Contents:
Adobe Flash is the technology that both made the Internet into something you love and exposed you to getting hacked via Flash vulnerabilities. It will die also in 2020 as its makers will pull support from it.
Until then, make sure you know what Adobe Flash is, what Flash vulnerabilities are and how you can avoid getting your data compromised.
First of all, here is how to disable Flash Player in your operating system:
- On Windows, open the Start menu, type “Programs and Features” or “Apps and Features” for Windows 10 into the search bar, and hit Enter. Find “Adobe Flash Player” in the program list, and double-click to open the uninstall dialog.
- On MacOS, download the Adobe Flash Player Uninstaller, find your Mac OS version by clicking the Apple icon and choose About This Mac. Input that information in Adobe Flash Uninstaller and remove Adobe Flash from your system.
For popular browsers, this is how you disable Adobe Flash Player:
- In Chrome: go to chrome://settings/content, click Advanced Settings, click Flash and select Ask First, so you will be warned if a website you visit uses Flash.
- In Chromium: Type about:plugins in the address bar of the browser window, click Details in the right upper corner, find Adobe Flash or Shockwave Flash and click the Disable button.
- In Edge: go to the top-right corner and click the three dots. Scroll and go to View advanced settings, then deselect Use Adobe Flash Player
- In Firefox: click the menu button in the top right corner and choose Add-ons. It will open Add0ons Manager. Then select the Plugins panel, find Adobe Flash Player and select Never Activate.
This is why we recommend this.
You, me and millions of other people in the world use Flash Player. To most of us, it’s a necessity and we don’t pay much attention to it because it’s that thing that runs in the background that some apps need in order to work.
But here’s why you should care:
Adobe Flash is one of the preferred methods that cybercriminals use to attack users worldwide!
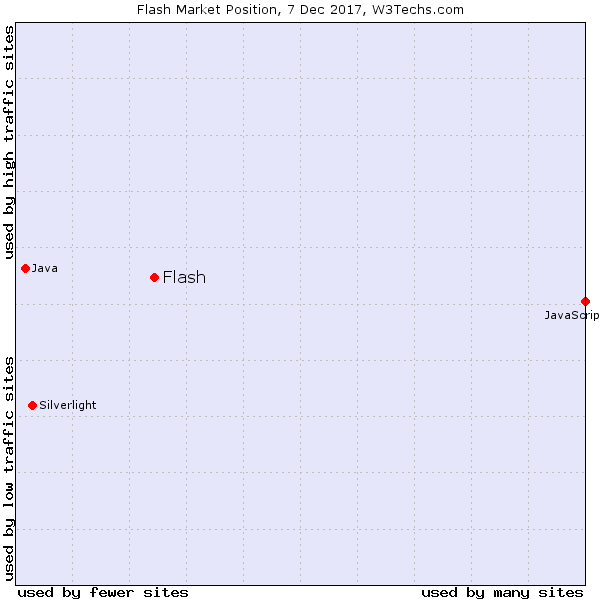
You might wonder why, so I’m going to take you on a short and informative ride through its troubled history, showing how all this affects you specifically.
Here are some numbers to start you off with:
- more than 1 billion devices are addressable today with Flash technology
- more than 20,000 apps in mobile markets, like the Apple App Store and Google Play, are built using Flash technology.
- 24 of the top 25 Facebook games were built using Flash technology. The top 9 Flash technology-enabled games in China generated over US$70 million a month.
- More than 3 million developers used the Adobe Flash technology to create engaging interactive and animated web content.
But here’s the worrying statistic of the set that Adobe provides on the official page:
- More than 400 million connected desktops update to the new version of Flash Player within six weeks of release.
Six weeks is a very long time when it comes to cybersecurity. In six weeks, millions of Flash users can be compromised. And the worse news is that they usually become victims of cyber attacks.
At the beginning of February 2018, CERT from South Korea rang the alarm bells for a zero-day exploit of North Korean origins.
The CVE-2018-4878 vulnerability impacted Flash versions 28.0.0.137 and allowed malicious hackers to execute code across Windows, Linux, macOS and Chrome OS.The vulnerability was exploited to embed malicious Flash content in Office Documents who then were spread via email.
According to FireEye, the malicious group taking advantage of this vulnerability was Group 123, of possible North Korean origins. Adobe delivered a patch after a week.
If you’re not using Heimdal™ Threat Prevention to automatically update your apps, we highly recommend you apply the Flash patch yourself as soon as possible.
That is if you’re still relying on Flash, even though the numbers don’t look good.
Do you how many Adobe Flash vulnerabilities were identified in 2017 alone?
And out of those 63 security vulnerabilities, 57 were critical, allowing information exposure, allowing attackers to bypass intended access restrictions and obtain sensitive information via unspecified vectors or to execute arbitrary code.
Translation: vulnerabilities in the code provide cyber-criminals with the opportunity to infiltrate their own code into the victims’ computers. From there, they can do pretty much what they want, including collecting your login data, your credit card information or encrypting your computer and asking a hefty ransom.
[Tweet “More than 63 security vulnerabilities affected Adobe Flash users in 2017!”]But what does Flash actually do and why do we need it?
Adobe created Flash (formerly called Macromedia Flash and Shockwave Flash) as a platform that allows developers to create vector graphics, animation, browser games, rich Internet applications, desktop applications, mobile applications and mobile games.
Here’s what Flash can do:
- Display text and graphics to provide animations, video games, and applications
- Allows audio and video streaming
- Can capture mouse, keyboard, microphone, and camera input.
It can do lots of other things as well, but you probably already got the idea:
Flash is ingrained in your web browser, your applications, and the websites you use every day.
Fortunately, better technologies appeared and Adobe Flash is approaching the natural end of its life cycle, so support is being discontinued.
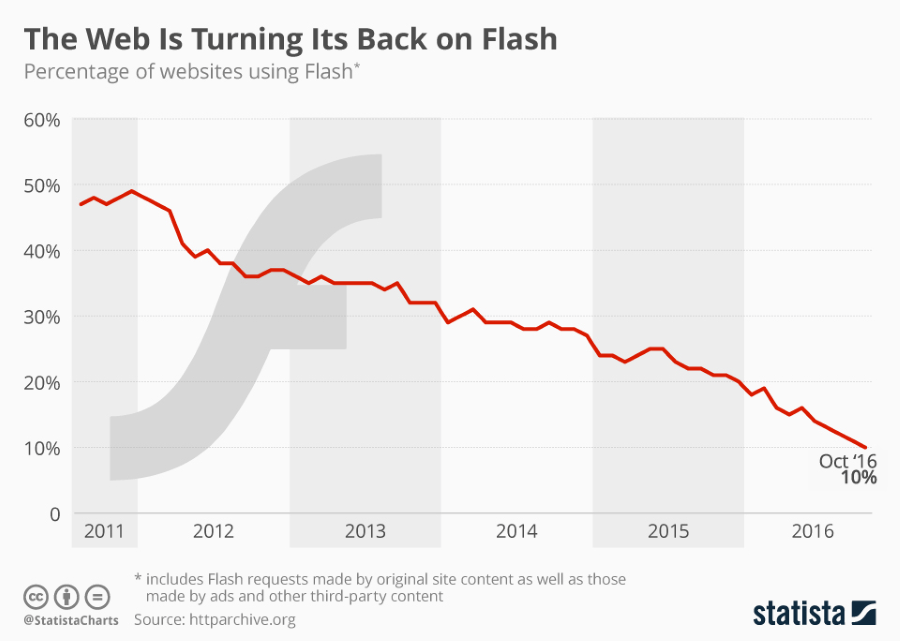
Statista shows a good trend, but the real numbers behind those percentages are huge.
(And you should protect yourself, not wait for Flash to die its natural death).
FACTS:
- Flash Player is used on 5.6% of all the websites in the world. This means more than 65 million websites
- Adobe Air, also built in Flash, is the base for thousands of popular apps, from banking tools to Disney content, as stated by Adobe itself.
- Adobe Reader is used for opening 200 billion PDFs every year and over 6 billion electronic and digital signature transactions are processed through Adobe Document Cloud every year.
Again, these numbers come from the horse’s mouth.
And they spell trouble when it comes to cybersecurity.
These apps and technologies are constantly exposed to vulnerabilities which turn into cyber threats which, more often than not, turn into fully-blown cyber attacks. Particularly concerning is the fact that PDFs are prime malware infection sources.
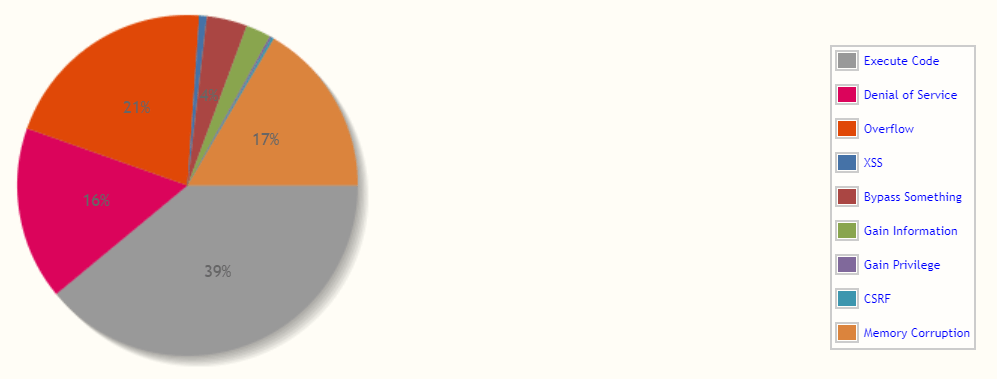
And these types of threats can sometimes be combined to incur even more damage.
Can’t software developers use other, more secure platforms?
For a long time, Flash has been the platform of choice. Now developers moved on to other technologies, but Flash still has a strong market share and Flash vulnerabilities abound.
In hindsight, Steve Job’s decision to give up Flash was very appropriate, although it may not have seemed so for many at that time.
Realistically speaking, chances are, as another platform will become the go-to solution for developers, it will suffer the same fate as Flash.
But let’s see how things actually work:
So how do cybercriminals use Flash vulnerabilities against you?
The more complex software gets, the more security holes it has. It’s as simple as that.
This is a simple version of how things happen in real life:
A vulnerability or more are discovered.
The software makers, in this case, Adobe engineers, work on an update to fix the Flash vulnerabilities.
They release the update – sometimes relatively fast, because users are sure targets for cyber attacks – and more bugs appear.
And this loop NEVER ends.

Here’s how cyber-criminals use vulnerabilities in Flash or other software to penetrate your system:
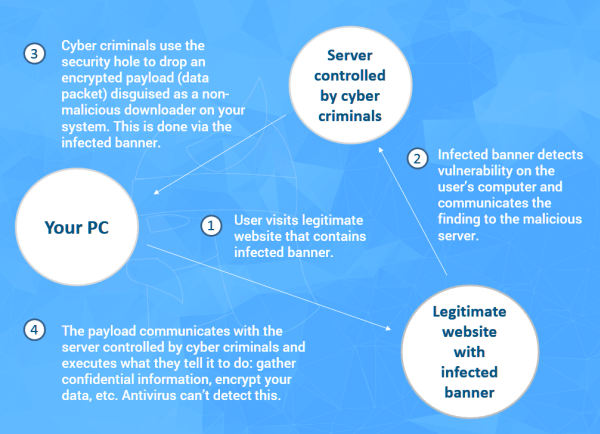
That’s why we insist that unpatched software is a huge security threat. By ignoring cyber threats and allowing vulnerabilities to exist, we’re fueling the malware economy, which is impacting all of us.
[Tweet “Do you know how cybercriminals can penetrate your system via a Flash security hole?”]Cybercriminals have a number of approaches they use when targeting their victims:
- They infiltrate advertising networks that deliver banners and infect those banners (which sometimes are displayed on healthy, normal websites)
- They infect browser games
- They share PDF documents that exploit vulnerabilities in readers, such as Adobe Reader, to drop ransomware or other types of malware
- They penetrate desktop applications and many more.
To put it bluntly: they can be anywhere and they also change tactics during their attacks.
Why exploits kits target Flash and go undetected until it’s too late
One of the most common methods of infection that cybercriminals use is exploit kits.
An exploit kit is a toolkit that automates the exploitation of client-side vulnerabilities. It targets browsers and programs that a website can invoke through the browser.
Here’s what Trustwave had to say about this in their 2017 Global Security report:
Trustwave conducted an experiment in 2016 running online ads that tested for vulnerable versions of Flash to gauge the cost of spreading exploits through malvertising. Researchers estimate an attacker could reach approximately 1,000 computers with exploitable vulnerabilities for about $5 — less than $.01 per vulnerable machine.
So it’s dirt cheap for malicious hackers to target you. Aaand incredibly profitable for them!
Cybersecurity specialist Lenny Zeltser explains why:
A key characteristic of an exploit kit is the ease with which it can be used even by attackers who are not IT or security experts. The attacker doesn’t need to know how to create exploits to benefit from infecting systems. Further, an exploit pack typically provides a user-friendly web interface that helps the attacker track the infection campaign.
Some exploit kits offer capabilities for remotely controlling the exploited system, allowing the attacker to create an Internet crimeware platform for further malicious activities.
We also examined exploit kits’ history in one of our security alerts. It seems they’ve come a long way since 2006!
Furthermore, exploits kits pose a serious challenge to traditional cyber security products, such as antivirus.
Antivirus can’t protect you from advanced exploit kits. Find out what can! [Tweet “Antivirus can’t protect you from advanced exploit kits. Find out what can!”]
Highly advanced exploit kits sometimes don’t even need to place a single file on your system, so antivirus is useless against them. Since antivirus employs a file-detection system to identify a threat or an infection, it won’t be able to block an exploit kit such as Angler.
There are, of course, next-generation anti-hacking tools that can help you enhance your protection against sophisticated threats, so I recommend you test them to see what fits your needs best. We explored here the anti-virus vs anti-malware dilemma and what the best protection is.
Hot topic: the Zero Day Flash vulnerabilities problem
Exploits kits are especially dangerous when they go after Zero-Day vulnerabilities. A Zero-Day vulnerability is a security hole in the software that is unknown to the software vendor. That means that cybercriminals can exploit that hole before any updates that can fix it are released.
Here’s the Zero Day scenario, as depicted in the 2015 Trustwave Global Security Report:

And here’s a headline from October 2017, as seen on Wired:
SECURITY NEWS THIS WEEK: RUSSIAN SPIES RUSH TO EXPLOIT THE LATEST FLASH ZERO-DAY
It’s about an Adobe Flash vulnerability that allowed malicious hackers to compromise Microsoft Word documents with Finspy malware. How did it spread? Those malicious actors posed as refugees and sent journalists a harrowing “personal” tales from the migrant crisis, knowing they will definitely open those documents.
So it’s not easy-as-pie to avoid Zero Hour exploits and exploit kits in general. It’s not impossible though! You just have to do a bit of research on your part to make sure malicious websites don’t affect you.
I recommend a mix of security products that include:
- an antivirus solution
- a product that ensures anti-exploit protection
- a security product that filters your Internet traffic for threats and blocks them before reaching your system
- and a patching tool that delivers software updates as soon as they’re available
Some of these products can be found standalone, and some of them include these features bundled. Do take some time to do a little research, it will save you a lot of trouble (and money) in the future!
When it comes to Adobe, its history of Zero Day Flash vulnerabilities is not something to ignore.
So how do you protect yourself from cyber threats targeting Adobe Flash?
If you’ve read this blog before, you must’ve heard this plenty of times. Still, here it goes again:
Keep your software updated at all times!
Now there are 2 ways you can do this:
- Manually
- Automatically
If you choose to update your software manually, you should never ignore an update prompt!
But what if you’re somewhere where you have limited Internet access?
Or click away from the update window?
Or turn off your computer by mistake, run out of battery, etc., etc.?
Then you should choose option number 2.
Flash can deliver automatic updates by itself or through various applications that have Flash built-in, such as Google Chrome.
The easiest way, however, is to use a patching application. It will update not only Flash but also other vulnerable software on your system, such as browsers. Install it, forget it, benefit from protection!
Then focus on the other important aspect! Exploits use your browser most of the time, so make sure you secure it properly. We put together the definitive list of steps to enhance your browser’s protection.
The question is….
Can you live without Flash?
Yes, you can, but you might find it annoying if you’re used to having everything ready to go.
Security specialist Brian Krebs did an experiment earlier in 2015 and tried to go without Flash Player for a month. Of course, it’s been a while, so nowadays living without Flash is pretty easy. There’s no reason why you should still have it on, at least not without serious protective measures.
In almost 30 days, I only ran into just two instances where I encountered a site hosting a video that I absolutely needed to watch and that required Flash (an instructional video for a home gym that I could find nowhere else, and a live-streamed legislative hearing).
We already stressed enough that you should not allow Flash content. Browsers already warn you so, the next time you see a message like this, please think twice about clicking Allow.
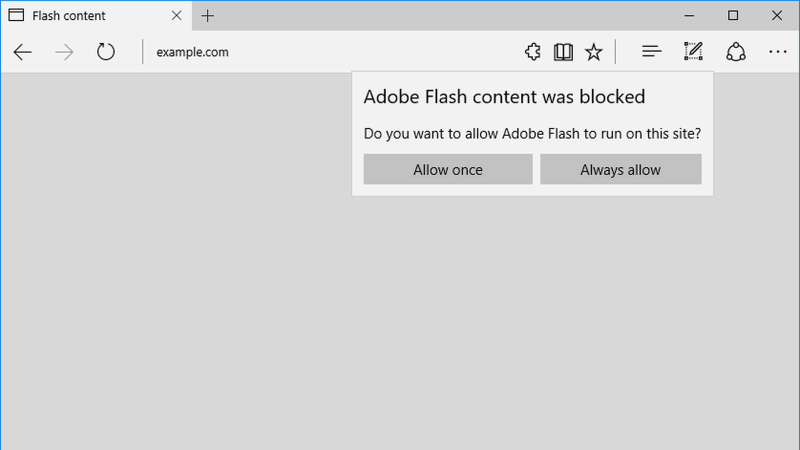
The risks of Flash far outweigh the benefits. Such is always the case when using free software – it may sometimes cost you your privacy or security, or both. Don’t let that be the case and avoid Flash vulnerabilities by simply not using this antiquated tech.
Keep your software up to date, use the appropriate cybersecurity tools and keep an eye out for trouble. That’s what you need to enjoy everything that the web has to offer!

INSTALL IT, FORGET IT AND BE PROTECTED
Download Heimdal™ FREE

 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security