Contents:
Selecting the best endpoint security software is crucial for protecting your organization from evolving cyber threats.
Choosing the right solution can feel overwhelming, especially in a market valued at 13.4 billion U.S. dollars in 2024 and expected to grow to 29 billion U.S. dollars by 2027.
That’s why we’ve listed the 12 best endpoint tools on the market, looking at the features, pros, cons, pricing, and more.
How can you benefit from endpoint security software?
A reliable endpoint security software solution provides various benefits that make it an attractive investment for a business.
Perhaps most importantly, this type of solution helps you protect your devices from potential threats, including ransomware, malware, viruses, and other malicious software that can wreak havoc on your operations, saving you time and money in the long run.
Secondly, it improves your organization’s ability to detect and respond to potential data breaches.
By constantly monitoring device behavior and network traffic, it quickly identifies suspicious activities or break-in attempts, enabling swift action to stop unauthorized access and data breaches.
Additionally, it enhances productivity by reducing downtime and minimizing the impact of cyberattacks.
Another perk is that it helps you achieve compliance, as endpoint security software protects connected devices, prevents data leakage, and ensures adherence to industry regulations.
What are the top endpoint security solutions in 2024?
To help you decide which one is best for your needs, I’ve carefully curated a list of the best 12 endpoint security solutions you should consider for your company.
1. Heimdal® EDR
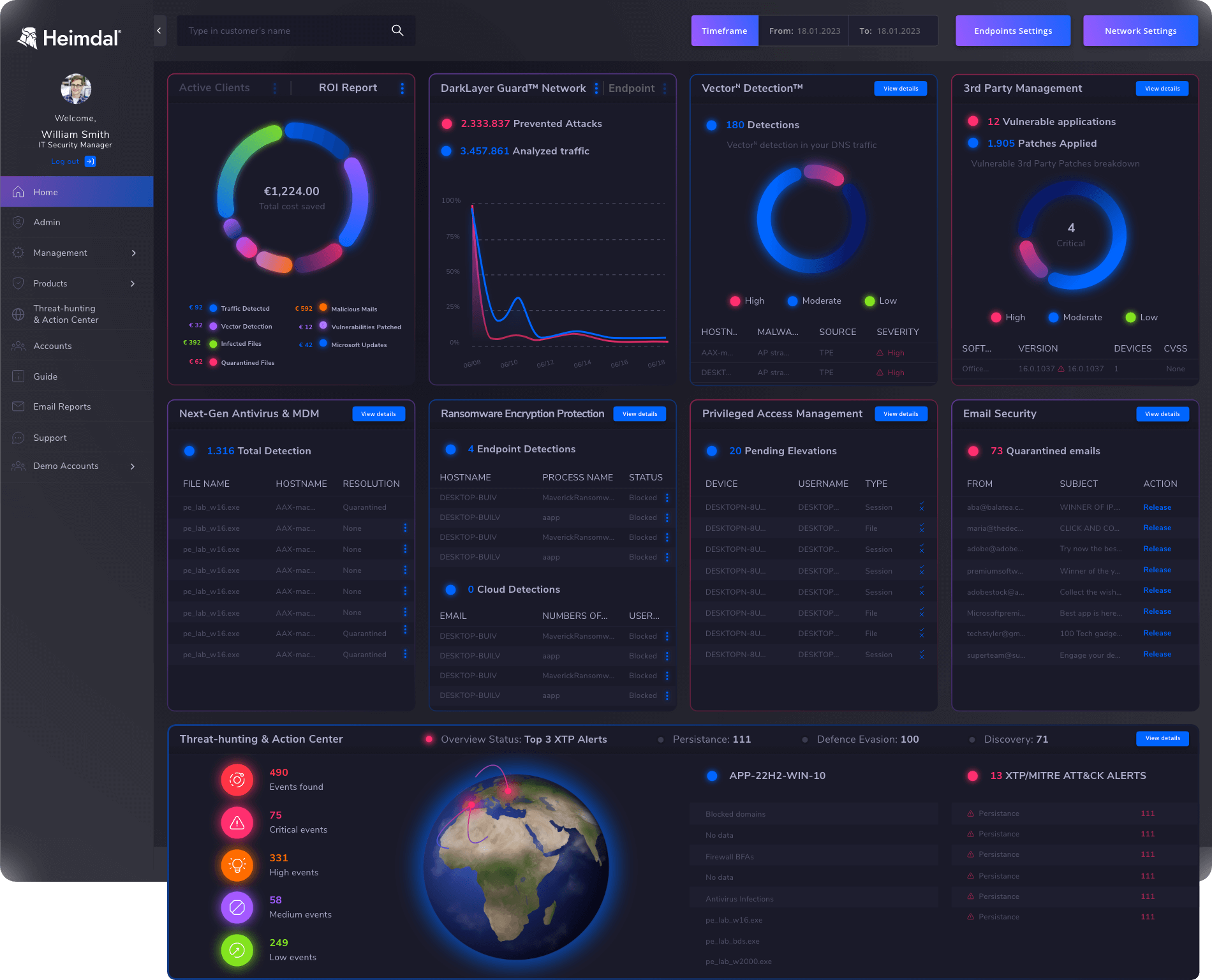
When it comes to choosing the best endpoint security tools, Heimdal® stands out as number 1, a trusted industry leader with a track record dating back to 2014.
For almost a decade, Heimdal has been dedicated to helping customers worldwide secure their domain name systems, earning a reputation for excellence along the way.
A key differentiator that sets Heimdal apart is its unique feature within the Threat Prevention Endpoint product – Predictive DNS.
This cutting-edge technology combines artificial intelligence and machine learning to continuously analyze user traffic in real-time.
By proactively identifying and blocking infected domains, this tool can achieve an impressive 97% accuracy rate in predicting threats.
In recent years, however, Heimdal went all the way and developed an entire suite of products to accommodate their customers’ needs and extended their endpoint security offering with 5 more products:
- Next-Gen Antivirus, Firewall & Mobile Device Management (MDM) solution
- Ransomware Encryption Protection Module (REP)
- Patch and Asset Management solution
- Privileged Access Management
- and an Application Control product
These six products work together to block malware, DNS-based attacks, MiTM, APTs, exploits, viruses, and brute force attacks.
They also prevent ransomware encryption, automate patching, manage permissions, and stop data breaches, offering comprehensive protection for your organization.
Best of all, they are managed from a single dashboard, streamlining security team efforts.
Heimdal®’s Top Endpoint Security Features
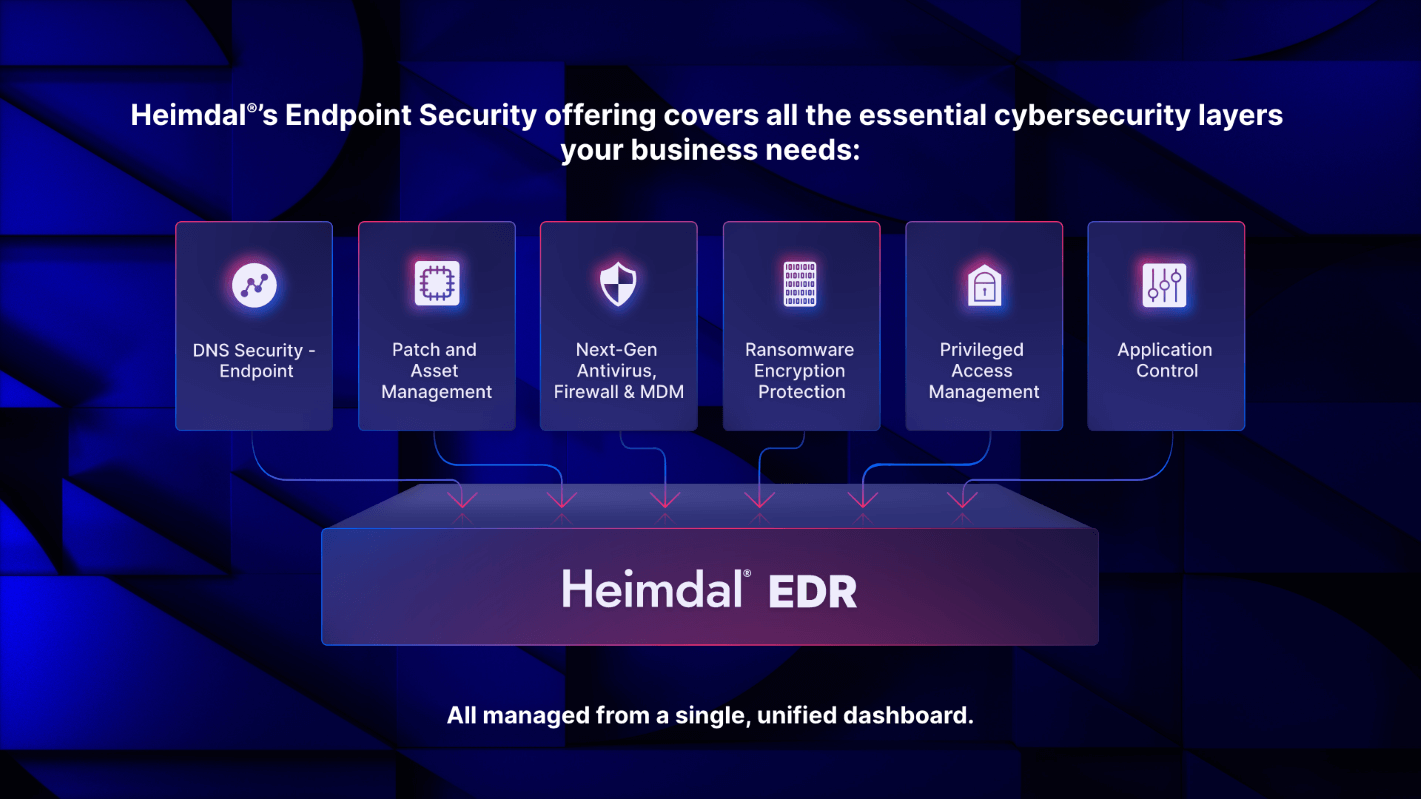
A six-in-one cybersecurity suite, essential to any business with multiple endpoints to protect:
- Integrates unique Predictive DNS feature powered by AI and ML.
- Real-time traffic scans proactively block malicious domains.
- Achieves an impressive 97% accuracy in threat prediction.
Heimdal’s DNS Security stands out with its Predictive DNS feature, employing AI and ML to scan user traffic on the go.
By proactively blocking infected domains and stopping communication with malicious infrastructures, it ensures robust protection.
Its remarkable compatibility with any system and quick deployment (less than an hour) make it an indispensable asset for any cybersecurity framework.
Ransomware Encryption Protection:
- Enhances the defense mechanism of existing antivirus tools
- Monitors disk structure for ransomware activity
- Swiftly detects processes initiating file encryptions & automatically isolates ransomware infections.
Heimdal’s Ransomware Encryption Protection acts as a vigilant sentinel.
It meticulously scans disk structures, swiftly detecting and isolating ransomware initiations. Moreover, it aids in tracing back to attacker origins and understanding the nexus of file connections.
Next-Gen Antivirus, Firewall & MDM:
- Merges both traditional and next-gen Antivirus methods
- Detects and handles a broad spectrum of threats from viruses to data leaks
- Leverages the potent XTP engine for comprehensive threat insights.
Heimdal’s endpoint security software acts as a vigilant sentinel, providing an extra layer of defense.
It meticulously scans disk structures, swiftly detecting and isolating ransomware initiations. Moreover, it aids in tracing back to attacker origins and understanding the nexus of file connections. This proactive approach minimizes damage and helps contain the threat before it spreads.
This ensures robust protection against viruses, APTs, financial frauds, and ransomware. With the power of the XTP engine, it dives deep into threat insights, aligning defense strategies with the MITRE ATT&CK tactics and techniques.
- Remotely and automatically install updates for Windows, Linux, and third-party applications
- Conveniently schedules updates according to your preference
- Easily tracks and manages your entire software inventory.
With automated updates, you can save considerable time and effort while ensuring that your systems stay up-to-date. The ability to remotely schedule updates offers flexibility and control over update deployment. Moreover, the comprehensive inventory feature provides a clear picture of all your software assets.
- Automatically elevates admin rights upon request
- Easily approves or rejects escalation requests with a single click
- Helps gain insights with a comprehensive audit trail of user behavior.
Heimdal’s PAM solution simplifies user privilege management. It automatically elevates admin rights, streamlining operations. One-click escalation control balances user freedom and security. An audit trail offers clear insight into user actions. Plus, smart auto-de-escalation boosts security when infections are detected.
- Removes permanent rights and provides access on a need-to-use basis
- Features a comprehensive audit trail for Allowed, Blocked, and Passive Mode executions
- Enhances security and control over application usage.
Heimdal’s Application Control enhances your security by granting application access only when necessary. With a complete audit trail of application executions, you gain valuable insights and maintain control over your software environment.
Heimdal® Endpoint Security Pros
- Automation Capabilities & Swift Response Time
Heimdal uses advanced technologies, powered by AI & ML to proactively detect both known and novel threats. This minimizes the window of opportunity for malicious activities to cause damage, as automated processes can detect, analyze, and respond to threats in real-time, often faster than a human analyst.
- Ability to Stop Malware at Entry Points
Heimdal intercepts malware by monitoring all points of ingress, and ensures it’s intercepted before it gains a foothold, providing a robust line of defense.
- Comprehensive Protection Against Advanced Threats
Heimdal goes beyond traditional security measures by harnessing the power of Machine Learning and AI-driven intelligence. It offers protection against a broad spectrum of threats, from Advanced Ransomware and Insider Threats to DNS Vulnerabilities and even unknown threats.
- Unified Endpoint Protection
Heimdal’s EDR system packs six next-gen security solutions into a single lightweight agent. This ensures streamlined deployment, efficient system performance, and comprehensive coverage against all potential attack vectors.
Heimdal® Endpoint Security Cons
Heimdal’s endpoint security offering covers DNS security, next-gen antivirus, firewall, mobile device management, ransomware encryption protection, vulnerability management, privileged access management, and application control.
If your organization has a more complex IT infrastructure, you can opt for the extended protection module, Heimdal XDR, that combines 10+ fully integrated security solutions to deliver next-level cybersecurity protection (and allows you to consolidate up to 7 disparate providers in a single platform).
New features are also in the works, as we love to innovate, so stay tuned!
Heimdal® Pricing
Our pricing model is regarded as competitive, providing good value while offering a comprehensive set of security features.
- Pricing covers all operating systems: Windows, Mac OS-X, and Android.
- Different price ranges for seat counts (1 to 20,000+) and servers (1 to 100+).
- Licensing costs vary by subscription period: monthly, yearly, 3-year, and 5-year.
- Discount available for combined Threat Prevention for Perimeter and Endpoint based on seat counts.
2. Cisco Secure Endpoint
Cisco Secure Endpoint, formerly known as Cisco AMP for Endpoints, is designed to provide advanced threat protection before, during, and after a cyberattack. It’s a known fact that Cisco has a long history in the world of networking technology, dating back to 1984.
But while Cisco is a veteran in networking and cybersecurity, Heimdal’s offering includes more products essential for endpoint security, such as Patch and Asset Management, Ransomware Encryption Protection, and Privileged Access Management, all managed from the same unified dashboard.
Main features:
- Advanced Threat Protection: Combines global threat intelligence, sandboxing, and continuous monitoring to proactively and retroactively guard against malware and breaches.
- In-depth Investigation & Response: Offers Endpoint Detection and Response (EDR), threat hunting, and detailed system snapshots via Orbital Advanced Search, facilitating thorough incident investigation.
Pros
- The licensing process is uncomplicated. Organizations only need to determine how many users they want on the system, ensuring that costs align with actual usage and scalability needs.
- One of its standout features is the centralized dashboard. This consolidates all security alerts, making it easier for IT teams to monitor potential threats and take appropriate action.
- Flexibility is another strength. The system allows administrators to group users and assign unique security protocols to each group. This customization ensures specific departments or teams have security measures tailored to their needs.
Cons
- Agent Deployment: Some users believe that it might be beneficial to refine how it handles process-based queries across all machines for even smoother integration.
- Interface and Response Time: The interface could be made a bit more intuitive. Additionally, a slight boost in query response time would enhance the user experience.
Pricing
Cisco’s Secure Endpoint pricing is not public but is perceived as reasonable. A free 30-day trial is available for companies with more than 50 employees.
3. VMware Carbon Black EDR
Carbon Black EDR is a security solution designed to provide comprehensive threat detection, incident response, and a range of other security services to protect endpoints.
But while Carbon Black is great for forensics, Heimdal has a significantly wider offering that also covers DNS security, automated patch management, ransomware encryption protection, and privilege access management.
Main features
- Comprehensive Endpoint Insight: Carbon Black EDR offers continuous monitoring and recording, which allows for post-event analyses and a deep understanding of endpoint behaviors.
- Proactive Security: It integrates threat-hunting capabilities, behavior-driven detection, and the latest threat data to spot issues early.
- Cloud-Centric & Customizable: Designed with a cloud-first approach, it ensures smooth scalability and straightforward deployment.
Pros
- Efficient Resource Use: VMware Carbon Black EDR is optimized to use minimal system resources, ensuring smooth operations.
- Intuitive Interface & Functionalities: The software has great UI & UX, making navigation straightforward. Its threat-hunting capabilities and live response tools further enhance its usability and effectiveness.
Cons
- Limited Triage Capabilities: The software does not offer the ability to download triage for any host, potentially limiting detailed offline analyses or investigations.
- Delayed Bug Fixes: Customer-reported bugs are not promptly addressed, often requiring 2-3 update cycles to resolve the underlying issues. This can lead to prolonged periods where users experience known problems.
Pricing
Carbon Black products are sold through partners. Costs vary based on the number of protected endpoints and subscription duration, with longer terms offering more savings. For instance, a partner might charge $52.99 per endpoint for a one-year subscription, which reduces to $38.40 for five years.
Though higher priced than many competitors, VMware Carbon Black offers EDR features that others might not. However, VMware’s indirect pricing approach contrasts with the more transparent practices of some modern security SaaS competitors.
4. Cybereason Defense Platform
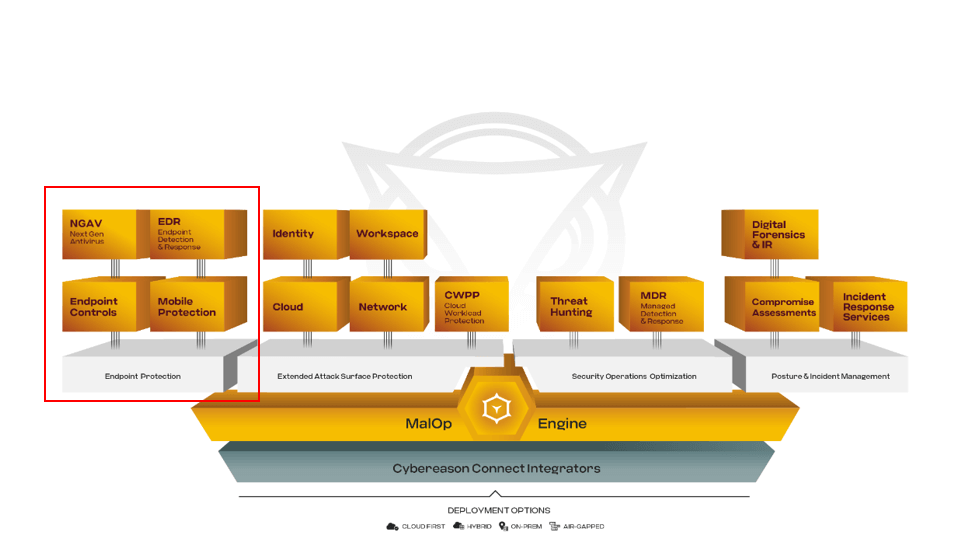
The Cybereason Defense Platform is an integrated cybersecurity solution offering endpoint detection and response (EDR), advanced antivirus, and threat hunting. Using a behavior-based approach, it provides in-depth insights into complex cyber threats, focusing on the broader context of attacks rather than isolated alerts.
However, if you’re looking for a solution that could also help you with vulnerability and privileged access management and a friendlier interface, Heimdal is the better choice.
Main features
- Endpoint Detection and Response (EDR): Real-time monitoring and analysis of endpoint activities to identify and respond to threats.
- Next-Generation Antivirus (NGAV): Advanced protection against malware and other malicious software, leveraging behavioral analysis rather than just signature-based detection.
- Threat Hunting: Proactive tools and insights to search for, identify, and neutralize potential threats before they manifest as attacks.
Pros
- Ease of Deployment: Cybereason can be quickly and effortlessly set up in an environment.
- Efficient Detection, Mitigation, and Response: The platform is highly effective at identifying threats and taking prompt corrective actions.
- Accurate Results: Utilizing the MOSS scoring system, coupled with actual analyst insights, ensures immediate and precise threat evaluations.
Cons
- Challenging Product Tuning: The platform can be hard to manage and potentially challenging to adjust for optimal performance, according to some users.
- Customer Service Issues: The support team’s responsiveness and quality of assistance have been found lacking by some users.
Pricing
Pricing for Cybereason’s Cyber Defense Platform begins at $50 per endpoint, with discounts available for bulk purchases. A free trial is available.
5. ESET Enterprise Inspector
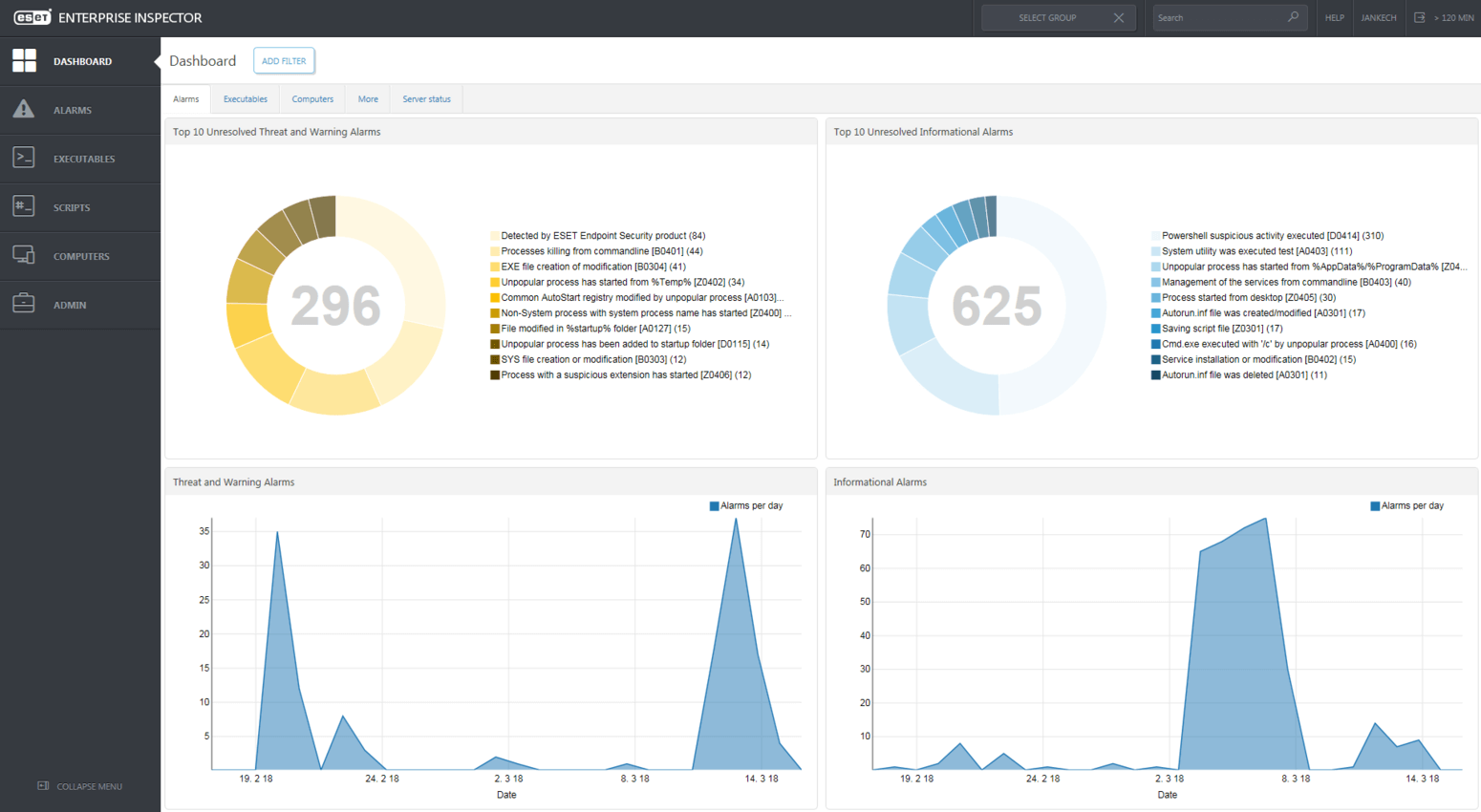
ESET Enterprise Inspector is ESET’s EDR solution designed to detect unusual activities, identify breaches, assess risks, and conduct in-depth forensic analyses. It also includes features to address and neutralize identified threats.
The Heimdal solution stands out by providing a broader perspective on the threat landscape by mixing prevention and detection capabilities (DNS filtering, patching, privilege access management, ransomware encryption protection), whereas ESET is focused on a traditional, reactive approach.
Main features
- Incident Handling: ESET Inspect identifies and manages security incidents, offering comprehensive response capabilities to mitigate detected threats.
- Threat Detection: The system recognizes indicators of compromise, anomalies, and unusual behavior patterns that might signal potential security threats.
- Policy Enforcement: ESET Inspect monitors for policy violations and ensures adherence to organizational security policies.
Pros
- Customizable Rules: the ability to create rules using XML language, which track and filter endpoint events. If an event aligns with a rule, the rule is activated.
- Exception Handling: the capacity to manage false positives by implementing exceptions, especially beneficial when dealing with a large volume of data.
- Learning Mode: helps in creating exceptions for processes that are known and have a good reputation.
Cons
- Resource-Intensive: In a Virtual Desktop Infrastructure (VDI) environment, ESET can have a negative impact during installation, consuming resources and causing user slowdowns, according to some users.
- Hardware Requirements: ESET may be too bulky for computers with lower processing power, making it more suitable for powerful PCs.
- Support Issues: The support team might not be as helpful as desired, particularly for small businesses.
Pricing
The pricing for ESET Enterprise Inspector depends on the number of users. For a 1-year subscription, the price per endpoint is around:
- 100-249 Users: $32
- 250-499 Users: $28
- 500-999 Users: $26
6. Harmony Endpoint (Check Point Software)
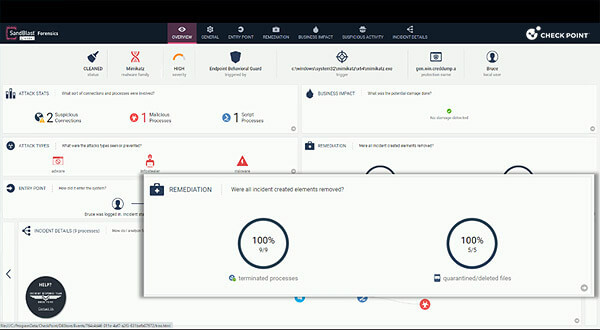
Harmony Endpoint is a comprehensive endpoint security solution designed to protect remote workers from complex threats, combining advanced EPP, EDR, and XDR capabilities in a single client.
Both Harmony Endpoint and Heimdal offer solid endpoint security solutions, but Heimdal stands out in terms of architectural considerations, and investigation capabilities and it has a wider business offering that includes automated patching, privilege access management, and ransomware encryption protection.
Main features
- Complete Endpoint Security: It provides full security coverage for devices used by remote workers, protecting against a wide range of threats.
- 360-degree Protection: Offers all-around protection for endpoints (devices like laptops and smartphones).
- Advanced Features: Comes with advanced security tools, including EPP (Endpoint Protection Platform), EDR (Endpoint Detection and Response), and XDR (Extended Detection and Response).
Pros
- Ease of Use and Setup: Harmony Endpoint is stable, easy to install and configure, and offers a user-friendly interface that allows quick access to its features.
- Efficient Resource Use: The solution consumes minimal system resources, making it suitable for various systems without impacting performance.
- Advanced Security and Insights: uses artificial intelligence and machine learning for proactive threat prediction and provides comprehensive forensic analysis with detailed and customizable reports for understanding threats better.
Cons
- Technical Support Issues: The technical support team is not very responsive, leading to longer wait times for assistance, according to some users.
- Integration and Compatibility Challenges: Some users say that integration with existing endpoint solutions can be difficult, and there are issues when attempting to install Harmony on machines with varying operating system versions.
Pricing
The pricing is available per request and varies depending on company size and security demands, but is generally seen as competitive. A free trial is available.
7. Malwarebytes EDR
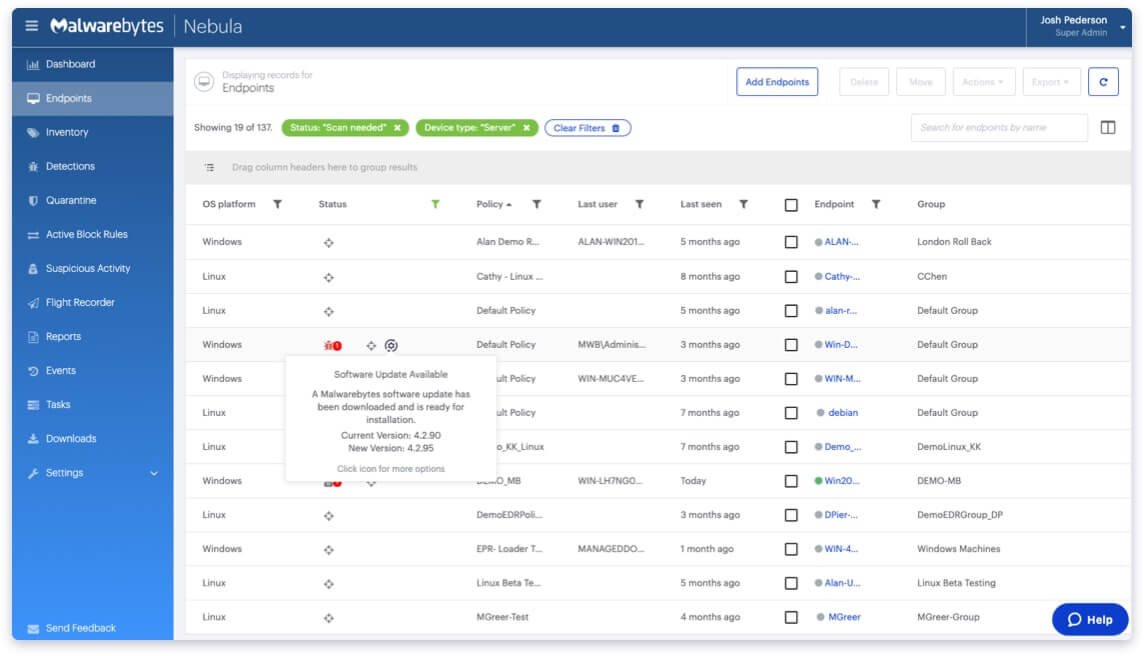
Malwarebytes EDR is a business-focused security solution that provides real-time threat detection, investigation, and response capabilities across an organization’s network, along with comprehensive reporting and analytics.
But Heimdal EDR stands out with a wider lineup of security features, including patching, exploit mitigation, DNS/HTTP/HTTPS filtering, antivirus, ransomware encryption protection, data leakage protection, and a firewall. It also includes privilege access management and application control.
Main features
- Real-Time Protection and Response: Malwarebytes EDR offers real-time threat detection, incident investigation, and response capabilities, including endpoint isolation and ransomware rollback.
- Comprehensive Insights: Provides detailed reporting and analytics to understand the organization’s security posture, trends, and scope of security incidents.
- Centralized Management: Offers a unified dashboard for centralized management and monitoring of endpoint security across Windows, macOS, and Linux platforms.
Pros
- Ease of Use: user-friendly for both administrators and end-users, making it simple to set up and operate.
- Flexible Configuration: It can be tailored to minimize system impact on older or slower machines, ensuring optimal performance across different systems.
- Cloud-based Management: The cloud-based platform allows administrators to monitor the security status of every machine on the network remotely, offering immediate insights into compromises or threats.
Cons
- Insufficient Documentation: Some new features may not be well-documented during their initial release, which can lead to confusion during the setup process.
- Support Delays: There may be occasional delays in resolving support tickets, leading to longer wait times for issue resolution.
- Limited Trial Features and Alerting: The trial version of Malwarebytes EDR has restricted features, and the alerting functionalities of the product might not be as comprehensive as desired, according to some users.
Pricing
The price for Malwarebytes Endpoint Protection for 10-99 devices starts at $4.96 per device per month. A free trial is available.
8. Microsoft Defender for Endpoint
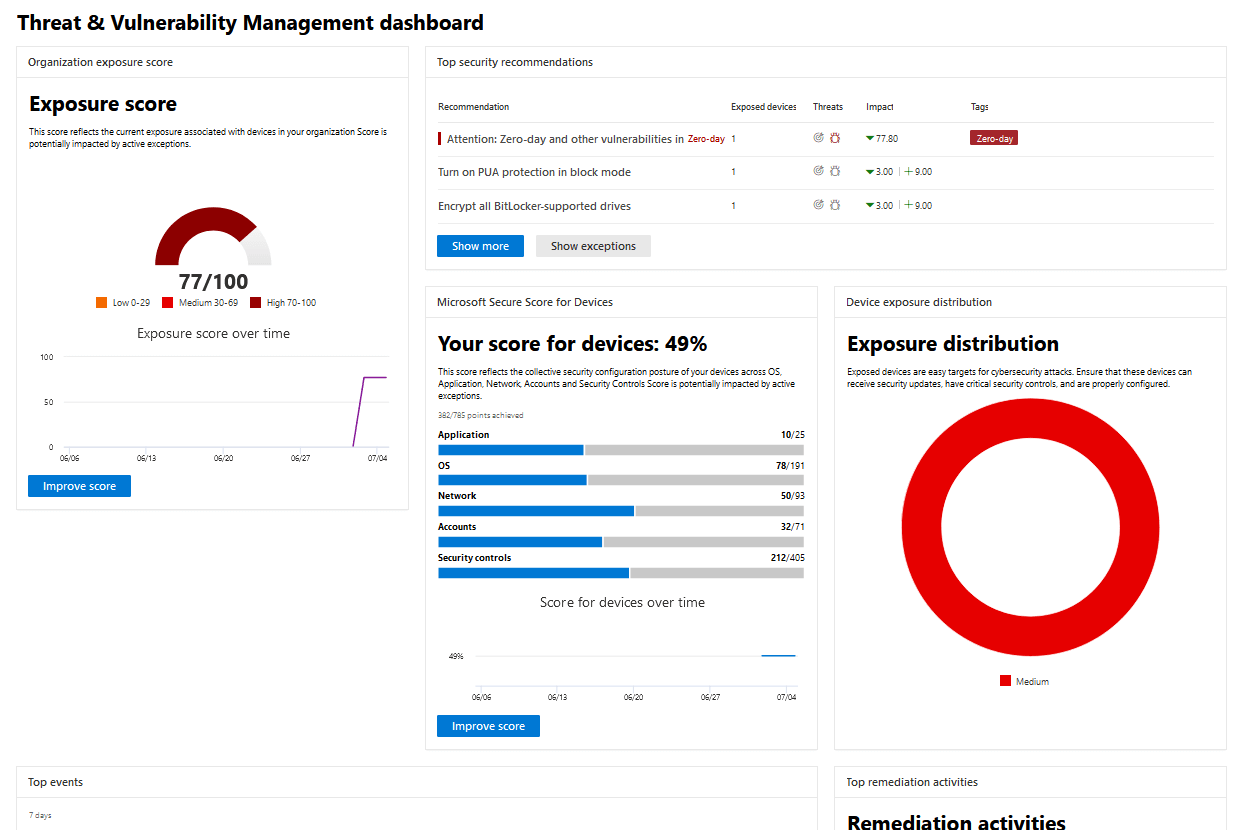
Microsoft Defender for Endpoint is an enterprise-grade security platform that safeguards endpoints from advanced threats, providing tools for prevention, detection, investigation, and response.
Heimdal stands out with a more comprehensive offering that also includes automated patching for Linux OS, 3rd party and proprietary software, privilege access management, ransomware encryption protection, and application control.
Main features
- Threat and Vulnerability Management: Microsoft Defender identifies and manages vulnerabilities, enhancing overall security posture.
- Next-generation Protection: Incorporating modern defense technologies, it offers advanced protection against threats.
- Endpoint Detection and Response (EDR): It provides robust tools for detecting and responding to security incidents on endpoints.
Pros
- User-Friendly Interface: Microsoft Defender features a simple, intuitive user interface that is accessible to users of all technical skill levels.
- Robust Malware Protection: The software provides strong protection against malware and other cyber threats, ensuring comprehensive security.
- Good Performance: Despite its robust protection features, Microsoft Defender maintains high-performance levels on devices, ensuring a seamless user experience.
Cons
Limited Customization: Microsoft Defender’s user interface, while streamlined and uncluttered, offers limited customization options and granular control over policy settings compared to some competitors.
- Inadequate Alert Context: When investigating alerts, the information provided on the alert page may not offer enough context to enable further in-depth investigation, which can be frustrating for some users.
- Confusing Exception Implementation: Implementing exceptions can be confusing, especially during organizational transitions such as migrating from Microsoft Endpoint Configuration Manager (MECM) to Intune.
Pricing
Microsoft Defender for Endpoint provides a free trial and a variety of pricing options ranging from $10 to $57 per user per month.
9. Sophos Intercept X
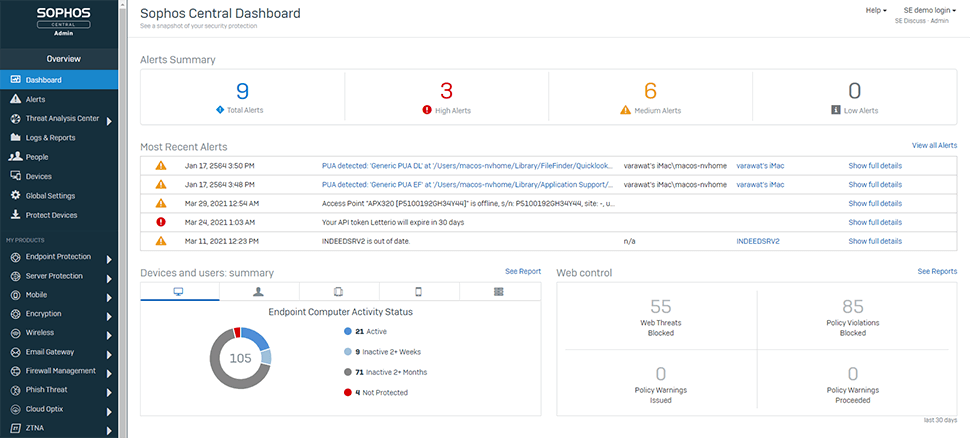
Sophos Intercept X is a cloud-based endpoint protection solution that builds upon the features of Sophos Endpoint Protection, an on-premise solution. It offers anti-malware, application control, data loss prevention (DLP), intrusion prevention system (IPS), and mobile device management (MDM) features.
But while Sophos is focused on remediation, Heimdal is more focused on prevention. Heimdal has a stronger patching product that offers full Windows and 3rd party patching and customization, HTTP/HTTPS/DNS traffic filtering solution, and a privilege access management module.
Main features
- AI/Machine Learning: Intercept X leverages advanced AI and machine learning technologies to detect and protect against new and emerging threats.
- Activity Dashboard and Tracking: The platform features a comprehensive activity dashboard and tracking system that provides real-time monitoring and reporting of endpoint activities.
- Multifaceted Security Features: Intercept X offers a wide range of security features including anti-virus, application security, behavioral analytics, and data collection, providing comprehensive protection against various threats.
Pros
- Anti-Ransomware & Anti-Exploit: Intercept X excels in protecting against ransomware and exploit attacks, offering both online and offline protection, as well as the ability to roll back any unwanted encryption caused by ransomware.
- Ease of Use with Cloud Management: The cloud management feature in Intercept X allows for easy and convenient management of the security solution.
Cons
- Support: The support services for Intercept X can be slow to respond and resolve issues, which can be frustrating for some users.
- Resource-Intensive: The software may use a lot of system resources, particularly during scans, leading to a decrease in overall system performance.
- User Interface Issues: Some users may find the navigation panel on the left side of the web user interface to be lacking in terms of usability and design.
Pricing
Sophos Intercept X offers three pricing tiers, ranging from $28 to $79. The pricing options are available by request on their website. A free trial is not available.
10. Symantec Advanced Threat Protection
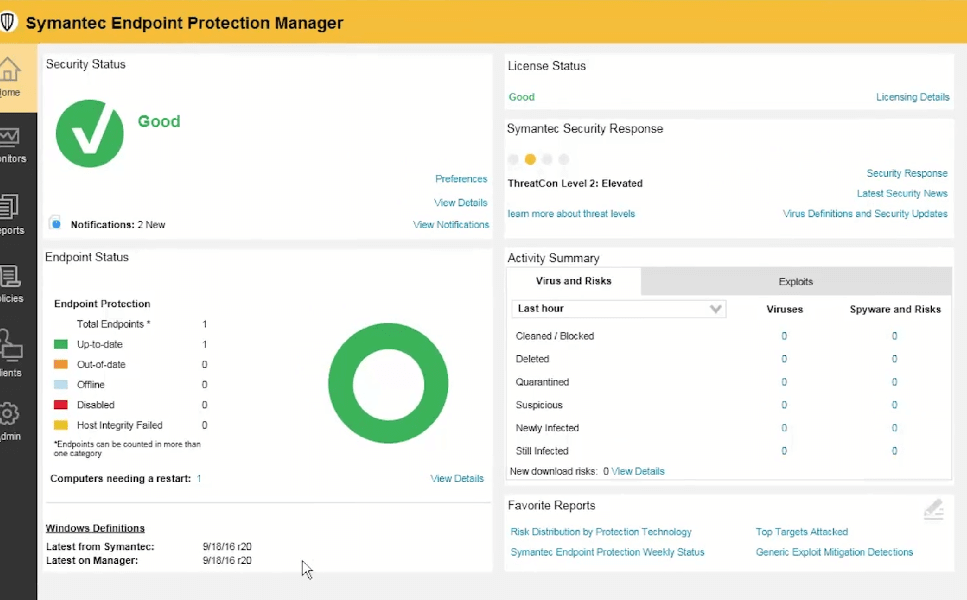
Symantec Advanced Threat Protection is a unified security solution that combines intelligence from endpoint, network, and email control points with Symantec’s global sensor network to detect, prioritize, and remediate advanced threats without requiring the deployment of new agents.
Heimdal covers a bigger attack surface than Symantec, delivering DNS security, patching for both MS and 3rd party, ransomware encryption protection, a next-gen AV, and privilege access management.
Main features
- Control Compliance Suite: allows organizations to automatically assess their security measures and compliance with various regulatory frameworks and best practices.
- Encryption: includes encryption capabilities, which means it can encode data to protect it from unauthorized access.
- Security Analytics: in-depth network traffic analysis and forensic tools to help organizations identify security threats in real time.
Pros
- Effective Threat Detection: comes equipped with built-in rules to detect threats and anomalies.
- Fast and Smooth Log Analysis: uses the ELK stack (Elasticsearch, Logstash, and Kibana) for log analysis and storage, delivering fast and seamless investigation capabilities.
- Ease of Use and Remediation: easy to set up and has a user-friendly, clear, and fast GUI. The platform also offers various options for threat remediation, including the ability to counter complex attacks and delete malicious files across all endpoints.
Cons
- Conflict with Other Software: Users have reported that Symantec ATP can conflict with other monitoring software, leading to issues in the overall system operation.
- Slow Support Response: Some users have expressed dissatisfaction with the speed of response and level of assistance provided by the support team when trying to resolve software conflicts and other issues.
- Performance Degradation: Some users said that, depending on the device and the level of detail required in the scan, Symantec ATP can slow down the system and consume a significant amount of RAM, which may affect the performance of other applications running on the device.
Pricing
Symantec does not have a free trial version. The pricing is only available via request, but according to one of their partner websites, the costs start at $39.00 per endpoint per year.
11. Trend Micro
Trend Micro is a global cybersecurity company offering a range of solutions to protect against cyber threats such as malware, ransomware, and phishing for individuals, businesses, and enterprises.
Heimdal stands out with a more comprehensive offer that includes DNS security, automated patching, ransomware encryption protection, privilege access management, and more, all managed from the same unified dashboard.
Main features
- Security Risk Protection: safeguards computers from threats like viruses, malware, and spyware, regularly updating the server for the latest protection.
- Web Reputation and Anti-Spyware: uses Web Reputation technology to block harmful websites and protects against a diverse range of spyware.
- Plug-ins and Security Features: includes a customizable plug-in manager, an integrated firewall, and cleanup services to remove malicious remnants.
Pros
- Effective and Versatile Protection: offers comprehensive protection against various threats, ensuring businesses are safe from potential security incidents.
- Simplicity and User-Friendly: easy to use and manage, with a user-friendly interface and straightforward policy deployment, making it simple to implement and maintain security measures.
- Advanced Features and Support: provides advanced features such as an intrusion prevention system for real-time protection against network-based attacks and an agent-based architecture for monitoring and protecting across different environments.
Cons
- Resource-Intensive and False Positives: can be resource-intensive, potentially affecting system performance, and may generate false positives that can lead to alert fatigue, making it challenging for security personnel to distinguish between real threats and false alarms, according to some users.
- High Cost: Trend Micro Deep Security can be expensive, especially for small and medium-sized organizations, requiring significant investment in hardware, and software licenses, as well as ongoing maintenance and support fees.
Pricing
Trend Micro offers a range of security products with varying prices, starting from around $40 per year for individual users, while enterprise solutions like Trend Micro Deep Security have higher costs.
Pricing is available via a customized quote on Trend Micro’s website. They offer a free trial.
12. WatchGuard EDR (Panda 360)
WatchGuard EDR is a security solution from WatchGuard Technologies that offers advanced threat detection, automated response actions, and continuous monitoring of endpoint activity to protect devices connected to a network from cyber threats.
But while WatchGuard is an excellent product for detection, Heimdal is more focused on preventing attacks through a wider security offering that covers DNS protection, patch management, ransomware encryption protection, privilege access management, and application control.
Main features
- Continuous Monitoring: constantly monitors endpoints to detect any suspicious activity or potential threats such as APTs, exploits, and file-less attacks.
- Zero-Trust Application Service: classifies all processes (pre-execution, running, and post-execution) using a Zero-Trust approach, ensuring maximum security.
- Automated Detection and Response: can automatically detect targeted attacks and in-memory exploits, respond to threats, and prevent unknown processes from executing, with added support from the Threat Hunting Service.
Pros
- User-Friendly Interface: intuitive software that makes it easy for users to navigate and access the features they need.
- Centralized Management Console: its central management console provides a clear view of the network’s security status, allowing users to quickly identify and address any security issues that arise.
- Effective Endpoint Protection: uses advanced machine learning algorithms that help prevent attacks and they offer good technical support.
Cons
- Slower Scanning Speed: some users reported that the platform’s scanning speed is slower compared to other products in the market, which can result in delays in detecting potential threats.
- Relatively Expensive: may be relatively expensive compared to other endpoint protection solutions, potentially limiting its appeal to small or budget-conscious organizations.
- Limited Reporting Capabilities: its reporting features are somewhat limited, and users may desire more detailed and customizable reports to gain better insights into their network’s security posture.
Pricing
WatchGuard EDR offers tiered pricing for a 1-year term, ranging from $53.50 per license for 1-50 licenses to $24.10 per license for 5001+ licenses, with discounts applied as the quantity increases. The pricing is tiered for a 3-year term as well. A free trial is available.
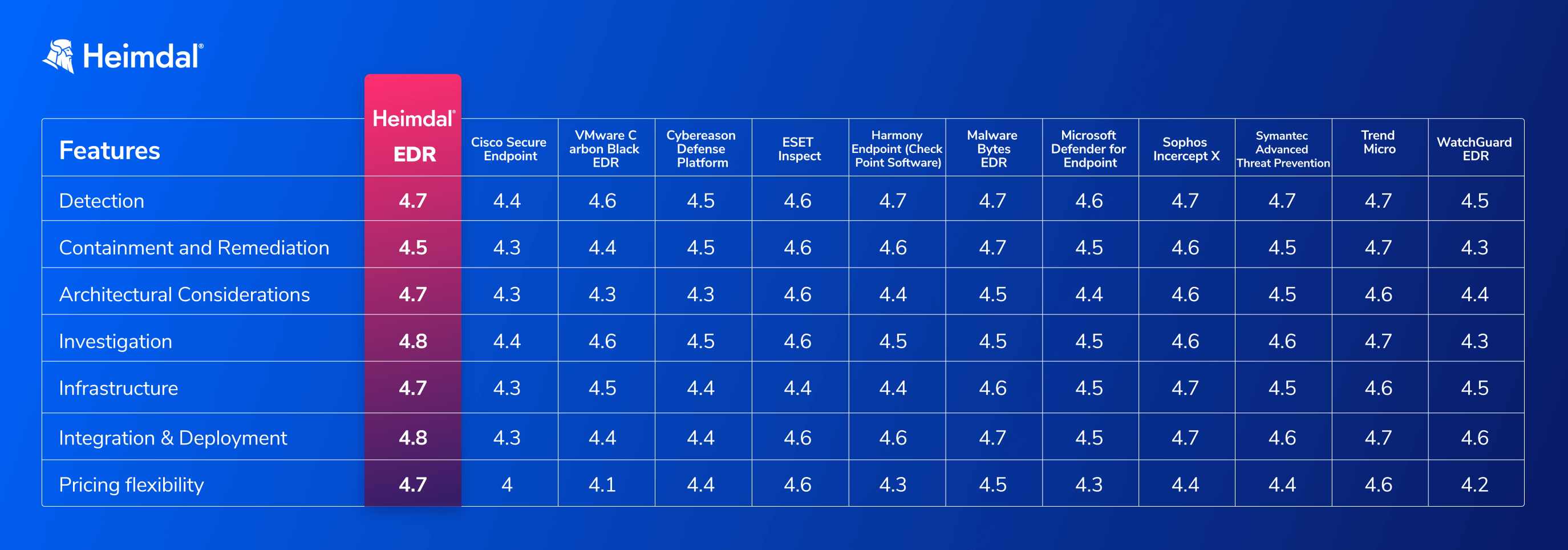
How to choose the right endpoint security platform for you
Here are a few factors that you should keep in mind when you choose the best endpoint security platform to fit your organization’s needs:
Detection
Evaluate the platform’s ability to detect a wide range of threats, including known and unknown malware, zero-day exploits, and advanced persistent threats. Check if it uses advanced technologies such as artificial intelligence, machine learning, or behavior analysis for more accurate and proactive threat detection.
Containment and Remediation
Assess the platform’s capabilities to isolate infected endpoints, prevent the spread of threats, and automatically or manually remove malicious software. It should also be able to roll back changes made by malware to restore the system to a clean state.
Architectural Considerations
Determine whether the platform’s architecture fits your organization’s needs. It could be cloud-based, on-premise, or hybrid. A cloud solution is scalable and easier to manage, while on-premise offers more control over data and infrastructure.
Investigation
Consider the platform’s forensic capabilities. It should provide logs, alerts, and reports to help your security team investigate incidents, understand attack vectors, and strengthen defenses.
Infrastructure
Ensure that the platform supports your existing infrastructure, including operating systems, devices (desktops, laptops, mobile devices), and network architecture. It should be compatible with your organization’s hardware and software requirements.
Integration & Deployment
Evaluate the ease of deployment and integration with your existing security stack, IT management tools, and network infrastructure. The platform should complement your current security solutions and be able to work seamlessly with other tools.
Pricing flexibility
Consider the platform’s pricing model, including any licensing, subscription, or additional fees. Make sure the cost aligns with your budget and offers flexibility for future growth or changes in your organization’s needs.
The definitive list of endpoint security software features
Considering a purchase? Although each endpoint security solution has unique features, we recommend focusing on a platform with the following key capabilities:
Efficient Threat Tracking & Analysis – an endpoint security solution should offer complete visibility into endpoint activity, correlating data with actionable Threat Intelligence. It should include proactive Indicators of Compromise (IOCs) and enhanced Indicators of Attack (IOAs), allowing you to mitigate even concealed malware.
Advanced Attack Prevention – Endpoint security software should go beyond traditional solutions, using machine learning and AI to stay ahead of threats like ransomware, APTs, exploits, brute force attacks, and more. The more automated an endpoint security solution is, the faster it will detect and respond to threats.
Unified Platform – an endpoint security solution should have a user-friendly interface, with all components managed from a single dashboard for better visibility and faster threat response.
Elevate Your Company’s Endpoint Security with Heimdal®
Choosing the right EDR is crucial to prevent data breaches, protect sensitive information, and reduce financial and reputational risks.
An effective endpoint security solution should detect and respond to advanced threats that bypass traditional security measures. Heimdal’s EDR offering goes beyond traditional, reactive security and delivers real-time, proactive security for your company’s endpoints.
Our platform integrates DNS filtering, proactive detection, patching, antivirus, ransomware protection, and admin rights management for continuous security.

- Next-gen Antivirus & Firewall which stops known threats;
- DNS traffic filter which stops unknown threats;
- Automatic patches for your software and apps with no interruptions;
- Privileged Access Management and Application Control, all in one unified dashboard
FAQs
What is endpoint security?
Endpoint security protects end-user devices like desktops, laptops, and mobiles from threats and unauthorized access. It is aimed at safeguarding these devices against cyberattacks and preventing data breaches.
What is considered an endpoint?
An endpoint is any remote device that communicates with a connected network. Examples of endpoints include desktop computers, laptops, smartphones, tablets, servers, routers, and Internet-of-Things (IoT) devices. Essentially, any device that can connect to a network and transmit or receive data is considered an endpoint.
What are endpoint security solutions?
Endpoint security solutions protect network endpoints like computers and mobile devices from cyberattacks. They quickly detect common threats like malware and also offer endpoint monitoring, detection, and response. This enables businesses to identify advanced threats such as file-less malware, polymorphic attacks, and zero-day exploits.
What are examples of endpoint security?
Endpoint security solutions include antivirus software, firewalls, EDR, data encryption, MDM, VPNs, and more.
What are the three main types of endpoint security?
The three main categories of endpoint security are EPP, EDR, and XDR.
What is the difference between EPP and EDR?
Endpoint Protection Platforms (EPP) are proactive, focusing on prevention by blocking known and unknown malware on endpoint devices.
In contrast, EDR solutions are reactive, detecting and responding to threats that have bypassed EPP defenses.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security











