Contents:
From securing e-commerce transactions to encrypting data sent via email and verifying software packages, Public Key Infrastructure (PKI) and encryption are essential to secure online communications. But what exactly is PKI, how does it work, and what role does it play in encryption and internet security as a whole?
What Is Public Key Infrastructure?
The internet is an inherently insecure and dangerous place and PKI is the intricate ecosystem the internet relies on for security. It’s what allows us to make purchases and submit sensitive personal information safely and securely online.
At its core, PKI is the combination of processes and technologies (and their governing policies) that work in the background to secure online communications. You use PKI every day when you:
- Communicate securely with a website via HTTPS,
- Send or receive an encrypted email,
- Allow your OS to verify a software installer before executing it,
- Set up secure server-to-server communication, and
- Connect an IoT device securely to a gateway or server.
But what exactly does Public Key Infrastructure help you do? In a nutshell, PKI allows you to:
- Use verifiable identity to your benefit. Your digital identity makes it possible to accurately identify who (or what server) you’re connecting with. It also enables you to authenticate yourself to access protected resources (in specific circumstances).
- Protect the data you store or transmit online. This is done using encryption. If you don’t encrypt your data (or the channels it transmits through) when sending data online, then it travels in cleartext format that anyone who knows how can intercept and read.
- Offer assurance that your data hasn’t been modified. If you want users to know that your emails, software, and other data is legitimate, this is where data integrity comes into play.
The 5 Key Elements That Make PKI Work
Okay, there’s a lot to cover when talking about what makes up PKI and encryption. Here’s a quick overview of PKI’s five components:
1. Cryptographic key pairs — Cryptographic keys are long, random strings of data used to encrypt or decrypt data. Public-private key pairs (asymmetric) are integral to PKI; they’re what make it work. Once you encrypt data with a public key, only the holder of the associated private key can decrypt it. You can’t even decrypt it using the same public key that encrypted it.
2. Digital certificates — Digital certificates are small digital files that tie an identity (such as an email address, domain name, company name, person’s name, IP address, etc.) to a key pair. These certificates essentially serve as your ID card on the internet. The most common types of digital certificates include:
- SSL/TLS certificates: Commonly referred to as SSL certificates or website security certificates, TLS certificates are the digital files that make the padlock and HTTPS appear next to your URL on your website. They’re what enable you to serve your website via the secure Transport Layer Security.
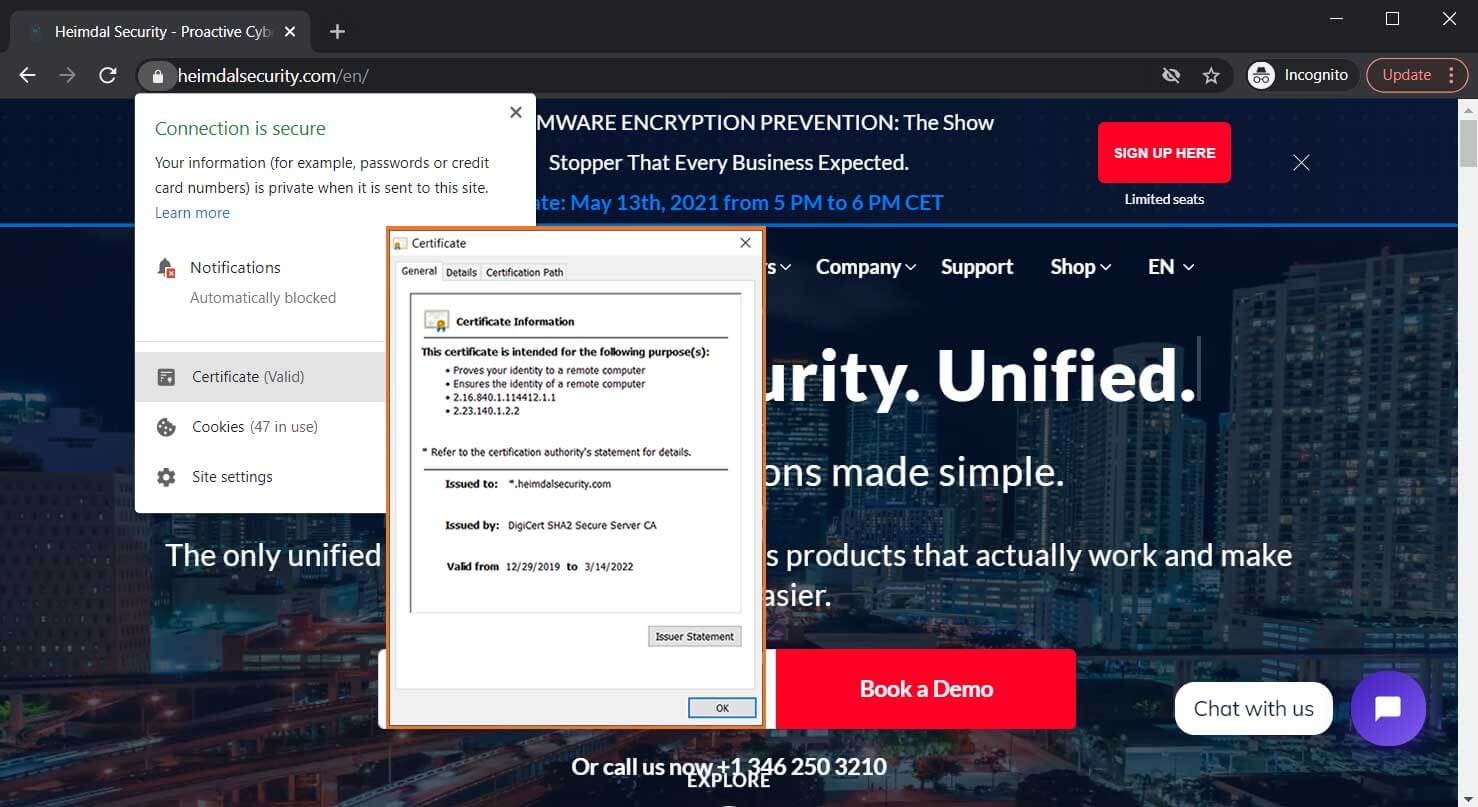
A screenshot of the security information that displays to site users when you secure your website using an SSL/TLS certificate.
- S/MIME certificates: These certs allow you to digitally sign and encrypt your emails (which is why they’re also known as email signing certificates). This process ensures secure, end-to-end communications when corresponding with other S/MIME certificate users and is one of several ways to improve your organization’s email security.
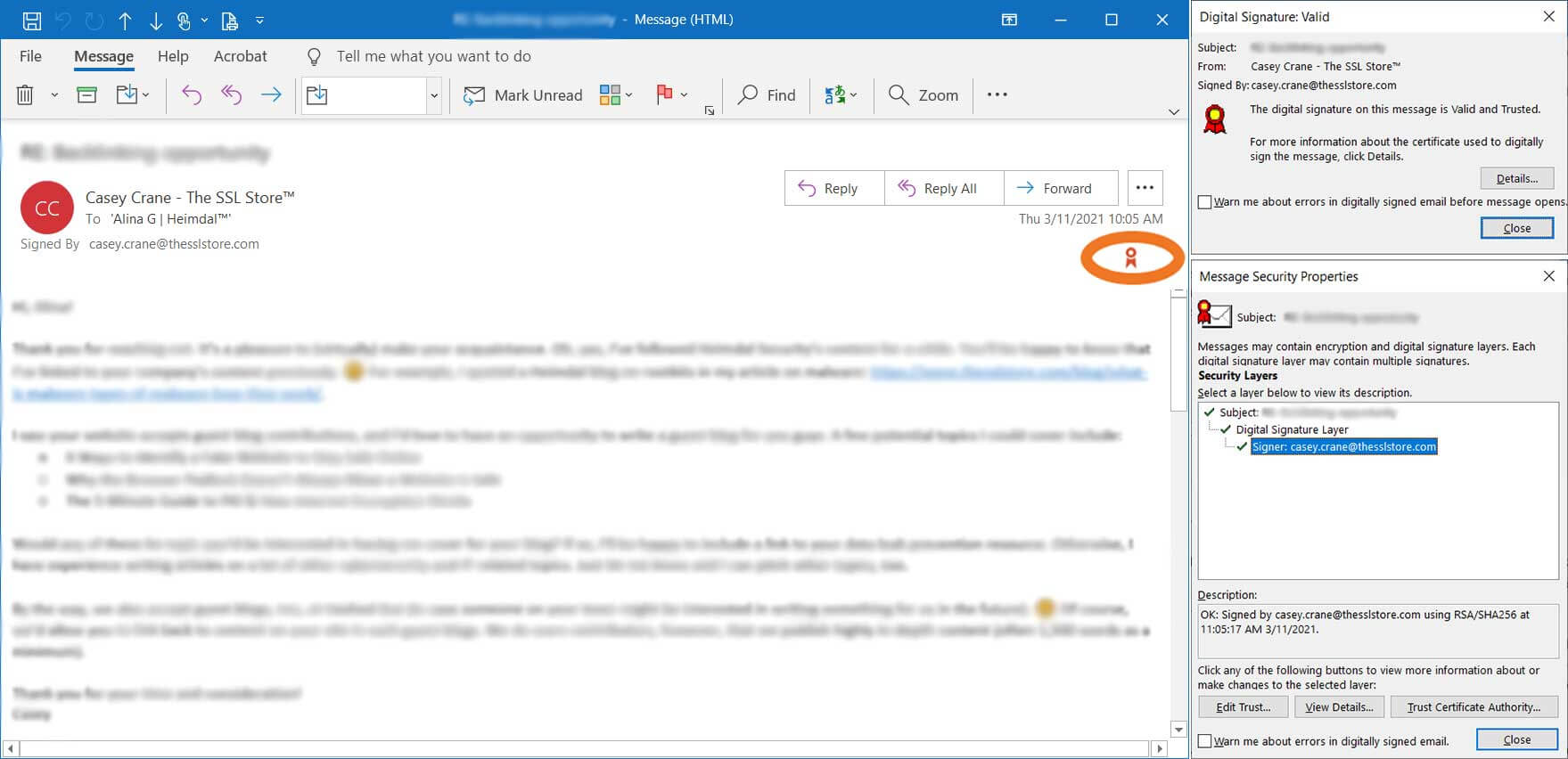
A compilation of screenshots that show the types of information that display when you digitally sign your emails using a S/MIME certificate.
- Code signing certificates: Much like the name implies these certificates are great for organizations and individual devs. You can sign your software to let users, browsers, and clients know your software is legit and hasn’t been altered.
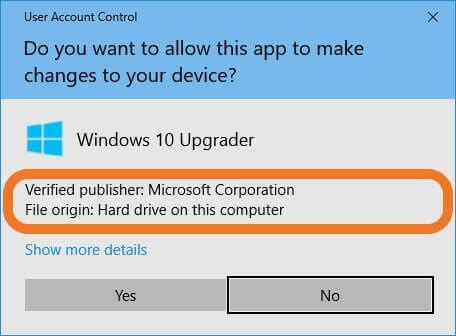
An example of software that’s been digitally signed by an EV code signing certificate.
- Client authentication certificates. These certificates allow you to prove your identity and log in without having to type in hard-to-remember (and potentially insecure) usernames and passwords. This helps you avoid brute force attacks and other password-based attacks.
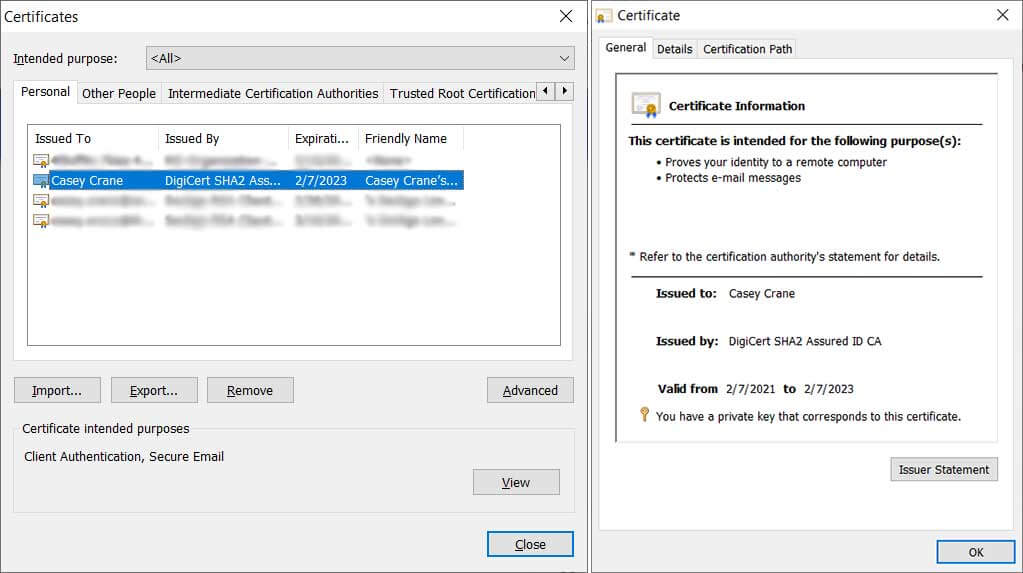
A screenshot example of a client authentication certificate.
3. Certificate authorities — Generally, when we talk about a certification authority (CA), we’re talking about a publicly trusted third party that validates organizations and individuals prior to issuing digital certificates to them. However, there’s a second type of certificate authority that’s known as a private CA. This is a CA you create and operate to validate and issue your own certificate. It’s important to note, however, that these private certs only work on devices that manually install your root certificate. So, they aren’t trusted automatically by external clients and devices.
4. Chain of trust — This is the hierarchy of linked certificates (roots, intermediates, and leaf certificates) that helps browsers and clients alike know whether digital certificates are legitimate. It’s kind of like a certificate’s family tree — it allows you to trace each certificate’s lineage back to the secure root that it originated from. Here’s an example of what an SSL/TLS certificate chain of trust looks like:
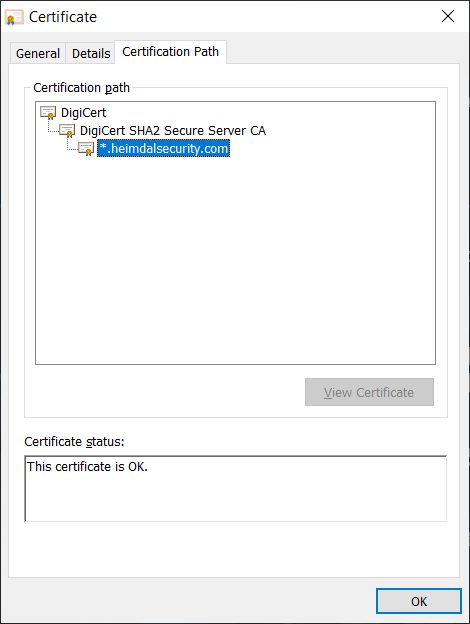
5. Digital signatures — Users apply this unique hashed data to guarantee that their data (such as software code or email messages) are genuine. This way, users who receive a digitally signed message can tell if the data has been modified since it was sent or published.
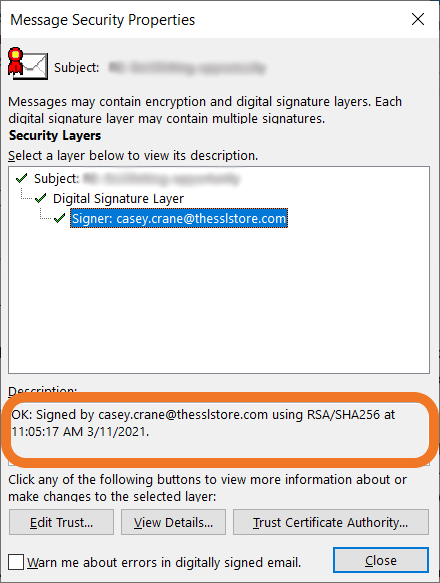
A screenshot showing how an email digital signature displays in Outlook.
Of course, for PKI to work, it requires organizations and users to have valid digital certificates and keys. Proper certificate management entails having the right tools, policies, and processes in place that help you stay on top of these certificates so you’re compliant with data security and privacy regulations.
If your website security certificate expires or get revoked, then your users will see error messages like this:
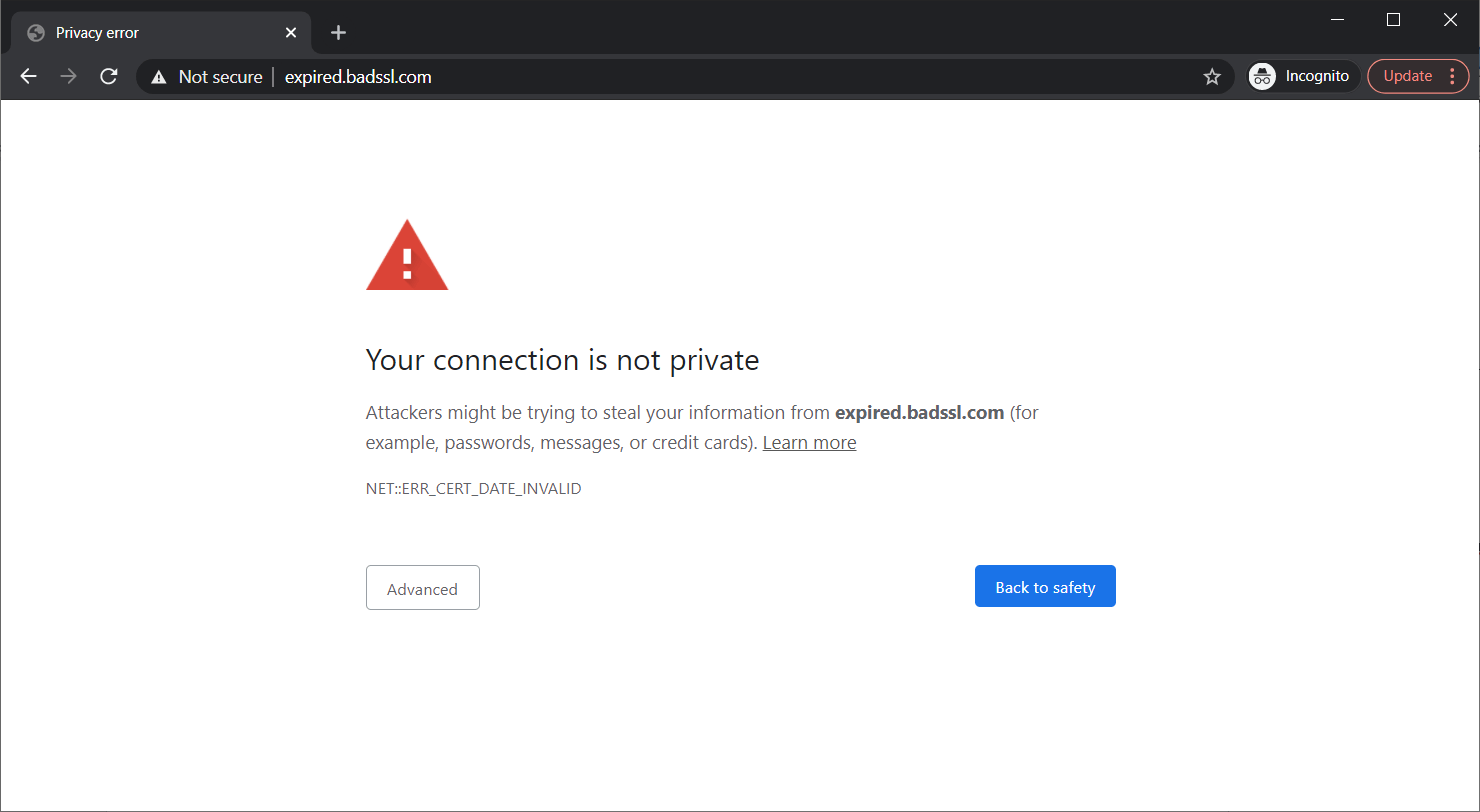
A screenshot of the message that displays to site users when your website’s SSL/TLS certificate expires.
Now, if you’ve never heard of PKI before now, don’t fret. Although PKI has been around since the 80s, most everyday users don’t know the term and aren’t familiar with its different components. Even if you don’t know the acronym, you’re likely familiar with what PKI helps you do online.
What PKI Does
The public key infrastructure uses authentication and encryption to secure communications between two entities or endpoints (e.g., a customer’s smartphone browser and your website) in public channels. It does this by distributing public keys to help endpoints and users that don’t know one another so they can exchange data securely.
Why Is it Necessary?
When you transmit information across the internet, it bounces from one router to the next in a readable format until it reaches its intended destination. That means there are lots of places someone can intercept your data. And if that data isn’t secure (encrypted), it means they can read, manipulate or steal it without your knowledge. PKI, along with its digital certificates and keys, keeps your sensitive data out of the hands of unintended third parties.
To better understand what PKI does, let’s consider it in the context of website security. Installing an SSL/TLS certificate on your site makes the security padlock and HTTPS appear in your browser. These two security indicators mean that your data is transmitting from your browser to the server of the website you’re connected to securely (i.e., no one else can intercept or read it).
However, being “secure” isn’t the same as being “safe.” Bad guys can slap DV SSL/TLS certs on their fake websites just as easily as legitimate companies because they require the lowest level of validation. The Anti-Phishing Working Group published a report in 2020 stating that 84% of phishing websites use TLS certificates.
So, unless you know who’s on the other end of that secure connection, your data isn’t truly safe. This is where identity comes into play.
The Role of Identity in PKI
PKI can be a very powerful tool for managing identity because digital certificates contain verified info. But not all certificates are created equally.
Say you want to purchase something from Amazon that you’ve had your eye on for a while, but when typing amazon.com, you accidentally mistype it as amzon.com, which takes you to a fake website. If you make your purchase on this fake website, even if it’s using HTTPS, then your data is no more secure than it would be if you physically handed over your credit card to a bad guy. That’s because even if the website is using a secure connection, you’re securely sending your data to the cybercriminal sitting on the other end.
This is why knowing the verified identity of the entity on the other end of your connection is crucial. Certificate authorities are the ones that validate domains and/or organizations. Website security certificates come in three different validation levels, and domain validation is the most basic level. It only requires site owners to verify they own or control the domain name. It’s the next two levels — organizational and extended validation — that help you identify legitimate websites from imposters.
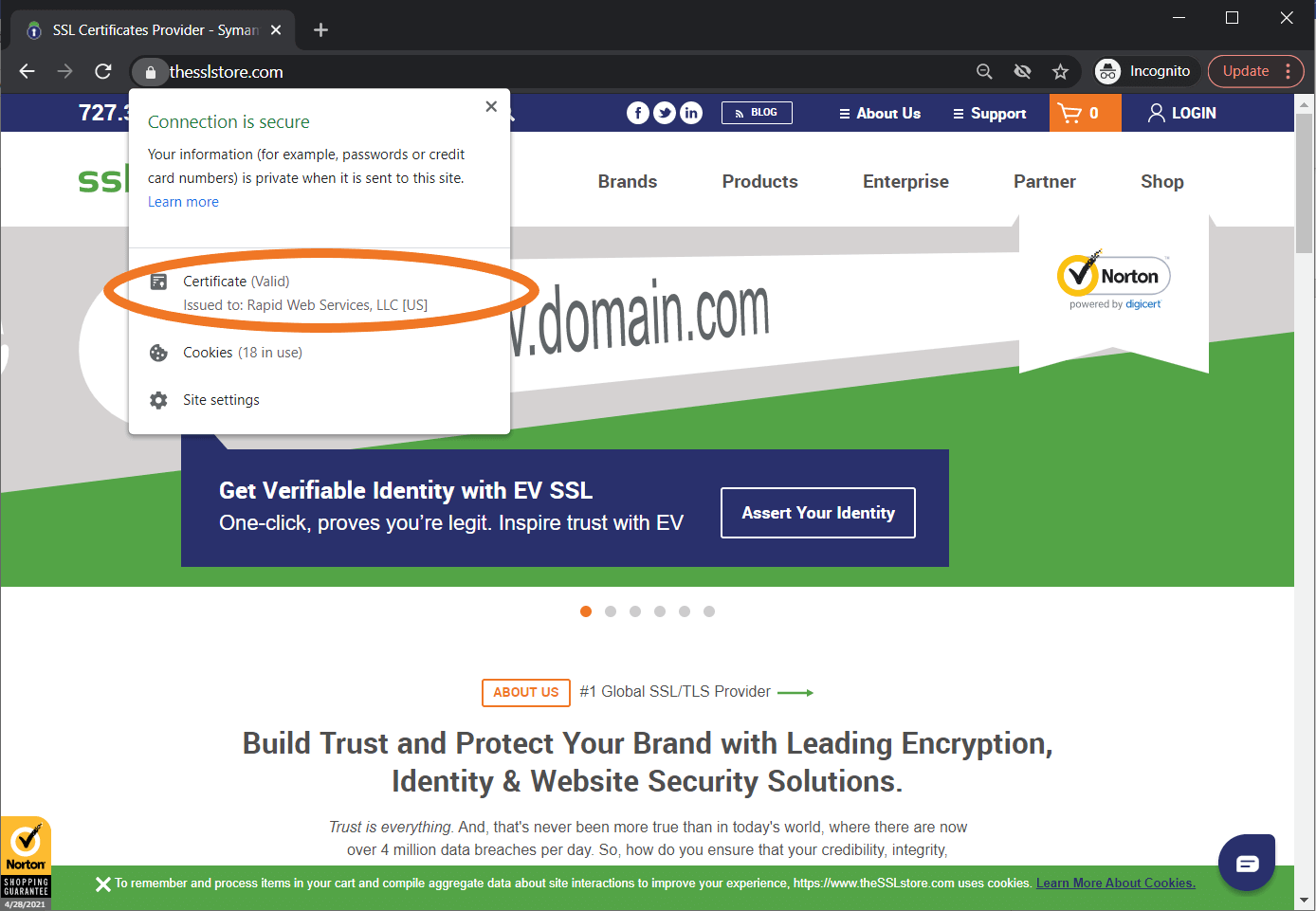
If a website has an OV SSL/TLS certificate, it means that a trusted public CA has done its due diligence and taken the time to verify certain aspects of the organization. On the other hand, an EV SSL/TLS certificate tells you that the CA has carried out the most stringent verification level. This is what makes the company’s name appear in the browser:
An Example of PKI in Action
Historically, if you wanted to communicate securely with someone, you had to physically meet up with them to exchange encryption and decryption keys. That doesn’t work online, though — you can’t drive to your local Amazon warehouse to get an encryption key every time you want to buy something.
PKI solves this problem by allowing you to use asymmetric encryption to verify who you’re communicating with online, then set up secure encryption and decryption keys so you can send each other information that nobody else can read or access. While symmetric encryption (which uses a single key to encrypt and decrypt) technically isn’t PKI, it’s what PKI helps you to achieve using public channels.
Let’s continue with using a website connection here as an example. Whenever you connect to a website, your browser starts a conversation with the server using asymmetric encryption. This so-called “handshake” enables two endpoints to use asymmetric encryption to:
- share and agree upon technical details that enable a secure connection. This includes protocols, cipher suites, etc.
- verify one or both endpoints’ identities. In the former, the server sends its SSL/TLS certificate and public key to the browser. The latter occurs when a user also provides their client authentication certificate to access a secure resource.
- exchange secret information that generates a session key. This exchange of info and the resulting key generation enables them to change over to a faster & secure communication channel using symmetric encryption.
Here’s a simplified overview of how the TLS handshake process works:
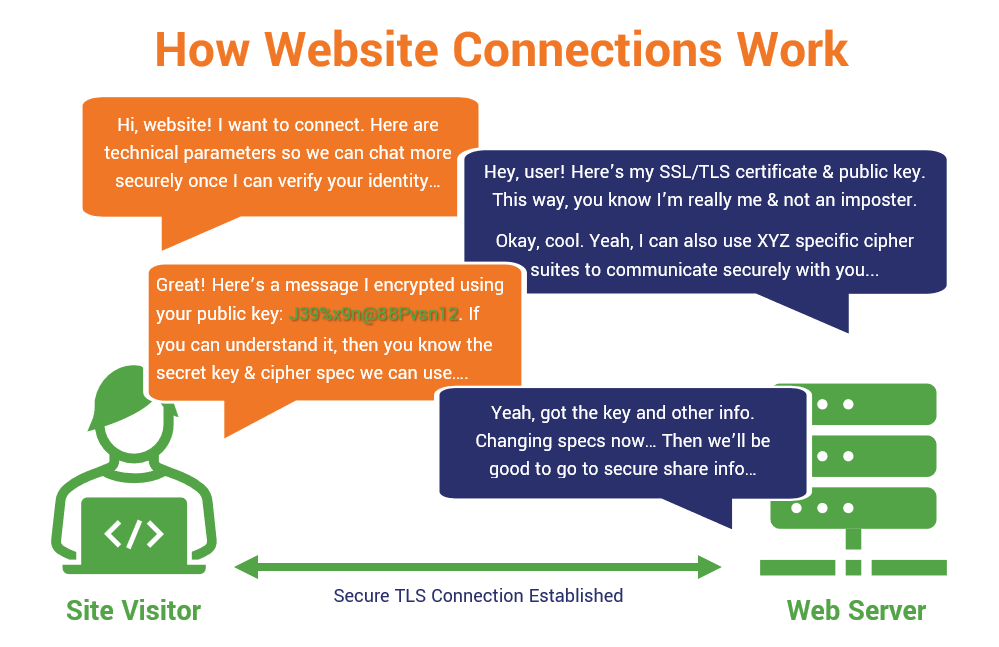
A simplified overview of how a TLS handshake works. (Yes, there are technical differences between TLS 1.2 and 1.3, but I’m not getting into all of that here. You can check out another article on the TLS handshake for more specific information.)
How Can Heimdal® Help?
Heimdal is a Cybersecurity-as-a-Service (CSaaS) provider that brings a unique offering into the market, emphasizing security unification, ease of use, and first-class Support for all its customers:
When we put ourselves in the place of the customer and we try to think “what would really help me, if I was having their problems?” – that’s when we make pivotal changes. The advantages of a unified cybersecurity suite are absolutely staggering, and companies that adopt it, whether we’re talking about small and medium-sized businesses or multinationals with thousands or millions of employees, can see significant returns on their investments.
Heimdal Threat Prevention is a DNS traffic-filtering solution that makes sure malware doesn’t set foot in your endpoints.
Next-Gen Endpoint Antivirus has four layers of impeccable detection which will help you detect and mitigate even the most complex threats.
Heimdal Patch & Asset Management, its automatic patching, and updating engine keeps all your apps and software up to date, regardless of the machine’s status, time zone, or package size. The updating/patching module also allows your system admin to deploy proprietary software on all the machines.
Heimdal Privileged Access Management, our Privileged Access Management (PAM) solution will help you increase your UA hygiene and take full control of what goes on inside your machine. This is the only PAM solution on the market that automatically de-escalates user rights on threat detection.

Heimdal® DNS Security Solution
- Machine learning powered scans for all incoming online traffic;
- Stops data breaches before sensitive info can be exposed to the outside;
- Advanced DNS, HTTP and HTTPS filtering for all your endpoints;
- Protection against data leakage, APTs, ransomware and exploits;
Wrap Up: Final Thoughts on PKI and Public Key Encryption
Public Key Encryption and the Public Key Infrastructure it relies upon are essential to businesses and individual users alike. But for it to work for your organization, just remember that you have to:
- ensure you’re using valid digital certificates and keys that are issued by public CAs (if you want them to be automatically trusted by virtually all devices),
- make sure your certificates are installed correctly and the site is configured properly, and
- properly manage the lifecycle of your digital certificates and keys. This point is especially important and often gets overlooked.
If you don’t do these things, then your site visitors and customers may experience SSL vulnerability issues.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.
This article was originally written by Casey Crane, SEO Content Manager at The SSL Store™, and updated by Mihaela Marian, on January 25, 2023.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









