Contents:
Following DNS best practices helps keep your business stable and secure, even when facing potential threats.
Many companies are shifting to cloud-based services, leaving traditional on-site computing behind. This transition to a cloud-based, remote work environment makes following DNS best practices more important than ever.
Experiencing a DNS attack can prevent your team from accessing vital business information. When you can’t reach your DNS servers or trust their data you risk losing your present or potential customers’ trust.
To help you create a safe and dependable DNS infrastructure, I’ve put together a list of the most important practices to take into account.
- Make sure DNS is highly available and redundant
- Only make available what is necessary
- Conceal your primary servers
- Use your local DNS server
- Limit access
- Safeguard the integrity of your data.
Implementing DNS best practices benefits
Applying DNS best practices comes with several key benefits:
Enhanced security
Applying DNS best practices mitigates the risk of DDoS attacks or DNS hijacking, like spoofing, tunneling or rebinding. The result is integrity and confidentiality for your network.
Increased reliability
Consistent and reliable DNS resolution means minimum downtime and better access to network resources and services.
Better performance
Optimizing DNS queries and responses reduces latency and improves the overall speed of network communication.
Scalability
Efficiently managing DNS traffic and resources supports the growth of your network infrastructure and enables you to accommodate more users and services.
Better compliance
Following DNS best practices helps meet regulatory requirements. A structured monitoring and logging process helps in troubleshooting and ensures compliance with industry standards.
Better user experience
A healthy DNS environment means smooth access to services and applications for your users. It creates an overall better experience for customers and employees.
DNS best practices
Implement redundancy
In case of a DNS attack or any other server failure, redundancy helps maintain service continuity.
All email, file-sharing, and Active Directory services depend on reliable DNS performance. For example, the Active Directory uses the Domain Name System to locate services and domain controllers within the internal network. Each domain controller registers service (SRV) records in DNS signal its presence and services. In case the DNS server fails, login failures and authentication issues would occur.
So, the DNS infrastructure must be always available to keep data networks working.
Use at least two DNS servers – a primary and a secondary one – to ensure availability and reliability. Primary DNS servers handle all DNS queries for a domain and store all relevant DNS records. Secondary DNS servers host read-only copies of the zone files. They work as a backup in case the primary ones fail or get hacked. Also, secondary DNS servers help with load balancing. Setting up a secondary DNS server mitigates the risk of Denial-of-Service, by using a technique called round-robin DNS.
You should use redundancy for both internal and external DNS servers.
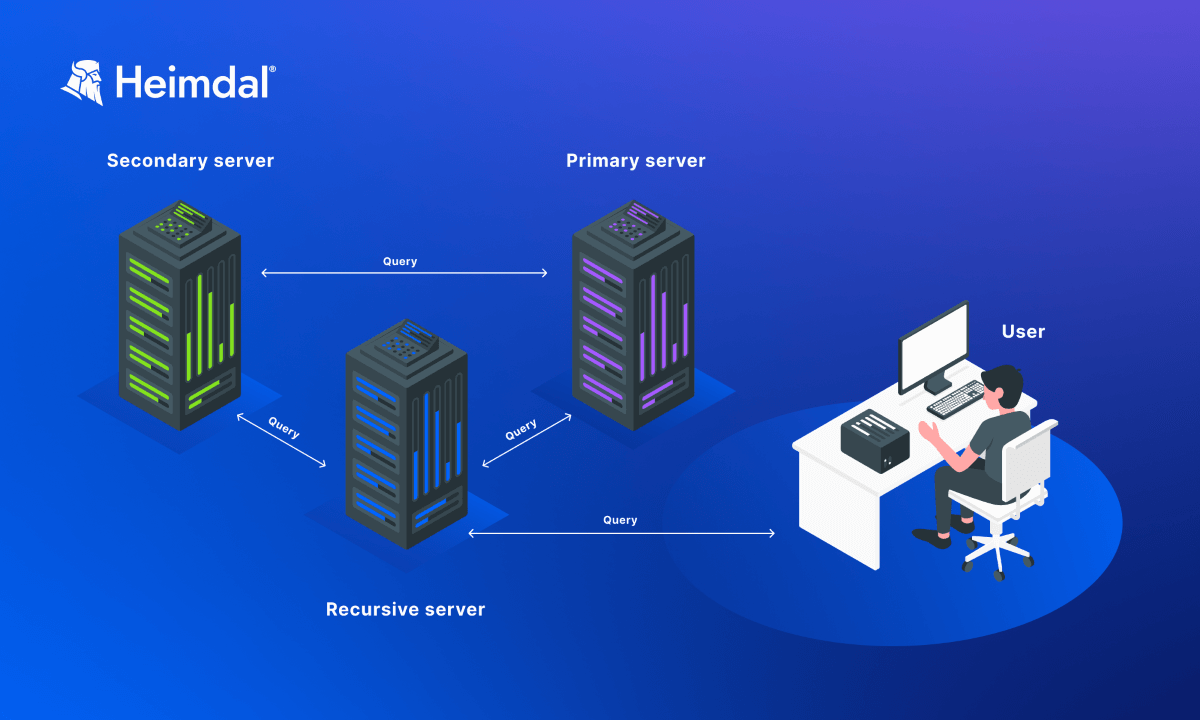
Internal DNS servers cover communication for internal device only.
External or public DNS servers handle DNS queries from the public internet. In their case, companies should use geographically dispersed servers to protect against local disruptions, like natural disasters or power outages.
This means placing the DNS servers in different physical locations around the world. This way, if one location experiences a problem the servers in another country still provide DNS services.
Secure access to DNS servers
DNS servers should only store and provide the necessary data for those users and applications that need it to accomplish their tasks. Configure an Access Control List (ACL) and enforce privileged access management policies to make sure the main servers in your company are only accessible to authorized IT staff. All internal users having access to your principal DNS servers poses serious security risks.
In addition to firewall ACLs, zone transfers should be secured by on-server Transaction Signatures (TSIG). TSIG secures the communication between the primary and the secondary DNS server. This method uses a shared secret key and one-way hashing to make sure that DNS packets come from an authorized sender. 
Hide sensitive DNS records
External users should not be able to see any data about your primary DNS server. It should not appear in the name server’s records or respond to any queries. Limit the number of DNS records that are exposed to public. Never share with public what version of DNS software you use.
Preventing anyone other than those in charge from accessing the primary nameservers helps secure DNS data integrity. When using publicly accessible nameservers, you must protect the primary nameservers with a firewall, implementing appropriate rules to ensure that only the secondary nameservers can query and transfer to the primary nameservers.
Disable recursion for external servers
DNS servers that are reachable from the public internet should be authoritative-only. External users are not required to query your recursive DNS servers. An elevated configuration involves a server only responding to recursive queries for the specific zones for which it is the authoritative server.
Monitor DNS traffic
Once you have configured your DNS system, monitor inbound and outbound connection attempts. Additionally, you should enable DNS filtering, to spot and block malicious communication requests.
Firewalls are an effective network security measure but are not self-sufficient. Unusual DNS queries can be Indicators of Compromise (IoCs) for ransomware attacks, data exfiltration or other threats. Also, unexpected and unmotivated traffic spikes can point to a DDoS attack attempt.
Keep and analyze DNS logs. In case of an attack, DNS logs can help you:
- better understand the nature of the incident
- track the source of the attack
- block other malicious attempts
Setting up an alert system to monitor unusual DNS requests allows you to catch in time any malicious activity. An AI-based DNS security solution, like Heimdal’s, saves time by streamlining the process and mitigates the risk of a DNS attack.
Use your local DNS server
Most large companies have offices in various countries. Each office should have a local DNS server, to speed up DNS request responses.
A user experiences slower load times when a query goes over a wide area network to a distant nameserver. A regular web page could connect to dozens or hundreds of sites, and each one might call for a DNS lookup before loading the page.
The latency between both the end user and the designated nameserver increases load times and the workload on the support desk.
All devices load faster when using the nearest DNS server. By using a local DNS server, you relieve some of the strain on the remote server at headquarters and enhance its functionality.
Enable DNSSEC
Use DNS Security Extensions (DNSSEC) to protect against DNS spoofing and cache poisoning by digitally signing your DNS data, ensuring its integrity and authenticity. DNSSEC digitally signs DNS information so nameservers may validate its accuracy before responding to queries.
The Internet Corporation for Assigned Names and Numbers (ICANN) explains that
DNSSEC adds two important features to the DNS protocol:
- Data origin authentication allows a resolver to cryptographically verify that the data it received actually came from the zone where it believes the data originated.
- Data integrity protection allows the resolver to know that the data hasn’t been modified in transit since it was originally signed by the zone owner with the zone’s private key.
For authentication, the IT admins use a Public key infrastructure (PKI) that creates a chain of confidence between the root server located at the top of the DNS tree and the lowest end nodes, or the nameserver for the end user.

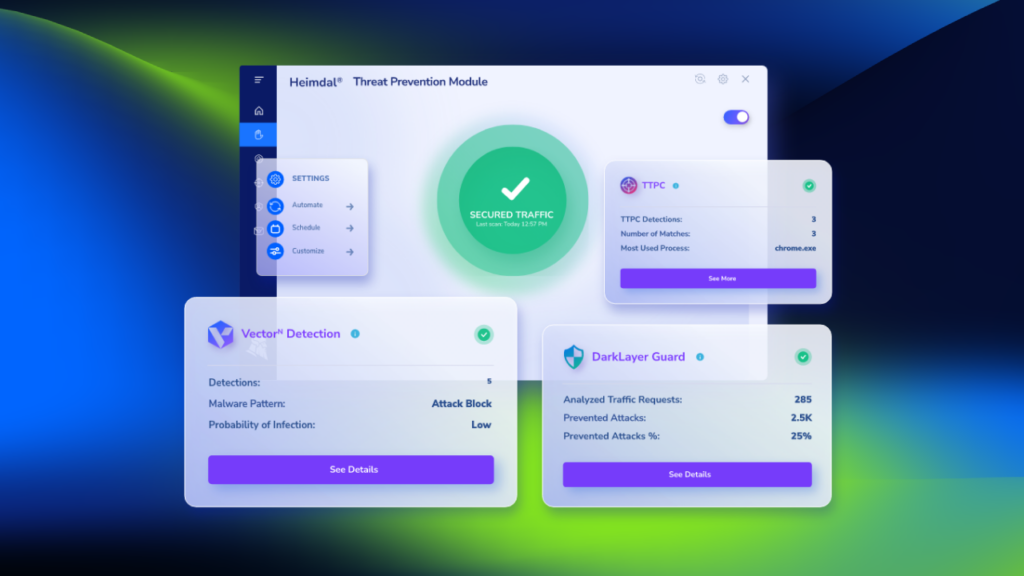
Heimdal® DNS Security Solution
- Machine learning powered scans for all incoming online traffic;
- Stops data breaches before sensitive info can be exposed to the outside;
- Advanced DNS, HTTP and HTTPS filtering for all your endpoints;
- Protection against data leakage, APTs, ransomware and exploits;
How Can Heimdal® Help?
Implementing DNS filtering is the first step toward a secure DNS. A strong DNS filtering engine, like Heimdal® DNS Security’s, can prevent malicious data packets from damaging your endpoints and network.
Our product reduces latency by using both local and cloud queries. The DNS traffic filtering engine examines data packets each time your machine performs a DNS query to check for anything suspicious hidden in the Internet traffic. Additionally, Heimdal’s DNS Security tool will automatically block the connection if it detects any odd behavior when querying.
This means you’ll be able to prevent:
- man-in-the-browser attacks
- zero-day exploits
- data exfiltration and data loss
- network infections
The Hybrid DNS module in DNS Security – Network improves local DNS servers with advanced filtering. It secures internal DNS traffic without sending queries to the Heimdal’s TPN resolvers. Users can choose any DNS forwarder and use dynamic IP addresses on local DNS resolvers. This makes it perfect for both on-premises and cloud-based DNS environments.
Wrapping Up…
The DNS is an essential tool in any workplace as it is integral to the framework of the World Wide Web. Understanding how it works and how to secure it appropriately should therefore be at the top of your company’s list of priorities.
If you adhere to the advice provided above, you will take care of the crucial elements your DNS infrastructure requires to remain safe and dependable. You can also do that with the help of Heimdal. Contact us at sales.inquiries@heimdalsecurity.com for additional details or to schedule a demo.

DNS Security for Dummies
An eBook that gives a comprehensive role-based security approach and addresses the numerous dangers to the Domain Name Systems (DNS) as cyberattacks increase globally.
FAQs
What is a DNS strategy?
A DNS strategy is an extensive plan for managing and securing a company’s Domain Name System (DNS). It includes aspects like redundancy, access control, threat monitoring, data integrity via DNSSEC, and optimal server configuration to guarantee DNS dependability, security, and efficiency.
How DNS works step by step?
Here’s how the Domain Name System (DNS) functions: Your device will contact a DNS resolver when you type a domain name (like example.com) into the browser. If the IP address is not already stored in the resolver’s cache, it will query the root servers, then the TLD (Top-Level Domain) servers, and finally the domain’s nameservers.
To learn more about how DNS works step by step, check out this article: What Is DNS? An Introduction to the Internet’s Phonebook and How It Works.
What are the most common DNS attacks?
The most common DNS attacks include DNS spoofing (or cache poisoning), where attackers divert traffic to fraudulent sites; DDoS (Distributed Denial of Service) attacks, overwhelming the server with traffic; DNS tunneling, using DNS queries for data exfiltration or command and control; and DNS hijacking, redirecting queries to malicious sites.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security