Contents:
A quick search on the Internet retrieved a pack of VMware Carbon Black alternatives for endpoint protection services.
Analyzing key features, pros, cons, and pricing is what led me to my conclusions. So, here’s a list of the 9 Best Carbon Black Alternatives on the cybersecurity market.
Key takeaways
Heimdal® – Fully integrated, cross-platform suite offering proactive protection and unified endpoint management. Comprehensive and modular
Microsoft Defender for Endpoint – Native Windows tool with real-time protection and streamlined integration for Microsoft environments.
CrowdStrike Falcon – Cloud-native platform excelling in real-time threat intelligence and scalable endpoint visibility.
Trellix Endpoint Security – Modular and legacy-rich solution offering comprehensive protection with a complex setup.
SentinelOne Singularity Complete – AI-driven defense system with ransomware rollback and EDR.
Sophos Intercept X Endpoint – Dual-product solution known for its deep threat prevention and centralized control.
Trend Micro – Hybrid (cloud/on-prem) security platform combining behavioral analysis with advanced EDR.
ESET Protect – Lightweight, cross-platform antivirus solution offering simple management and scalable coverage.
Malwarebytes Endpoint Protection – Cloud-based platform with layered threat detection and low performance impact.
9 Best Carbon Black Alternatives for Endpoint Security
I chose each option in the Carbon Black alternatives list based on standout capabilities in endpoint protection, threat detection, and system performance. Whether you’re seeking stronger prevention, easier management, or broader coverage than Carbon Black, these tools are strong alternatives to match different business needs and budgets.
1. Heimdal®
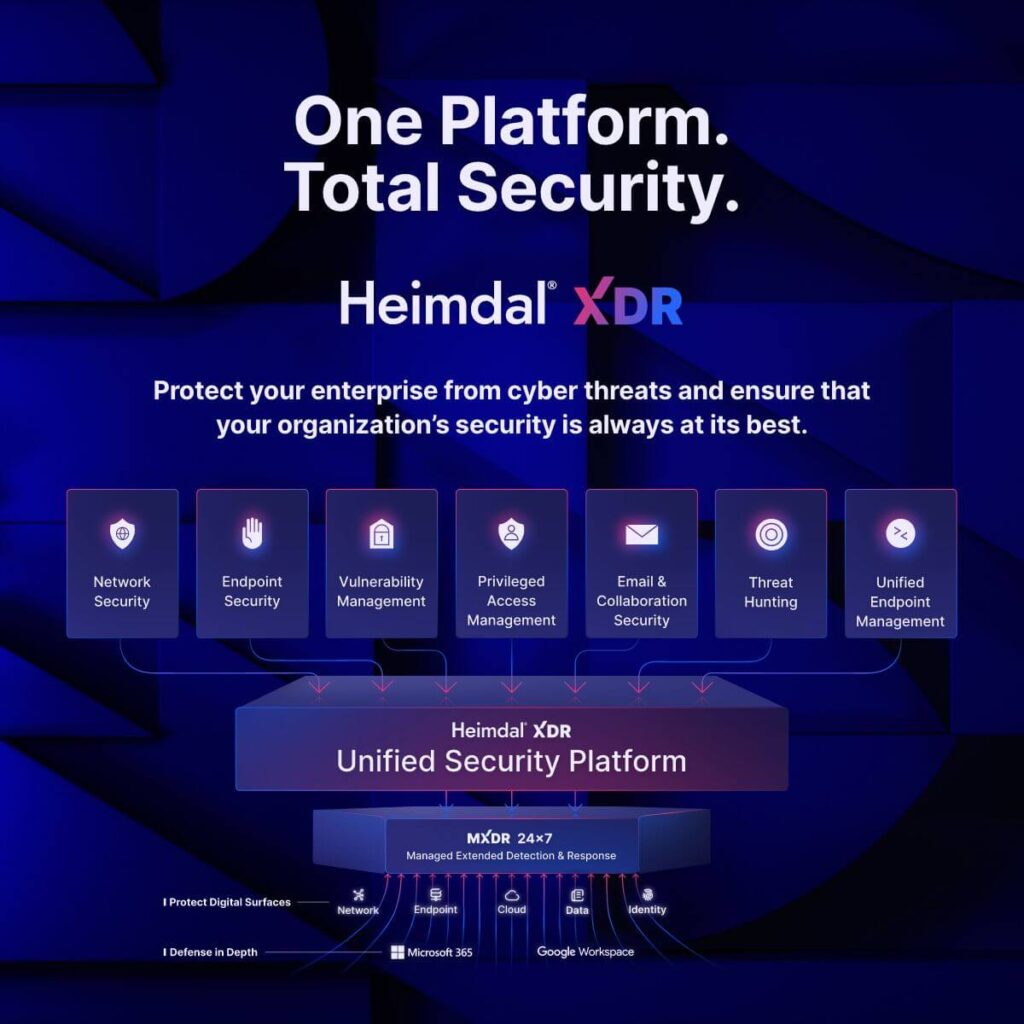
Heimdal® stands out as the number 1 endpoint security tool. It works as well on Linux and MacOS as it does on Windows.
Another feature that differentiates Heimdal® from other Carbon Black alternatives is its outstanding technical support service.
The extensive variety of integrated tools and services offers users unparalleled visibility across the whole system and ease of management.
What makes Heimdal the best alternative to Carbon Black?
Heimdal’s unified platform integrates tools and capabilities like DNS security, Patch Management, Next-Gen Antivirus, Threat Hunting, Privileged Access Management, and Email security.
As a Carbon Black alternative it covers the most endpoint protection areas.
The suite enables you to prevent, detect, and respond swiftly to a variety of cyber threats. Using it keeps your data and system safe from phishing attempts, ransomware attacks, malware deployment, and DNS hijacking.
VMware Carbon Black Cloud offers a Next-Gen AV, endpoint detection and response (EDR), threat hunting, and vulnerability management. It works well if you need to detect and respond to an attack that has already happened.
However, you will still need additional tools to cover other critical security layers. One example is DNS layer security. Heimdal’s DNS Security Network & Endpoint and Patch and Assets Management could very well work along VMware Carbon Black.
You can easily have the two solutions working together, due to Heimdal’s easy to integrate, modular approach. In this scenario, Heimdal would cover the prevention part, by fast, flawless patching and 96% accuracy in detecting and blocking malicious communication.
Meanwhile, VMware Carbon Black can take care of forensics and the remediation process.
Nevertheless, using a unified and integrated suite that covers all is a more effective and convenient choice.
What do our customers say?
The product was named as one of the top alternatives for the Carbon Black Endpoint protection software.
Having the full suite of security layers within a single package but the OS and 3rd Party Patching is second to none!
Easy to use, Easy to install great reporting module, perfect support channel.
Heimdal is light weight. Very little impact on system resources.
The other thing though is it’s “quiet” … it works in the background helping to shield from threats without interfering with your work with dialog boxes.
The other things that’s particularly nice is that it keeps other applications up to date with the latest patches and builds, thus removing what otherwise could be entry points for system exploits.
Key Features
- Total visibility and unified control over all endpoints.
- DNS filtering engine trained on a deep learning neural network.
- AI-powered, machine-learning-based DNS, HTTP and HTTPS traffic filtering.
- Proved 96% accuracy in predicting unknown threats.
- Ability to detect malicious processes, and to backtrack the attacker’s origins.
- Integrated DNS-over-HTTPS traffic filtering.
- Outstanding malware hunting capabilities, including detecting fileless attacks.
- Fast and effective support response.
Pros
- Increased Network Visibility. Provides continuous monitoring for real-time threat detection and response, detecting malicious traffic and investigating attack sources.
- Improved Compliance. EDR helps organizations adhere to data storage and access regulations like HIPAA, NIS2, or GDPR by keeping track of suspicious activity and investigating potential threats.
- Reduced Risk. Endpoint Detection and Response services reduce a company’s risk by constantly monitoring the network and endpoints, enabling prompt detection and response to threats in real-time.
- Cost Efficiency. Helps companies save money by providing real-time monitoring and quick response to security threats, which cuts down on the costs related to managing security incidents.
- Stronger Security Posture. Can enhance your defense against cyber threats by reducing false positives while still identifying real threats swiftly.
Cons
- Hardware. Heimdal® currently lacks some functionality to manage hardware insights and alerts.
Pricing
We offer various pricing tiers based on the number of seats required. The ranges go from as low as one to over 20,000, as well as for servers, going from one to over 100.
The licensing costs vary depending on the chosen subscription period, with options for monthly, yearly, 3-year, and 5-year pricing. Use this calculator to get an instant price estimation for what you need.
2. Microsoft Defender for Endpoint
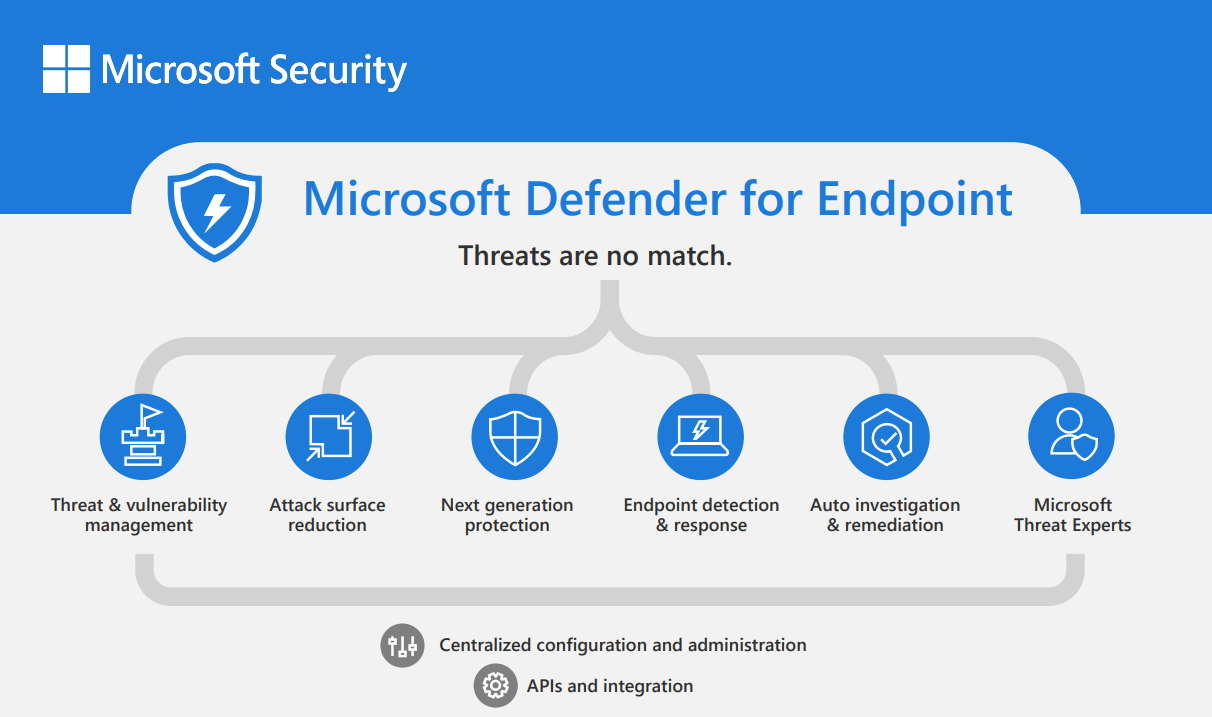
Microsoft Defender for Endpoint offers real-time protection against ransomware and other malware, viruses, and phishing attacks.
It offers a management console, so deployment, configuring, and monitoring go pretty easy for Windows.
Key Features
- Machine-learning capabilities.
- Endpoint detection and response (EDR).
- Antimalware protection.
- Centralized reporting.
- Attack surface reduction.
Pros
- AI-based threat definitions.
- End-to-End encryption.
- User-friendly UI.
Cons
- False positives.
- Management console doesn’t offer remediation options.
Pricing
The price depends on configuration and licensing program. For more information, please contact the vendor.
Testimonials
Microsoft Defender for Endpoint Pros
+ This is a solution perfectly compatible with the Windows operating system. This makes them easy to configure and manage for people familiar with Microsoft tools.
From the device side, it ensures safety and risk that even an unintentional threat will be quickly detected, removed and properly communicated to the team responsible for security as well as to the end user.
Microsoft Defender for Endpoint Cons
– Some users express concerns about occasional false positives in threat detection, which can lead to disruptions.
While Microsoft Defender for Endpoint has improved in this aspect, it’s an area where user experience could be further refined.
Additionally, the system’s resource consumption during scans may impact device performance, causing slowdowns in certain scenarios.
3. CrowdStrike Falcon
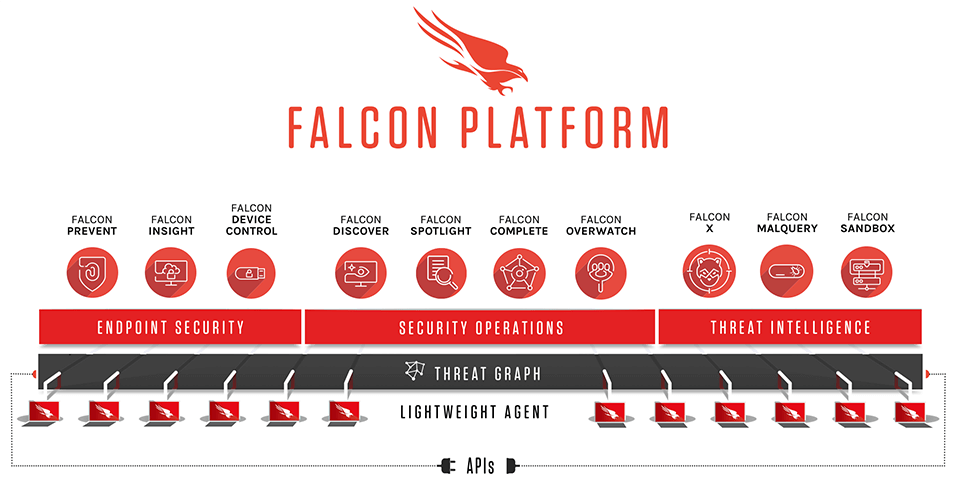
Users marked CrowdStrike‘s cloud-delivered endpoint protection as a powerful tool.
Yet, it misses certain capabilities that are becoming a standard in the cybersecurity industry.
Like vulnerability management, for example. Additionally, the USB control feature is tricky to use.
Key Features
- Endpoint Security & XDR.
- Identity protection.
- Threat intelligence and threat hunting.
- Machine-learning capabilities.
- Malware detection.
- Behavioral analysis.
Pros
- Advanced threat detection with machine learning.
- Scalable cloud-native architecture.
- Granular endpoint control and visibility.
- Integration with diverse threat intelligence.
Cons
- Premium pricing.
- Reliance on internet connectivity.
- Complex deployment.
- Privacy concerns.
Pricing
- Falcon Go: $299.95/year.
- Falcon Pro: $499.95/year.
- Falcon Enterprise: $924.95/year.
Testimonials
CrowdStrike Falcon Pros
+ CrowdStrike Falcon for Endpoint is a potent cybersecurity tool that improves endpoint security for businesses by providing real-time visibility and reaction, advanced threat information, a lightweight agent, preventative security measures, and professional managed threat hunting services.
CrowdStrike Falcon Cons
CrowdStrike Falcon Endpoint Protection GUI may look easy on the eye but there is alot going on under its “hud” that I would say isn’t user friendly, you need to get the hang of using CrowdStrike Falcon Endpoint Protection to know how to navigate through it and set things well in their place.
4. Trellix Endpoint Security (ENS)
Trellix Endpoint Security is another one of the VMware Carbon Black alternatives.
It is designed to safeguard servers, desktops, laptops, and tablets.
Their modules can integrate into a single Trellix ENS interface.
Key Features
- Threat Prevention
- Firewall
- Web Control
- Adaptive Threat Protection
- Data Loss Prevention solution
Pros
- Behavior-based threat detection.
- Centralized management for easy deployment.
- Integrated threat intelligence.
- Low system impact.
Cons
- Limited scalability.
- Complex configuration.
- Resource-intensive.
- Dependency on updates.
Pricing
Trellix features several pricing tiers.
- Trellix Advanced (SaaS-MVA): $118.44/user/year.
- Trellix Premium (SaaS-MVP): $222.32/user/year.
- Trellix Complete (SaaS-MVC): $366.08/user/year.
- Trellix Endpoint Security (TRXE1): $136.16/user/year.
- Trellix Protect Plus EDR (MV6): $104.65/user/year.
- Trellix Protect Plus and EDR Premium (MV7): $176.767/user/year.
- Trellix EDR (MV4): $54.54/user/year.
- Trellix EDR Premium (MV5): $145.978/user/year.
- Trellix Protect Standard: $43.98/user/year.
- Trellix Protect Plus (MV2): $87.13/user/year.
- Trellix Mobile Security Advanced (MV3): $101.6/user/year.
- Trellix Insights (MVI): $35.45/user/year.
Testimonials
Trellix Endpoint Security (ENS) Pros
+ Trellix is a product with long history inherited from Mcaffee.
You can see this when using the software as it has all security components and functions you could imagine, and it provides complexed endpoint security.
The modules are very well integrated with each other which works very good in case some threats are present in the environment.
Trellix Endpoint Security (ENS) Cons
– It is a little challenging to figure out how to use Trellix Endpoint Security at first if you lack the experience.
However, you will find a lot of information that will help you get started.
Expanding the resources to include Arabic on the main website would support more users.
5. Singularity Complete by SentinelOne
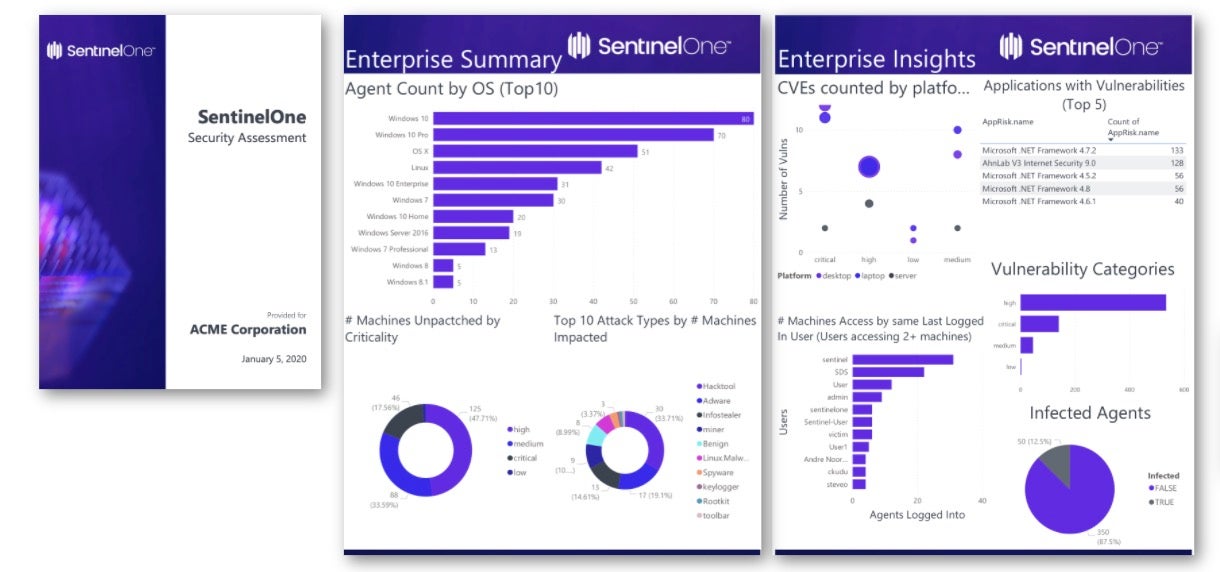
When it comes to comparing SentinelOne’s Singularity XDR with VMware Carbon Black, the ability to reverse ransomware file encryption is an attractive feature.
Key Features
- Automated threat remediation.
- Extensive event data analysis.
- Real-time detection.
- Threat intelligence.
- Behavioral Analysis.
Pros
- AI-powered threat prevention.
- Autonomous response capability.
- Single agent architecture for easy management.
- Comprehensive endpoint visibility.
Cons
- Costly licensing.
- Resource-intensive operations.
- Complex customization.
- Dependence on timely updates.
Pricing
A Singularity Complete license costs $45.00 per year.
Testimonials
Singularity Complete Pros
+ EDR that constantly updates without intervention.
Scans attached drives, and computers when files are downloaded with automatically.
Onboarding walks you step by step to get setup and using the portal quickly and efficiently.
Support is always available.
Threats are stopped automatically and restored back to normal if set to protection mode vs just detection mode.
Singularity Complete Cons
One thing that I dislike about SentinelOne is that there is no way to further categorize a report once it has been ran.
The end result, depending on the frequency can be slightly overwhelming as you a sifting through the large list of reports.
This is something that can be improved overtime and has a great amount of potential.
6. Sophos Intercept X Endpoint
The Sophos solution brings two products under the same umbrella. Among other endpoint security solutions, they are known for offering good threat management capabilities.
Sophos Intercept X Endpoint is highly appreciated for its web filtering and URL check features.
Key Features
- Advanced anti-malware.
- Website browsing protection and filtering.
- Data loss prevention (DLP).
- Client firewall.
- Application and device control.
- Host-based intrusion prevention system (IPS).
Pros
- Effective Threat Prevention. Intercept X stops malware and ransomware effectively.
- Centralized Management. Sophos Central simplifies management across all endpoints.
- Endpoint Detection and Response. Includes capabilities for quick incident response.
- Integration. Seamlessly integrates with other Sophos security products.
Cons
- Resource Intensive. Can slow down older devices.
- Learning Curve. Might require time to master.
- Cost. Licensing costs may be high for smaller businesses.
- False Positives. Occasionally flags harmless activities as cyber threats
Pricing
- You can choose between an annual and a three-year license.
- The starting price is $28/year/user.
- Free trial available.
Testimonials
Sophos Intercept X Endpoint Pros
+ I’d like to highlight a few major features here:
Our day-to-day lives have been made easier by capabilities like Live Response and Live Discover under the endpoint detection response capability.
The recently launched third-party integration on top has proven to be a lifesaver.
Our team can now work on any malicious detections and log them to notebooks using the investigation/cases capability.
The ability to block SHA values using the blocked items functionality has greatly aided us in addressing the shadow issue.
Sophos Intercept X Endpoint Cons
– One thing its extensive feature set and configuration options in intercept X may be overwhelming for users who are not familiar with endpoint security solutions.
It may require a learning curve for administrators to effectively configure and manage the product.
7. Trend Micro
Trend Micro’s endpoint security solution works both cloud-based and on-premises and covers multiple operating systems.
It offers integrated threat detection and response as well as a patch management tool.
Key Features
- Antivirus and malware application control.
- Endpoint Detection and Response.
- Data encryption.
- Data loss prevention.
- URL filtering.
- Response time and detection module.
Pros
- Effective Protection. Guards against malware, ransomware, and phishing.
- Centralized Management. Simplifies control and monitoring.
- Advanced Detection. Uses behavioral analysis to spot new threats.
- EDR Capability. Enables proactive threat investigation and response.
Cons
- Resource Usage. Might slow down devices due to its comprehensive features.
- Learning Curve. Takes time to get used to, especially for beginners.
- Costly. Licensing can be expensive, particularly for small businesses.
- False Alarms. Could generate unnecessary alerts at times.
Pricing
- Comes at a starting cost of $37.75/user/year.
- Free Trial available.
Testimonials
Trend Micro Apex One Pros
+ The customizable and insightful reports assist me in pinpointing areas that require attention. It provide features like cloud application security, which sets it apart from products.
Trend Micro Apex One Cons
– They need to extend reporting functionalities with the same apex dashboard itself.
Instead, they are providing via apex central; false positives: Some users have reported that Apex One can sometimes produce false positives, which may lead to legitimate applications or files being flagged as threats.
8. ESET PROTECT
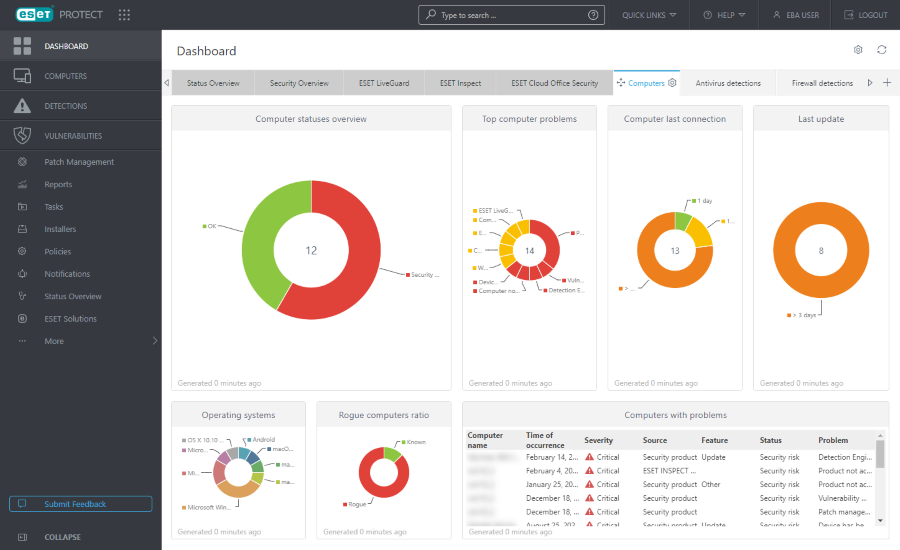
ESET PROTECT enables organizations to gain full visibility across all assets.
It works on Windows, MacOS, and Linux, as well as on Android and iOS operating systems. The solutions has low impact on resource consumption and threat detection capabilities.
Key Features
- Incident reports
- Asset management.
- Firewall.
- Malware detection.
- Web control.
Pros
- Effective Security. Protects against malware and phishing effectively.
- Simple Management. Easy centralized control and monitoring.
- Lightweight. Doesn’t slow down devices.
- Scalable. Fits businesses of all sizes.
Cons
- Fewer Features. Might lack some advanced options.
- Complex Interface. Management console can be tricky for new users.
- Support Varies. Quality of support may differ.
- Integration Challenges. May not integrate seamlessly with third-party solutions.
Pricing
- Cost ranges from $39.99 to $59.99/device/year.
- 30-day free trial available.
Testimonials
ESET PROTECT Pros
+ It is a digital security application that is focused on locating and removing malware being one of the tools that has more than 20 years in the market being a leader and very important for files, mobile devices as it is responsible for encrypting the firewall system and control the web of the same, has a very good overall approval for the removal of viruses and its technical support is highly qualified and is self-dependent.
ESET PROTECT Cons
– Problems with the Linux version especially with the installer, the mobile application is not one of the best I have detected errors, it stops working suddenly, the application gets stuck, it is a really expensive software, there are other much cheaper options, but this does not mean that it does not do its job well.
9. Malwarebytes Endpoint Protection
Malwarebytes Endpoint Protection is a cloud-based solution that uses various techniques to detect and respond to attacks.
It covers all stages of the attack chain by using a mix of signature-less and matching-technology layers.
Key Features
- Advanced threat prevention.
- Detects unprotected systems.
- Centralized cloud management console.
- AI-powered next-generation antivirus software.
- Automated security reports.
Pros
- Effective Malware Detection. Identifies a wide range of malware threats, including ransomware and viruses.
- Centralized Management. Simplifies deployment, configuration, and monitoring across all endpoints.
- Low System Impact. Runs quietly in the background without significant performance impact.
- Regular Updates and Support. Receives timely updates and offers comprehensive customer support.
Cons
- Limited Platform Support. May not fully support all operating systems, especially legacy ones.
- Cost Considerations. Pricing structure may be expensive, particularly for larger deployments.
- Complexity for Novice Users. Advanced features may be challenging for users with limited cybersecurity expertise.
- Potential False Positives. Occasionally flags legitimate files or applications as malicious, causing user frustration.
Pricing
- Reduced cost per year for 10 to 99 devices starts from $594.99,
- The pricing model offers custom fees for more than 100 devices or servers,
- Free trial available.
Testimonials
Malwarebytes Endpoint Protection Pros
+ ThreatDown has allowed us as a small team to manage hundreds of endpoints effectively.
Agent installation is straightforward while management through the ThreatDown Nebula platform is incredibly responsive and easy to use.
We have rarely had to deal with false positives and ThreatDown’s unique “PUP” removal is a unique and helpful feature compared to its competitors.
On top of all that, a chat option for support is now available for the few and far between times it’s needed!
Malwarebytes Endpoint Protection Cons
– There are times when we noticed the tool will install a new version without removing the old version.
This causes conflict on the Windows based machines and causes it to slow down.
At the time that happens, you have to go in and remove the older version and the system will return to normal.
Frequently Asked Questions (FAQ)
What is a better alternative to Carbon Black Endpoint?
Among other Carbon Black alternatives, Heimdal® stands as one of the best due to its both comprehensive and modular approach. It offers an extensive range of tools integrated into a unified, easy-to-use platform and gives you the freedom to only pay for those you want and use.
Heimdal’s technical support is also reportedly the best.
How do I choose the best endpoint security solution?
It depends on your organization’s specific needs: number of employees, location, work environment, industry, and device ownership.
However, top endpoint protection solutions offer extensive, integrated protection across multiple layers.
Using a unique platform that encompasses Next-gen AV, firewall, encryption, device and asset management, DNS filtering, and EDR is the best choice.
Benefits like complete visibility across the whole system and ease of management save time, energy, and money.
What does endpoint security software do?
Endpoint security software is an important line of any data protection strategy. It secures any kind of device, from laptops to mobiles, printers, and servers from various cyber threats.
It blocks, detects suspicious activity, and mitigates malware, trojans, ransomware, and zero-days.
Best software comes with a disaster recovery capability, mass malware protection, mobile devices management, automation of repetitive security operations.
The increased detection rate of unknown threats is also a strong differentiator that security teams appreciate.
What is the difference between EDR and XDR?
Endpoint Detection and Response is a unified set of tools that integrates data collecting and analysis, forensics, and threat hunting.
EDR is software that identifies and responds to malware and other cyberattacks at an endpoint level.
It prevents data breaches and data exfiltration from happening, enforces secure access policies, and defends against virus attacks.
Extended Detection and Response (XDR) is a multi-layered detection and response platform.
XDR does not only collect and analyze data from endpoints, but also from emails, servers, cloud, and network. It also aims to achieve flawless endpoint protection.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube, for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security