Contents:
Industry reports highlight the urgency: vulnerability management systems are essential for identifying and mitigating risks before attackers strike. Malicious actors can exploit a vulnerability within just 15 days of its discovery (CISA).
The longer you wait, the larger the target on your back grows. Without proper vulnerability management tools, your business not only risks data breaches but also the loss of customer trust, and revenue, and potentially faces legal ramifications.
But with so many options to choose from, which solutions truly stand out in 2025?
What is Vulnerability Management?
Vulnerability management is a systematic process that identifies, evaluates, and addresses security flaws in an organization’s IT infrastructure.
By proactively detecting and mitigating vulnerabilities, organizations can improve their cybersecurity posture, reduce potential risks, and maintain the integrity and trustworthiness of their digital assets.
What are the top Vulnerability Management Systems & Tools in 2023?
To assist you in making an informed decision, I’ve prepared a list of the top 12 vulnerability management solutions and tools leading the way this year.
These systems play a critical role in proactively identifying, assessing, and mitigating security risks before they can be exploited.
For each one, you’ll find a brief overview of standout features, pros and cons, but also insights into their pricing structures and information on the availability of free plans or trials.
1. Heimdal® Patch & Asset Management
Heimdal stands out from the crowd, and it’s easy to see why: Heimdal® Patch & Asset Management streamlines the patching and vulnerability process, helping businesses save resources and shift from a reactive to a proactive security approach.
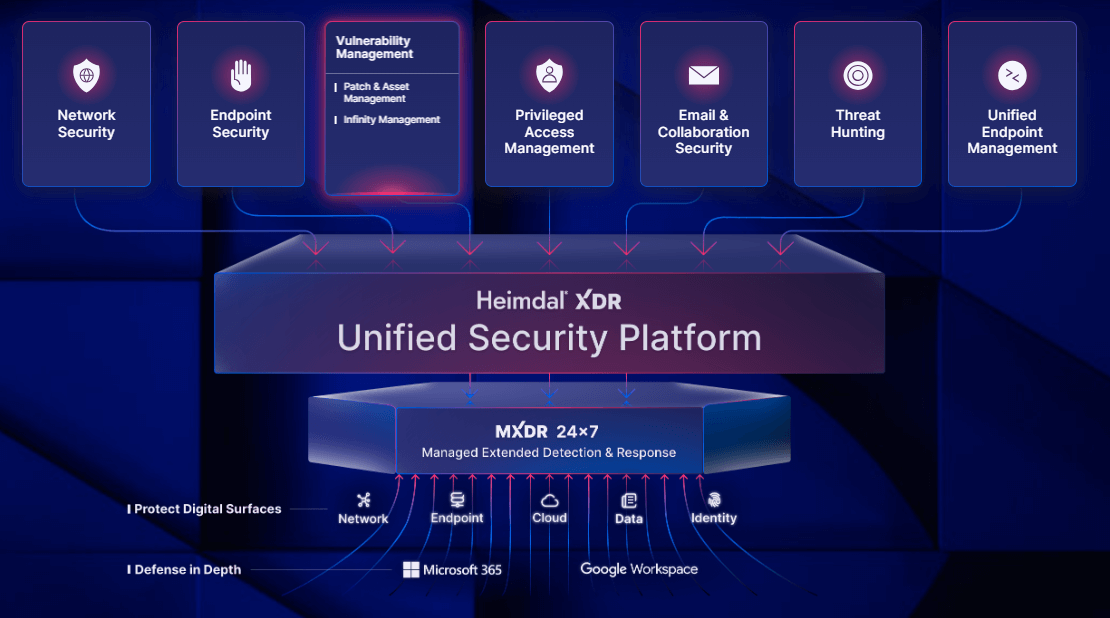
Whether it’s Microsoft, Apple, or Linux platforms, Heimdal’s seamless integration across all ensures that no vulnerability is left unaddressed. With a keen eye on compliance, from GDPR to Cyber Essentials, Heimdal helps companies maintain operational integrity.
And, perhaps most importantly, Heimdal optimizes productivity, smoothly managing vulnerabilities whether your team is onsite or globally distributed.
Features
- Unified Patching: It covers a range of platforms, from Windows, Linux, and macOS to third-party and proprietary apps, all under one roof.
- Asset Management: Heimdal allows users to generate detailed software and asset inventories effortlessly. Read a SysAdmin’s opinion about how patch management tools can help overcome patching challenges.
- Broad Application Support: With support for over 180 applications, Heimdal aims for thorough patching, reducing the need for multiple tools.
- Unparalleled Compliance: Heimdal simplifies compliance challenges by automatically generating reports tailored to GDPR, UK PSN, HIPAA, PCI-DSS, and NIST standards.
- Automated Vigilance: Helps admins handle vulnerability and risk management processes without manual intervention.
- Worldwide Accessibility: Heimdal allows administrators to schedule deployments to their liking, ensuring zero interruptions for end-users, irrespective of their global positioning.
- Customization at its Best: Above all, it can be fine-tuned to align perfectly with an organization’s specific security requirements.
Pros
- Seamless Deployment & Integration: Heimdal’s deployment ease, combined with its ability to update a wide range of software, ensures consistent coverage for all teams.
- Top-Notch Customer Support: Heimdal’s service is widely acclaimed, emphasizing not just product quality but also strong customer relationships.
- User-Friendly Design: Heimdal’s intuitive dashboard and hassle-free deployment make it a top choice for ease of use.
- XDR Capabilities: The full Heimdal suite offers 10+ integrated solutions with Extended Detection and Response capabilities that include patch and asset management but also privilege access management, DNS security, next-gen antivirus, ransomware encryption protection, threat hunting, and a 24×7 SOC service.
Cons
- Frequent Updates: Always adding new features based on client feedback, so expect regular updates and improvements.
Pricing
Our pricing model is regarded as competitive, providing good value while offering a comprehensive set of security features.
- Pricing covers all operating systems: Windows, Mac OS-X, and Android.
- Different price ranges for seat counts (1 to 20,000+) and servers (1 to 100+).
- Licensing costs vary by subscription period: monthly, yearly, 3-year, 5-year.
- Discount available for combined Threat Prevention for Perimeter and Endpoint based on seat counts.
Here are a few insights from users who shared their experience with Heimdal:
Heimdal’s patching and deployment software is the easiest and most flexible solution we used so far. I like the fact that it can do deployment and update of Microsoft and 3rd party software but also our in-house, which is rare to find.
We use its automation features with scheduling and can deploy to our employees anywhere they are, which is also a great benefit because our employees are 80% of the time working remotely.
General Manager, Retail Industry (Gartner)
The platform is an excellent way to automate patching for both Windows updates and third-party updates. The list of supported 3rd party apps continues to grow, and setup is straightforward.
A more complex module exists for bespoke deployments of bespoke/naturally unsupported software. This platform has allowed us to conform with CyberEssentials+ patch deployment.
IT Network Manager (Capterra)
2. Qualys
Qualys is a cloud-based assessment and vulnerability management tool that offers a wide range of features, including asset discovery, vulnerability scanning, and reporting. It’s known for its scalability and integration capabilities.
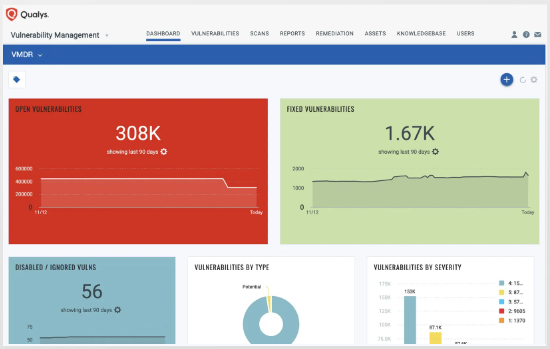
Features
- Vulnerability Identification: Pinpoints and organizes vulnerabilities across various platforms.
- Asset Management: Discovers and inventories IT assets, from hardware like servers to software components.
- Real-time Monitoring: Offers continuous insights into the security status of IT assets.
Pros
- Speedy Remediation: Efficiently addresses threats.
- Asset Oversight: Manages vulnerabilities throughout their lifecycle.
- User Interface: Clear and accurate interface with reduced false positives.
Cons
- Licensing: Many of Qualys’ features require additional licensing to use.
- Scan Result Delays: It can take a significant amount of time to retrieve scan results.
- Customer Support Concerns: Some users have noted issues with the quality of customer support.
Pricing
Qualys has a trial option and paid plans starting at $500/month.
3. Rapid7 InsightVM
Rapid7 InsightVM is a cloud-based vulnerability management program designed to offer scanning, monitoring, reporting, and remediation services. It claims to cater to small to mid-sized organizations by integrating with various endpoint security tools.
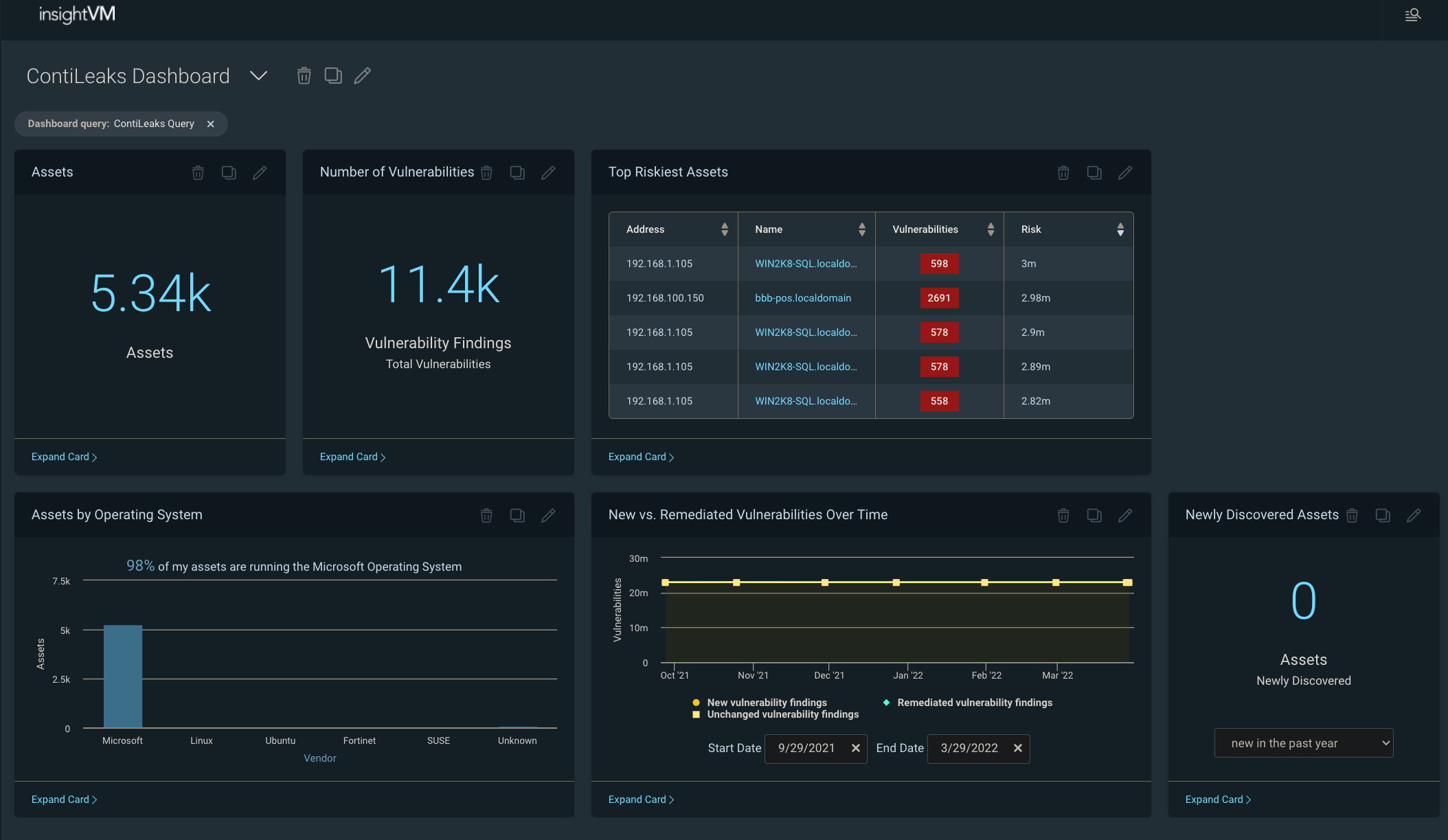
The platform emphasizes risk prioritization and can be outsourced as a managed service for organizations lacking robust security departments.
Features
- Real-time risk viewing through customizable dashboards.
- Integrated threat feeds and integrations with security solutions such as McAfee, CyberArk, and Palo Alto.
- Asset grouping with a focus on risk prioritization and step-by-step remediation guidance.
Pros
- Has a feature for vulnerability exceptions, letting organizations note accepted risks.
- Can be accessed as a managed service for teams without extensive security expertise.
Cons
- Costs can be high, with pricing determined by the number of assets.
- Instances of false positive findings and challenges with device removal.
- The database’s stability has been questioned, with some users citing significant data loss.
Pricing
Starting with a base of 250 assets, Rapid7’s cost is roughly $2.19 per asset each month. A free trial is available.
4. Tenable
Tenable offers a cloud-based vulnerability management tool that emphasizes a risk-based approach to detect and manage vulnerabilities across networks, websites, and applications.
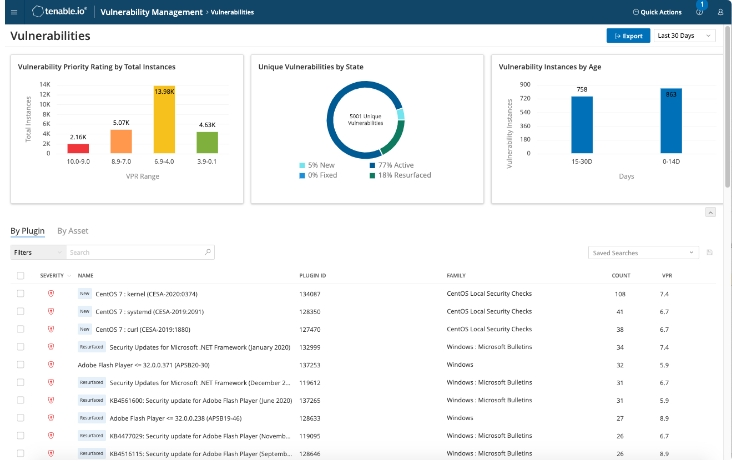
It provides real-time insights, leveraging threat intelligence to categorize and prioritize vulnerabilities based on their severity and potential impact.
Features
- Continuous monitoring and assessment of cloud assets.
- Prioritization of vulnerabilities based on threat intelligence and severity.
- Integration capabilities with third-party tools like AWS, Splunk, and ServiceNow, ensuring compliance and benchmarking against best practices.
Pros
- Offers comprehensive visibility across the entire IT environment, boasting robust CVE and security configuration support.
- Uses machine learning automation to analyze an extensive range of threats.
- Simplified initial setup and availability of predefined templates for asset assessment and auditing.
Cons
- Many essential features are hidden behind a paywall.
- The user interface has been noted to be less flexible and user-friendly.
- Customer support has garnered some negative feedback, and the pricing structure may not be appealing to all users.
Pricing
Tenable’s subscription begins at $2275 per year, covering protection for up to 65 assets. Free Trial is not available.
5. GFI Languard
GFI LanGuard is an enterprise vulnerability scanning, patch management, and network auditing solution suitable for protecting and managing a network’s security.
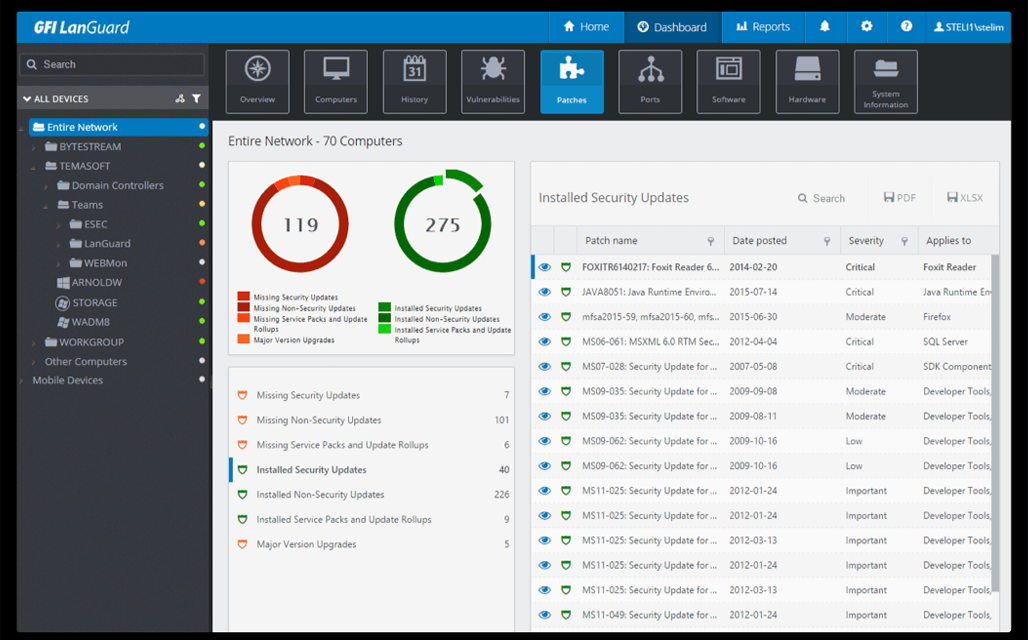
It specializes in automatically detecting network assets, monitoring them for vulnerabilities, and implementing patches centrally or on individual devices.
Features
- Comprehensive patch management capabilities, including patch rollback.
- Built-in vulnerability assessment database that scans for over 60,000 known vulnerabilities.
- Supports various virtual machines and includes asset discovery for network devices.
Pros
- Strong asset discovery for networking devices, such as routers, switches, and virtual machines.
- Regular updates to its vulnerability assessment database, ensuring protection against the latest threats.
Cons
- Lacks robust risk scoring and prioritization features.
- May not be suitable for large enterprises due to missing advanced functionalities.
- The automatic discovery and proactive monitoring might be overwhelming for some users.
Pricing
GFI LanGuard prices range between $10-26$ per machine per year. A free trial is available.
6. Intruder
Intruder is a cloud-based vulnerability management solution tailored to identify security vulnerabilities for internet-facing systems. The platform identifies vulnerabilities, provides real-time alerts, and suggests remediation strategies.
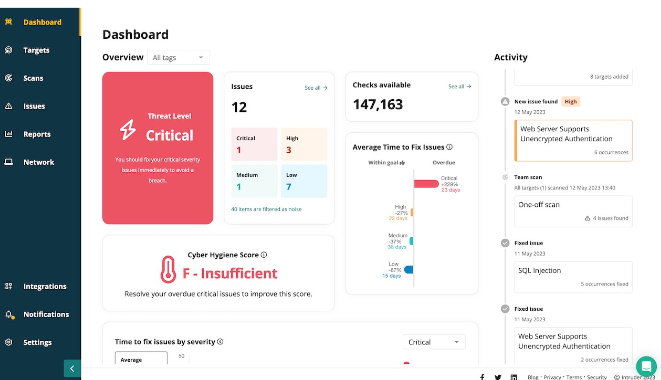
Features
- Continuous Scanning: Identifies vulnerabilities in digital assets.
- Responsive Monitoring: Initiates scans when changes are detected.
- Reporting: Produces prioritized vulnerability reports.
Pros
- User Interface: Designed for streamlined security management.
- Customer Support: Provides dedicated assistance.
Cons
- Complexity for Novices: While user-friendly, those new to vulnerability management programs may face a learning curve.
- Limited Free Trial: Offers a 30-day free trial for the Pro plan but might not suffice for comprehensive testing.
Pricing
Intruder offers a 30-day free trial for the Pro plan. Actual pricing varies based on assets scanned, with monthly or yearly billing options available via a quote on their website.
7. ManageEngine Vulnerability Manager Plus
ManageEngine Vulnerability Manager Plus is an on-premises powerful vulnerability management tool and compliance solution that offers extensive threat visibility, built-in, vulnerability detection and remediation, and CIS benchmark checks for system configurations.
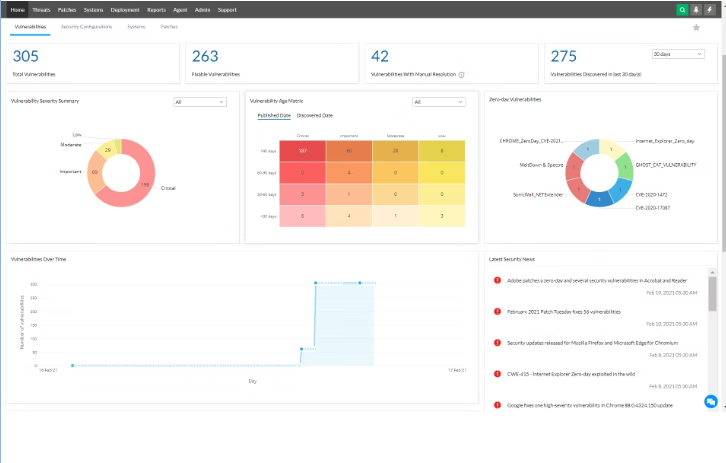
Features
- Continuous Vulnerability Assessment: Provides real-time scans and assessments of threats affecting OSs, applications, and servers.
- Automated Patch Management: Customizes and automates the patching process.
- Security Configuration Management: Includes over 75 CIS benchmarks for secure system baselining.
Pros
- Comprehensive Coverage: Scans and prioritizes vulnerabilities across OSs, and third-party applications.
- Built-in Remediation: Features robust tools for threat mitigation.
Cons
- macOS Limitations: macOS does not support the full range of vulnerability management tools.
- Manual Patch Approval: Vulnerability patches are not auto-approved and require manual intervention.
- Limited Immediate Patch Deployment: Allows only 50 clients to be selected for immediate patch deployment.
Pricing
Free edition available. Enterprise edition begins at $1195 per year. For the professional plan, users must contact ManageEngine for a quote.
8. TripWire
TripWire IP360 is a vulnerability management solution by Fortra that offers deep visibility across on-premises, container, and cloud assets.
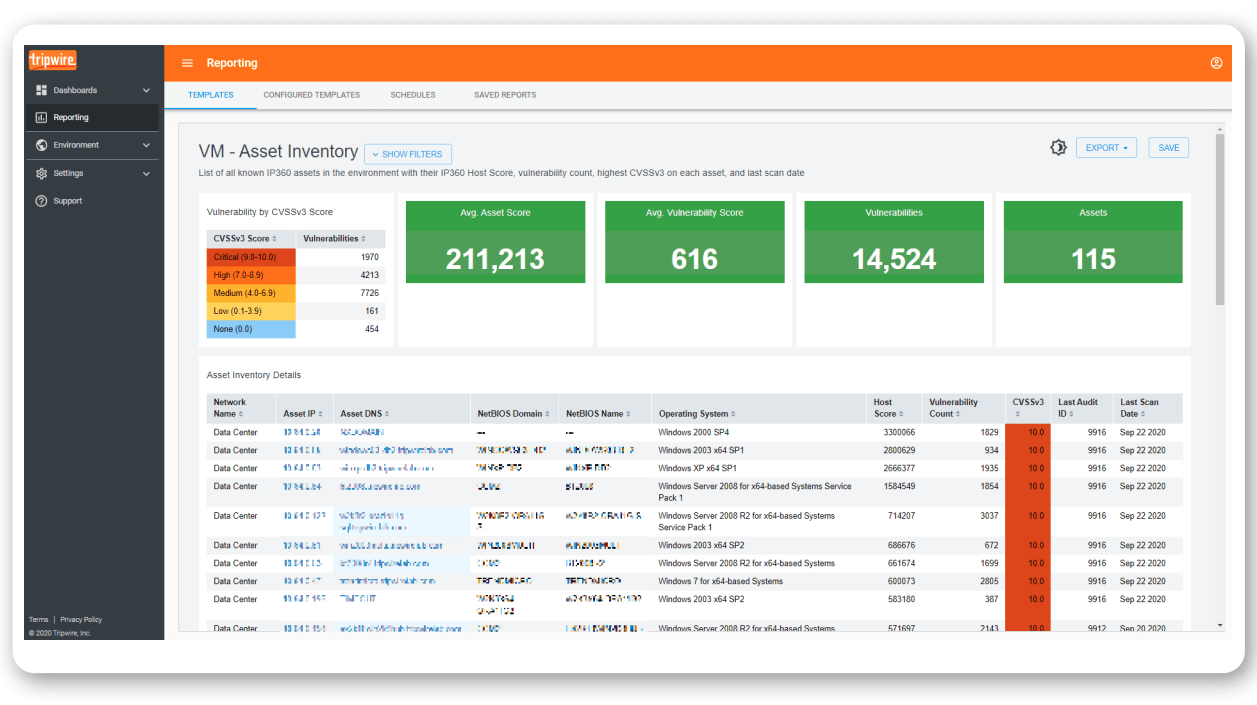
It prioritizes critical vulnerabilities using an advanced scoring system, integrates with existing systems, and ensures precise asset detection through agent-based and agentless scans.
Features
- Full Network Visibility: Provides insights across all assets in your organization, whether they’re on-premises, in containers, or in the cloud.
- Prioritized Risk Scoring: Uses a vulnerability risk scoring matrix that evolves with the age of the vulnerability and considers the potential risk of a successful exploit.
- Flexible Integration: Seamless integration with existing asset management systems, SIEM, and intrusion detection solutions.
Pros
- Detailed Vulnerability Scoring: TripWire’s scoring system provides a clear picture of vulnerability severity, aiding prioritization of remediation.
- Comprehensive Asset Detection: Both agent-based and agentless scanning methods ensure accurate identification of all assets.
Cons
- Complex Initial Setup: The deployment and initial setup of the software can be time-consuming, taking up to a week or more.
- Performance Issues: In some instances, the scanning process can cause performance disruptions.
- Customer Support Concerns: Some users have reported issues with technical support and found the professional services hard to engage.
Pricing
The pricing is available via a quote on their website.
9. Acunetix
Acunetix is a sophisticated application security testing platform that effectively scans and secures websites, APIs, and web applications.
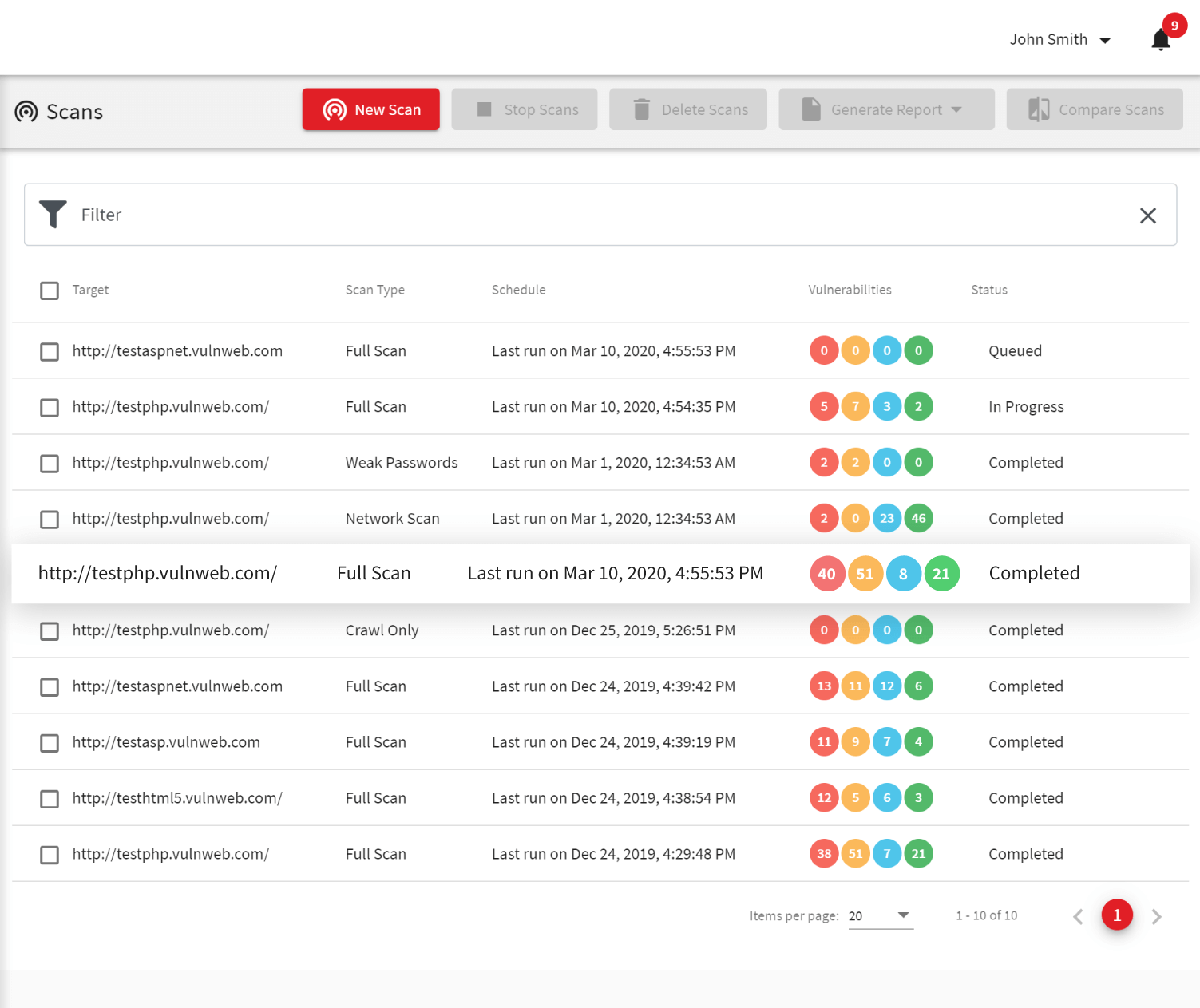
Recognized for over 7000 vulnerability scans, it ensures rapid detection without server overload, boasts advanced automation for scheduled scans and seamlessly integrates with numerous tracking systems.
Features
- Macro Recording Feature: Allows for scanning of password-protected areas and multi-level forms.
- Scan Scheduling: Provides automation for setting scans at specific times or intervals.
- Integration Features: Can integrate with various tracking systems, including Jira, Bugzilla, and Mantis.
Pros
- User-Restricted Views: The unique feature of multiple users and multiple roles ensures users only access the content relevant to them.
- Scanning Capabilities: Detects a range of vulnerabilities, such as SQL injections, XSS, and weak passwords.
Cons
- Stability Issues: Some versions of the tool have been reported as unstable.
- Scan Configuration Limitations: Offers fewer options for tweaking scan configurations.
Pricing
The pricing is available via a quote on their website.
10. SecPod SanerNow
SanerNow is a vulnerability management platform designed by SecPod. Its main function is to provide a consolidated approach to the vulnerability management process, integrating both vulnerability assessment and patch management.
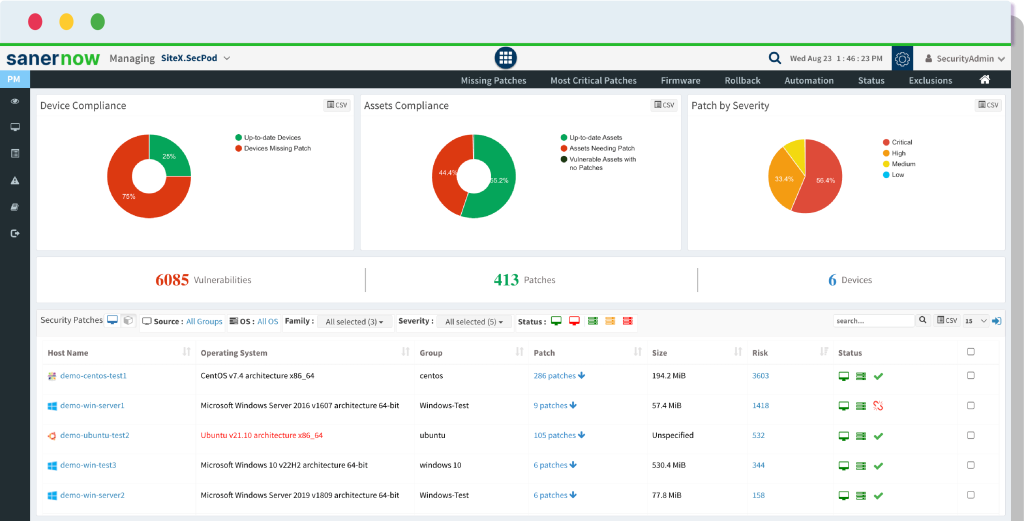
Features
- Rapid Scanning: Completes vulnerability scans in approximately 5 minutes.
- Extensive Database: Contains over 160,000 vulnerability checks.
- Compatibility: Supports major operating systems and networking hardware.
Pros
- Comprehensive end-to-end vulnerability management solution.
- Rapid detection and remediation capabilities.
- Supports a variety of OS and network devices.
Cons
- Some users say bugs and missing functionalities reduce the tool’s potential.
- Costs are comparatively high given its current capabilities, according to some users.
- A steep learning curve necessitates substantial training.
- Some interfaces, like the patch remediation, are inconsistent and non-responsive for some users.
Pricing
Pricing starts at $50/year/device. A free trial is not available.
11. Syxsense
Syxsense is a cloud-driven solution for businesses of varying sizes, focusing on endpoint management and security.
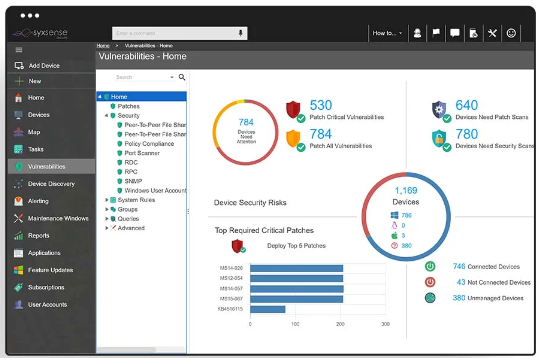
Features
- Automated Patching: Automatically rolls out patches for OS, and third-party applications, and even automates Windows 10 feature updates.
- Syxsense Cortex Remediation Workflow: Simplifies threat remediation using over 100 pre-built workflows for various vulnerabilities.
- Open API: Facilitates smooth data integration between Syxsense and existing IT and security tools.
- Custom Notifications & Reports: Tailor alerts, queries, and reports to fit unique organizational needs.
Pros
- Quick and hassle-free remote connections to users’ machines.
- Automation eliminates the need for manual updates.
- Convenient software packaging
Cons
- Remote control tools might exhibit instability over slower connections.
- Some users say that navigating between monitors can be cumbersome.
- A noticeable gap between vulnerability assessments and patch deployments.
Pricing
Pricing for Syxsense starts at $600 per year for a bundle of ten devices. A 14-day free trial is available.
12. Astra Pentest
Astra Pentest is a vulnerability management tool that blends automated scanning with manual penetration testing to provide a strong defense against potential security threats everywhere.
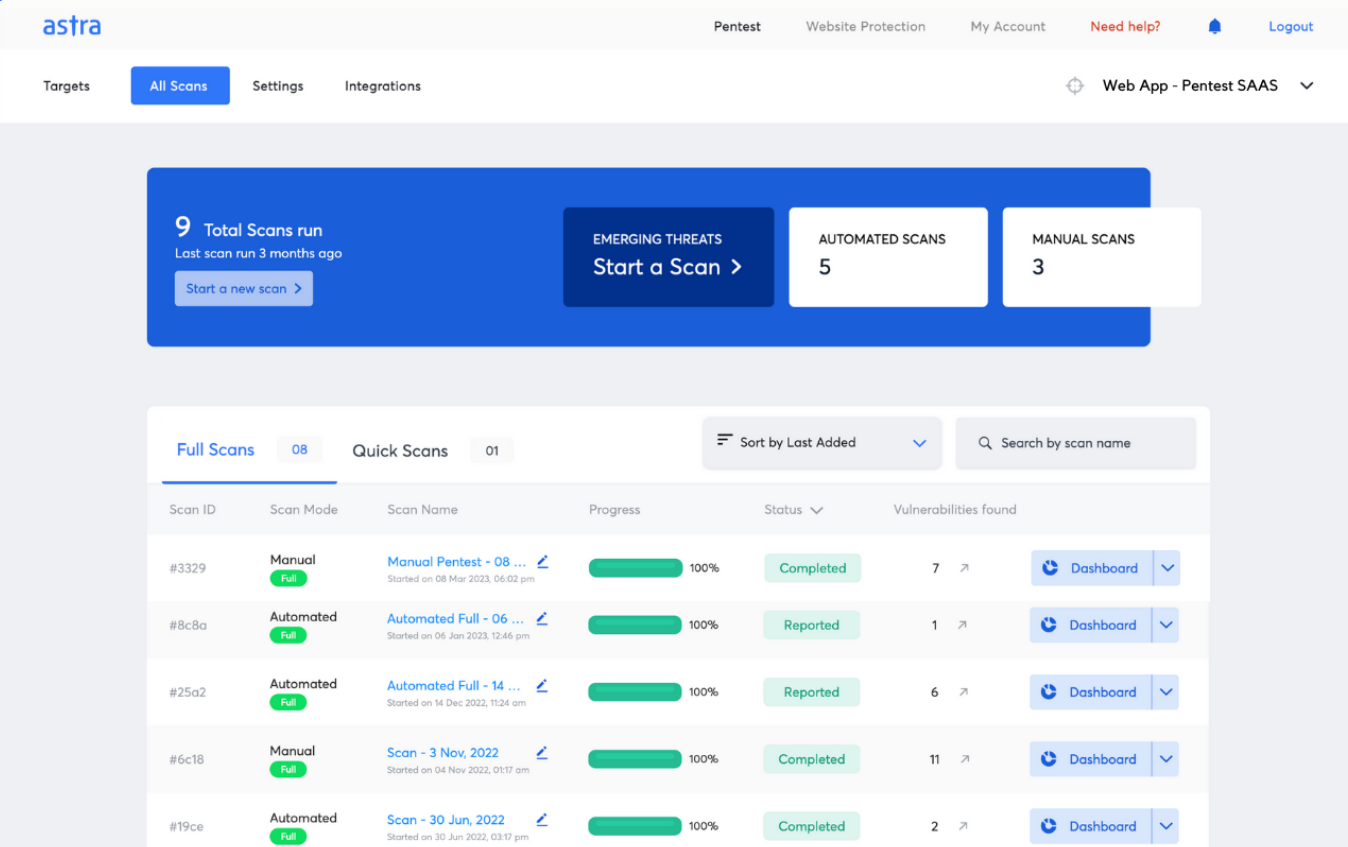
Features
- Broad Testing Scope: Conducts 8000+ tests covering major compliance standards.
- Continuous Scanning: Automates the scanning process to consistently look for vulnerabilities.
- Uses intelligence gathered from years of penetration testing and updates with the latest vulnerabilities.
- CI/CD Integration: Seamlessly integrates with platforms like GitLab and Slack.
Pros
- Integration with platforms like CI/CD, Slack, and Jira.
- Accurate risk scoring with detailed remediation guidelines.
- Swift and comprehensive support.
Cons
- Limited options when it comes to third-party integrations.
- Potential misses on certain malware attacks.
- Its high-powered scans can sometimes be intrusive, according to some users.
- Reliance on external manual pen-testing for optimal performance.
Pricing
Astra Pentest offers three pricing tiers, ranging from $199 to $6,999. They also provide a free trial of their service.
How can you benefit from a Vulnerability Management Solution?
Every organization has weak points in its digital defenses. From outdated software to overlooked security flaws, these vulnerabilities are prime targets for cyber attacks. By investing in a vulnerability management system, you aim to identify and patch these weak spots, reducing the risk of data breaches.
Now, let’s explore the key benefits of adopting this type of solution.
Stronger Security: Regular scans and updates enhance defenses, making it harder for threats to penetrate.
Cost Savings: By automating tasks, you can avoid expensive fixes in the future and ensure efficient resource use.
Prompt Response: Stay updated in real-time, allowing for quicker actions against new risks.
Clear Reporting: Get straightforward, actionable reports to understand the security situation better.
Efficient Workflows: Reduce manual tasks, focus on what matters, and ensure consistent security measures.
Regulatory Compliance: Some sectors require vulnerability assessments to maintain compliance standards.
The definitive list of Vulnerability Management Tools Features
To ensure the best vulnerability management software solution for your organization, consider your IT setup, budget, and unique security concerns. Thoroughly explore each choice, and run tests to identify the solution that truly fits your needs.
While every solution will vary in its offerings, I’d suggest ensuring that your choice includes the following features:
- Automated Patching: Offers automated fixes or clear guidance on fixing issues.
- Asset Inventory: Ensures that no devices or software are missed during the patching process.
- Easy Integration: Works well with other IT and security tools.
- Broad Scanning: Can scan various assets and detect the latest threats.
- Risk Ranking: Prioritizes vulnerabilities by their threat level.

Heimdal® Patch & Asset Management
- Create policies that meet your exact needs;
- Full compliance and CVE/CVSS audit trail;
- Gain extensive vulnerability intelligence;
- And much more than we can fit in here...
FAQs
What is a vulnerability management system?
Vulnerability management is a proactive and frequently automated strategy to protect computer systems, networks, and business apps from cyber threats and breaches. It’s an important component of a comprehensive security framework.
What is an example of vulnerability management?
Consistently updating software and security patches, automated patch management, limiting access to sensitive data and systems to only approved users, and employing scanning tools to detect and address vulnerabilities before they’re exploited.
What is CVE in vulnerability management?
CVE, or Common Vulnerabilities and Exposures, is a system that assigns standardized identifiers to known cybersecurity vulnerabilities and exposures, offering a public platform for sharing this information.
Comparatively, CVSS, or Common Vulnerability Scoring System, rates the severity of these vulnerabilities. Essentially, while CVE names and lists the vulnerability, CVSS provides its severity score.
Another vulnerability scoring system is EPSS – a tool that measures the probability of a CVE being exploited.
The top vulnerability for 2023 is CVE-2023-27350 — the year’s most critical threat. With a QDS of 100 and a severity rating of 9.8, it targets the widely-used print management software, PaperCut, and presents a major security risk to numerous enterprises.
How many new vulnerabilities were discovered in 2023?
In 2022, global internet users uncovered more than 25,000 new IT security vulnerabilities and exposures (CVEs), marking an all-time annual high. From January to April 2023, this count reached 7,489 (Statista).


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security











