Contents:
DNS-layer security protects users by blocking potentially malicious communication on the spot. All successful phishing campaigns depend on establishing a connection with the victim through DNS to download malware or harvest credentials. In fact, researchers say 91% of cyberattacks are conducted through DNS. So, imagine what ignoring DNS protection can do to your cyber defense.
Why Is DNS Layer Security Important?
Enforcing security policies to track unusual DNS behavior and filter traffic enhances network protection and improves the detection of malicious activity at an endpoint level.
Imagine DNS-layer security as your network’s guardian. It stops shady visitors at the door, keeps an eye on what people do inside, and even checks what they’re taking with them when they leave. Things like content filtering and domain categorization help it do the job right.
This thorough gatekeeper changed the game in cybersecurity. For a long time, businesses relied on antivirus software for their safety. Traditional antiviruses check lists of already reported threats to detect and block malware.
While they do a useful job, antiviruses can’t prevent threats from entering the system. Also, most of them can’t recognize new malware strains as malicious.
This means that even with the best traditional AV, the company’s sensitive data and infrastructure are at risk. Is there a better way to protect against cyberattacks? Yes.
Setting up DNS layer security helps stop threats before they get in, so you can avoid:
- spending time and energy on cleaning up incidents
- digging through forensic investigations
- risking your company’s data being exposed or stolen
How Is DNS Used in Cyberattacks?
Understanding how hackers use DNS makes it easier to understand why you should consolidate this security layer. Daily activities become more and more digitalized, so using the Domain Name System is something you can’t avoid. If your DNS isn’t protected, hackers can hijack it to redirect traffic to fake websites, steal login details, or spy on your activity.
There are two main DNS attack types that you should know about.
Denial-of-Service – DoS and DDoS attacks
Threat actors flood a DNS server with traffic aiming to make it unavailable to its legitimate users and even take it down. DoS attacks vary according to the vulnerability or protocol\system\code limitation they use. DDoS, which stands for Distributed Denial of Service, employs botnets to launch DoS-type attacks on large targets.
Turning services unavailable is not the only purpose of DoS attacks, says Cybersecurity Expert Robertino Matausch:
hackers can use Denial of Service (DoS) to turn a system unstable. Then they use other hacking tools to enter the system or cover traces tampering with the system. For example, hackers may use DDoS attacks to shut down a banking page so you cannot log in. Then they create a banking simulation page and send a phishing message saying: “Hey, we know we have problems, please use our secondary log in Page for logging in”. And that’s how they succeed in phishing your credentials.
DNS Hijacking
In this case, the threat actor manipulates a DNS query’s resolution and redirects it to a compromised DNS server. Unsuspecting visitors will come upon an infected website. This is also known as DNS poisoning or DNS redirection. DNS spoofing, also known as DNS cache poisoning maliciously directs the victim to a forged website built by the hacker.
DNS tunneling is another malicious way of leveraging the phone book of the Internet. Through this technique, which is not harmful per se, hackers manage to send malicious data avoiding network filters and firewalls. Threat actors use DNS attacks for phishing campaigns, deploying malware and ransomware, and exfiltrating data.
Read on to find out what DNS layer security is based on.
Main Components of DNS-Layer Security
With time, it became obvious that unsecured DNS servers were both a target and a way of conducting malicious activities. So, security specialists had to find innovative solutions to the increasingly disrupting DNS security problem.
Years after the DNS was created, DNS-layer security is a worldwide recognized practice and is based on two main components:
Domain Name System Security Extensions (DNSSEC)
DNSSEC is the most basic form of DNS security. It was meant to defend Internet users against fake DNS data by using an embedded digital signature. DNSSEC checks the DNS query responses before communicating them to the client. The data is verified through a system of public keys and digital signatures. Public key cryptography is the basis of DNSSEC validation.
DNS filtering
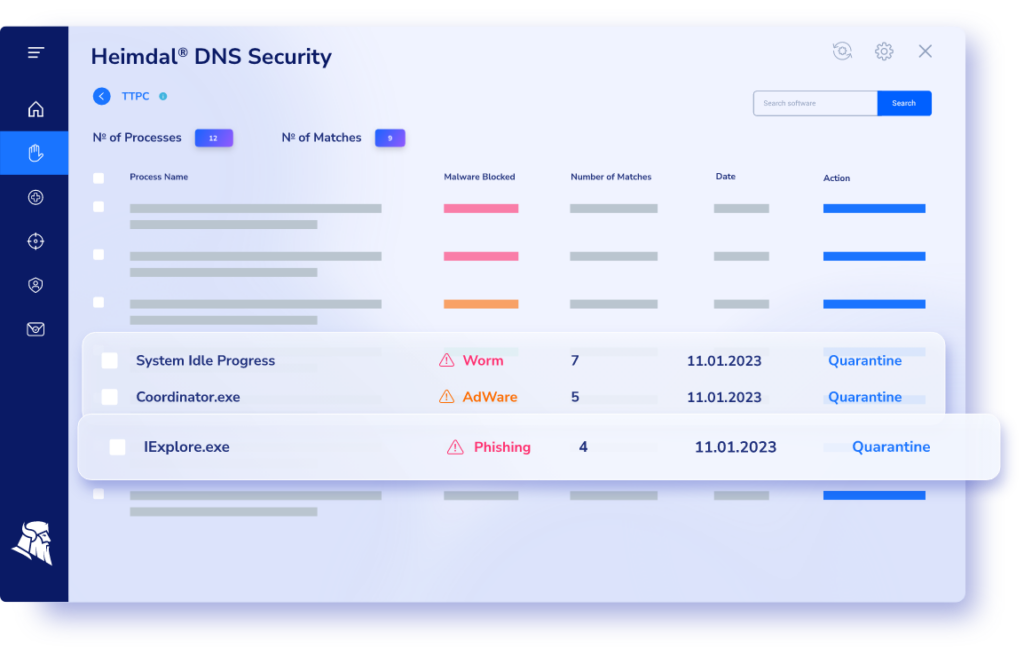
DNS filtering is also known as DNS firewall or DNS blocking. It’s a method of preventing access to potentially malicious domains. Every time a user issues a DNS query, the DNS filtering solution uses a blacklist of malicious domains or IP addresses to check if the requested website is harmful. If the domain is on the list, the DNS query won’t be resolved, and access will be denied. This access denial to harmful content saves the security team a lot of time and trouble. DNS filtering is a company’s first line of defense, as it can block harmful DNS connections on the spot.
DNS security software should of course cover both components. But what makes the best of them stand out is their DNS filtering accuracy. To make the best decision when choosing a DNS security solution, read more about how DNS filtering works.
How DNS Filtering Blocks Cyber Threats
DNS filtering blocks access to malicious websites, thus reducing the risk of infections. By doing this, it prevents:
- unsuspecting employees to fill in their credentials in spoofed login forms
- unintentional malware installation generated by clicking on a malicious link
- compromised machines beaconing to command-and-control servers
- data exfiltration to command-and-control servers
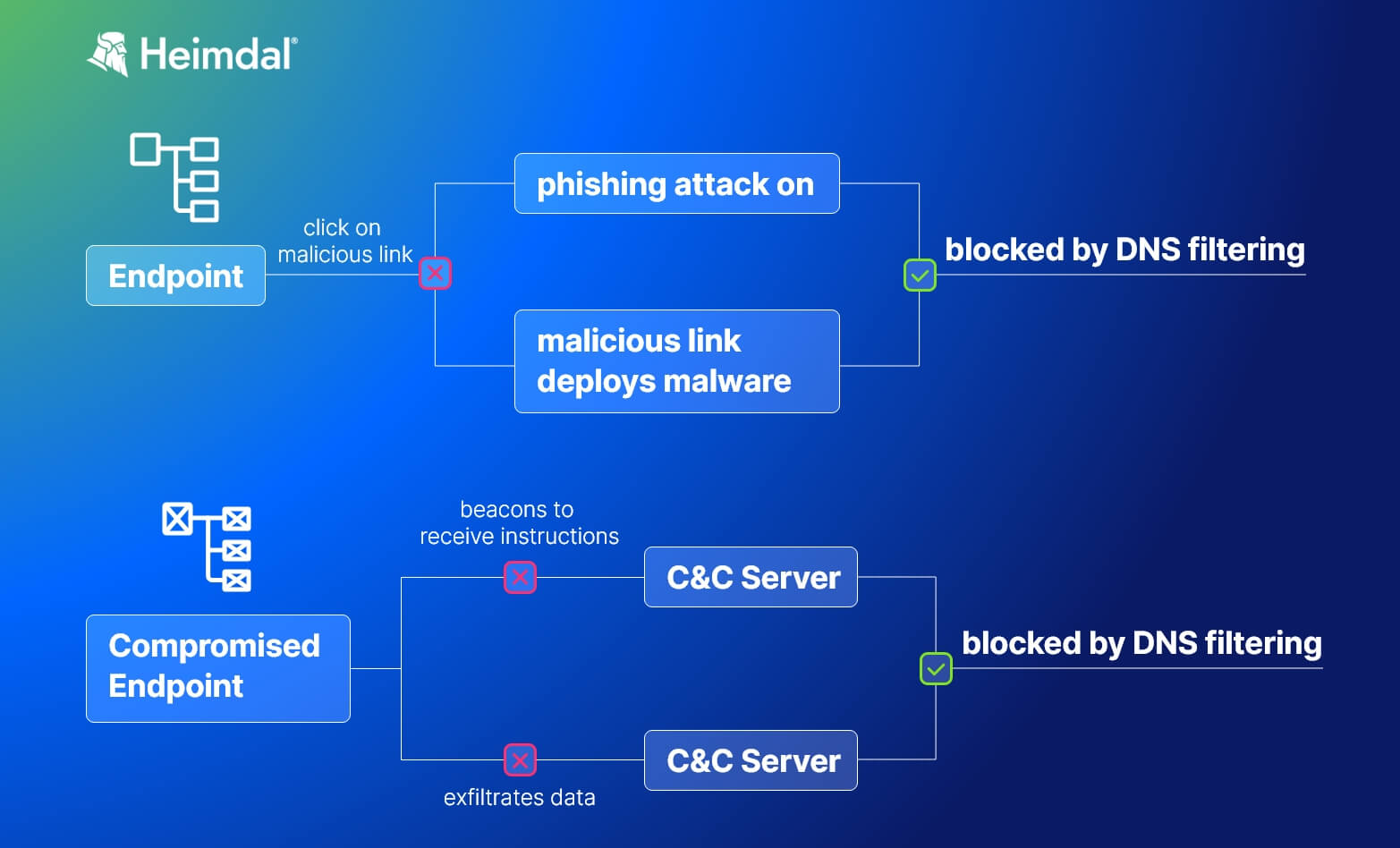
All these are possible due to the DNS filtering system’s ability to spot malicious domains. Some of the products out there use default operations for DNS content filtering while others are controlled by admins.
Here are three main filtering ways:
- category filters block access by evaluating the nature of the websites’ content: racial hatred, pornography, gambling, etc.
- keyword filters analyze a website’s content and decide to block it if they find certain words, like “chat” or “Netflix”, for example.
- finally, there are administrator-controlled Blacklists and Whitelists. Those offer personalized DNS content filtering, entirely decided by the administrator.
Not using a DNS filtering solution makes your company vulnerable to the following:
1. Step one: the user clicks on a malicious link, gets on a harmful website and downloads, without suspecting a thing, a malware installer.
2. Step two: the malware installer attempts (and succeeds) to connect with another harmful website, that deploys more malware that will compromise the system.
3. For the third step, the malware communicates to the C&C which starts exploiting the system for malicious purposes, like ransomware, for example.
How Can Heimdal®Help Enforce Strong DNS Security
DNS filtering is a great instrument; you should definitely insert it into your company’s security mix. However, most DNS security tools only rely on blocking malicious domains on known blacklists.
So, what happens with the yet-undiscovered ones? As cyber criminals are currently able to use domain generation algorithms, they can instantly create hundreds of new malicious domains. It’s impossible to blocklist them all, unless you improve filtering techniques.
Heimdal’s DNS Security suite for endpoints and networks does the job differently and better. It uses AI-driven “Character Based” Neural networks intelligence to foresee threats that researchers did not discover yet. In doing so, it has a stunning 96% accuracy.
The tool also hunts, detects, and responds to threats faster than other DNS security solutions by using the Heimdal TTPC Technology. It prevents command & control server connections and data leakages and enables you to log network traffic for compliance reporting and forensics.
Also, Heimdal’s DNS Security solution integrates filtering directly into your local network, enhancing protection for both cloud-based and on-premises environments.
Wrapping Up
During this blog I highlighted how important DNS layer security is for your cyber defense mix. Sure, you might not take my word for it. So, here‘s what the numbers say, according to the Global Cyber Alliance, about the economic impact of DNS filtering on the company’s finances.
Nearly 3,700 of the 11,079 breaches could have been avoided in the past five years, if a properly configurated DNS filtering solution had been in function. Consequently, losses between $19 and $37 billion in the U.S. or an average $150 to $200 billion globally could have been prevented.
In the end, using a professional DNS layer security solution to thoroughly protect the company’s assets will turn out to save a lot of money and energy for both the business and the team.
Watch this DNS security product demo to learn more about what Heimdal’s DNS solution can do for you:
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security