Contents:
A DNS attack is particularly hard to detect because it compromises a legitimate function of the internet. For the same reason, DNS attacks can impact large numbers of interconnected devices and users.
The Domain Name System (DNS) is an essential element of the internet. However, its creator, Paul Mockapetris, didn’t focus much on securing it. At the moment, he couldn’t foresee the rise of cybercrime.
That’s why today, while enhancing our digital lives, DNS has also become a prime target for hackers.
There are various DNS attack types out there, using different methods and targeting different vulnerabilities. In this article, I’ll explain how they work and how you can prevent being a victim of a DNS attack.
Key takeaways
- Hackers use exploit DNS vulnerabilities to divert traffic, deploy malware, and disrupt services
- Use encrypting VPN to protect from DNS hijacking
- Threat actors can compromise DNS records and use them in their DNS attacks
- Use an automated DNS traffic filtering tool, like Heimdal’s DNS Security to keep your network safe
What Is a DNS Attack
A DNS attack is a malicious activity that exploits the Domain Name System’s vulnerabilities. Threat actors use the DNS as an attack vector to compromise a network’s DNS service availability or integrity.
The Domain Name System (DNS) makes the internet as we know it work. It is a protocol that translates human-friendly domain names – like www.example.com – into IP addresses that computers use to find each other on the network. A DNS attack aims to disrupt this process and use it to:
- divert traffic to a malicious site
- take a website offline
- exfiltrate data
- enable hackers to communicate stealthily with a command-and-control server
Common Types of DNS Attacks
There are two main types of DNS attacks: denial of services and hijacking. Those further divide into various subtypes. DDoS attacks are in fact a DoS version, but since they also come in various forms, I’ll treat them as a third category.
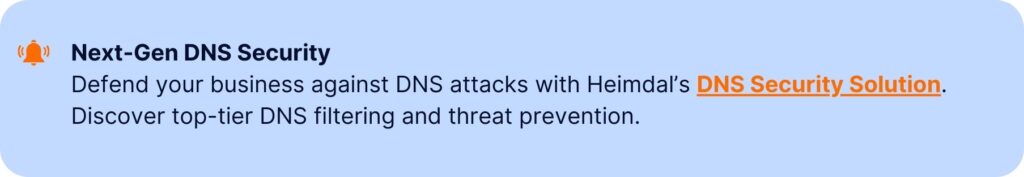
Denial-of-Service (DoS)
DoS is short for Denial-of-Service. A DoS attack aims at barring users from a machine or a network by either exhausting its resources or effectively shutting it down.
This DNS attack is largely used by hacktivists to make up a point in their fights against various political regimes or ideas. But there’s another reason why someone would try to turn a service unavailable.
A least known fact about DoS(s) is that hackers also use this type of DNS attack to hide tracks or hamper the victim’s recovery efforts. Here’s an example from cybersecurity expert Robertino Matausch:
Hackers may use DDoS attacks to shut down a banking page so you cannot log in.
Then they can create their own banking simulation page. Next, they send a phishing message saying “hey, we know we have problems, please use our secondary log in Page for logging in”. And then they start phishing credentials.
There are several kinds of DoS attacks, each levering a vulnerability or protocol\system\code limitation or unexpected machine-side replies. DoS attacks commonly aim high-value targets, like large companies and governmental institutions.
DNS Amplification
A DNS amplification attack, also known as DNS reflection, uses open DNS servers to overwhelm a victim’s system with DNS response traffic.
The attacker sends DNS queries to a DNS server but spoofs the queries to appear as though they are coming from the target’s IP address. Consequently, the DNS server will send the DNS record response to the target.
The request will ask as much information about the DNS zone as possible. The result is that the answer’s size will exceed the size of the query. This enables the hacker to boost the amount of traffic that will reach the victim’s server.
Using a botnet too send fake queries will amplify traffic, which will in the end block the target.
Resource Depletion
A resource depletion DoS attack relies on using up the device’s resource pools:
- CPU
- memory
- disk
- network
For instance, the attacker can drive up the CPU consumption of a forum-type application hosted on a server by bombarding the victim with intricate REGEX queries. To loop those queries, they will use a self-launching script.
For a memory depletion attack, the threat actor could upload hundreds of thousands of attachments to a draft mail, for example. Since unsent emails are stored locally, filling them with junk could exhaust the machine’s memory.
How about disk depletion? Most apps produce logs which are pretty useful for figuring out what went wrong with an app. Logs take up just a few kilobytes.
However, by knowing which “buttons” to push to recreate a specific error, the threat actor can force the application to fill up all the available disk space with logs. It takes a lot of research, and resources, but it can be done.
Buffer Overflow
The Buffer Overflow Attack (BOA) aims to force the system to write memory to a nearby buffer instead of the intended spot. When the memory is written in the buffer instead of the “regular” place, it causes the application using that memory to crash.
This type of limitation is endemic to C-written applications.
Hackers use buffer overflow attacks for more than DoS activities. For instance, an attacker can potentially tamper with or replace values in either the base pointer or the indicator pointer to run malware.
ICMP Flood
Also called a ping flood, this kind of DoS attack abuses a common connectivity test for crashing, freezing, rebooting, or rendering the target machine inoperable. Conventionally, the ICMP ping test helps determine the strength of connectivity between two endpoints operating on the same network.
A machine sends an ICMP echo request to another machine. In turn, the receiver sends back an echo reply. By measuring the round-trip, you can determine the connection’s strength.
Hackers abuse the ICMP mechanism to overload the victim’s network. Launching a ICMP flood attack has some requirements:
- the attacker’s bandwidth must be larger than the victim’s bandwidth
- they must know the victim’s IP address to focus the attack
- they have to search for information on the victim’s router
SYN Flood
Also called a “half-open” attack, the SYN flood abuses the TCP\IP three-way handshake mechanism.
I already covered the three-way handshake mechanism in a previous article. The way this works is that the attacker will trigger a deny user response in the server by repeatedly sending SYN packets and disregarding SYN-ACK, server-side packages.
Distributed Denial-of-Service (DDoS)
Distributed Denial-of-Service attacks use compromised hosts (bots) to launch full-scale DoS-type attacks on large targets.
DDoS attacks occur more frequently compared to simple DoS attacks. Why? Bots and botnets are readily available on the dark web and volumetric attacks have higher odds of success compared to DoS. Here are some common types of DDoS attacks.
UDP Flood
Fairly similar to the SYN flood, this type of DDoS leverages the User Datagram Protocol (UDP) and UDP packets. The attacker will flood the user’s opened ports with a bunch of junk UDP packets.
Thinking that these are legit UDP comm attempts, the host will attempt to listen on that port in search of the app sending those UDP packets. With no packets found, the host will have no choice but to reply with an ICMP unreachable destination packet. This goes on and on until the host’s network resources are exhausted.
ICMP Flood
Works the same way as the DoS counterpart. The only difference here is volume – DDoS attacks have the advantage of hundreds or thousands of bots capable of ICMP flooding the victim at the same time.
SYN Flood
Same DoS mechanism, but more “zombies” to do the heavy lifting.
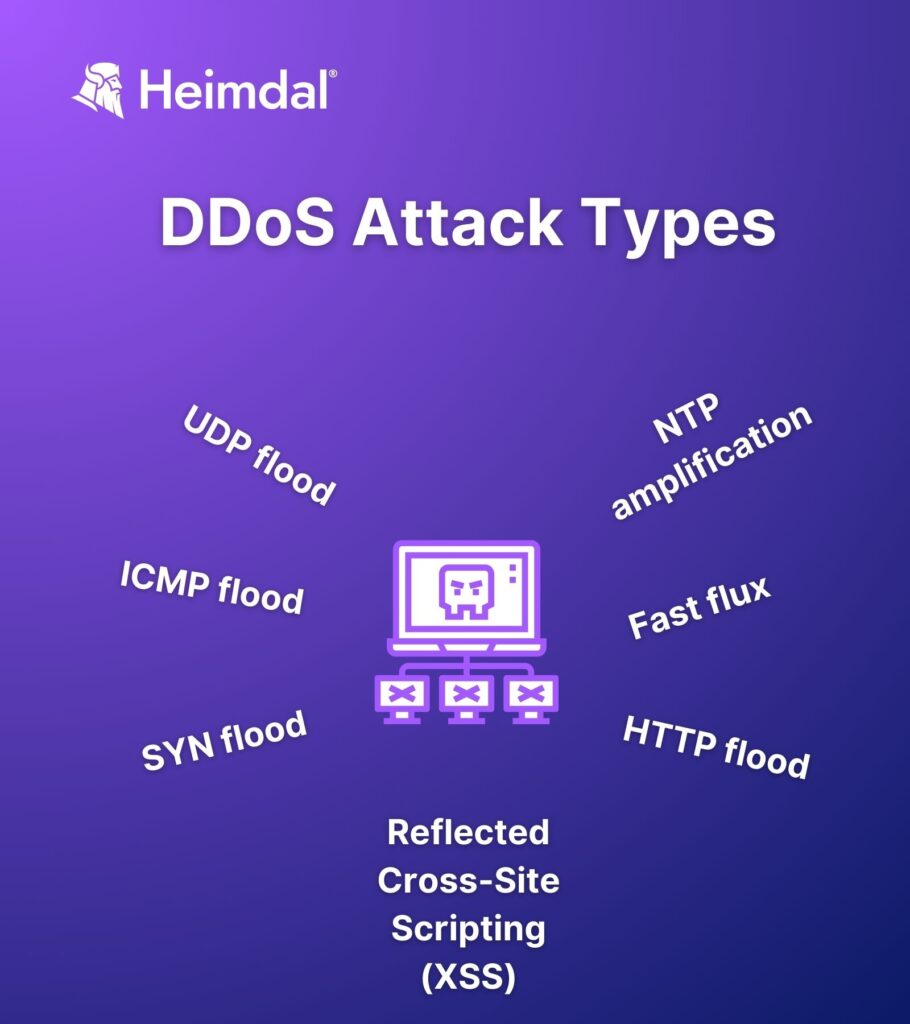
NTP Amplification
In Network Time Protocol (NTP) attacks the threat actor bombards public-facing NTP servers with UDP packets for DoS purposes. The name of the attack is given by how attackers exploit the so-called query-to-response ratio. The NTP server crashes when it’s no longer able to resolve all the queries received from the attacker.
HTTP flood
The HTTP flood is a very efficient DDoS attack, levering the GET or POST reply-response mechanisms. The threat actor sends as many legitimately GET or POST queries to the server, forcing it to answer each one of them. This resource-intensive replying process consumes server resources resulting in DoS.
Fast Flux
Fast flux is not an attack but rather an evasion method employed by botnet operators to avoid detection. With fast flux, threat actors can quickly change between compromised hosts, rendering them invisible to detection tools.
Reflected Cross-Site Scripting (XSS)
During a reflected cross-Site scripting attack (XSS), the threat actor seeks to abuse the HTPP response issued by an application receiving a request, kind of like an echo. The point is to discover whether or not an application receiving an HTTP request performs any kind of data checks upon receiving a query.
Here’s a quick example of this – some websites mirror back your search terms. So, if you search for something like “cat food”, you may receive a response such as <<you search for: “cat food”>>. In unsecured websites, threat actors could use this data processing method to append malicious arguments in the URL, resulting in an XSS attack.
In this case, the hacker will not be the one actually executing the attack. The blow would be dealt by the next user who searches for something on the website.
DNS Hijacking
DNS hijacking means that an attacker manipulates a query’s resolution, redirecting it to a compromised server that they control. By doing so, hackers can trick visitors into stumbling upon an infected website without their knowledge. This DNS attack is also known as DNS poisoning or DNS redirection.
DNS hijacking attacks are very common. A 2021 study found that 47% of companies that responded said they had experienced this kind of attack. 33% also noted cache poisoning, which is essentially the same thing as DNS hijacking.
DNS hijacking may also involve subversion or changing a reliable DNS server’s behavior. It’s not only hackers that can do it, but also reputable sources like your Internet service provider.
ISPs do this to gather information for stats, display adverts, and other self-serving uses. Additionally, DNS service providers may use traffic hijacking as a kind of censorship to prevent access to particular pages.

DNS Spoofing
DNS spoofing, also known as DNS cache poisoning, is a method that cybercriminals use to trick you into connecting to a malicious website rather than the one you intended. When someone requests to access a website through the Domain Name System and the DNS server responds with an inaccurate IP address, it is considered a DNS spoofing attack.
DNS spoofing can happen on both Microsoft Windows Server and BIND. First, the hacker identifies the domain you’re attempting to reach. Then they read your message and give you information leading you to assume you’re on a legitimate website. You would be routed to a fake website that mimics the legitimate one but is infected with malware.
Hackers use this method to access email accounts and other private data.
DNS Tunneling
DNS tunneling attacks help establish a channel for data to travel without triggering security tools. Hackers camouflage malicious data packets into apparently legitimate DNS queries to get through network filters and firewalls. By using DNS tunneling, they can secretly send data through networks that would normally block such traffic.
However, DNS tunneling is not intrinsically malicious. It is a technique that encapsulates data belonging to other protocols within DNS queries and responses.
Sometimes, to access websites that are restricted in a country or region, users evade censorship by employing a virtual private network (VPN), based on the DNS tunneling technique.
DNS Rebinding
DNS rebinding is a cyberattack that tricks a victim’s browser into connecting to a malicious site by exploiting the way browsers cache domain name resolutions.
To launch such a DNS attack, hackers can use any internet-connected device, including smartphones, without needing to authenticate.
By DNS rebinding attacks, attackers can reroute a victim’s browser’s request for a domain name to a malicious server. By altering the victim’s account URL, which forces all requests for this account to go via the attacker’s server, it can also be used to take control of social media accounts.
For example, if your browser or device is compromised, when you input www.mybankname.com into your address bar, you will end up on a malicious site instead of your bank’s one.
DNS Typosquatting
A social engineering attack technique inspired by DNS hijacking, DNS typosquatting uses typos and misspellings in domain names. A common DNS typosquatting attack starts with the attacker registering a domain name that is purposefully misspelled. However, it will look very much alike the real site’s domain name.
The attacker then develops a false website, designed to persuade users to provide sensitive information:
- login passwords
- credit card details
- other personal information
It’s www.paypall.com instead of www.paypal.com, for example.

Heimdal® Network DNS Security
- No need to deploy it on your endpoints;
- Protects any entry point into the organization, including BYODs;
- Stops even hidden threats using AI and your network traffic log;
- Complete DNS, HTTP and HTTPs protection, HIPS and HIDS;
How to Mitigate DNS Attacks
All of these DNS attacks can severely disrupt operations. Some DDoS and ransomware operators can destroy the data, device, or both after the attack’s done. Here are some mitigation measures you can apply against DNS attacks.
DoS Attack Mitigation
- Use legitimate cloud-based hosting.
- Implement availability monitoring.
- Don’t forget about registrar locking.
- Invest in an IDS\IPS tool.
- Complete automatic static and dynamic analysis.
- When in doubt, resort to the fuzz testing technique.
- Implement data execution prevention.
- Ensure that coding is secure.
- Take advantage of the compiler warning.
- Stack canaries.
- Curb the processing limit of inbound ICMP messages.
- Put perimeter firewall fine-tuning into use.
- Use the oldest half-open TCP\IP connection once the backlog is full.
- Don’t forget about SYN cookies.
DDoS Attack Mitigation
- Perform deep-packet inspection.
- Put traffic-scrubbing filters into effect.
- Keep the “worst is yet to come” rule in mind. Most DDoS attacks come in waves. The first wave is the attacker testing out defenses. Be sure to expect a second and even a third wave.
- Curb system response rate of ICMP packets.
- Perform regular traffic profiling.
- Keep IP reputation in mind.
- Execute JavaScript parsing.
- Verify IP sources.
- Disable monlist.
- Implement an access control
- Apply cyber-awareness practices such as not clicking on suspicious links, not opening emails from untrusted or unknown sources, etc.
- Use a web application firewall.
DNS Hijacking Attack Mitigation
- Shut down the DNS resolvers you don’t need
- Place legitimate DNS resolvers behind a firewall and ensure users outside of your organization cannot access them. Heimdal’s DNS Security – Network tool can help you with that. The solution’s Hybrid DNS module enables advanced filtering on any local DNS servers. You’ll be able to filter DNS traffic in your internal network, without any other intermediary.
- Separate your authoritative name server from the DNS resolver.
- Apply patches for known vulnerabilities as soon as they are released by their respective developers.
- Implement client lock on your DNS registrar.
- Ensure that your organization is using a DNS registrar with DNSSEC support.
- Always enable DNSSEC.
- Use an encrypted VPN connection for your enterprise.
- Implement a router password hygiene policy.
Conclusions
The prevention methods in the previous section can protect you only to a certain extent. DNS servers, by their nature, are one of the most exposed devices in your infrastructure.
For that extra ounce of protection, you should give Heimdal™ DNS Security a try. It brings DNS traffic filtering, deep-packet inspection, and everything you can think of in terms of DNS attack prevention at your fingertips.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security