Contents:
The Smurf Attack is one of the oldest, simplest, and effective cyber-attacks, one that can draw down many unpleasant consequences for any targeted company.
What Is a Smurf Attack?
Before trying to understand what is a Smurf Attack, we must first understand the concepts of DoS and DDoS.
Denial-of-Service or Distributed Denial-of-Service attacks generally try to make a network’s resources unavailable for legitimate users. This usually happens by sending attacks to it from multiple points of the network. DDoS attacks can be classified as follows:
a. Flood attacks: in this type of attack, multiple compromised devices called bots or zombies send large volumes of traffic to a victim’s system. Flood attacks use packets of HyperText Transfer Protocol (HTTP), Internet Control Message Protocol (ICMP), User Datagram Protocol (UDP) or Session Initiation Protocol (SIP).
b. Amplification attacks: these attacks imply zombies sending messages to a broadcasted IP address: “This principle will cause all the systems in the subnet reached by the broadcasted address to send a reply to the victim’s system.”
The most common types of DDoS amplification attacks are Smurf Attack and Fraggle Attack.
A Smurf Attack is a DDoS form that makes computer networks inoperable by exploiting IP (Internet Protocol) and ICMP (Internet Control Message Protocols) vulnerabilities.
c. Coremelt attacks: as Shi Dong and Mudar Sarem explain, “in this attack, the zombies can be divided into two groups. The attacker designates the zombies to communicate with the zombies in another group which will lead to sending and receiving huge data. When communication happens, it is difficult to track this attack through legitimate packets. In fact, in this Coremelt Attack, the Attack’s target is not the single host, but also the zombies, and by communicating with each other, they create network flood [16]. So, large numbers of packets are sent to the same host, the destination IP address, and the port number. Then, eventually, the system will crash.“
d. TCP SYN attacks: in this attack, hackers use TCP vulnerabilities by sending a large number of SYN requests to the server. Dong and Sarem explain why this is troublesome: “The server replies to the request by sending SYN + ACK packet and waits for the ACK packet from the client. Let us suppose that the attacker does not send the ACK packet, and the server waits for non-existent ACK. The limited buffer queue of the server becomes full and the incoming valid requests will be rejected.”
e. Authentication Server attacks: during this type of attack, the authentication server checks the attacker’s bogus signature, thus consuming more resources than it would normally do for generating the signature.
f. CGI Request attacks: this kind of attack implies that the hackers send a large number of CGI requests – this uses up the victim’s CPU cycles and resources.
How Does a Smurf Attack Work?
A Smurf Attack consists of 5 stages:
Firstly, a fake Echo request containing a spoofed source IP is generated through the Smurf malware. The spoofed IP is actually the target server address.
Secondly, an intermediate IP broadcast network is used to send the request.
Afterwards, the request is transmitted to every network host on the network.
During the penultimate stage of a Smurf Attack, each host sends an ICMP response to the spoofed source address.
In the last stage, the target server is brought down if there are enough ICMP responses forwarded. Moreover, as Hang Chau mentions in his paper, Defense against DoS/DDoS Attacks, “Smurf Attack uses bandwidth consumption to disable a victim system’s network resources. It accomplishes the consumption using amplification of the attacker’s bandwidth. If the amplifying network has 100 machines, the signal can be amplified 100 times, so the attacker with relatively low bandwidth (such as the 56K modem) can flood and disable a victim system with much higher bandwidth (such as the T1 connection). “
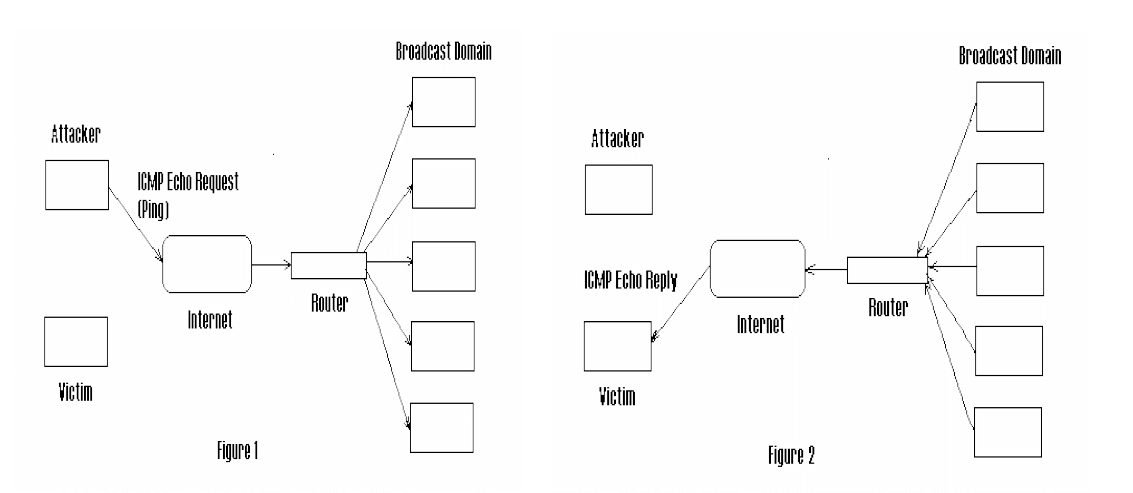
Source: Defense against DoS/DDoS Attacks
Smurf Attack Types
There are two types of Smurf attacks:
a. Basic
In the Basic Smurf Attack, the seemingly endless ICMP request packages include a source address set to the broadcast address of the target’s network. If these packets disperse properly, there will be an echo from every single device on the network, which will create the overwhelming traffic that usually gets systems down.
b. Advanced
In the case of Advanced Smurf Attacks, the echo answers to the ICMP requests can configure their sources so that they respond to third-party victims. In this way, hackers can reach various, bigger targets at once.
The first Smurf Attack goes back to the 1990s, when the University of Minnesota was targeted in 1998. The Minnesota Smurf Attack lasted more than an hour and “set off a chain reaction throughout the state, shutting down some computers entirely and in other cases causing data loss and network slowdowns.”
As Techslang says, “The attack created a cyber traffic jam that also affected the rest of Minnesota, including Minnesota Regional Network (MRNet), one of the state’s Internet service providers (ISPs). As a result, MRNet’s clients, which included small businesses, Fortune 500 corporations, and universities, were also affected.”
How to Detect a Smurf Attack
Your company’s network administrator will probably realize pretty quickly you’ve been hit by a Smurf Attack, since there are a few telltale signs that point in its direction: a Smurf Attack affects the bandwidth, the router, and the server, which will probably crash, which will probably make your Support team very busy trying to handle conversations with angry or insistent clients.
The goal of a Smurf Attack might be to make your system useless, but it can also serve as a cover for more harmful attacks, such as stealing sensitive information. Whatever the case is, the consequences are similar:
– loss of revenue – since the whole network will slow down or get shut down, the company’s operations will be interrupted for a certain period of time.
– loss of data – it is not uncommon for hackers to steal data while your team is busy dealing with the DoS / DDoS attack.
– reputation damage – remember those angry clients I mentioned below? They might give up on your services or products because the sensitive data they entrusted to you got exposed.
Prevention Strategies
A Smurf Attack implies 3 players: the hacker, the intermediary / the amplifier, the victim. In order for the attack to start, the intermediary has to let a source-spoofed IP packet leave its network. Therefore, prevention has to be done on two levels: you must avoid being attacked and you must avoid being used to launch an attack.
To avoid being the amplifier, you should disable IP-directed broadcast on the router – this will make it deny the broadcast traffic to the internal network from other networks. You can also try to apply an outbound filter to your perimeter router, as well as configuring hosts and routers not to respond to ICMP echo requests.
To avoid being the victim, you should:
– have a prevention strategy based on traffic network monitoring that can detect any oddments – like packet volume, behaviour and signature. This could help you stop a Smurf Attack before it even begins.
– install an antivirus and an anti-malware solution and protect your servers with network firewalls or specialized web application firewalls. You could try for that matter Heimdal™ Next-Gen Endpoint Antivirus. Its firewall can help you prevent incoming attacks, while the AV uses 4 stages of scanning (Local File/Signature & Registry Scanning; Real-time Cloud Scanning; Sandbox and Backdoor Inspection; Process Behaviour-based Scanning) to detect and identify even the most advanced threats. Our solution’s firewall also offers full management of the windows firewall and device Isolation in case of major outbreaks, enabling IT to lockdown departments quickly, according to the NIST AC-7 Policy regarding Authentication Failures.
– buy more bandwidth. You should have enough bandwidth to handle traffic spikes that might be the result of malicious activity.
– build redundancy. Your servers should spread across multiple data centers and have a good load balancing system for traffic distribution. The data centers should be, if possible, in different regions of the same country or even in different countries and should be connected to different networks.
– protect your DNS servers. Besides building redundancy, you could also try to move to a cloud-based DNS provider, whose services are specifically designed with DDoS prevention in mind.
Heimdal® Network DNS Security
Wrapping Up
Neither money loss, nor data breaches and reputation damage are something you would want for your company. As with pretty much any cybersecurity threat that’s out there, prevention is the best strategy.
Whatever you choose, please remember that Heimdal™ Security always has your back and that our team is here to help you protect your company and your home and to create a cybersecurity culture to the benefit of anyone who wants to learn more about it.
Drop a line below if you have any comments, questions or suggestions – we are all ears and can’t wait to hear your opinion!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security











