Contents:
Tenable alternatives offer solutions for those facing challenges with implementation and support. Their products are renowned for their capabilities in threat detection and vulnerability management.
Still, many users share a common frustration – implementation mishaps and unresponsive support, leaving critical vulnerabilities unaddressed.
In this article, we’ll look into the depths of Tenable’s top 10 alternatives and explore strategies to tackle these challenges.
10 Best Tenable Alternatives & Competitors
Here’s a list of the very best Tenable alternatives. Enjoy!
1. Heimdal®
Tenable has long been a familiar name in the field of cyber, offering a suite of tools known for their effectiveness in threat detection and vulnerability management.
However, there’s a strong alternative to Tenable and that is Heimdal®.
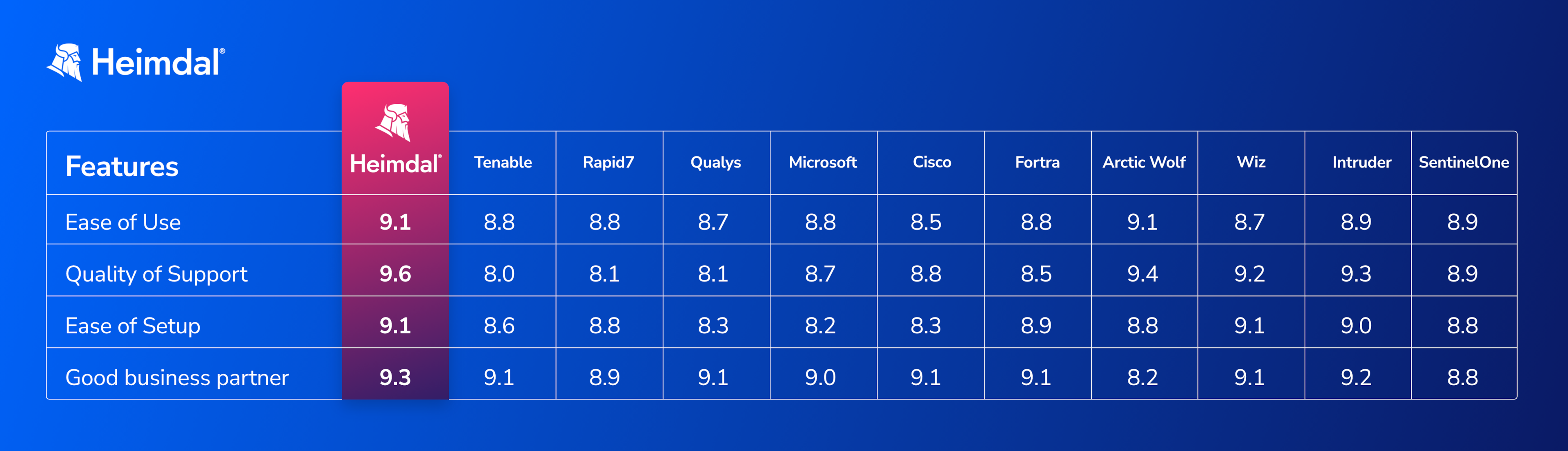
What Makes Heimdal the Best Alternative to Tenable?
It’s essential to remember that the “best” alternative depends on the specific needs and requirements of an organization. This includes:
- Advanced Threat Prevention. While Tenable excels at vulnerability management, Heimdal® can provide advanced threat prevention capabilities by actively blocking threats before they can breach your defenses.
- Intelligent Automation. Heimdal® leverages AI and machine learning to automate security processes, reducing your workload and enhancing your protection.
- User-Friendly Interface. Heimdal®’s unified intuitive interface ensures that you can easily navigate and manage your security, without the need for a dedicated IT team.
- Rapid Response Support. Heimdal®’s customer-centric approach means you’ll have a dedicated support team ready to assist you when you need it most.
What Do Our Customers Say?
We believe we’re the best alternative to Tenable, but don’t just take our word for it.
Support is second to none – very responsive and helpful. Peace of mind is absolute and the admin overview and ability to remediate remotely is fantastic. It is also built for the work-at-home culture when have settled into after covid.
Brian W, Owner, Computer & Network Security
Great Co, Great Product and excellent customer service – Heimdal Security stands proud for showing the industry how it should be done!
Mark F, Director, Computer & Network Security
The install was incredibly straightforward, and we’ve barely had to touch it since. We use it for ourselves and recommend it to all of our customers.
Warren L, General Manager, Information Technology and Services
Heimdal® Key Features
Here are the core features that solidify our position as the best alternative to Tenable.
- Threat Prevention. Heimdal’s threat prevention solutions keep you ahead of the curve, blocking malware, ransomware, and advanced threats in real time.
- Patch Management. We automate patch management to ensure your software is always up-to-date, closing vulnerabilities before they can be exploited.
- DarkLayer Guard. Our unique DNS filtering technology provides an additional layer of security, safeguarding you from malicious web traffic.
- MDM Integration. Heimdal seamlessly integrates with your existing Mobile Device Management (MDM) solutions, ensuring a cohesive security strategy.
Heimdal Pricing
Our flexible pricing models cater to businesses of all sizes. Whether you’re a small startup or a large enterprise, Heimdal offers cost-effective solutions to suit your budget.
- We have several different price ranges for seat counts (from 1 up to 20.000+) and servers (from 1 up to 100+).
- The licensing cost varies depending on the subscription period (monthly pricing/ yearly pricing/ 3-year pricing/5-year pricing).
Our unified platform integrates cutting-edge threat intelligence, automated response actions, and advanced behavioral analysis. By staying one step ahead, your organization will outsmart cybercriminals and remain resilient to attacks.
– Nabil Nistar, Head of Product Marketing
2. Rapid7
Rapid7 InsightVM is a powerful vulnerability management tool designed to help organizations of all sizes proactively secure their digital assets.
It offers customizable dashboards and reporting, making it easy to track your security program’s progress and communicate insights across your organization.
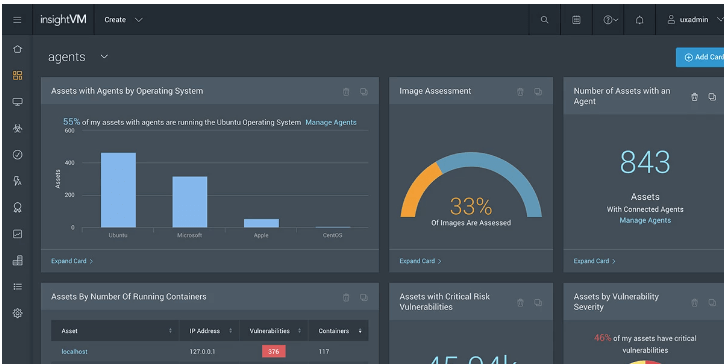
Key Features
- Autonomously gather information from every endpoint, including those belonging to remote employees and sensitive assets that aren’t open to active scanning or rarely connect to the corporate network.
- Create custom cards and full dashboards from system admins to CISOs.
- Assess vulnerabilities through Active Risk feature.
Pricing
Rapid7 InsightVM has 5 pricing editions, from $26.25 (for 250 assets, per asset) to $19.43 (for 1250 assets, per asset) billed annually.
Testimonials
Pros
+ InsightVM efficiently manages our cloud workloads through its robust agent installation.
We can overview and scan all our images at various stages in deployment. We can also identify potential risks and prioritize handling vulnerabilities in our infrastructure.
Since it is an agent-based platform, we can conveniently focus on our enhancements and let InsightVM take care of the underlying dependencies.
Cons
– Memory consumption sometimes is at its peak. Apart from that, compared to other VM tools it has enough features with other tool even don’t have as a whole solution.
3. Qualys
Qualys is a leading cybersecurity company providing a comprehensive cloud-based security and compliance platform. A more detailed comparison with Tenable is available on our blog, as well as a Qualys alternatives article.
Key Features
- VMDR features risk-based vulnerability management and user-friendly, no-code workflows.
- Identify every asset in the environment, even unmanaged.
- VMDR identifies the most up-to-date patch for a vulnerable asset and facilitates deployment.
Pricing
The pricing varies based on your choice of Cloud Platform Apps, the number of network addresses (IPs), web applications, and the number of user licenses you select.
Testimonials
Pros
+ The best aspect of Qualys VMDR is its user-friendly interface that allows for easy and intuitive vulnerability scanning.
The platform empowers us to select and customize the specific types of scans we need, providing a tailored approach to address our unique security requirements.
This flexibility and simplicity have significantly improved our overall scanning efficiency and helped us stay on top of potential vulnerabilities, ensuring a robust security posture for our organization.
Cons
– False positives and false negatives can be a concern with Qualys VMDR.
The platform’s complex nature may pose challenges for organizations with limited resources or less mature security programs, as it demands a heightened level of asset exposure.
It is important to consider these factors when evaluating Qualys VMDR’s suitability for specific enterprise environments.
4. Microsoft Defender Vulnerability Management
Microsoft Defender Vulnerability Management safeguards your systems, helping you stay one step ahead of emerging threats.
With actionable recommendations, it simplifies the process of patching and managing vulnerabilities across your network.
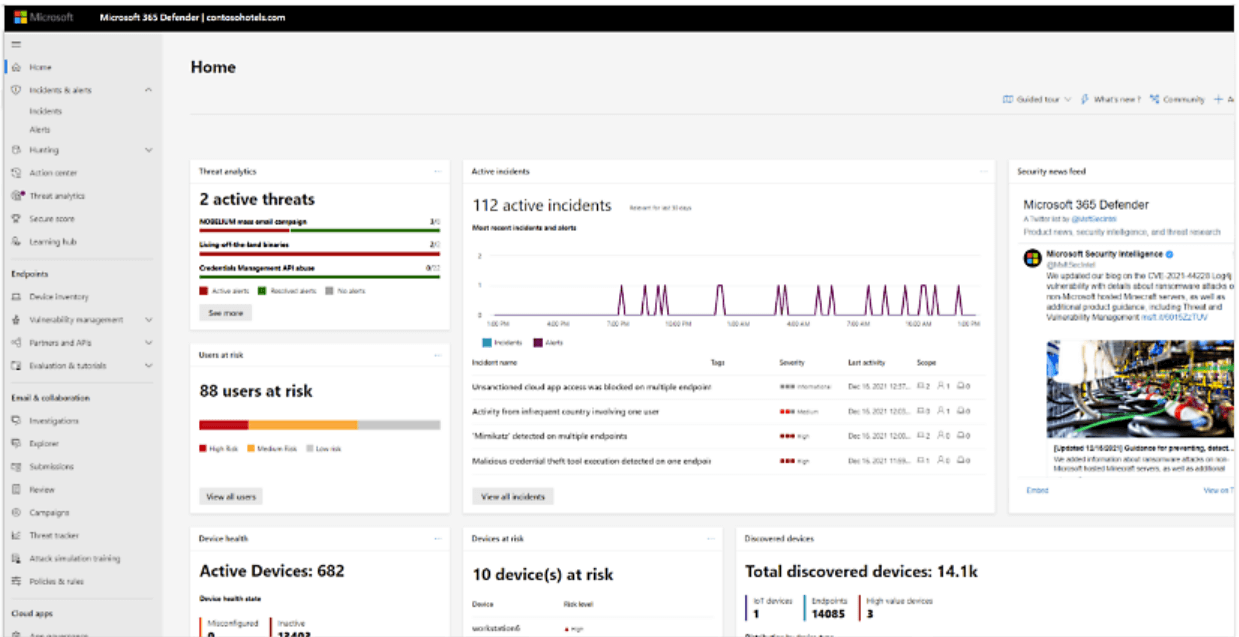
Microsoft Defender Vulnerability Management Key Features
- Uncover potential risks on managed and unmanaged devices with integrated components and scanners that don’t require agents, even when devices aren’t linked to the corporate network.
- Gain access to detailed lists of entity level devices, software apps, digital certificates, browser add-ons, and firmware evaluations.
- Focus on the most critical threats by accessing a unified display of top-priority recommendations from various security sources.
Pricing
In the pipeline is the release of a standalone version of Microsoft Defender Vulnerability Management, anticipated to have a pricing of $3 per user per month.
Testimonials
Microsoft Defender Vulnerability Management Pros
+ There are many solutions on the market for this purpose, but only few of them are non-demanding for CPU/Memory like Microsoft Defender Vulnerability Management.
You really cannot notice it’s working, no affection at all on system speed, but it gets the job done perfectly.
Customization is also great, and can be configured just for your needs very quickly.
Microsoft Defender Vulnerability Management Cons
– As it is primarily designed for Windows-based systems, there could be limitations for organizations with diverse IT environments.
The vulnerability management workflow automation does not support all operating systems, and EDR does not support all types of Linux and Unix systems.
Even on Windows-based systems, detections are not always accurate.
5. Cisco Vulnerability Management
This solution provides a comprehensive view of your organization’s security posture, enabling better decision-making and risk management.
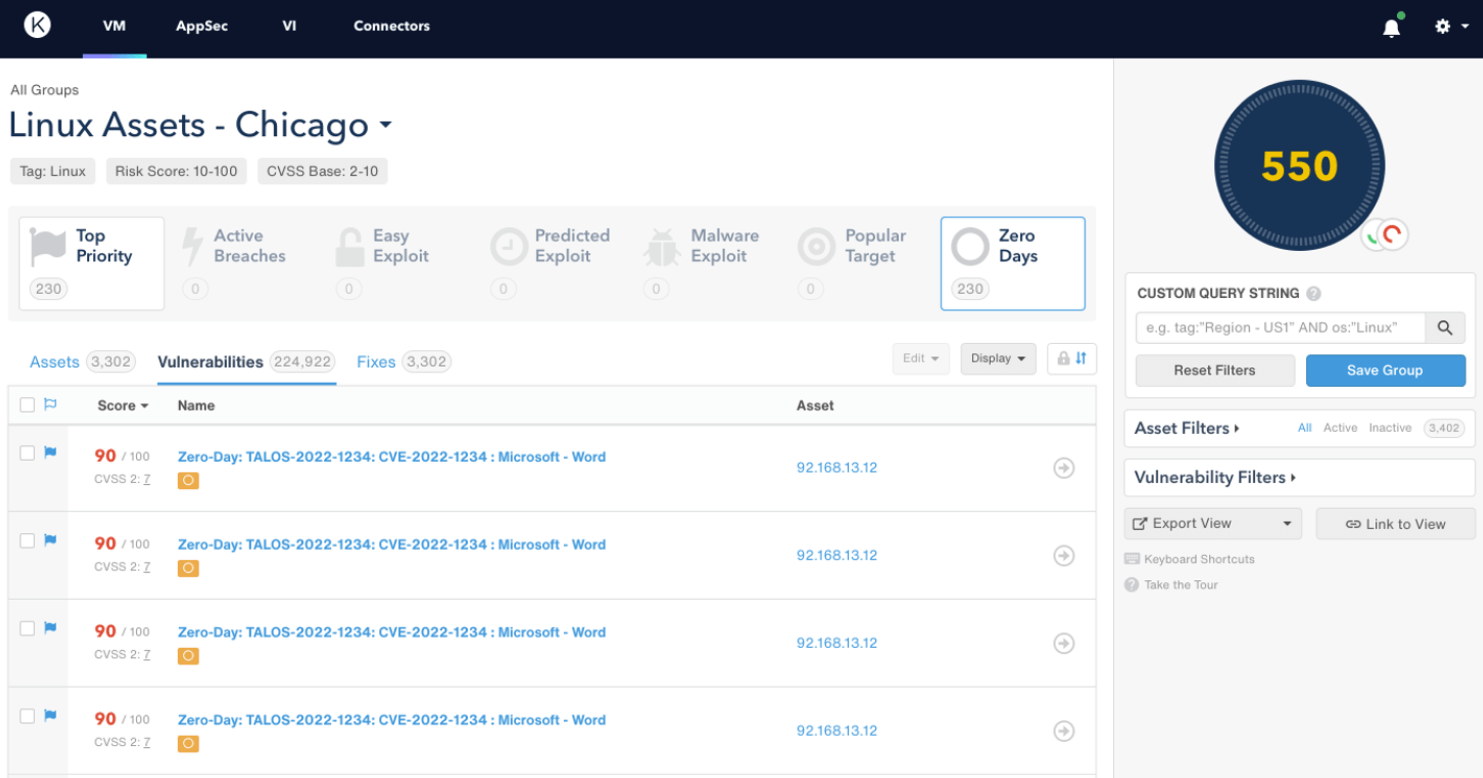
Cisco Vulnerability Management Key Features
- Understand risk more intuitively by using straightforward risk scores to measure vulnerabilities, assets, and asset groups.
- Utilize Top Fixes to swiftly pinpoint the vulnerabilities that genuinely lower your cybersecurity risk.
- Establish service-level agreements (SLAs) driven by data, considering your risk tolerance, asset importance, and the vulnerabilities you aim to resolve.
Pricing
Cisco does not disclose pricing details for this product, however, they offer two packages: Cisco Vulnerability Management Advantage and Cisco Vulnerability Management Premier.
Testimonials
Cisco Vulnerability Management Pros
+ A clutter free minimal dashboard which shows a brief information on your assets, vulnerabilities and also possible fixes for vulnerabilities.
Moreover, the dashboard shows quick visible links to filter based on easily exploitable vulnerabilities, popular malwares etc.
Such filters are easy to use for a novice user as well as a person with limited tech knowledge.
To add, there are custom query filters to search assets based on tags as well as check boxes to filter the vulnerabilities based on status for e.g. open, closed, ports, classification etc.
Cisco Vulnerability Management Cons
I’ve noticed that when I am viewing a group and click the Fixes tab, if I click on the number of assets affected by a vulnerability, I am unable to then hit the back button to return to the group view. This is frustrating.
6. Fortra
Fortra’s Frontline Vulnerability Manager (Frontline VM™) empowers organizations with robust vulnerability management solutions, helping them proactively protect their digital assets.
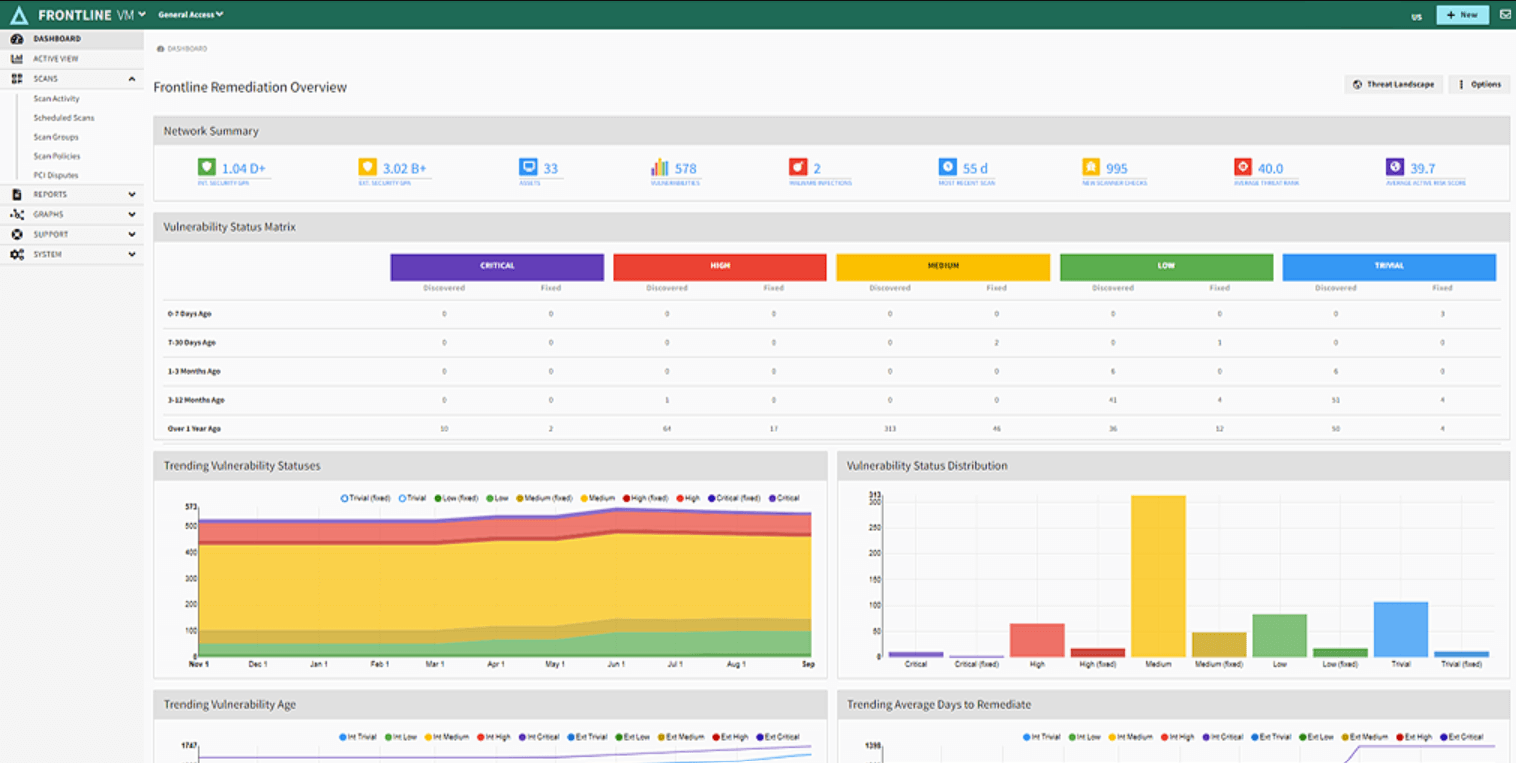
Frontline VM™ Key Features
- Vulnerability assessment accurately detects both internal and external vulnerabilities.
- Effortlessly categorize your assets, making them easily searchable. In addition, dynamic labeling allows you to create on-the-fly groups using various criteria.
- Create customized vulnerability and patch management reports for specific assets, using powerful filters for your audience or compliance requirements.
Pricing
Fortra’s Frontline VM™ prices start at $180/ month for assets up to 35 to $326,052/ month for assets up to 1,000,000.
Testimonials
Frontline VM™ Pros
+ I like how the dashboard and active view consolidates and prioritizes the findings. This and the notes features keep our team on the same page while remediating vulnerabilities.
Frontline VM™ Cons
– Exceptions and remediation are difficult to record and not very effective even when you do.
Albert T., Senior Security Analyst
7. Arctic Wolf
Arctic Wolf’s cloud-native approach and dedicated security experts deliver comprehensive protection, making them a trusted partner for businesses seeking robust cybersecurity solutions.
With a focus on simplicity and effectiveness, Arctic Wolf empowers organizations to minimize risk and respond swiftly to security incidents.
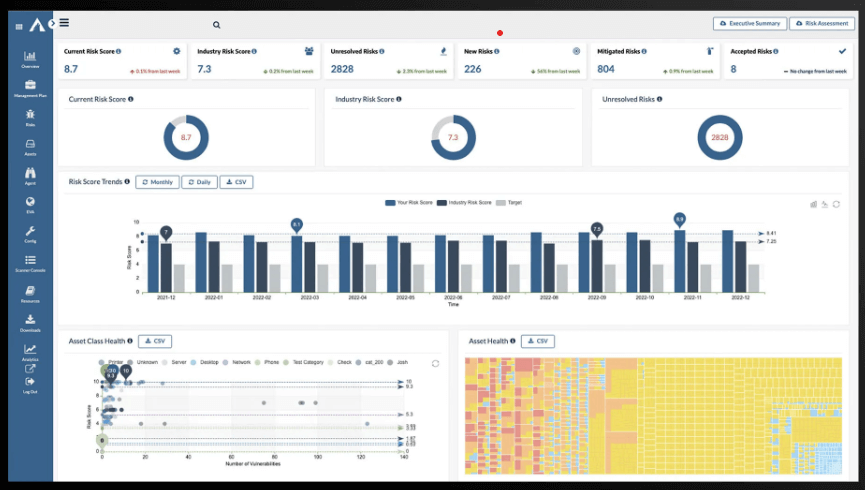
Arctic Wolf Key Features
- Round-the-clock monitoring of your network and endpoints, using advanced threat detection technology to identify and respond to security threats in real time.
- Offers a centralized hub for managing and monitoring security events, providing organizations with a comprehensive view of their cybersecurity posture and enabling streamlined incident response.
Pricing
They offer 3 plans starting at 2,99 per user per month up to 4,99 per user per month.
Pricing includes components for 30-100 users and is billed annually at the time of purchase.
Testimonials
Arctic Wolf Pros
+ The Arctic Wolf product and team are the all-in-one solution to keep your business on the cutting edge.
Their attention to detail and coverage rival top-tier vendors in their fields.
From the begining of our relationship they have been forthcoming, easy to use, the integration was painless and the number of features available is outstanding.
We use it daily and we don’t receive extraneous notifications to clutter up our day.
Their customer support is quick, concise and to the point with no fluff.
Arctic Wolf Cons
– The MR portal needs a major revamp and same with the ticketing systems. From what we can tell, it is being worked on and it’s just a matter of time.
8. Wiz
Wiz offers comprehensive visibility into cloud-related security risks, delivering s a holistic perspective on security vulnerabilities spanning clouds, containers, and workloads.
Key Features
- Prioritizes vulnerabilities based on risk, allowing you to focus resources on addressing the most critical security issues first.
- Provides automated and continuous monitoring of cloud environments to identify misconfigurations and compliance violations.
- Comprehensive visibility into cloud assets and their relationships.
Pricing
Although WIZ.io provides a wide range of security services, it might be relatively expensive for small businesses and startups. They offer two solutions.
| Plan Name | Pricing |
|---|---|
| Wiz Essential | $24,000/ 12 months; $48,000 /24 months; $72,000 /36 months. |
| Wiz Advanced | $38,000/ 12 months; $76,000/ 24 months $114,000/ 36 months. |
Testimonials
Pros
+ The tool is easy to use. Easy to implement into various public clouds. Also the support from Wiz.
Cons
– The security graph is really fine grained to the point that it is difficult to filter what you are looking for and organize it in a tabular view as you need.
It has a steep learning curve to master it.
9. Intruder
This Tenable alternative offers continuous vulnerability scanning and prioritization, empowering businesses to stay one step ahead of potential attackers.
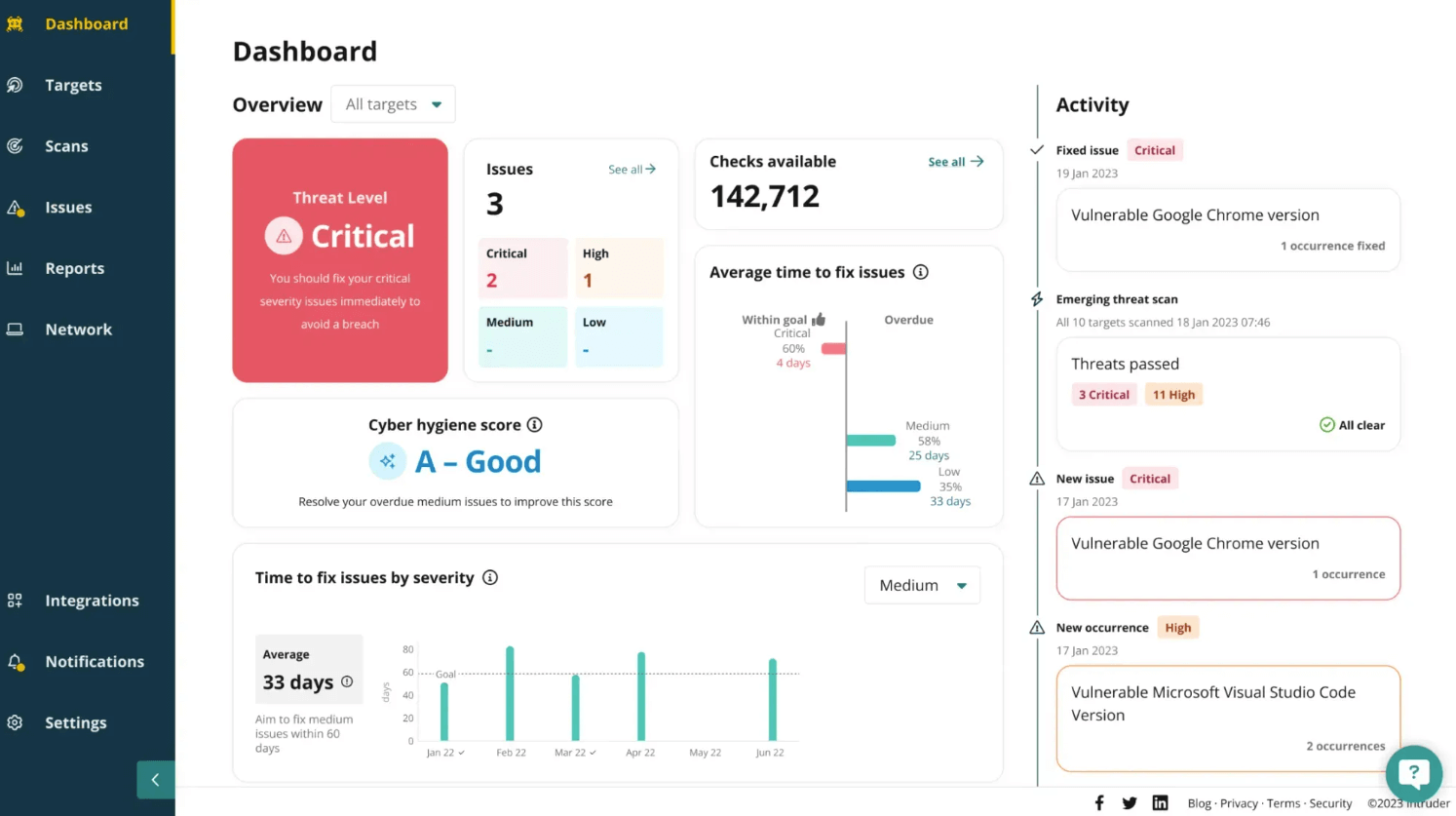
Key Features
- Automated and continuous scanning of your digital infrastructure to identify vulnerabilities in real time.
- Prioritize vulnerabilities based on their severity and the likelihood of exploitation.
Pricing
Intruder’s Pricing Options.
| Plan name | Pricing |
|---|---|
| Essential | $157 per month, billed at $1,884 per year. |
| Pro | $221 per month, billed at $2,656 per year. |
| Premium | Starting from $3,633 per year. |
Testimonials
Pros
+ The scanner allowed our company to pass security assessments and allowed us to participate in various engagements.
It helped me determine what computers were out of date with software, and some registry issues I didn’t know existed in Windows.
The monthly reports were a great tool to see what updates were available, especially as a small business running remotely.
The GUI is great to see what’s wrong at a glance. Customer support is quick and friendly.
Cons
– Some agents would sometimes stop responding and the only fix was a re-install, this was further compounded by having then wait 30 days for the license to be released before re-adding, this also made re-imaging laptops as we had to wait 30 days for them to be re-added.
10. SentinelOne
SentinelOne’s unique approach combines endpoint protection, detection, and response in a single, easy-to-use solution.
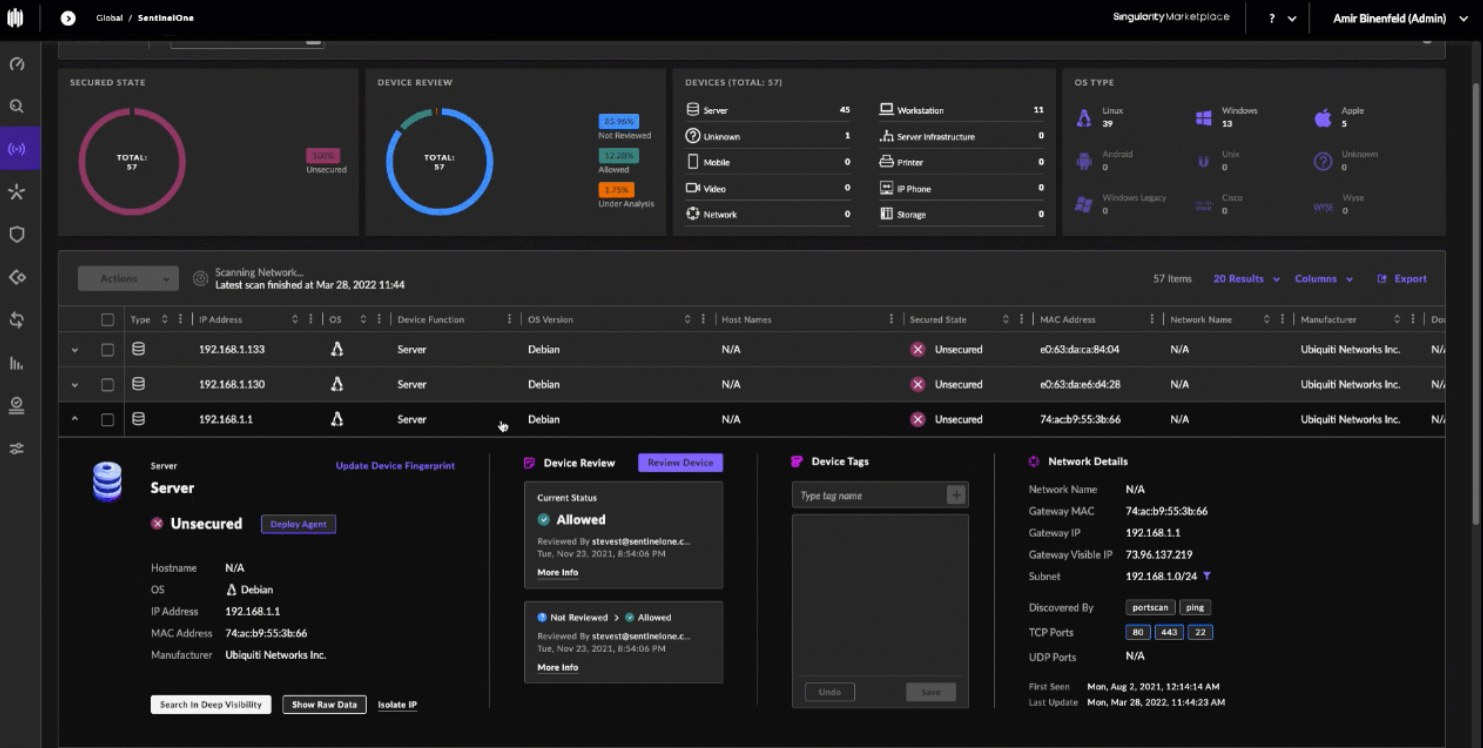
SentinelOne Key Features
- Rapidly identify high-velocity threats.
- Effortlessly remediate and roll back with just one click.
- Tailor your endpoint and detection dashboard to suit your needs.
Pricing
The cost varies depending on the features and services needed, with prices ranging from $4 to $6 per month per device.
Testimonials
Pros
+ EDR that constantly updates without intervention.
Scans attached drives, and computers when files are downloaded with automatically.
Onboarding walks you step by step to get setup and using the portal quickly and efficiently.
Support is always available.
Threats are stopped automatically and restored back to normal if set to protection mode vs just detection mode.
Cons
One thing that I dislike about SentinelOne is that there is no way to further categorize a report once it has been ran.
The end result, depending on the frequency can be slightly overwhelming as you a sifting through the large list of reports.
This is something that can be improved overtime and has a great amount of potential.
Frequently Asked Questions (FAQs)
Q: What kind of tool is Tenable?
A: Tenable One is a platform for managing exposure, crafted to assist your organization in understanding its modern attack surface, directing efforts towards preventing likely attacks, and effectively conveying cyber risk to enhance overall business performance.
Q: Is Tenable a vulnerability scanner?
A: Tenable equips you with the essential vulnerability assessment tools to achieve a holistic view and deep understanding of your entire environment. Nessus extends its coverage to encompass over 47,000 distinct assets, encompassing IT, IoT, and OT devices, various operating systems, a diverse array of applications, and much more.
Q:What is Tenable Nessus?
A: Nessus, created by Tenable, is a versatile platform designed to check for security weaknesses in devices, applications, operating systems, cloud services, and various network assets.
Q: Is Tenable suitable for businesses of all sizes?
A: Yes, Tenable is designed to serve businesses of different sizes, from small startups to large enterprises.
Q: Can Tenable One integrate with other security solutions?
A: Yes, Tenable One is designed to integrate seamlessly with various other security solutions and technologies.
If you want to keep up to date with everything we post, don’t forget to follow us on LinkedIn, Twitter, Facebook, and Youtube for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security











