Contents:
For a long time, app permissions were something the regular PC user had no idea about. When installing new software on a computer, we were never asked if application X could access our web camera, our list of contacts, etc. We just clicked “Agree” on the terms of use and that was it.
But in the current era of breakneck pace of Internet usage and device adoption, we are given the power to decide. It’s just that we have a lot of decisions to make and we don’t amaliclways know what to choose.
App permissions may seem like a nuisance, but the better you know how they work, the safer you can keep your data.
Before we begin, here’s a set of helpful links to help you navigate the guide and see what you can learn by reading on:
>>Operating system permissions
>>Web app permissions
>>Social media app permissions
>>Mobile app permissions
>>Permissions can change over time
>>Cyber threats targeting mobile devices
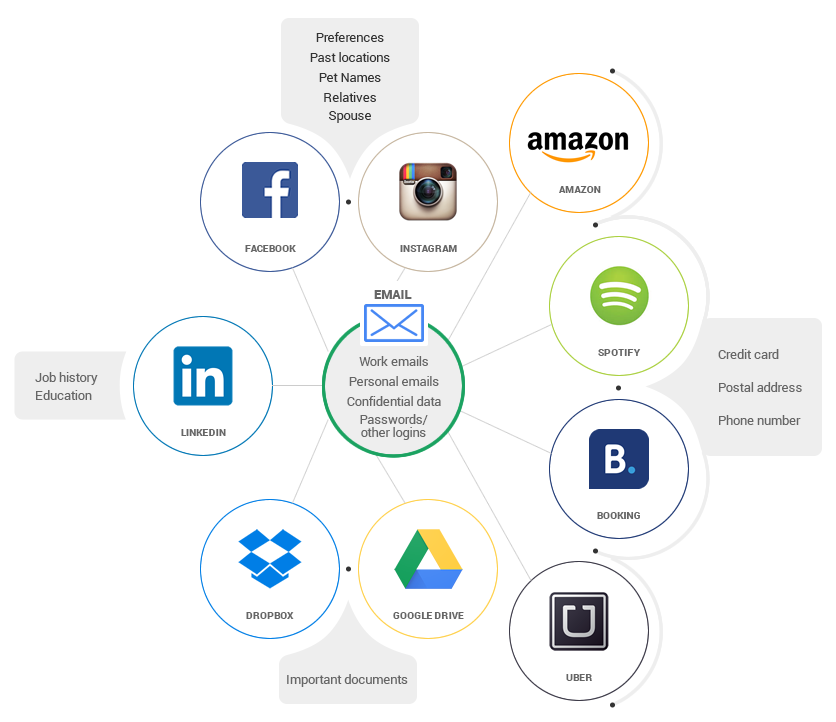
Maybe you never thought about how your accounts are interconnected on the web. Take a peek at this super simple graphic and imagine all your online accounts and how they’re linked to one another.
Now consider that there are a lot more apps that you’ve given permission to use some of the data in your key accounts (like email or Facebook) for different purposes.
Here are some examples:
- Each time you use your Facebook or Google account to log onto a website, that website will be able to access some of your data.
- Each time you use an app that connects to your Instagram account, some of your data is transferred into the new app.
- Each time you allow WhatsApp to save photos directly into your Dropbox, you’re giving Dropbox access to some of the data in your WhatsApp account. And the list could go on and on and on…
Because it’s so simple to do it (tap, tap here, and a tap, tap there), people rarely realize what they’re giving away / access to.
Just because it’s simple to use, it doesn’t mean that it’s not complicated in the background.
And then there’s the question of data security: should one of the apps connected to one of your main accounts become rogue (this can happen for a number of reasons) or be compromised, all the others will be compromised as well. And don’t even get me started on password reuse (please, please, PLEASE never do that).
Fortunately for us, due to increasing concern over privacy and online safety, app makers have been forced to make it clearer to users what data they’re requesting access to and why. They’ve even been forced to give users the ability to use their service / product even if the user didn’t allow all the privileges that the product / service requested. And the European Data Protection Regulation coming into effect in 2018 will strengthen the user’s position as the decision maker over what happens to his/her data.
But having access to these options doesn’t make them self-explanatory. So I’ve developed a guide to help you understand what app permissions mean for your data and how you can manage them to ensure your cyber security is never compromised.
OPERATING SYSTEM PERMISSIONS
Things have certainly evolved a lot in terms of how transparently operating systems work. In the latest versions of Microsoft’s Windows and Apple’s Mac OS X, you have better control over permissions. Let me show you exactly what I’m talking about.
Windows 10
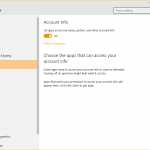
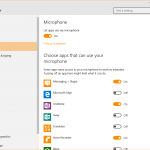
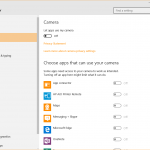
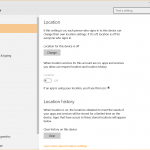
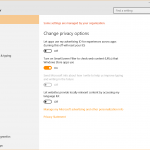
In Windows 10, go to Settings and then choose Privacy.
In this section, you’ll find plenty of options to help you manage the type of information and capabilities that Windows and third party applications can access. These options include:
- Data about your PC usage and browsing history
- Location information
- Access to your PC’s camera and microphone
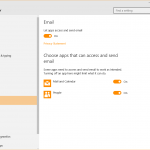
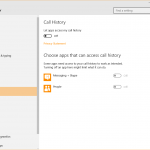
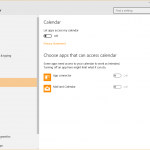
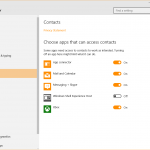
- The right to use your account info, contacts, calendar, call history, email and messaging apps (given the fact that Windows 10 is a cross-platform operating system)
- Access to radios (such as Bluetooth) and connections to other devices
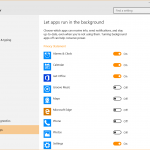
- But also the types of apps you allow to run in the background.
In these permission settings, you can see at a glance which apps can access which type of information on your PC. And you can also choose which one can continue to use those permissions and which cannot, if you haven’t set these permissions from the beginning.
Mac OS X
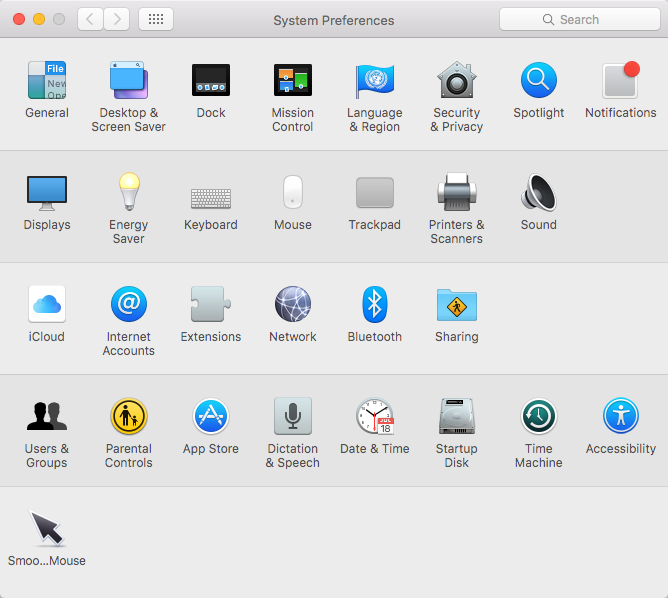
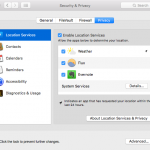
If you’re a Mac OS X user, go to System Preferences and then to Security & Privacy.
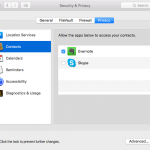
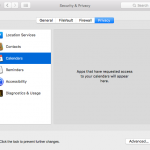
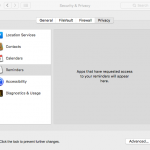
The list is a bit simpler in this case, with Apple giving you the options to manage permissions for:
- Your location
- Your contacts
- Your calendar
- Your reminders
- Accessibility
- Diagnostics and usage.
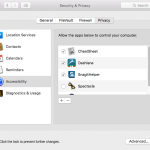
If you install any dedicated apps for social networks (Facebook, Twitter, LinkedIn, etc.), you’ll also find their permissions listed here.
Set them to your liking and then kick back knowing that you have a clear inventory of how your desktop apps access and use your specific hardware or software features on your device.
How cyber criminals can abuse this: they can use your camera to spy on you (which is chilling), they can use your PC’s microphone to listen to you, access your contacts to send them spam emails, etc.
WEB APP PERMISSIONS
Getting to know your apps can really be an eye-opening experience if you haven’t done it before. Going through this process might help you become more aware of how your data flows through these apps, to and from the Internet. Just keep in mind that all this data is about you: what you like and dislike, what you use, what you’re interested in, and so on.
Because I couldn’t possibly cover all the permissions for all the apps you might install, consider this a framework you can use to apply the same type of analysis for other situations.
Because browsers play a huge role in our digital activities, you should know how to handle permissions for them.
Chrome permissions
There are two types of permissions you can manage in Chrome:
- Privacy and content settings
- Permissions for Chrome extensions (also known as add-ons).
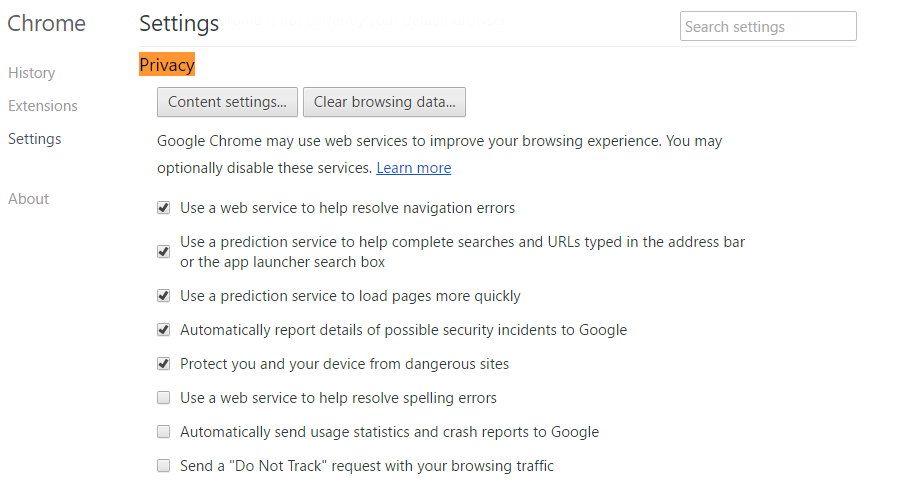
To adjust privacy and content settings, just go to your Chrome settings and click on Privacy. There, you’ll be able to choose if you want Chrome to monitor your browsing history and preferences, so it can offer suggestions based on this data. Check out this printscreen to get a better idea of what you can do here:
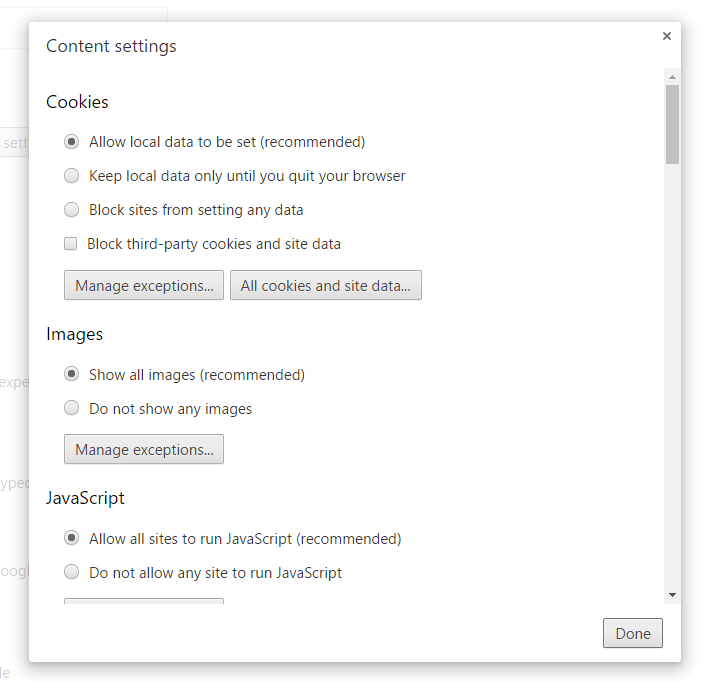
If you want to dig deeper, click on Content settings and adjust:
- The way cookies are handled
- The way images are displayed
- If JavaScript is allowed or not (this is an up and coming cyber threat)
- If key generation is allowed or not (read more about this)
- If you allow handlers
- How plugins run in your Chrome browser
- If you allow pop-ups or not
- If Chrome can use your location
- If Chrome can send you notifications
- How Chrome handles protected content
- If Chrome can use your microphone and camera
- If you allow unsandboxed plugin access
- If you allow automatic downloads via Chrome
- And a few more other options you should probably check personally.
When it comes to extensions, you should be extreeeemely careful with what you plug into your browser. Browser extensions can access a great deal of your data and can become powerful vector for cyber attacks if they’re compromised by cyber attackers or if you install rogue extensions.
3 rules to safely install Chrome extensions:
- First of all, make sure you only install Chrome extensions from the Chrome Webstore.
- Second, verify the extension maker and see if it’s a legitimate one. The extension’s page should display all the necessary details. If it doesn’t, that can be a warning sign.
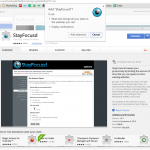
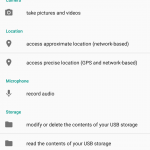
- Third, carefully read and analyze the permissions which the extension requires to run. Here are a few examples of what kind of permissions an extension might ask for:
If you find that an extension is rogue or malicious, go to its page in the Chrome Webstore and report it by clicking on the Report abuse link provided by Google.
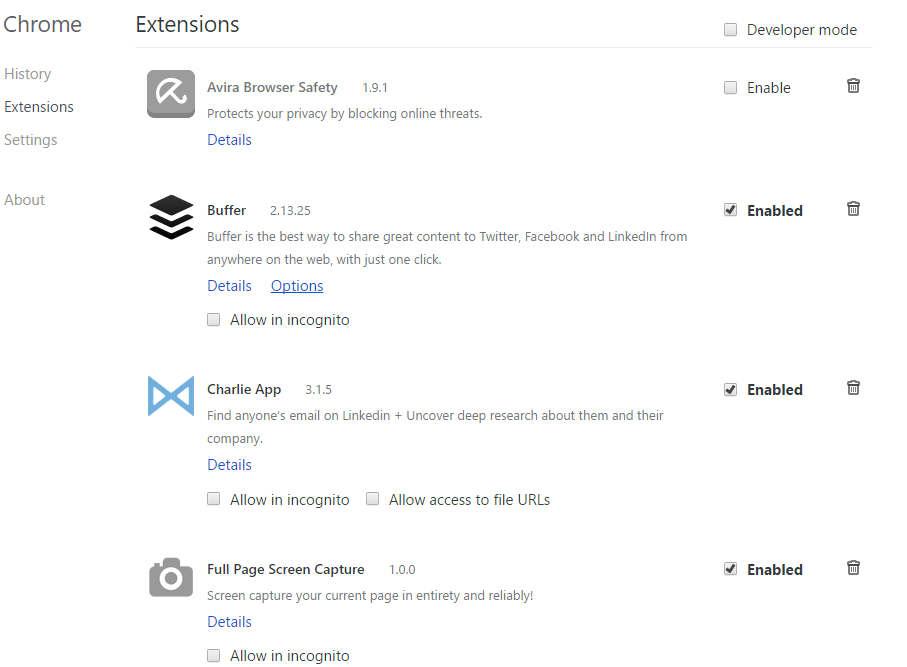
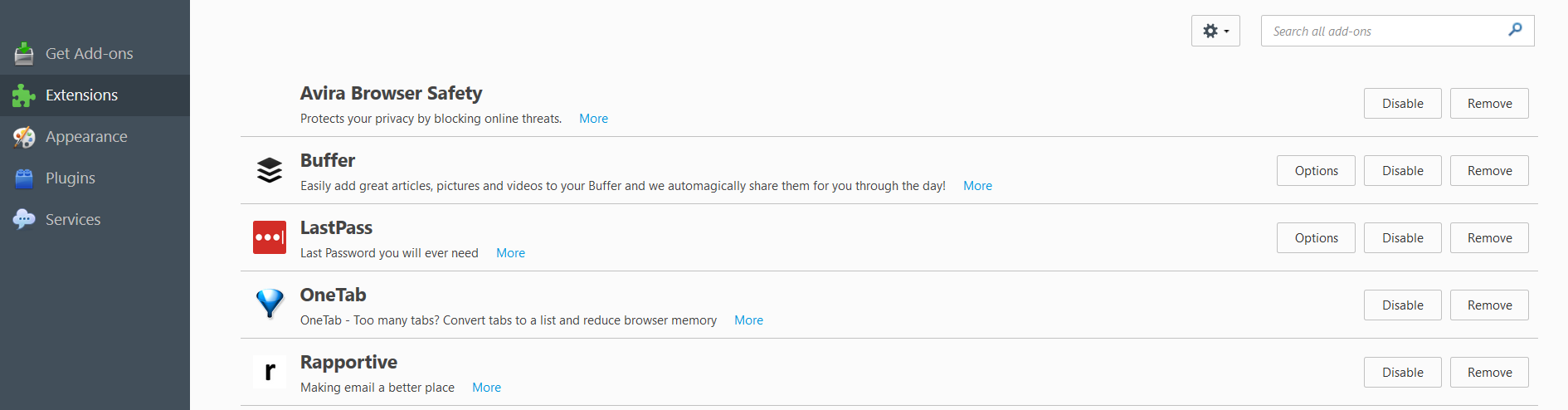
If you’ve never done a check-up of your Chrome extensions until now, go to your Chrome menu, click on Settings and choose Extensions.
Here, you’ll be able to enable, disable and delete extensions, or allow them to run in incognito Chrome windows. It’s all pretty straightforward.
Firefox permissions
When it comes to Firefox, things are a bit more complicated, but not unmanageable. There are types of add-ons you can install in Mozilla’s browser:
- Extensions
- Appearance
- Plugins.
You can read about them in the dedicated resource created by Mozilla.
3 rules to safely install Firefox extensions:
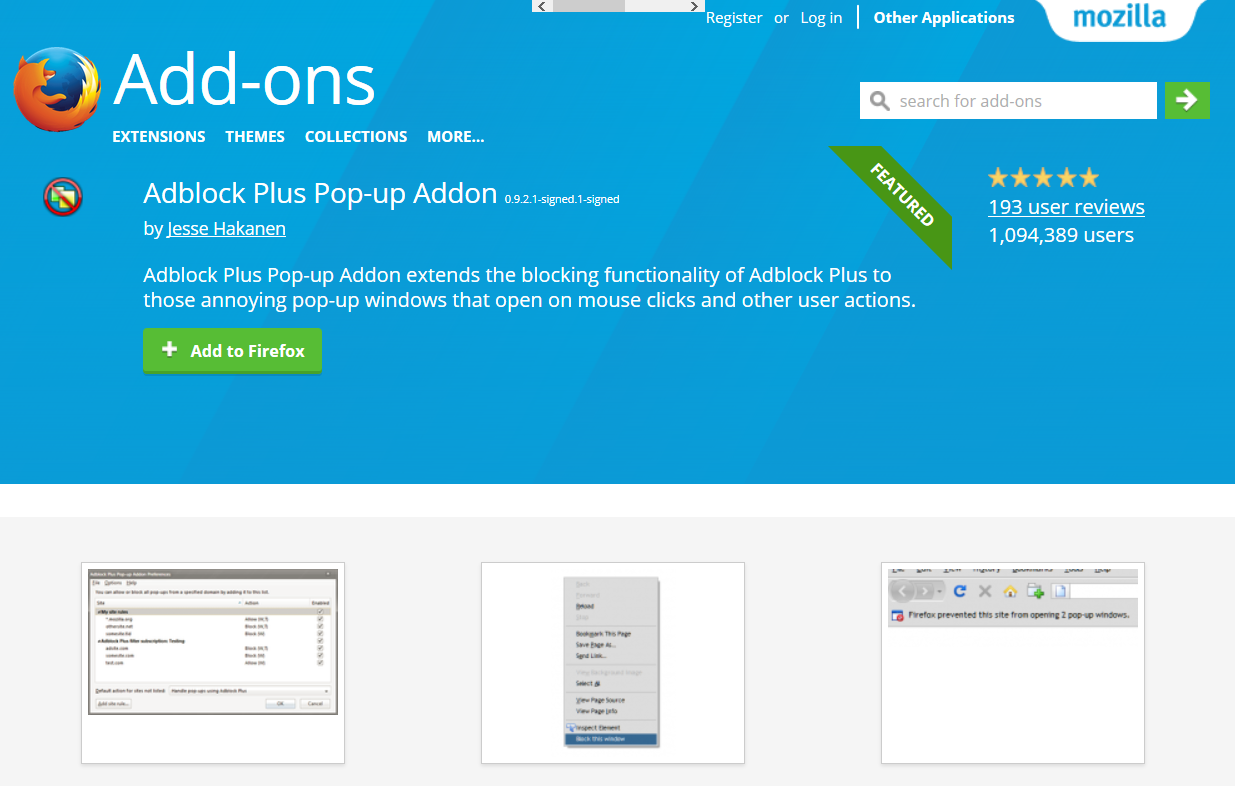
- As with Chrome, make sure you only install Firefox extensions from Mozilla’s Add-ons store.
2. Second, verify the extension maker and see if it’s a legitimate one. The extension’s page should display all the necessary details. If it doesn’t, that can be a warning sign.
Also, you should know that Firefox add-ons/extensions are different from Chrome ones, because Firefox is an open-source browser, so the add-ons are open source as well. This means that add-ons are not necessarily verified by Mozilla as thoroughly as Google monitors Chrome extensions. This discussion on Reddit may help you shed some light over this complex issue.
3. Third, carefully read and analyze the description and reviews (if there are any). You may also want to Google the name of the extension or of the add-on maker, so you can see if there are any issues with it before you install it.
In case you discover that an extension is rogue or malicious, go to its dedicated page in the Add-ons store and report it by clicking on the Report abuse link.
Unfortunately, Firefox add-ons won’t tell you what permissions they need when you install them, so there’s really no way to tell what type of access they use. This is one more reason to be very careful with what you install, as malicious add-ons can turn your browser into the perfect vector attack for delivering ransomware, financial malware, malvertising or other types of cyber threats.
I recommend you do a check-up of your Firefox extensions and plugins right now. Go to the Firefox menu, select Add-ons and go to Extensions.
Disable or remove any extensions that you don’t trust or use frequently (daily or weekly).
Then do the same for appearance add-ons, which are basically themes you can use to personalize your browser.
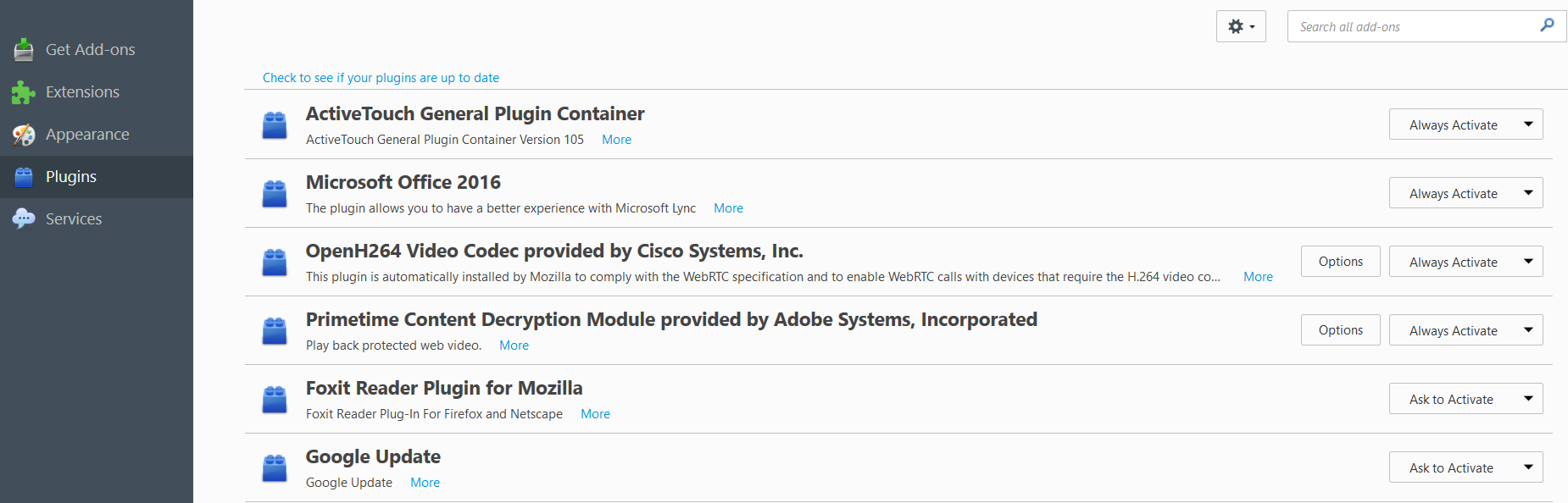
And don’t forget about the Firefox plugins, which are a major source of vulnerabilities and a rich source of attack opportunities for cyber criminals. Flash and Java are especially unsafe, so I recommend uninstalling them altogether. You can uninstall them from your programs list, not from Firefox directly, as other software may use these plugins as well (like Google Chrome or other browsers).
In this section, you can manage your plugins by selecting one of these three options:
- Ask to activate – recommended for most plugins. You should use them only when necessary. You’ll receive a prompt you can then accept or dismiss, according to the context.
- Always activate – not recommended, as plugins can become vulnerable over time.
- Never activate – if you choose this option, you may as well uninstall that plugin and gain some peace of mind.
Mind you, not all the plugins offer all these three options, as some of them are required to always be activated in order for Firefox to run properly.
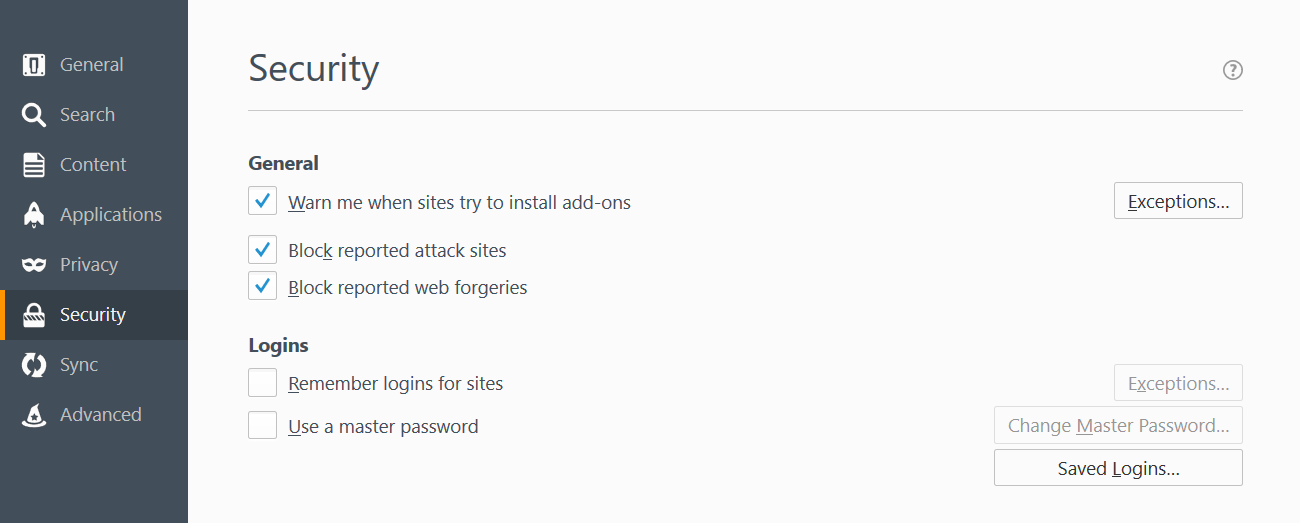
And there’s one more option you should turn on. This is located in Menu >>> Options >>> Security. Here, make sure you check “Warn me when sites try to install add-ons”, so no website will automatically install add-ons which can be malicious. This is checked automatically, but you can verify it nonetheless.
How cyber criminals can abuse this: accessing your browsers is pure gold to cyber attackers. They can inject malicious code in your browser so you’ll get infected with malware, they can redirect your traffic, log your keystrokes (using a keylogger), take printscreens of your browser, see your browsing history and much more. The browser is a key tactic to deliver cyber attacks (along with spam emails), so you have to do everything you can to keep it secure.
[Tweet “I never knew how important app permissions really were until now. Check out this guide:”]
By now, you’ve already gotten the gist of how permissions work. So now I’ll list the links you can use to manage your permissions on the most important social media accounts you have:
Facebook has a ton of information about you: your age, location, friends, relationships, likes and dislikes, etc. And this huge pool of data can be accessed by apps you connect to it, be it games or utility apps.
So it’s extremely important that you learn to control them. Here are a few useful links you can use to manage your app permissions:
How do I control my permissions when I sign up or log into an app or game?
App Privacy Settings & Your Info
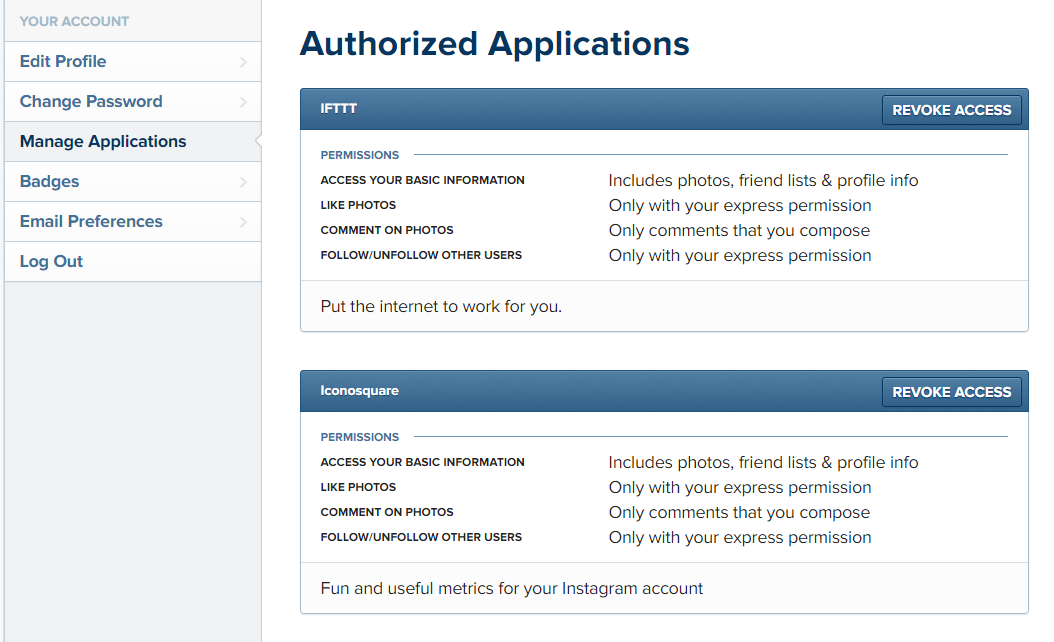
Revoke access to apps linked to your Facebook account
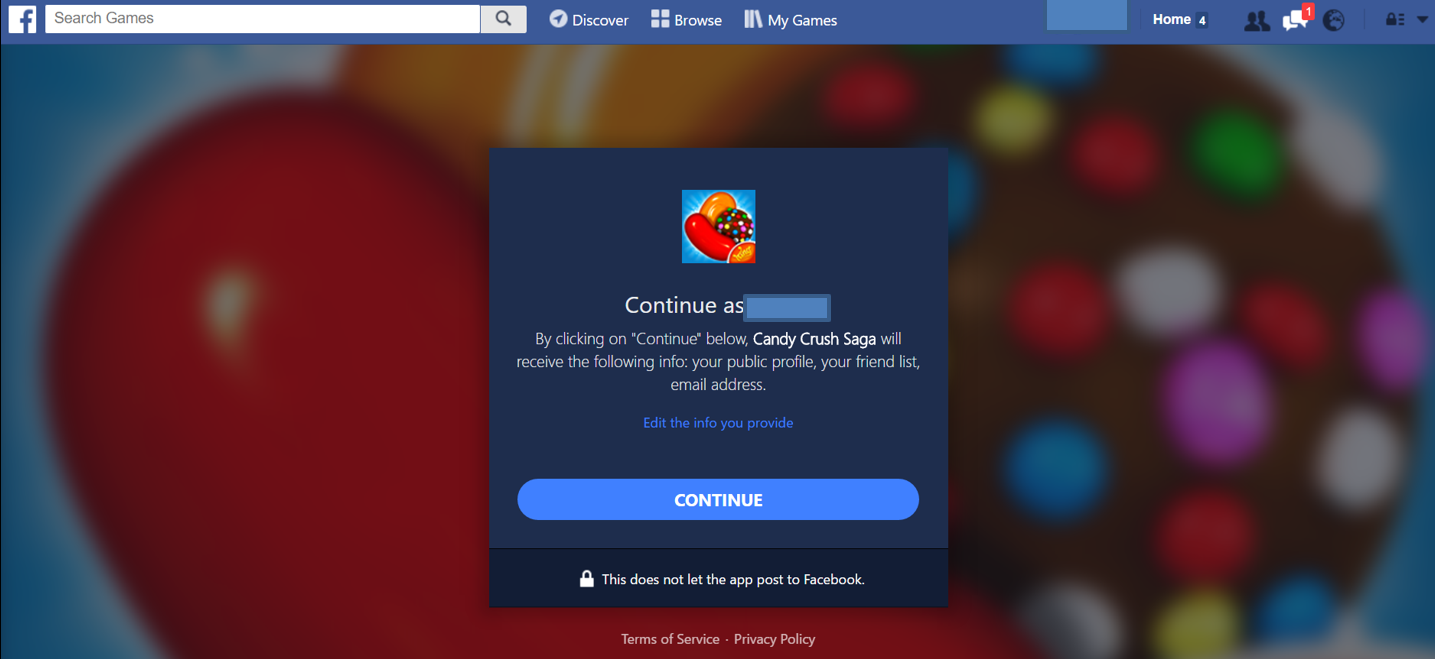
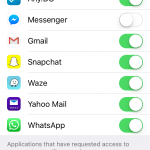
Also, remember that any app will ask for some permissions, so it’s really important that you pay attention to this aspect, even when you’re doing something as simple as start playing a game:
Do you use all kind of apps to make your Instagram pictures better? I’m talking about the likes of Hipstamatic, Overgram, Pic Stich or others. If so, then you should definitely do roundup and see what you actually use and what you’re just hoarding on your phone:
Revoke access to apps linked to your Instagram account
Being a network aimed to help you develop professionally, you should be really careful with the apps you link to your LinkedIn account. One wrong click and apps could start posting strange things on your profile or, worse, start spreading malware to your connections.
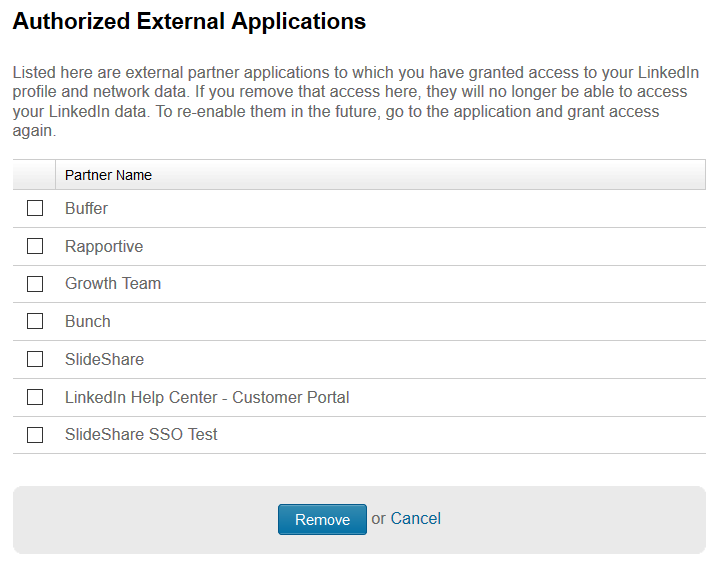
Clean Linkedin app permissions
There are many, many other apps, mobile or web-based, which use Twitter to let you sign in or do a bunch of other things. Consider your privacy and online security when doing this:
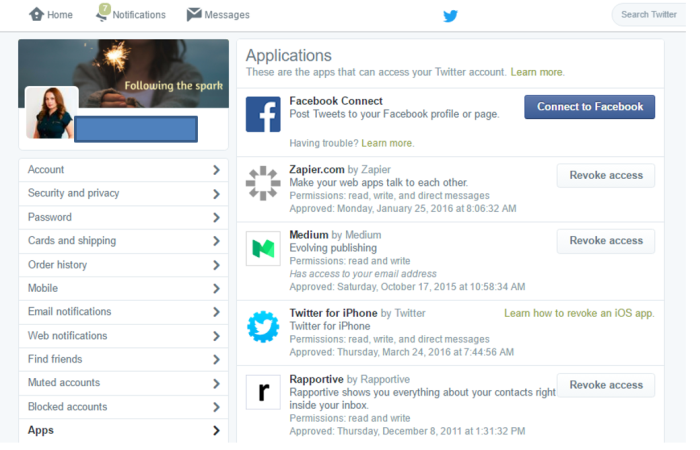
Manage your Twitter app permissions
While this is not exactly a social media platform, you’ve probably often used your Google account to log into other platforms, so you should still be very careful with how you use this feature. Especially since it’s connected to your email account, which you also use for SO many other purposes.
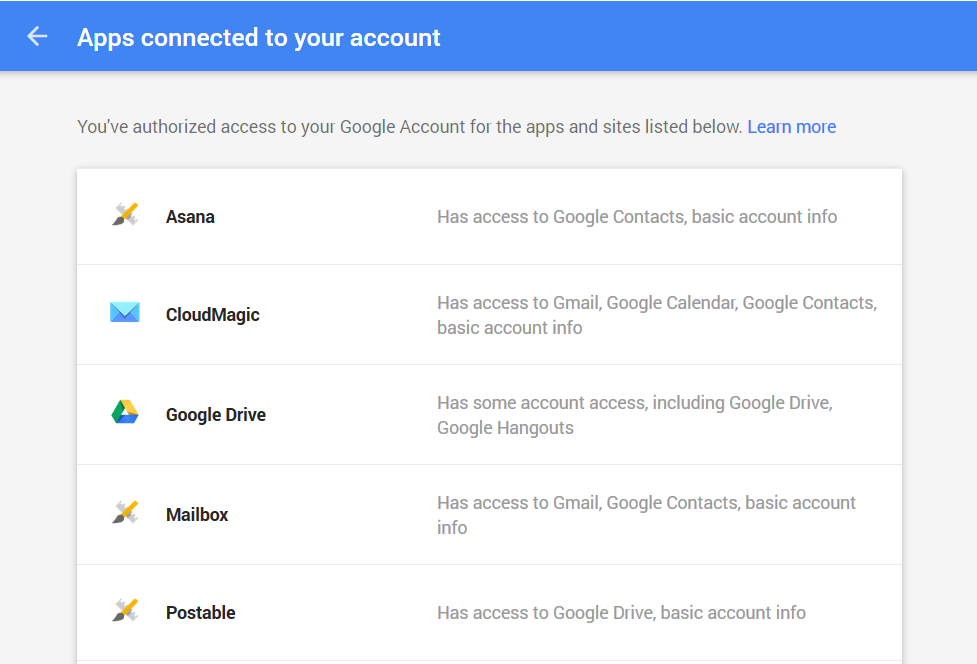
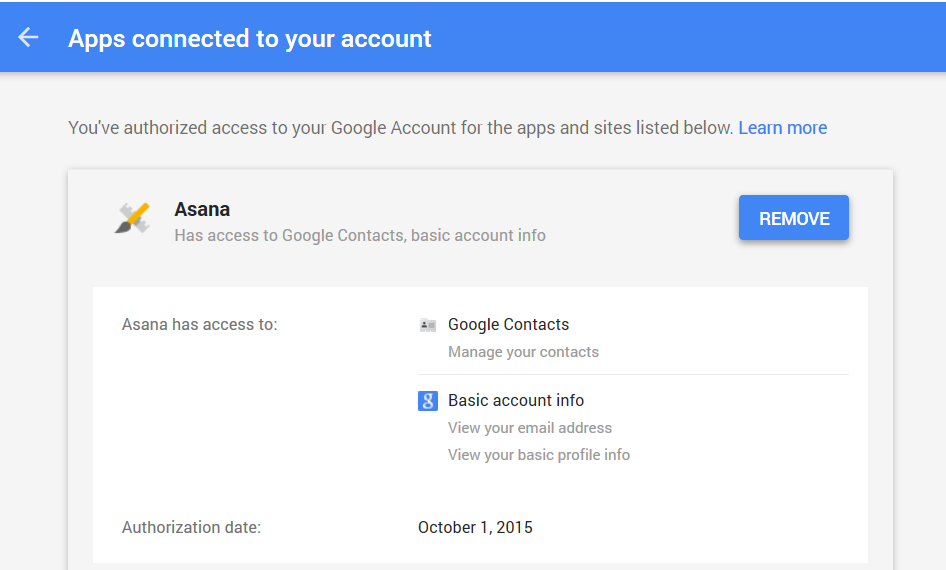
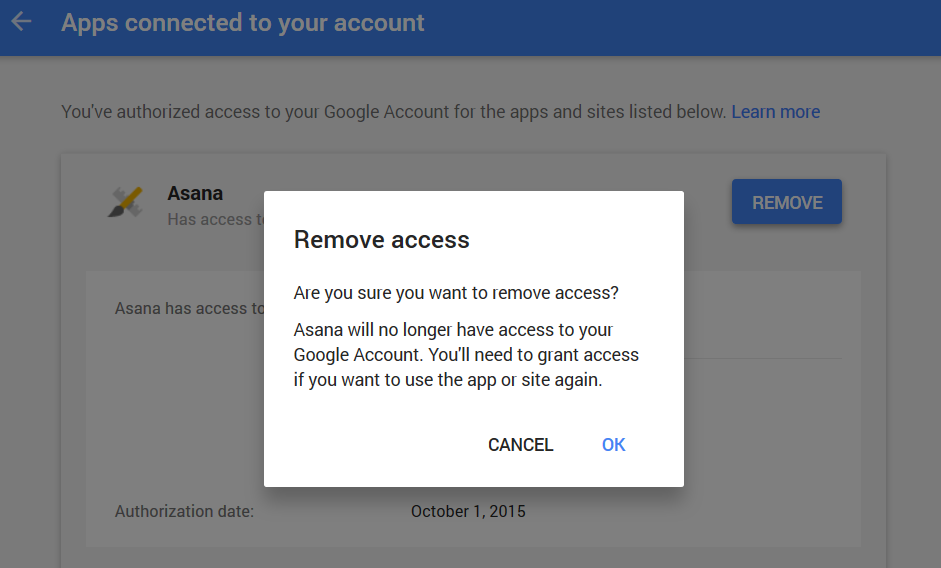
Google: Apps connected to your account
Click on an app for more details about what permissions they need and removal options. If you have any apps that have been sitting there, gathering digital dust, it’s time to let them go.
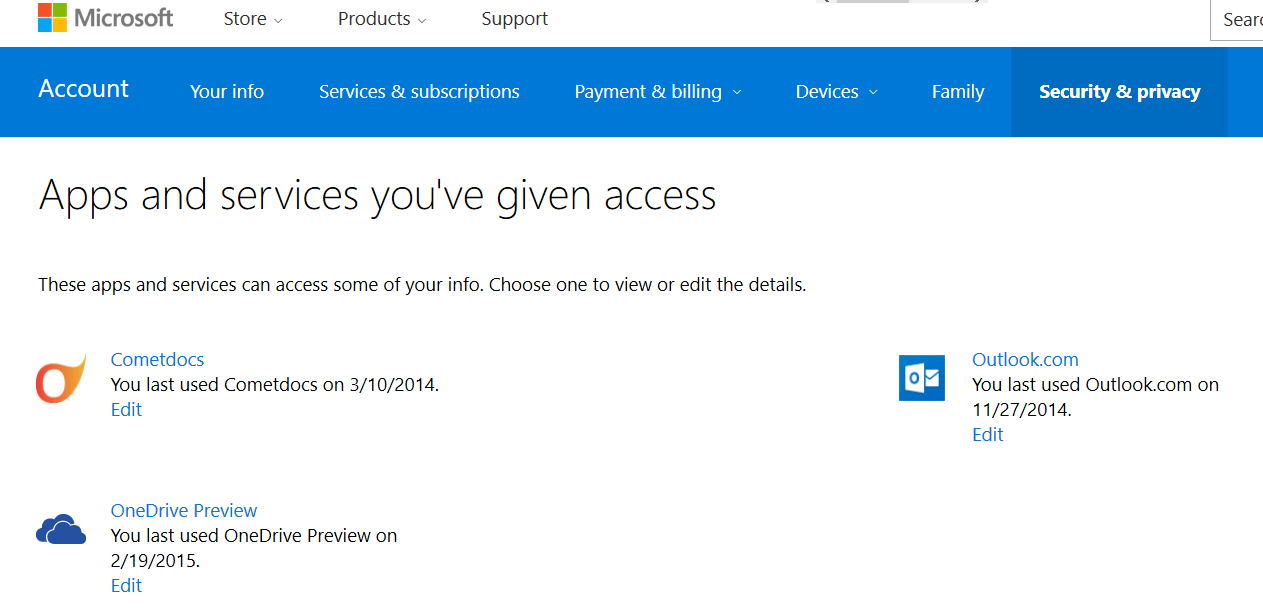
Microsoft
The same as for Google goes for your Microsoft account.
Apps and services you’ve given access
How cyber criminals can abuse this: the wealth of data you store and share on your social media accounts is a huge resource for malicious hackers. They can use all the data about you to breach your core accounts (email, banking) and defraud you. They can also use that data (IMs, friends, contact info, etc.) to steal your identity, spread malware to your social media connections, defraud you or your friends and family, etc. There are hundreds of social media scams that still work, which makes for a good reason to keep your eyes peeled.
MOBILE APP PERMISSIONS
When you think of app permissions, your thoughts probably jump directly to mobile apps. That’s probably the first place you ever noticed that app permissions existed in the first place. And it really makes sense, because this is a much more visible aspect on mobile.
Although an official classification doesn’t exist, we can define 7 major categories that app permissions fall into:
1. Location permissions
These type of permissions allow apps to read and use your phone’s approximate or precise location.
How cyber criminals can abuse this: they can use location data to track you, to gather data on you and correlate it with other pieces of information so they can send phishing emails or messages and in plenty other ways you’ve probably never thought of.
2. Account permissions
You need a Google account to use an Android mobile device and an iCloud account to use an Apple device. And then you probably also logged into Facebook, Twitter, LinkedIn and other accounts on your smartphone/tablet. This is for ease of use, as, by now, our phones store an incredible amount of data about us. Maybe even more than our PCs.
How cyber criminals can abuse this: Just imagine the extent of the damage a cyber attacker can do if you grant access to a rogue app to your accounts. They can steal/modify/sell this data or use it to spread malware and launch attacks against all your contacts.
3. Phone details permissions
This type of permissions allows your apps to recognize when you have an incoming call and pause the app in use to handle the call. But granting access to your phone details also means that an app can read and send the IMEI (International Mobile Equipment Identity) of your phone via the Internet.
How cyber criminals can abuse this: they can access and store your phone’s IMEI on their servers to track your phone without using more personal information.
4. Contacts permissions
The same logic as the one applied to your account permissions is relevant here. Apps usually request access to your contacts so you can share things. But if you don’t want to use this function, just make sure to deny it.
How cyber criminals can abuse this: more contact details, more potential targets! Need I say more?
[Tweet “A clear explanation for app permissions and why they’re essential for our online security:”]5. SMS and MMS permissions
This permission grants apps access to read and send text messages. That means that it’ll also be able to read your two-step verification codes (read more about two-factor authentication), which are a key security measure. Be very careful with this type of permission.
How cyber criminals can abuse this: by reading two-step verification codes, attackers can correlate the information with your Internet banking login information and access your account. Financial fraud targeting mobile banking apps can increase as a result of increased usage among smartphone/tablet users.
6. Storage permissions
This category allows apps to access and modify the files stored on your mobile device, be they music, photos, documents or something else. This also means that dangerous apps you grant access to can delete files stored on your device.
How cyber criminals can abuse this: replacing a harmless file with a malicious one can happen if you allow apps to modify your device’s storage. From there, a malware infection can spread like wildfire.
7. Connectivity permissions
We’re not just talking about Internet access here. Bluetooth and NFC are also involved. This means that apps with connectivity permissions can download data onto your device or collect and send data from your device to servers on the web.
How cyber criminals can abuse this: attackers routinely use the Internet to launch and spread malicious code and, consequently, compromise devices and the data on them. Carefully evaluate which apps you grant these important permissions to.
Now that you know what the main types of permissions are, let’s do a quick review of how you can better manage them. I’ll focus on the two most used mobile operating systems in the world: Android (82.8% market share) and iOS (13.9% market share).
Android app permissions
There are two ways you can see what permissions an Android app asks for:
When you install the app, you can see them in the app page’s details (check for Permission details) and in the screen that pops up to ask for you to grant the permissions the app asks for.
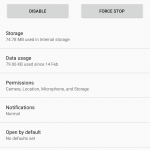
And you can also go to Settings >> Apps on your Android device and tap the app you want to check. Scroll to the bottom of the page to see what permissions the app currently has.
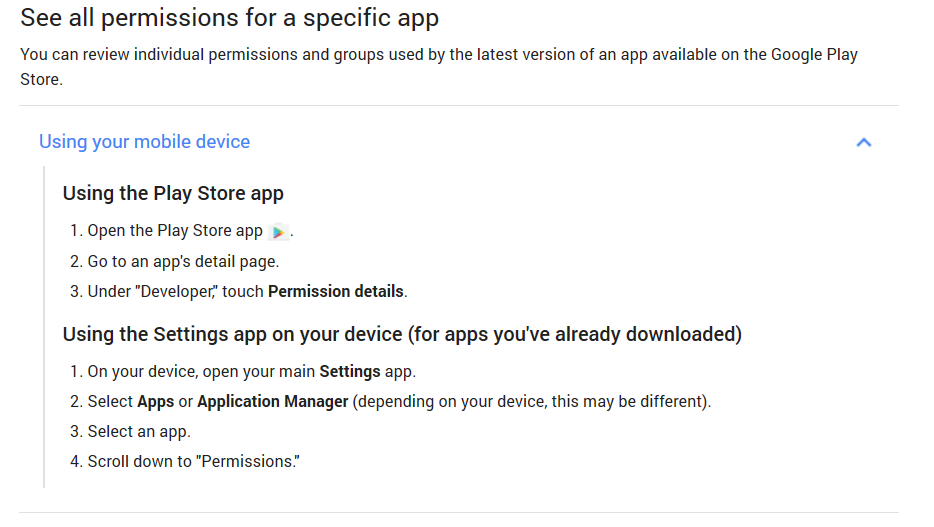
Here’s a quick recap, directly from Google:
If you’re a bit of techie, you can also read the permissions manifest dedicated to Android app developers. It explains various permissions, so you can use it as a resource in case you come across a permission you don’t understand.
TOP TIP:
Use Clueful Privacy Advisor or the SnoopWall Privacy App to evaluate the apps on your Android device and see what you should uninstall or manage more attentively.
iPhone app permissions
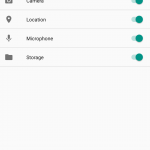
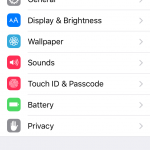
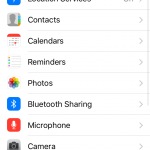
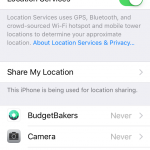
In iOS, things are a bit simpler. Go to Settings >> Privacy. From here, you can manage how apps use your location settings, contacts, calendars, reminders, photos, Bluetooth connection, photos, microphone, camera and more.
You can simply move the toggle to adjust the app to your preferences. The app will still run, but some of its functionality may be impaired, so keep that in mind.
Permissions can change over time
If you’ve granted an app a set of permissions, it doesn’t mean that things are permanent. In time, applications may ask for additional permissions or (rarely) give up on asking for certain types of access.
On Android, when an app changes the permissions it asks for, you’ll have to manually update it, even if you’ve set your Play Store to update your apps automatically. When manually updating the app, you’ll review the new permission requests for a chance to decide if you agree with them or not. All the new permissions will be marked by the word “New” next to them.
Useful read: 12 most abused Android app permissions
On iOS, you won’t see this. If an app needs your permission to access a software or hardware feature, it’ll ask for it the moment it needs to, not before or upon installation. So even if it’s a new permission, the process will be the same.
Cyber threats targeting mobile devices
Given that there are over 1.4 billion active Android devices and 1 billion active iOS devices in the world, cyber criminals can’t possibly pass on this huge market.
Mazar BOT, the Android malware we reported on in February and April 2016, is proof of just that. Industry reports have been announcing an increase in mobile malware, as cyber threats directed at mobile devices affect individual users and organizations alike (in all industries).
Although Android devices are more prone to malware attacks, iOS devices aren’t unscathed either. But with more control and stricter rules, the App Store manages to do a much better job at keeping malicious apps at bay. And that also applies to the operating system’s architecture, in comparison to Android.
From spyware, to adware, phishing apps, ransomware and apps that tie your phone into a botnet, you’ll find that mobile threats are very similar to cyber threats that have been targeting PCs for so many years now. And their diversity will probably increase as cyber criminals start investing more resource into developing and distributing malicious code via cyber attacks.
[Tweet “Useful guide to app permissions (web, OS, mobile, social) – helped me secure my devices:”]
Conclusion
Devices are only as safe as their users. And this report shows that the difference between perceived app security and reality is HUGE! It’s not a general impression, the numbers tell it like it is.
So maybe it’s time we all start taking mobile security seriously. Our mobile devices are not just an accompanying device, but they often hold much more data and value than even our laptops. And they’re much more vulnerable to attack.
Keep an eye out for trouble and don’t click “Allow” unless you know what you’re doing.



 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security