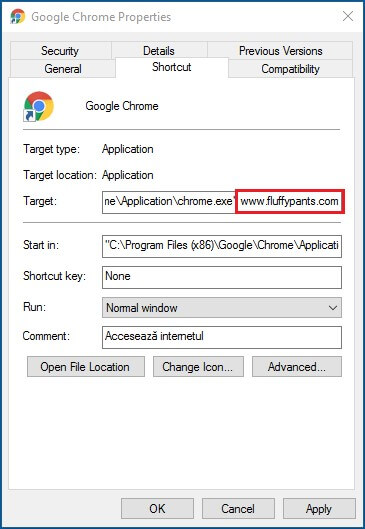
Fixing browser shortcuts altered by malware.
- Access your browser. Right-click on your browser, then go to Properties.
- Under the Shortcut tab, you’ll see the Target field.
What can actually happen is that the malware might have altered the target field and included a malicious URL in it. What happens is that now your browser will start up on this page each time you boot it up.
Normally, the browser target should look something like this:
Chrome: “C:\Program Files (x86) \Google\Chrome\Application\chrome.exe”
In our example case, the browser was targeted to go to a suspicious website, aimed at downloading malware on your PC.
You can fix that by simply remove the URL that comes after .exe”. Browser hijackers will change the homepage. Instead of changing the “Target” field in the “Shortcut” tab, some malware might just modify your browser homepage.
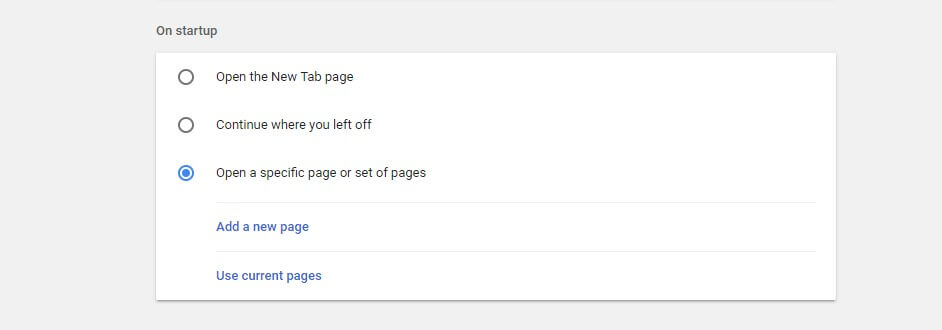
For the Chrome browser
Go to the Settings in the top right corner of the browser. Once there, go to the on-startup section. The first two options don’t have any homepage whatsoever, so you can go ahead and select either one of those.
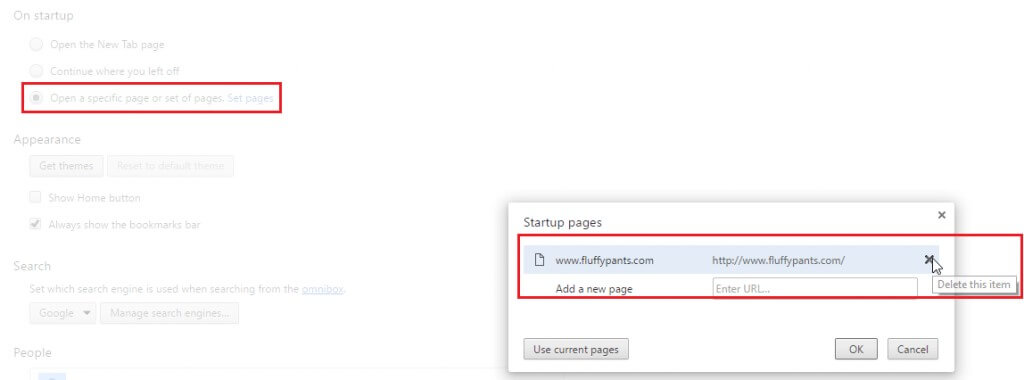
If however, you want to have your own homepage, then check the option to Open a specific page or set of pages and then click on Set pages. This should take you to this window where you can add or delete malicious links sneakily set as homepage.
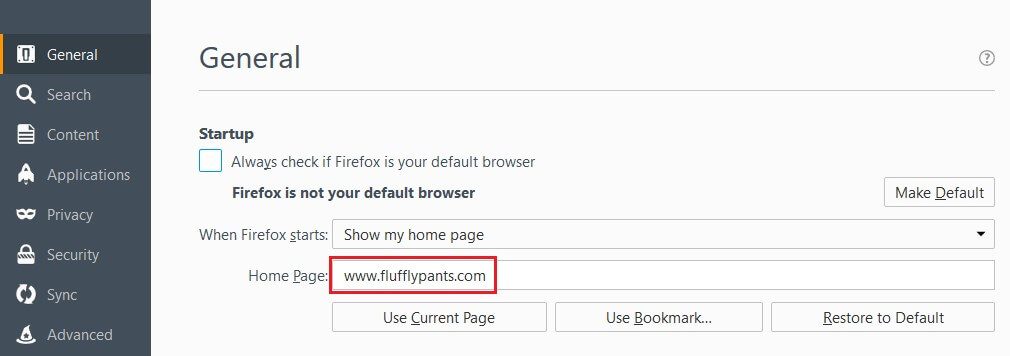
Settings for Firefox
You can access the Options menu in the top right corner of the browser. This will immediately take you to the General tab, where you can reset your homepage as you see fit.
Malicious hackers can also take control of your accounts through session hijacking by entering the server and access its information without having to hack a registered account. Additionally, he can also make modifications on the server to help him hack it in the future or to simplify a data-stealing operation.
Step 6. Verify your proxy settings
There is malware that can even change what Internet service you use to connect to the web. Simply removing the malware won’t reset these proxy settings, so it’s something you should fix before considering your PC squeaky clean. To access your proxy settings, go to Control Panel -> Network and Internet and then press Internet Options.
In the Internet Options menu, go to the Connections tab and press the LAN settings button.
Make sure that Automatically detect settings is on, and that the other two options, “Use automatic configuration script” and “Use a proxy server for your LAN” are unmarked. Here’s how your settings should look like:
How to prevent malware
Now that you’ve managed to clean up your PC and remove malware, it is important to take some protection measures to prevent getting another infection. Some malware programs operate stealthily, and you may not know the infection is there. They don’t visibly affect your PC.
Instead, they may collect sensitive information of yours such as passwords, credit card data, completed forms and screenshots. We recommend following these protection measures to prevent getting your computer infected:
Use two-factor authentication management system
If among other things you were also infected with a keylogger, then there’s a high chance your passwords and accounts were compromised.
One of the first things you should do is start using the two-factor authentication management system and manage your passwords safely. There is some malware that can take full control of your passwords.
This password security guide will provide all the details needed to set strong and unique passwords to prevent malicious hackers exploiting them and lock you out of your accounts. With the two-factor authentication system, you will add another layer of protection to your account.
Always keep your software up to date
Outdated software is one of the major causes of malware infections out there, mostly because they come with many vulnerabilities exploited by cybercriminals.
Keeping up your software permanently up to date will lower the chances for malicious hackers to get inside your device or limit any possibility for them to infect computers.
We know it can become a tedious, yet necessary task to constantly update your software, particularly those that patch frequently.
Heimdal™ Patch & Asset Management is a great solution that will automatically (and silently) update your software, without any annoying confirmation pop-ups. It’s light and unobtrusive, so it won’t slow down your system.
Use a traffic-filtering solution to secure your endpoint(s)
A traffic filtering software will nicely and efficiently complement an antivirus since it scans incoming and outgoing traffic for any malware and then blocks that traffic from entering your PC. In other words, it gets difficult for new malware to reach your device. Heimdal™ Threat Prevention – Network will sanitize your Internet traffic and block malicious sources, making sure you have both your financial and confidential information safely kept.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security