Contents:
Today, there are few businesses that can survive without internet access. For many, it’s the primary method by which customers find, explore, and buy your product or services.
But here’s the issue: When you load a webpage, you create connections with other devices elsewhere in the world – over which you have virtually no control or oversight. By its nature, the internet offers an attractive open door for hackers to target your environment.
So how do you stay safe? DNS security is a complex business, but it’s essential if you want employees and customers to securely access the internet.
But first, let’s take a moment to understand more about the DNS and why it’s such an attractive entry point for hackers.
What Is DNS Security?
The domain name system (DNS) is essentially the phonebook of the internet. It’s the fundamental service that makes it possible for devices to connect to each other – however far away they might be.
DNS security refers to the techniques and practices of defending DNS infrastructure against cyber threats to keep it performant.
DNS Security Basics: How the Internet Works
To understand how the DNS works, imagine we’re going to visit an eCommerce site, ‘www.quickbuys.com’. To do that, you’ll probably go to your browser, and then type or copy the URL into the search bar.
From the perspective of you, the user, that’s really the end of it. But for your device to locate and connect to that website, it needs to first convert that URL into an IP address. The DNS is the service that makes this possible.
Once the IP address has been retrieved, your computer can then make a connection with the client device on which that website is hosted. Once a connection is established, the client device transmits ‘packets’ of information over the internet to your computer, which combines them together to load the website.
Crucially, accessing just one website can create hundreds of connections that run in the background while you browse – all of which can be attractive entry points for hackers. That’s where DNS-based security comes in.
How the DNS Works
When you go on the internet to visit a domain like Google – you’re not actually going to Google.com. You’re going to an IP address, which is a numerical code made out of four sequences. Basically, the DNS is the service that finds the IP address behind your URL and takes you to that particular website, page, or domain.
Andrei Hinodache, Cybersecurity Community Leader, Heimdal
Before we explain the basics of DNS network security, it’s helpful to first understand a little more about how the network is built and the process it uses to convert URLs into IP addresses.
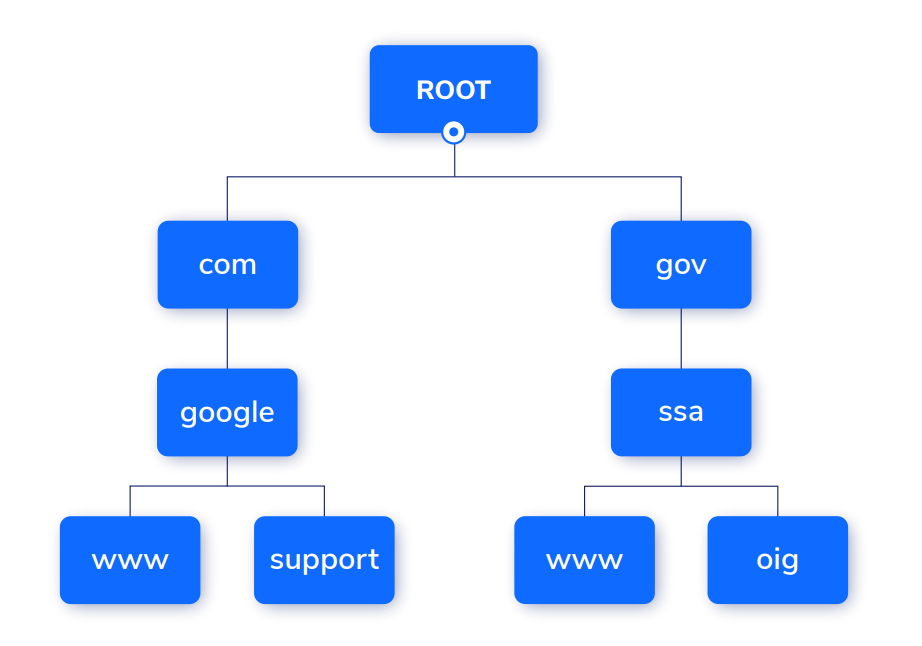
Let’s go back to our URL for a moment: ‘www.quickbuys.com’. As you can probably see from a basic glance, this has three main parts to it, though the DNS is actually reading these in reverse order:
- .com – The top-level domain, usually a recognizable acronym like .co/ .gov/ .org. There are a fixed number of TLDs that all domains have to choose from. Some websites might seem like they have customized TLDs, but they’re probably just using one associated with a small country like .so (Somalia) or .ai (Anguilla)
- quickbuys – The actual name of the website, this is referred to as the second-level domain (2LD). Unlike the top and third level domains, this has to be unique.
- www. – This is the third level domain (3LD) – and is actually the least important here. The default here is, of course, www., but organizations often have their own, such as with ‘mail.google.com’, where ‘mail’ is the 3LD. Some URLs don’t include a third level domain. Generally, it’s used to provide further clarity on where to direct web traffic to.
The system features four separate DNS servers, all of which have very slightly different jobs:
- Recursive server/ DNS server – The first stage of the process, this receives queries from the browser when you type an address into the search bar. It’s responsible for querying and retrieving information from the other three servers in this list.
- Root nameserver – This begins the process of translating a URL into an IP address. Based on the URL provided by the user, it retrieves the address for the TLD nameserver and sends it back to the recursive server.
- TLD nameserver – Then, the recursive server queries the relevant TLD nameserver, which responds with the IP address of the authoritative nameserver.
- Authoritative nameserver – The final server in the process – this holds the actual IP address records. If a match exists, this server will respond with the full IP address of the website being targeted.
So why do we need so many different servers to find one IP address? In essence, it works like a library index, where the top level domain is roughly analogous to e.g. the history or politics section. The goal is to break the internet down into (more) manageable chunks so it’s quicker to retrieve the right IP address.
At the risk of massively oversimplifying – this is pretty much how the internet works. But there’s one other element here that it’s important to be aware of: the DNS cache. This is a temporary repository of known IP addresses that you’ve already connected to that avoids your computer having to go through the whole DNS process each time you want to reconnect.
To continue the library metaphor, it’s a bit like if you were to note down the book’s location on the back of your hand so you don’t have to look it up from scratch next time. It’s important to be aware how this works, because the DNS cache is often manipulated to carry out security attacks. Effective internet security isn’t just about ensuring secure DNS servers.
Development of the DNS
This system has been at the heart of how the internet works since its earliest days. In fact, it was first rolled out in 1983, having been designed by Paul Mockapetris. At that point, devices were quickly beginning to go online, making the previous system too cumbersome.
Since then, there have been DNS security extensions, add-ons, and improvements, which we’ll elaborate more on below. But the basic infrastructure is still the same. Around the world, the system is managed by a network of 13 root servers, which collectively triage some 65 trillion monthly DNS queries.
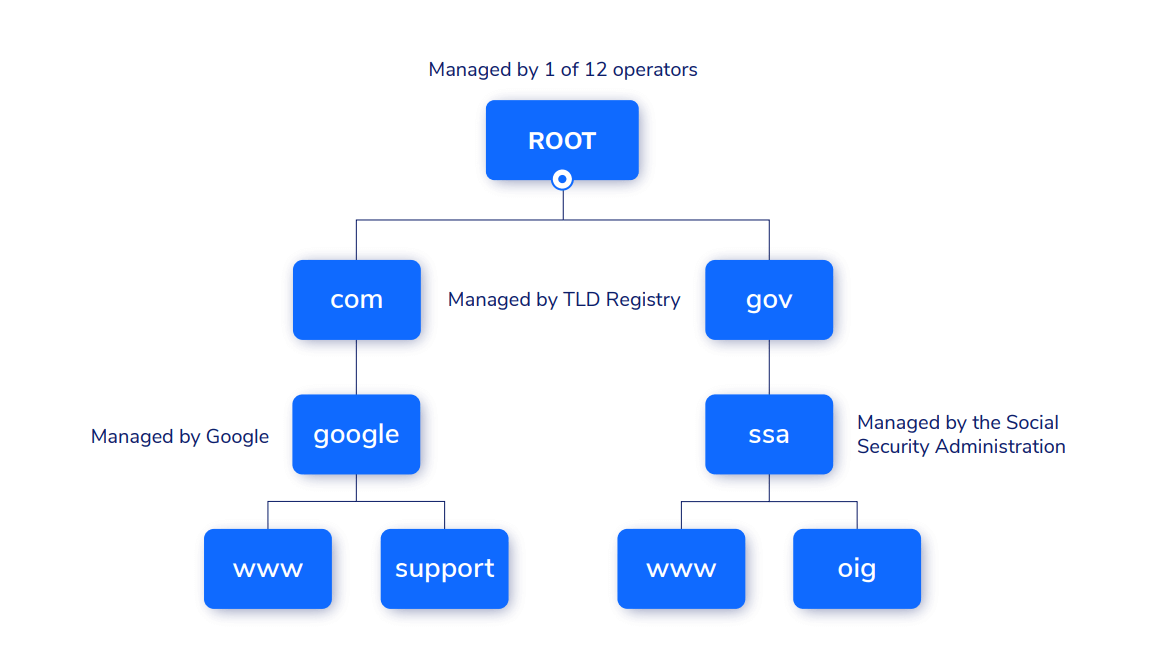
Crucially, the DNS isn’t owned or managed by a single company. In fact, it’s a decentralized network run by several organizations, government bodies, and universities – right around the world. You can find the full list of servers here.
The benefit to this system is clear: No one company, organization, or nation-state owns the internet. But the challenge here is there’s no single entity responsible for making that network secure. This is why DNS security is such a challenge for organizations large and small.
DNS Security (or lack thereof…)
If there’s one thing you take away from this blog, it should be this: The DNS is insecure by design. The fundamental infrastructure was rolled out when the internet was much smaller and more limited than it is now. Simply put, there was little to no need for cybersecurity in the early 80s. Needless to say, that’s changed significantly in the years since.
That means the DNS network has become one of the most popular targets for hackers. In fact, a recent study by IDC found that DNS-based attacks comprise some 24% of data theft, with 88% of organizations being affected in one way or another.
There are several ways that attackers target you via the DNS network. Generally, they’re trying to infect your IT environment with malware, remove sensitive data, or overload your servers to create a denial of service. More often, they’re using a combination of all these techniques to avoid detection.
So, if there’s no built-in DNS network security, how do you stay safe?
As ever in cybersecurity, there’s no one-size-fits-all approach. Hackers have many ways of manipulating your DNS to perform or lay the groundwork for a cybersecurity attack. Defending against them requires a combination of different methods – many of which we discuss in more detail below.
It’s helpful, however, to start with the oldest and most widely known: the Domain Name System Security Extensions (DNSSEC).
This is essentially a security ‘layer’ that was designed to resolve the fundamental insecurity of the internet in the late 90s. It requires connections between the recursive and authoritative servers to be identical, essentially making it harder for hackers to spoof or redirect the IP address. This was the first security DNS extension to address security and has become widely used since. It’s the basis for many of the DNS-based security tactics we discuss below.
DNS Attack Methods: And How to Protect Against Them
Common attacks usually come in multiple stages. If the hacker installs all the malware at once, it’ll get picked up and fought by the antivirus or other security tools. If they inject the malware bit by bit and do reconnaissance on the way, they’ll see exactly what security tools you have and can find out how to bypass them.
Andrei Hinodache, Cybersecurity Community Leader, Heimdal
To stay safe against DNS-based attacks, it’s important to understand how hackers are using the system to target your IT environment. Generally, there are a few things that hackers are looking to achieve across all these methods:
- Denial of service – This is when hackers try to overload your IT infrastructure to take down your systems. The goal here is to create so much traffic to your website that it’s impossible for legitimate customers to access your services, causing a loss of normal business operations.
- Inject malware – Once inserted, malware can do untold damage to your IT environment. It can give the hacker remote access, send them sensitive information, or lock down your IT environment entirely. Often, malware is used to aid a wider attack, since it can be a useful way to gain a foothold or perform reconnaissance within your network.
- Steal sensitive data – This is often the end goal of an attack since hackers can sell this for a profit on the dark web. There are many ways to perform a data breach, such as injecting malware that directly sends information to their own device. Alternatively, they can manipulate end-users into voluntarily sending that information, often by redirecting them to fake website pages where they enter their login credentials.
Here are the six main DNS attack methods that hackers use to target your IT environment – and how you can protect against them.
1. DNS Spoofing
DNS spoofing is a process where malware is used to change the endpoint DNS configuration, allowing the attacker to see what DNS queries have been sent, and redirect them to their server, showing you other results. In this case, if you were to search for Heimdal Security, it’s not going to show you our website – it’ll show you instead whatever IP address the hacker wants to send you to – so you can put your information in for them to steal.
Andrei Hinodache, Cybersecurity Community Leader, Heimdal
Also known as DNS cache poisoning, the goal here is for hackers to intercept the website you’re trying to access and instead redirect you to a domain owned by the hacker.
The hackers achieve this by injecting false information into the DNS resolver cache. Then, when you go to type a URL into the search bar, the DNS resolver retrieves the false IP address from the cache and sends you on to the hacker’s website.
From here, the cybercriminals might use this website to mine sensitive information (i.e. personal details, passwords) in the same way as with a traditional phishing strategy. They might also use the website to infect the target IT network with malware. This step is often used as the prelude to a wider attack.
DNS spoofing is possible because recursive servers were built with the user datagram protocol, or (UDP). Essentially, this protocol makes connections faster by avoiding the need to verify whether a connection is legitimate. This is the key cause of why hackers can get away with DNS spoofing.
How to Protect Against DNS Spoofing
Luckily, a series of well-established solutions have been rolled out in the industry to tackle this issue. The most well-known are the DNSSEC and HTTPs. These are essentially security layers that sit on top of the basic DNS network to perform additional security checks.
Both examples require the recursive and authoritative servers to perform a ‘digital handshake’, essentially verifying that the IP address being accessed matches that on the authoritative server. These layers are often rolled into operating systems and cloud environments by design, meaning there’s a good chance you’re already using it. If not, advanced DNS security solutions can help implement this preventative DNS protection.
2. DNS Tunneling
DNS tunneling attacks are another common tool used to steal data or infect malware. The strategy isn’t malicious by design – in fact, it’s the basis of VPN technology that allows people to connect to remote servers. But in this context, it generally uses malware to create a backchannel into your organization and bypass firewalls along the way.
Here’s how it works: First, a criminal registers a new domain, generally hosted on their own server, where DNS tunneling malware is also installed. Next, they’ll aim to infect a computer in the target network (ie a user’s device in your IT environment) with malware. They might do this using DNS spoofing, phishing, or any other range of tactics.
From there, the malware-infected computer will attempt to connect to the hacker’s domain. This connection involves sending a DNS request (just as you would to connect to any IP address on the internet). These are allowed through company firewalls since the internet couldn’t function if they weren’t.
Once a connection is established, the infected device will route internet traffic through the hacker’s remote server. From there, the hacker can inject malicious code or programs into the system, usually aiming to steal data directly or to aid a wider attack.
How to Protect Against DNS Tunneling
For this technique to work, hackers generally need to create a foothold through malware. That’s why the best DNS protection here is preventative; installing the latest anti-malware solutions and ensuring you’re up to date on vulnerability and patch management
There are also more sophisticated DNS threat prevention tools, designed to identify and prevent real-time DNS tunnel requests, using techniques like anomaly detection and payload analysis. These connections are often highly anomalous, carrying unusually large amounts of data, so the most up-to-date tools aim to identify and block these requests as they happen.
3. DNS Rebinding
DNS rebinding has a similar goal to DNS spoofing: to replace whatever website you’re trying to access with whichever one the hacker wants to direct you toward.
The goal is to get around the same-origin policy (SOP), which is a defense mechanism that browsers use to restrict how websites from different origins interact with each other. Here, the origin is defined by the port, domain, and protocol.
If these don’t match, there’s a good chance malicious activity is taking place. Therefore, the SOP prevents malicious actors from sending HTTP requests to IP addresses that don’t match their own.
To get around this, attackers create or take control of a malicious DNS server that’s designed to answer DNS requests for the hacker’s domain.
Then, they direct a user in the target organization to their domain, often through phishing or using other tactics on this list.
Then, the hacker’s server returns the IP address for their website, as normal. But instead, the hacker has modified this IP address to have an incredibly small time-to-live (TTL) value, often just a second.
The TTL governs how long the IP address is retained in the target organization’s DNS cache, and ensures a full DNS request is made again almost immediately after the target first accesses the hacker’s website.
From there, the hacker can substitute their malicious website’s real IP address for one within the victim’s own network. This then circumvents the SOP policy and allows hackers to inject code, malware, or execute applications.
How to Protect Against DNS Rebinding
There are a few steps that organizations can take to protect against these attacks. The most effective is to set a minimum period of time for TTL cache values, which prevents the hacker from forcing the victim’s device to make multiple requests to the same DNS server in a short space of time. This is known as DNS pinning.
Another way to avoid this is to implement HTTPs or DNSSEC. Like with DNS spoofing, this forces the recursive and authoritative server to perform a digital handshake to verify that the IP addresses match, thereby preventing DNS rebinding.
4. DNS Amplification
DNS amplification is a form of distributed denial of service (DDOS) attack, which aims to overload a target organization’s server with so much traffic that it can’t perform its usual function.
Here, the hacker is trying to send multiple small queries from different devices that all result in a disproportionately large response for the server. It’s a bit like if ten people call a restaurant from different places and all ask for everything from the menu. Easy to ask, near-impossible to deliver.
So how does it work? First, the hacker compromises a target device, using malware, phishing, or other techniques on this list. They’ll then send a DNS request to the DNS recursor using a spoofed IP address for the target victim’s device (rather than their own).
Generally, these are designed to create the largest possible response. The DNS server will then send a huge amount of responses to the target victim’s IP address, thus overloading it and usually taking the service online.
How to Protect Against DNS Amplification
By its nature, this is a difficult threat to prevent, because much of what the hacker is doing doesn’t take place in your IT environment. Often, that means internet service providers (ISPs) can proactively prevent these attacks by identifying spoofed IP addresses – but this is by no means a guarantee. They might also just take your website offline anyway to avoid them having to deliver the traffic.
The best approach here is preventative. For DNS amplification to work, hackers need to target insecure recursive servers. If these are badly configured and/or left open, it makes it much easier for hackers to access.
DNS resolvers should be configured to only provide services to endpoints within a trusted domain, thereby preventing the hacker from spoofing the IP address in the first place.
5. DNS Typosquatting
This is a pretty rudimentary tactic compared to many on this list, but it can still be surprisingly effective. To do this, hackers register domain names that are common typos for the websites of unknown brands, government agencies, or social media sites.
If you’ve ever misspelled a website in the search bar and ended up on something that just didn’t look right, you’re probably familiar with this. (Though often the perpetrators are just trying to generate accidental traffic to their site, rather than conducting a malicious attack).
From here, DNS typosquatting works like a fairly standard phishing campaign. Once the unsuspecting user has landed on the website (often disguised to look just like the real thing), they can be manipulated into entering sensitive information, downloading malware, or executing files.
How to Protect Against DNS Typosquatting
The best way to do this is to register misspellings of your own domain before the hackers have the chance to do the same. Then, you can simply redirect these back to your normal website. Try typing ‘www.faceboook.com’ into the search bar of your favorite browser; you’ll end up on the standard website despite the typo.
If you identify domains that have already been claimed by hackers, you can file a complaint with the Uniform Domain-Name Dispute-Resolution Policy (UDRP) to have it removed.
6. UDP Flooding
This is another type of DDOS attack, designed to overload a system or server. For this to work, the hacker has to send packets via a UDP connection to a device in the target organization’s IT environment.
Usually, when the recursive server encounters UDP packets, they’ll check to see if any programs running have made requests that match the incoming information.
This is designed to prevent random connections from sending malicious data. But in this case, having the connection refused is exactly what the hacker wants.
As the server processes the request, it uses up resources. And if the hacker can send enough requests at the same time, they’ll overload the server to the extent that it goes offline. This is a good example of hackers using a DNS defense system against itself.
How to Protect Against UDP Flooding
Again, this is a difficult one to do conclusively, because you can’t really control incoming traffic to your server. One common solution is to limit the response rate of packets so servers essentially refuse incoming traffic if it goes beyond a certain point. This can help avoid outages but also risks filtering out legitimate traffic as well.
However, there are a range of realtime monitoring solutions on the market that can help identify and mitigate DDOS attacks as they happen.
Organizations are also increasingly taking advantage of cloud services that can distribute huge loads across multiple servers, thereby reducing the strain and the chance of an outage, even if a successful DDOS attack does occur.
How to Secure DNS Systems Once And for All
When it comes to DNS security, there’s no single method, software, or tool you can use to prevent hackers from targeting your IT environment.
But with the right software, you can significantly increase the chances of identifying and reacting to these threats when they do occur.
So how does it work? A state-of-the-art secure DNS tool like Heimdal® takes advantage of machine learning and anomaly analysis to effectively detect attacks like those we described above as they’re happening.
Common tactics like DNS amplification, tunneling, and others are often highly unique and anomalous, meaning advanced scanners can often identify and prevent them.
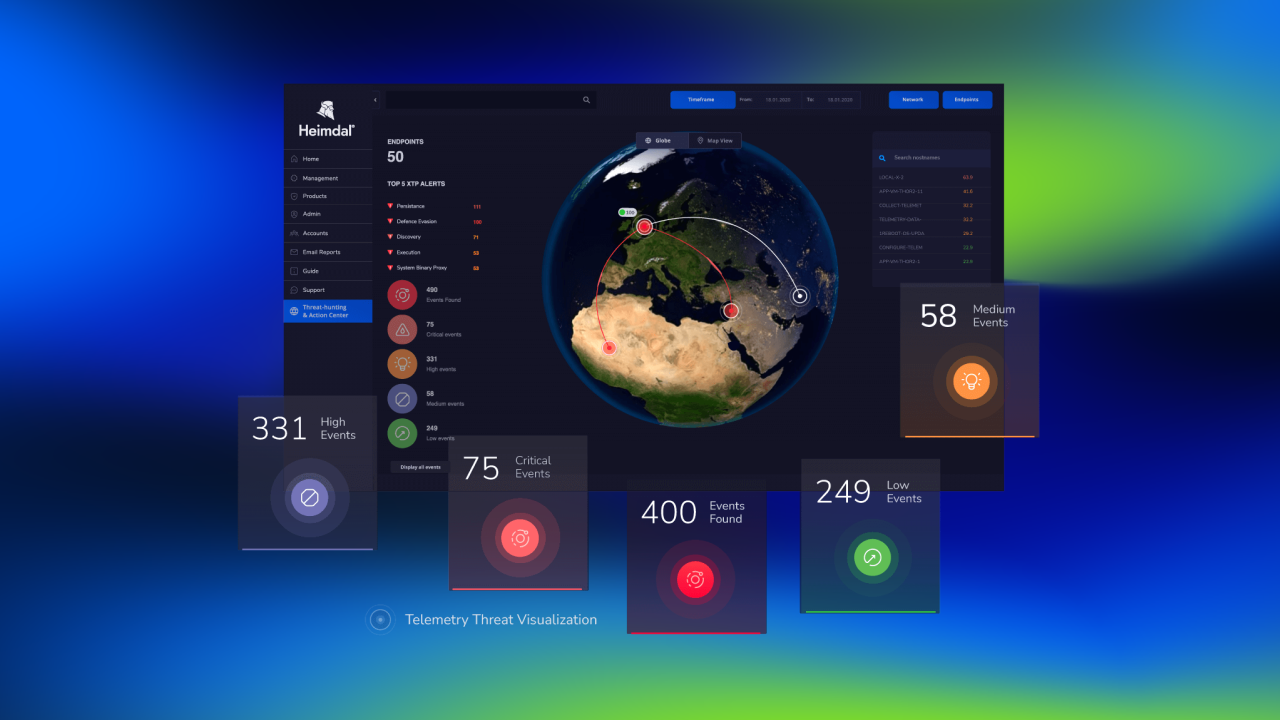
With Heimdal, you can monitor realtime traffic, in order to block infected domains and halt communication with hackers’ devices. Here’s how it works:
- Traffic filtering – Heimdal’s DNS Security Endpoint effectively identifies cyber threats at all connection levels. This allows you to defend against DNS attacks designed to circumvent traditional firewalls and antivirus measures.
- Machine learning predictions – Our DNS Security Endpoint product has a 96% accuracy when it comes to predicting future threats. This is down to our exclusive Predictive DNS technology, which uses state-of-the-art machine learning algorithms to identify anomalous behavior.
- Threat hunting – Identify malicious URLs and processes, then track the hacker’s activity and progress through a code-autonomous endpoint DNS threat hunting solution.
Heimdal®’s Threat Hunting product is an effective and robust security layer that monitors all incoming and outgoing DNS traffic to find and remove malicious traffic before it has a chance to steal your data or disrupt your services.
FAQs
What is DNS security?
The DNS is essentially the phonebook of the internet, translating URLs into IP addresses and allowing devices around the world to connect with each other. The system, rolled out in the early 80s is insecure by design, meaning organizations need to use a range of different tactics and procedures if they want to stay safe. These security methods all come under the umbrella term ‘DNS security’.
What is DNS protection?
DNS protection, or DNS security, is the series of tactics, tools, and procedures that organizations go through to ensure their IT environments are secure from internet-based attacks. This can include implementing DNSSEC, HTTPs, or other ‘security layers’ to monitor and verify incoming internet traffic.
How to secure DNS servers
There’s no one method for effective DNS security. A good place to start is to implement DNSSEC – a commonly accepted DNS security layer. Making good use of vulnerability scanners, anti-malware, and threat detection tools can also prevent hackers from gaining a foothold. The most up-to-date DNS security tools use machine learning and anomaly detection to detect and prevent realtime attacks as they happen.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security