Contents:
DDoS attacks are becoming a serious problem for companies all over the world. These highly disruptive attacks can cause huge revenue losses if you’re not ready to properly mitigate such an incident. Learn more about DDoS attacks and how you can keep your company safe!
What Is a DDoS Attack?
DDoS stands for Distributed Denial of Service and refers to an online attack in which legitimate users are prevented from accessing their target online location. This is usually done by flooding that particular site with a multitude of illegitimate information requests.
Such an attack can:
- Affect customer experience, since the customers may not be able to access your company’s website or mobile app.
- Affect the revenue, because retail sites or apps downtime will make purchases impossible.
- Affect the workflow, because a DDoS attack will leave employees unable to access the email and the other online resources they need to get their work done.
- Affect your brand reputation, because customers and business partners might think twice before connecting with you if you cannot ensure your business’s cybersecurity.
How Does a DDoS Attack Work?
Although we might see the Internet as this vast cyberspace of infinite possibilities, web servers and channels that connect the servers to the Internet and other network resources have a finite, limited number of requests and capacity. If this number is exceeded, usually by the hand of malicious actors, the responses to the requests that legitimate users launch will be much slower or the requests themselves might be totally bypassed, which actually represents the ultimate goal of a denial of service attacker.
Speaking of attackers’ goals, they DDoS for a variety of reasons:
- to discredit a business (that might be competition, but not necessarily);
- to ask for payment before stopping the attack – almost like ransomware offenders.
Types of DDoS Attacks
In general, DDoS attacks can be divided into 3 main types which include multiple techniques:
a. Volumetric Attack
Volumetric attacks are the most common type of DDoS and refer to the case in which a network’s bandwidth is overwhelmed by enormous numbers of false requests sent by bots to every open port they find, obstructing legitimate requests. Examples:
- UDP floods
- ICMP floods
- IPSec flood
- IP/ICMP fragmentation
- Reflection amplification attacks
b. Protocol Attack
Protocol attacks target the network parts that verify connections, but they can also be directed against firewalls. They include sending slow or abnormal pings (to the network) and large quantities of erratic data to (to the firewall). Examples:
- TCP Connection Attacks (or SYN Flood exploit)
- Fragmented packet attacks
- Ping of Death (PoD)
- Smurf DDoS
- Border Gateway Protocol (BGP)
c. Application-Layer Attack
DDoS application-layer attacks are, as the name suggests, directed to the applications that users work with, like HTTP, HTTPS, or DNS protocols. Examples:
- HTTP / HTTPS Flood
- Slowloris
- RUDY (R-U-Dead-Yet?)
- DNS query flood
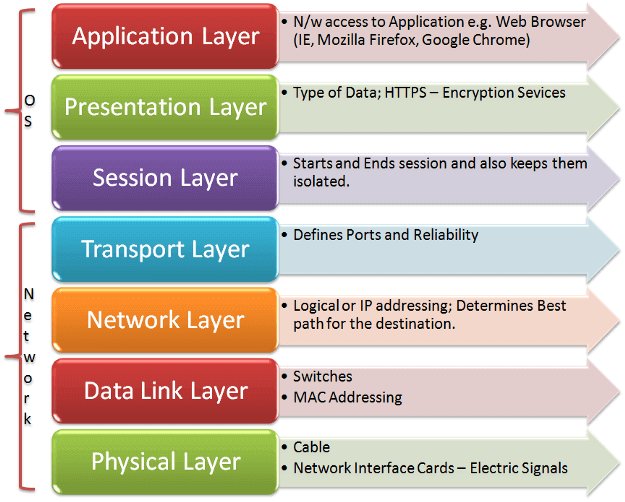
Another way of classifying DDOS attacks is by looking at which OSI (Open Systems Interconnection) model layer they affect. Most of the times, DDoS attacks target layers 3 (network), 4 (transport), 6 (presentation) and 7 (application).
DoS vs. DDoS
DoS represents a system-on-system kind of attack, whereas DDoS uses multiple systems against a single one. Apart from this main difference, there are other aspects that differentiate DoS and DDoS attacks:
| DoS Attacks | DDoS Attacks |
|---|---|
| Comes from a single source, machine | Uses multiple remote machines |
| Comes from a single location | Comes from multiple locations |
| Origin is easier to detect | Tougher to trace, disguising the original source |
| Small-scale attack, usually carried out by a single hacker | Large-scale attacks, usually carried out by a hacking group |
| Easy to mitigate and stop | Much harder to mitigate and stop |
| It usually targets small companies or individuals | It usually targets large companies |
| Launched through a script or a DoS tool | Executed through the use of botnets |
Examples of Notable DDoS attacks
Some of the biggest DDoS attacks in recent history were directed against GitHub, Dyn, US banks and Amazon Web Services.
US banks attack
In March 2012, “six U.S. banks were targeted by a wave of DDoS attacks—Bank of America, JPMorgan Chase, U.S. Bank, Citigroup, Wells Fargo, and PNC Bank. The attacks were carried out by hundreds of hijacked servers from a botnet called Brobot, with each attack generating over 60 gigabits of DDoS attack traffic per second.” The banks were affected in terms of revenue, customer service issues, mitigation expenses, but also branding and image.
Dyn attack
The attack against Dyn, a major DNS provider, took place in October 2016 and used the malware called Mirai to create a botnet of compromised IoT devices programmed to send requests towards their victim. Although Dyn resolved the attack in one day, the devastating incident affected major websites like Netflix, Airbnb, PayPal, Amazon, and The New York Times.
Google attack
In 2017, Google’s network was flooded with a record DDoS attack that lasted over six months and peaked at 2.5Tbps in traffic. It would appear that the source of this major security incident had been traced back to a government-backed group that brought into play four Chinese Internet service providers to execute the attack.
GitHub attack
GitHub, a platform for software developers, was hit by a DDoS attack in February 2018. As Wired notes, “1.35 terabits per second of traffic hit the developer platform GitHub all at once. It was the most powerful distributed denial of service attack recorded to date […]. GitHub briefly struggled with intermittent outages as a digital system assessed the situation.”
Amazon Web Services attack
Amazon Web Services was targeted by a huge DDoS attack in February 2020: “This was the most extreme DDoS attack in recent history and it targeted an unidentified AWS customer using a technique called Connectionless Lightweight Directory Access Protocol (CLDAP) Reflection. This technique relies on vulnerable third-party CLDAP servers and amplifies the amount of data sent to the victim’s IP address by 56 to 70 times. The attack lasted for three days and peaked at an astounding 2.3 terabytes per second.”
You can check this interactive Digital Attack Map for more DDoS stats.
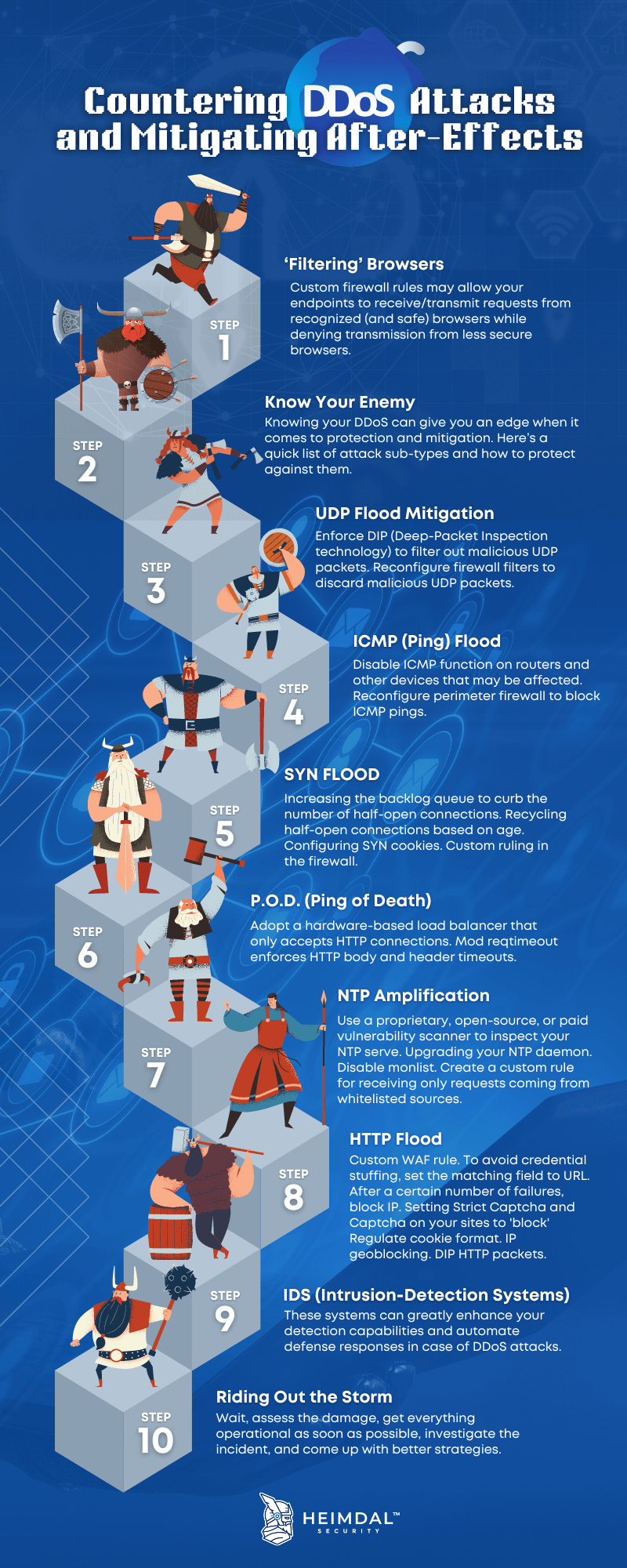
How to Protect Against DDoS Attacks
How to Protect Against DDoS Attacks
DDoS attacks only grow in volume and frequency, so having a prevention strategy is crucial for your business continuity. Let’s see what you can do to protect against DDoS attacks:
Create a Denial of Service Response Plan
When a company realizes it has become the victim of a DDoS attack, there is no time to think about the best next steps. To minimize damages, it’s important to have a beforehand plan on how you would respond to such an incident. Form a response team, define procedures, make a list of internal and external contacts that should be informed about this kind of security incident.
Ensure Basic Network Security
Sometimes, denial-of-service attacks are just a cover for more complex cyberattacks designed to infect an organization with malware or extract its data.
Once systems are back online, scan and search through every nook and cranny, and look for any malware. Be thorough, and don’t let anything slip through the cracks.
Any company’s cybersecurity suite should include advanced intrusion prevention and threat management software, firewalls, VPN, anti-spam, anti-phishing and content filtering solutions. Another important way to prevent compromising your business network is using secure and complex passwords, changed on a regular basis.
Watch for Warning Signs
It’s important to monitor your traffic and always look for anomalies. Is it a usage spike or an attack?
Network slowdown, intermittent website shutdown and irregular connectivity on the company network are some of the best indicators that you might deal with a DDoS attack. Although no network works perfectly all the time, if the lack of performance is more serious than usual or is prolonged, you should take action.
Keep Your System and Software Up to Date
Your system and all the software you use should be kept up to date to make sure that all the bugs and issues are fixed. Our Endpoint Detection and Response (EDR) Software could help you automatize patching and also ensure a powerful firewall, next-gen antivirus, and smart threat hunting powered by machine learning behavioral detection.
Simulate an Attack
It might seem counterintuitive, but if you simulate a DDoS attack against your IT infrastructure using 3rd party tools and pen testing, you will be able to see how it behaves in such a situation and check if you still have some additions to make to your denial of service response plan.
Contact your ISP provider and host
Many ISPs and hosting companies have backup measures and protocols in place to deal with a DDoS and help mitigate the damage to normalize activity.
Ideally, contact them before an attack happens, and plan ahead of time on how to include them in your response plan.
Use DDoS mitigation tools
Because of how widespread DDoS attacks have become, security vendors now offer several solutions to prevent and mitigate these kinds of attacks. Here are just a few of them:
Furthermore, since there are so many types of DDoS attacks, you might also try measures like:
- implementing a CAPTCHA-like test to differentiate bots from real users;
- limiting the requests rate;
- using a properly configured CDN to help you distribute the traffic.
Heimdal® Network DNS Security
Final Thoughts
DDoS attacks can severely affect a company’s revenue, customer experience, and brand reputation. Take precautionary measures and establish a mitigation plan in advance.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security











